信息网络安全 ›› 2024, Vol. 24 ›› Issue (2): 309-318.doi: 10.3969/j.issn.1671-1122.2024.02.014
基于Attention-BiTCN的网络入侵检测方法
- 1.空军工程大学防空反导学院,西安 710051
2.航天器在轨故障诊断与维修重点实验室,西安 710043
-
收稿日期:2023-10-04出版日期:2024-02-10发布日期:2024-03-06 -
通讯作者:孙红哲 E-mail:byxarrk@163.com -
作者简介:孙红哲(1983—),男,河北,工程师,硕士研究生,主要研究方向为入侵检测、网络安全态势感知|王坚(1982—),男,陕西,副教授,硕士,主要研究方向为智能信息处理、网络安全防护|王鹏(1999—),男,山东,博士研究生,主要研究方向为智能信息处理|安雨龙(1988—),男,陕西,助理工程师,硕士,主要研究方向为网络安全防护 -
基金资助:国家自然科学基金(61703426);国家自然科学基金(61876189)
Network Intrusion Detection Method Based on Attention-BiTCN
SUN Hongzhe1,2( ), WANG Jian1, WANG Peng1, AN Yulong2
), WANG Jian1, WANG Peng1, AN Yulong2
- 1. School of Air and Missile Defense, Air Force Engineering University, Xi’an 710051, China
