信息网络安全 ›› 2024, Vol. 24 ›› Issue (6): 863-878.doi: 10.3969/j.issn.1671-1122.2024.06.005
基于区块链的可验证可撤销属性加密方案
- 1.西安邮电大学网络空间安全学院,西安 710121
2.西安邮电大学无线网络安全技术国家工程研究中心,西安 710121
-
收稿日期:2024-03-06出版日期:2024-06-10发布日期:2024-07-05 -
通讯作者:杨鑫xin_27334313@163.com -
作者简介:郭瑞(1984—),男,河南,副教授,博士,CCF会员,主要研究方向为属性加密、云计算及区块链安全|杨鑫(1996—),男,陕西,硕士研究生,主要研究方向为属性加密、区块链|王俊茗(1999—),男,陕西,硕士研究生,主要研究方向为数据共享、区块链 -
基金资助:国家自然科学基金(62072369);陕西省创新能力支持计划(2020KJXX-052);陕西省自然科学基金(2024JC-YBMS-545);陕西省重点研发计划(2020ZDLGY08-04)
Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain
GUO Rui1,2, YANG Xin1,2( ), WANG Junming1,2
), WANG Junming1,2
- 1. School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
2. National Engineering Research Center for Secured Wireless, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
-
Received:2024-03-06Online:2024-06-10Published:2024-07-05
摘要:
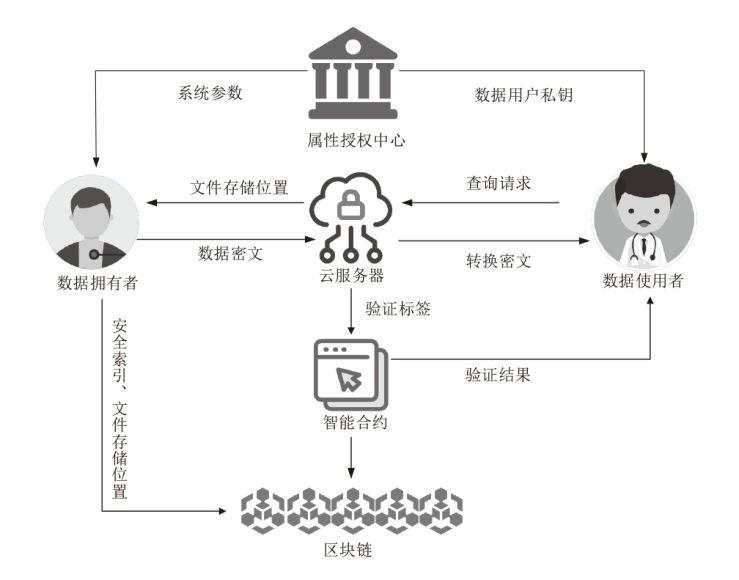
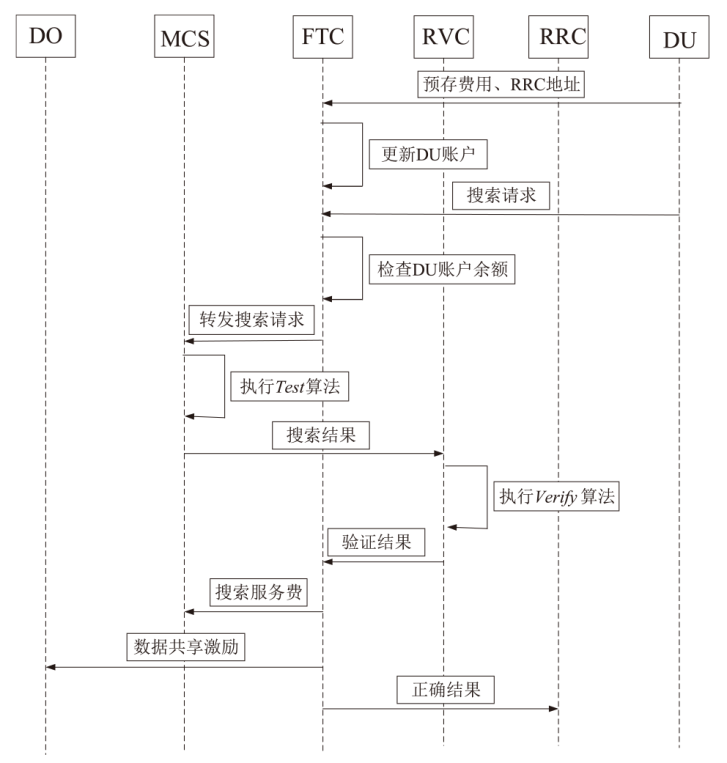
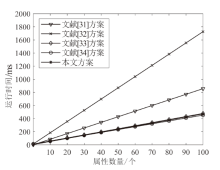
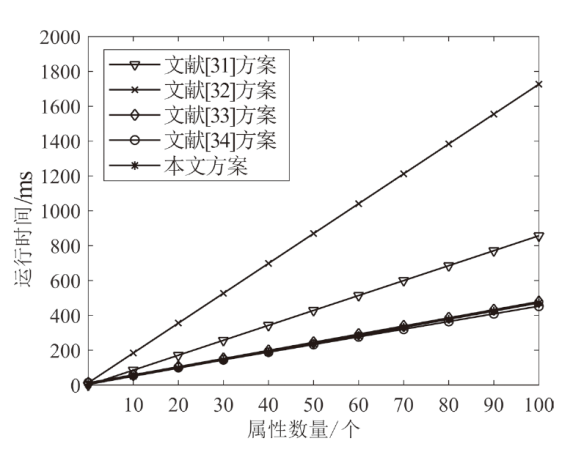
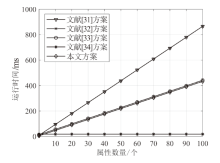
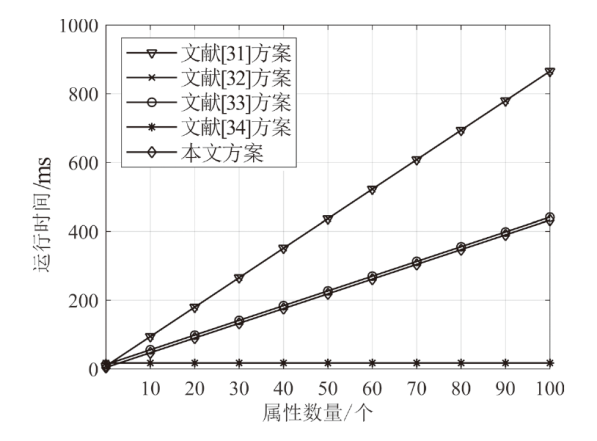
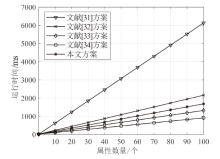
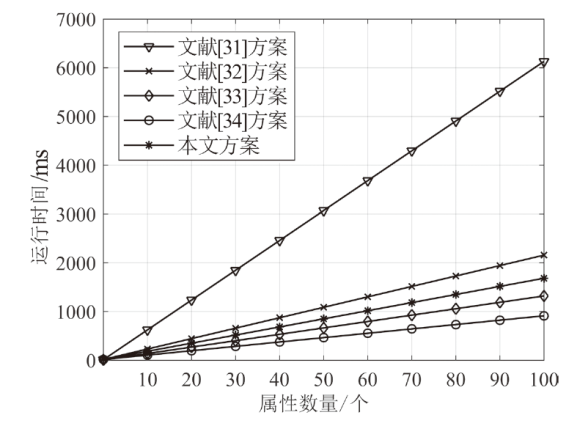
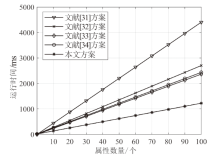