2. Key Laboratory for Fault Diagnosis and Maintenance of Spacecraft in-Orbit, Xi’an 710043, China
-
Received:2023-10-04Online:2024-02-10Published:2024-03-06 -
Contact:SUN Hongzhe E-mail:byxarrk@163.com
摘要:
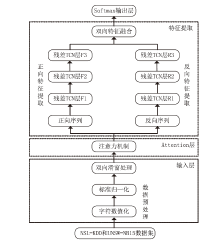
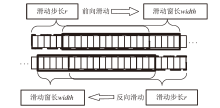
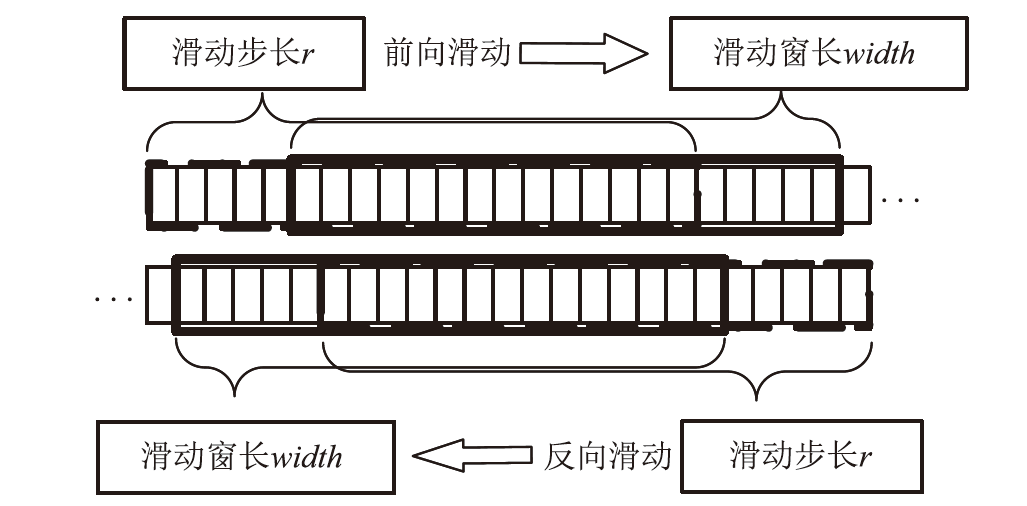
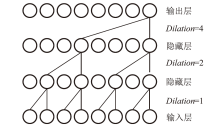
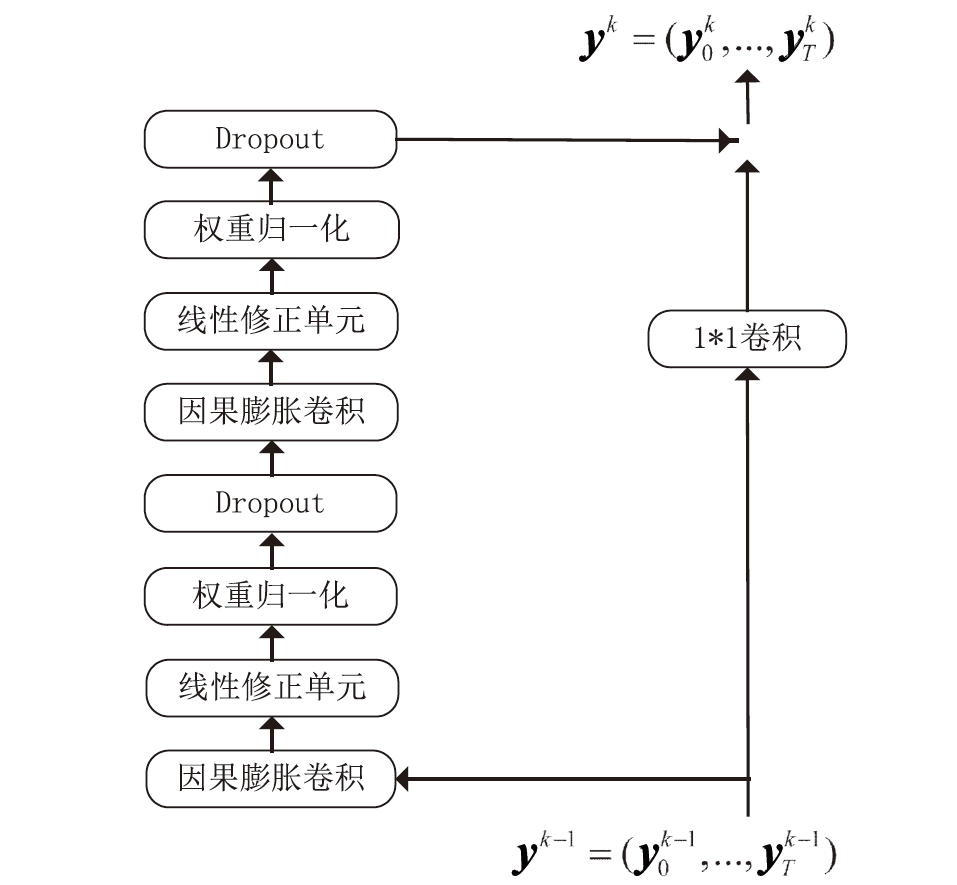
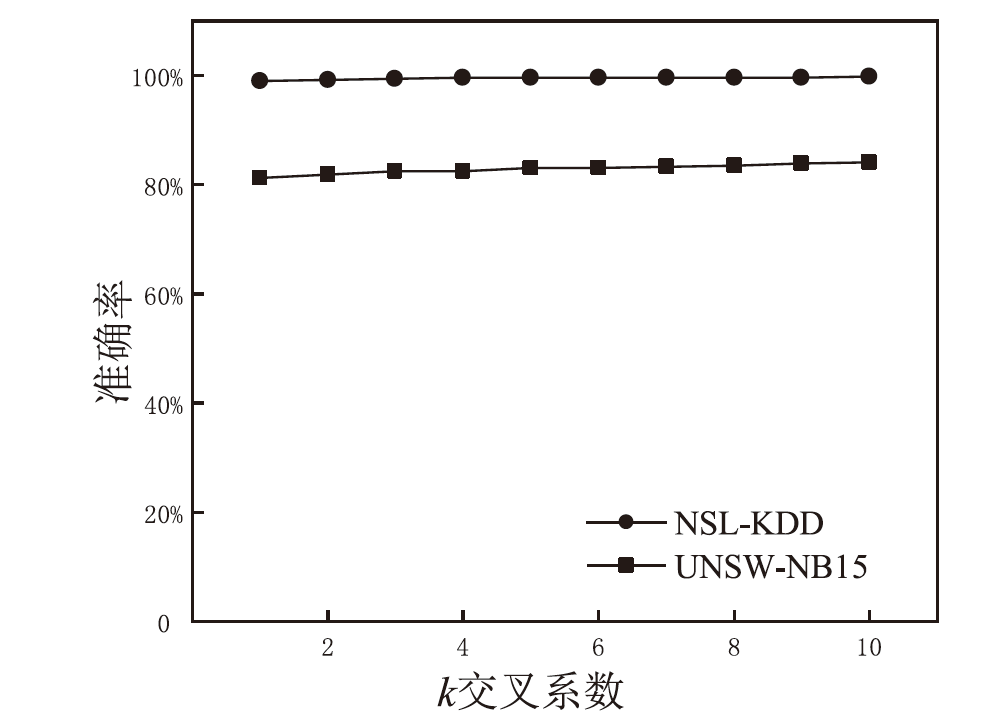
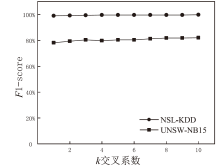
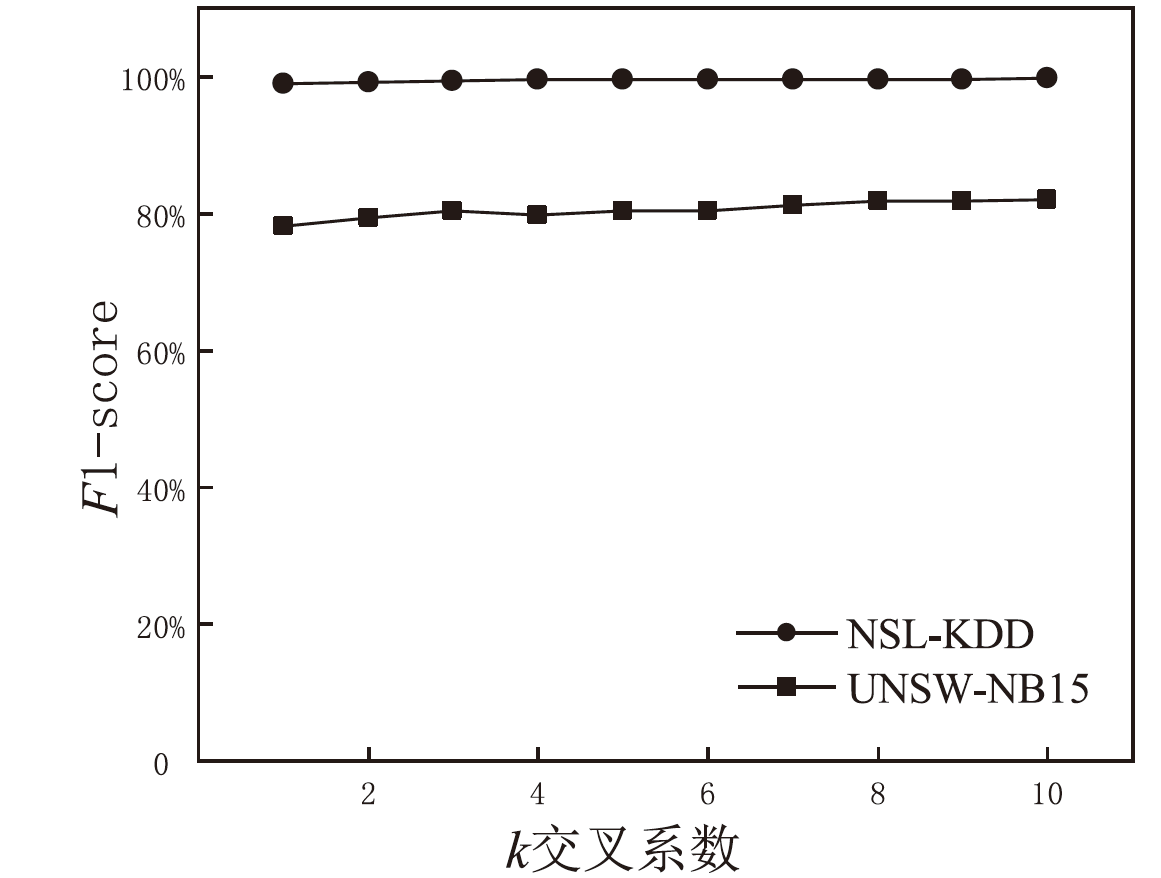
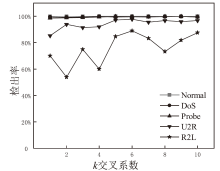
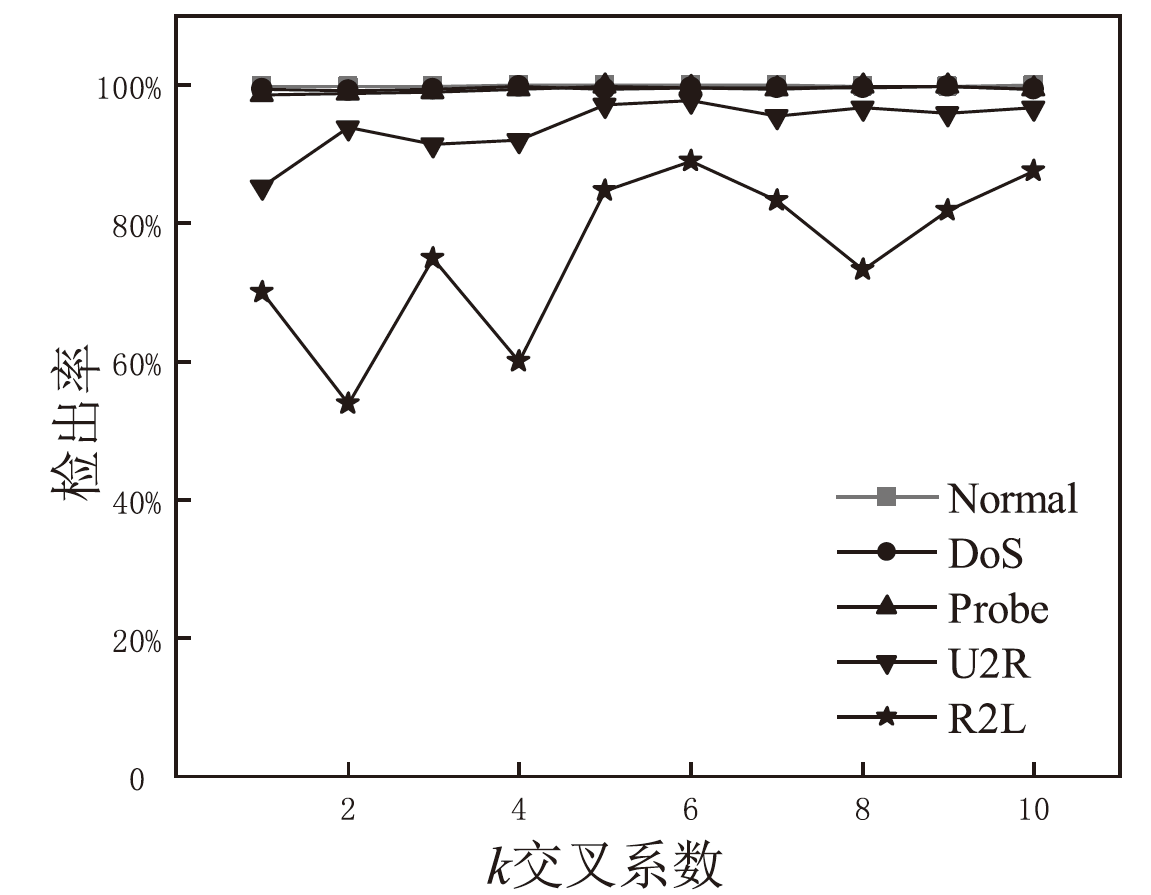
为解决网络入侵检测领域多分类准确率不高的问题,文章根据网络流量数据具有时序特征的特点,提出一种基于注意力机制和双向时间卷积神经网络(Bi-Directional Temporal Convolutional Network,BiTCN)的网络入侵检测模型。首先,该模型对数据集进行独热编码和归一化处置等预处理,解决网络流量数据离散性强和标度不统一的问题;其次,将预处理好的数据经双向滑窗法生成双向序列,并同步输入Attention-BiTCN模型中;然后,提取双向时序特征并通过加性方式融合,得到时序信息被增强后的融合特征;最后,使用Softmax函数对融合特征进行多种攻击行为检测识别。文章所提模型在NSL-KDD和UNSW-NB15数据集上进行实验验证,多分类准确率分别达到99.70%和84.07%,优于传统网络入侵检测算法,且比其他深度学习模型在检测性能上有显著提升。
中图分类号:
引用本文
孙红哲, 王坚, 王鹏, 安雨龙. 基于Attention-BiTCN的网络入侵检测方法[J]. 信息网络安全, 2024, 24(2): 309-318.
SUN Hongzhe, WANG Jian, WANG Peng, AN Yulong. Network Intrusion Detection Method Based on Attention-BiTCN[J]. Netinfo Security, 2024, 24(2): 309-318.