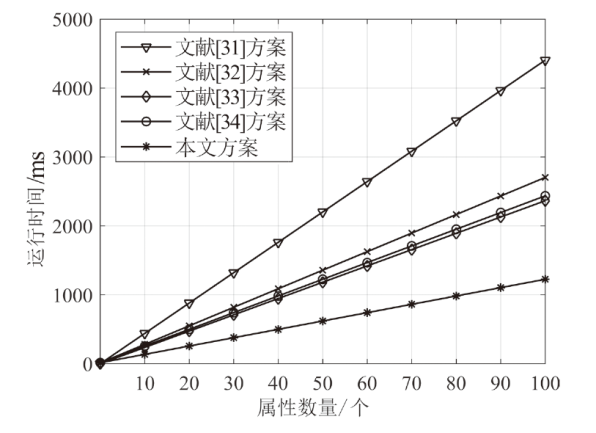
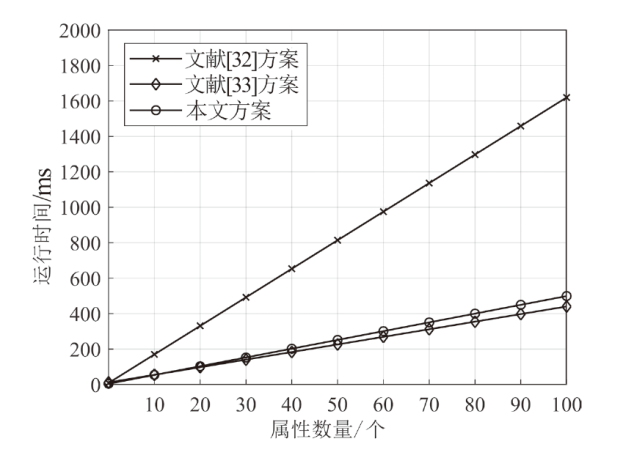
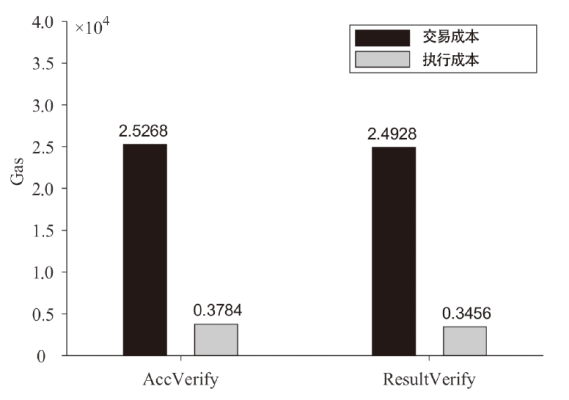
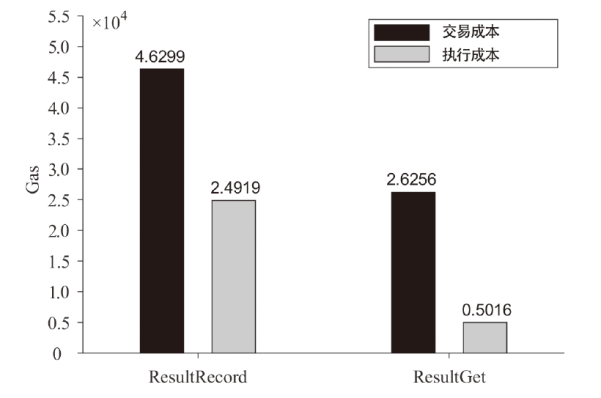
针对电子医疗系统在数据共享中存在的隐私泄露与用户权限管理问题,以及云存储服务器可能返回不完整、不正确的密文结果,文章提出了一种基于区块链的可验证可撤销属性加密方案。该方案利用密文策略属性加密技术,确保了电子病历系统中共享数据的机密性,实现了隐私数据的细粒度访问控制。同时,利用变色龙哈希函数设计了用户撤销算法,使得非授权用户无法继续访问共享数据。此外,利用密码累加器设计了结果验证算法,交由部署在区块链上的智能合约执行,确保了云服务器返回给用户数据的正确性与完整性。在安全性方面,证明了该方案的密文信息在选择明文攻击下是不可区分的。最后,使用JPBC密码库和Hyperledger Fabric区块链平台对文章所提方案与同类方案进行模拟仿真,结果表明该方案在密钥生成、加解密及用户撤销阶段均具有较高的计算效率。
中图分类号:
引用本文
郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878.
GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain[J]. Netinfo Security, 2024, 24(6): 863-878.
表3
通信成本比较
| 方案 算法开销 | 文献[ 方案 | 文献[ 方案 | 文献[ | 文献[ 方案 | 本文 方案 |
|---|---|---|---|---|---|
| 用户密钥 大小 | $2n\left| {{G}_{1}} \right|$ | $\begin{matrix} \left( 2n+2 \right)\left| {{G}_{1}} \right| \\ +n\left| {{Z}_{p}}^{*} \right| \\ \end{matrix}$ | $\left( n+3 \right)\left| {{G}_{1}} \right|$ | $n\left| {{G}_{1}} \right|$ | $n\left| {{G}_{1}} \right|$ |
| 转换密钥 大小 | $\left( n+2 \right)\left| {{G}_{1}} \right|+\left| {{G}_{2}} \right|$ | $\begin{matrix} \left( 2n+2 \right)\left| {{G}_{1}} \right|+ \\ n\left| {{Z}_{p}}^{*} \right| \\ \end{matrix}$ | $\left( n+3 \right)\left| {{G}_{1}} \right|$ | $\left( n+3 \right)\left| {{G}_{1}} \right|$ | $2n\left| {{G}_{1}} \right|$ |
| 密文 大小 | $\begin{align} & 3\left| I \right|\left| {{G}_{1}} \right|+(2\left| I \right|+ \\ & 2)\left| {{G}_{2}} \right|+2\left| I \right|\left| {{Z}_{p}}^{*} \right| \\ \end{align}$ | $\begin{matrix} \left( 3\left| I \right|+1 \right)\left| {{G}_{1}} \right| \\ +\left| {{G}_{2}} \right| \\ \end{matrix}$ | $\begin{matrix} \left( 2\left| I \right|+2 \right)\left| {{G}_{1}} \right| \\ +\left| {{G}_{2}} \right| \\ \end{matrix}$ | $\begin{align} & \left( 3\left| I \right|+2 \right)\left| {{G}_{1}} \right| \\ & +\left| {{G}_{2}} \right|+\left| {{Z}_{p}}^{*} \right| \\ \end{align}$ | $\begin{matrix} 2\left| I \right|\left| {{G}_{1}} \right|+ \\ \left| {{G}_{2}} \right| \\ \end{matrix}$ |
| 转换密文 大小 | $2\left| {{G}_{2}} \right|$ | $2\left| {{G}_{2}} \right|$ | $2\left| {{G}_{1}} \right|+\left| {{G}_{2}} \right|$ | $\left| {{G}_{2}} \right|$ | $\left| {{G}_{2}} \right|$ |
表5
计算开销比较
| 方案 算法 | 文献[ 方案 | 文献[ 方案 | 文献[ 方案 | 文献[ 方案 | 本文 方案 |
|---|---|---|---|---|---|
| 用户密钥 生成 | $2nE$ | $\left( 4n+3 \right)E$ | $\begin{align} & \left( n+3 \right)E+ \\ & M+nH \\ \end{align}$ | $\begin{align} & \left( n+1 \right)E+ \\ & nM+nH \\ \end{align}$ | $\begin{align} & P+\left( n+1 \right)E \\ & +nM+nH \\ \end{align}$ |
| 转换密钥 生成 | $\left( 2n+2 \right)E$ | $\left( 2n+2 \right)E$ | $\left( n+3 \right)E$ | $4E+M$ | $\left( n+1 \right)E$ |
| 加密 | $\begin{align} & \left( 3\left| I \right|+1 \right)P \\ & +\left( 9\left| I \right|+1 \right)E \\ \end{align}$ | $\begin{align} & P+(5\left| I \right|+ \\ & 2)E \\ \end{align}$ | $\begin{align} & P+(2\left| I \right|+ \\ & 2)E+(\left| I \right|+ \\ & 2)M+\left| I \right|H \\ \end{align}$ | $\begin{align} & \left| I \right|P+\left( 2\left| I \right|+4 \right)E \\ & +2\left| I \right|M+H \\ \end{align}$ | $\begin{align} & P+3\left| I \right|E+ \\ & \left| I \right|M \\ \end{align}$ |
| 外包解密 | $3\left| I \right|P+5\left| I \right|E$ | $\begin{align} & \left( 3\left| I \right|+1 \right)P \\ & +\left( \left| I \right|+1 \right)E \\ \end{align}$ | $\begin{align} & \left( 2\left| I \right|+2 \right)P+ \\ & 2\left| I \right|E+ \\ & \left( 2\left| I \right|+1 \right)M \\ \end{align}$ | $\begin{align} & \left( \left| I \right|+2 \right)P+ \\ & \left| I \right|E+\left| I \right|M \\ \end{align}$ | $2\left| I \right|P+2\left| I \right|E$ |
| 用户解密 | $E$ | $E$ | $P+E$ | $E$ | $E$ |
| 用户撤销 | — | $\begin{align} & nP+(2n+ \\ & 2)E \\ \end{align}$ | $\begin{align} & \left( n+1 \right)E+ \\ & 2nM+nH \\ \end{align}$ | — | $P+\left( n+1 \right)E$ |
| [1] | SUN Jianfei, XU Guowen, ZHANG Tianwei, et al. Share Your Data Carefree: An Efficient, Scalable and Privacy-Preserving Data Sharing Service in Cloud Computing[J]. IEEE Transactions on Cloud Computing, 2023, 11(1): 822-838. |
| [2] | LIU Jingwei, FAN Yue, SUN Rong, et al. Blockchain-Aided Privacy-Preserving Medical Data Sharing Scheme for E-Healthcare System[J]. IEEE Internet of Things Journal, 2023, 10(24): 21377-21388. |
| [3] | DENG Hua, QIN Zheng, WU Qianhong, et al. Achieving Fine-Grained Data Sharing for Hierarchical Organizations in Clouds[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(2): 1364-1377. |
| [4] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. Advances in Cryptology - Eurocrypt 2005. Heidelberg: Springer, 2005: 457-473. |
| [5] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. Proceedings of The IEEE Symposium on Security and Privacy. New York: IEEE, 2007: 321-334. |
| [6] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data[C]// ACM. Proceedings of the 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [7] | THUSHARA G A, BHANU S M. A Survey on Secured Data Sharing Using Ciphertext-Policy Attribute-Based Encryption in Cloud[C]// IEEE.Proceedings of the 8th International Conference on Smart Computing and Communications (ICSCC). New York: IEEE, 2021: 170-177. |
| [8] | ZHONG Hong, ZHOU Yiyuan, ZHANG Qinyang, et al. An Efficient and Outsourcing-Supported Attribute-Based Access Control Scheme for Edge-Enabled Smart Healthcare[J]. Future Generation Computer Systems, 2021, 115: 486-496. |
| [9] | GREEN M, HOHENBERGER S, WATERS B. Outsourcing the Decryption of ABE Ciphertexts[C]// USENIX. Proceedings of the 20th Usenix Conference on Security. Berlin:USENIX, 2011: 1-16. |
| [10] | LI Li, ZHU Jiangwen, YANG Chunyan. Overview of Research on the Revocable Mechanism of Attribute-Based Encryption[J]. Netinfo Security, 2023, 23(4): 39-50. |
| 李莉, 朱江文, 杨春艳. 基于属性加密的可撤销机制研究综述[J]. 信息网络安全, 2023, 23(4): 39-50. | |
| [11] | LI Tian, WANG huaqun, HE Debiao, et al. Blockchain-Based Privacy-Preserving and Rewarding Private Data Sharing for IoT[J]. IEEE Internet of Things Journal, 2022, 9(16): 15138-15149. |
| [12] | OLIVEIRA M T D, REIS L H A, VERGINADIS Y, et al. Smartaccess: Attribute-Based Access Control System for Medical Records Based on Smart Contracts[J]. IEEE Access, 2022(10): 117836-117854. |
| [13] | KRAWCZYK H, RABIN T. Chameleon Signatures[C]// NDSS. Proceedings of The Network and Distributed Systems Security Symposium (NDSS). New York: NDSS, 2000: 143-154. |
| [14] | QIN Baodong, DENG R H, LIU Shengli, et al. Attribute-Based Encryption with Efficient Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(7): 1384-1393. |
| [15] | WANG Huaqun, HE Debiao, HAN Jinguang. VOD-ADAC: Anonymous Distributed Fine-Grained Access Control Protocol with Verifiable Outsourced Decryption in Public Cloud[J]. IEEE Transactions on Services Computing, 2020, 13(3): 572-583. |
| [16] | QIU Tie, CHI Jiancheng, ZHOU Xiaobo, et al. Edge Computing in Industrial Internet of Things: Architecture, Advances and Challenges[J]. IEEE Communications Surveys & Tutorials, 2020, 22(4): 2462-2488. |
| [17] | ZHONG Hong, ZHOU Yiyuan, ZHANG Qingyang, et al. An Efficient and Outsourcing-Supported Attribute-Based Access Control Scheme for Edge-Enabled Smart Healthcare[J]. Future Generation Computer Systems, 2021, 115: 486-496. |
| [18] | ZHANG Wenfang, CHEN Zhen, LIU Xudong, et al. CP-ABE Scheme Supporting Fine-Grained Attribute Direct Revocation[J]. Journal of Software, 2019, 30(9): 2760-2771. |
| 张文芳, 陈桢, 刘旭东, 等. 支持细粒度属性直接撤销的CP-ABE方案[J]. 软件学报, 2019, 30(9):2760-2771. | |
| [19] |
SUN Lei, ZHAO Zhiyuan, WANG Jianhua, et al. Attribute-Based Encryption Scheme Supporting Attribute Revocation in Cloud Storage Environment[J]. Journal on Communications, 2019, 40(5): 47-56.
doi: 10.11959/j.issn.1000-436x.2019116 |
|
孙磊, 赵志远, 王建华, 等. 云存储环境下支持属性撤销的属性基加密方案[J]. 通信学报, 2019, 40(5):47-56.
doi: 10.11959/j.issn.1000-436x.2019116 |
|
| [20] | RAMU G, REDDY B E, JAYANTHI A, et al. Fine-Grained Access Control of EHRs in Cloud Using CP-ABE with User Revocation[J]. Health and Technology, 2019, 9(4): 487-96. |
| [21] | WEI Jianghong, CHEN Xiaofeng, HUANG Xinyi, et al. RS-HABE: Revocable-Storage and Hierarchical Attribute-Based Access Scheme for Secure Sharing of E-Health Records in Public Cloud[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(5): 2301-2315. |
| [22] | GUO Yuyan, LU Zhenhua, GE Hui, et al. Revocable Blockchain-Aided Attribute-Based Encryption with Escrow-Free in Cloud Storage[J]. IEEE Transactions on Computers, 2023, 72(7): 1901-1912. |
| [23] | LIU Jingwei, LI Xiaolu, YE Lin, et al. BPDS: A Blockchain Based Privacy-Preserving Data Sharing for Electronic Medical Records[C]// IEEE. Global Communications Conference. New York: IEEE, 2018: 1-6. |
| [24] | FAN Kai, PAN Qiang, ZHANG Kuan, et al. A Secure and Verifiable Data Sharing Scheme Based on Blockchain in Vehicular Social Networks[J]. IEEE Transactions on Vehicular Technology, 2020, 69(6): 5826-5835. |
| [25] | YAN Guanchen, JIANG Shunrong, LI Shengli, et al. Secure and Efficient Fuzzy Search for EHR Sharing Based on Consortium Blockchain[J]. Journal of Cryptologic Research, 2022, 9(5): 805-819. |
| [26] | WANG Zhiwei, CHEN Qinging, LIU Lei. Permissioned Blockchain-Based Secure and Privacy-Preserving Data Sharing Protocol[J]. IEEE Internet of Things Journal, 2023, 10(12): 10698-10707. |
| [27] | BEIMEL A. Secure Schemes for Secret Sharing and Key Distribution[EB/OL]. [2024-01-06]. https://www.researchgate.net/publication/243781866_Secure_Schemes_for_Secret_Sharing_and_Key_Distribution. |
| [28] | ROUSELAKIS Y, WATERS B. Practical Constructions and New Proof Methods for Large Universe Attribute-Based Encryption[C]// ACM.Proceedings of the 2013 ACM Conference on Computer & Communications Security. New York: ACM, 2013: 463-474. |
| [29] | BENALOH J, MARE M D. One-Way Accumulators: A Decentralized Alternative to Digital Signatures[C]// Springer. Advances in Cryptology—EUROCRYPT. Heidelberg: Springer, 2001: 274-285. |
| [30] | DE C A, IOVINO V. JPBC: Java Pairing Based Cryptography[C]// IEEE. 2011 IEEE Symposium on Computers and Communications (ISCC), New York: IEEE, 2011: 850-855. |
| [31] | DE S J, RUJ S. Efficient Decentralized Attribute-Based Access Control for Mobile Clouds[J]. IEEE Transactions on Cloud Computing, 2017, 8(1): 124-37. |
| [32] | MA Hui, ZHANG Rui, SUN Shuzhou, et al. Server-Aided Fine-Grained Access Control Mechanism with Robust Revocation in Cloud Computing[J]. IEEE Transactions on Services Computing, 2019, 15(1): 164-73. |
| [33] | ZHAO Jing, ZENG Peng, CHOO K K R. An Efficient Access Control Scheme with Outsourcing and Attribute Revocation for Fog-Enabled E-health[J]. IEEE Access, 2021, 9: 13789-13799. |
| [34] |
FAN Kai, XU Huiyue, GAO Longxiang, et al. Efficient and Privacy Preserving Access Control Scheme for Fog-Enabled IoT[J]. Future Generation Computer Systems, 2019, 99: 134-142.
doi: 10.1016/j.future.2019.04.003 |
| [1] | 凌治, 杨明, 余江银. 基于IPFS和区块链技术的电力安全交易平台研究[J]. 信息网络安全, 2024, 24(6): 968-976. |
| [2] | 田钊, 牛亚杰, 佘维, 刘炜. 面向车联网的车辆节点信誉评估方法[J]. 信息网络安全, 2024, 24(5): 719-731. |
| [3] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [4] | 胡海洋, 刘畅, 王栋, 魏旭. 基于区块链的清洁能源数据溯源机制[J]. 信息网络安全, 2024, 24(4): 626-639. |
| [5] | 薛茗竹, 胡亮, 王明, 王峰. 基于联邦学习和区块链技术的TAP规则处理系统[J]. 信息网络安全, 2024, 24(3): 473-485. |
| [6] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [7] | 何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238. |
| [8] | 吴昊天, 李一凡, 崔鸿雁, 董琳. 基于零知识证明和区块链的联邦学习激励方案[J]. 信息网络安全, 2024, 24(1): 1-13. |
| [9] | 朱郭诚, 何德彪, 安浩杨, 彭聪. 基于区块链和SM9数字签名的代理投票方案[J]. 信息网络安全, 2024, 24(1): 36-47. |
| [10] | 公鹏飞, 谢四江, 程安东. 基于HotStuff改进的多主节点共识算法[J]. 信息网络安全, 2023, 23(9): 108-117. |
| [11] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [12] | 赵佳豪, 蒋佳佳, 张玉书. 基于动态默克尔哈希树的跨链数据一致性验证模型[J]. 信息网络安全, 2023, 23(9): 95-107. |
| [13] | 邵震哲, 蒋佳佳, 赵佳豪, 张玉书. 面向跨链的改进加权拜占庭容错算法[J]. 信息网络安全, 2023, 23(8): 109-120. |
| [14] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [15] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||