| [1] | SHARMA S, GUPTA R K. Intrusion Detection System: A Review[J]. International Journal of Software and Its Applications, 2015, 9(5): 69-76. |
| [2] | JIAN Shijie, LU Zhigang, DU Dan, et al. Overview of Network Intrusion Detection Technology[J]. Journal of Cyber Security, 2020, 5(4): 96-122. |
| 蹇诗婕, 卢志刚, 杜丹, 等. 网络入侵检测技术综述[J]. 信息安全学报, 2020, 5(4): 96-122. | |
| [3] |
SHENG Long, YUAN Lina, WU Nannan, et al. Network Anomaly Detection Model Based on GSA and DE Optimizing Hybrid Kernel ELM[J]. Computer Engineering, 2022, 48(6): 146-153.
doi: 10.19678/j.issn.1000-3428.0061509 |
|
生龙, 袁丽娜, 武南南, 等. 基于GSA与DE优化混合核ELM的网络异常检测模型[J]. 计算机工程, 2022, 48(6): 146-153.
doi: 10.19678/j.issn.1000-3428.0061509 |
|
| [4] |
SULTANA N, CHILAMKURTI N, PENG W, et al. Survey on SDN Based Network Intrusion Detection System Using Machine Learning Approaches[J]. Peer-to-Peer Networking and Applications, 2019, 12(2): 493-501.
doi: 10.1007/s12083-017-0630-0 |
| [5] |
MISHRA P, VARADHARAJAN V, TUPAKULA U, et al. A Detailed Investigation and Analysis of Using Machine Learning Techniques for Intrusion Detection[J]. IEEE Communications Surveys and Tutorials, 2019, 21(1): 686-728.
doi: 10.1109/COMST.2018.2847722 URL |
| [6] | ARHAN B I, JASIM A D. A Survey of Intrusion Detection Using Deep Learning in INTERNET of Things[J]. Iraqi Journal for Computer Science and Mathematics, 2022(31): 83-93. |
| [7] |
ZHANG Hao, ZHANG Xiaoyu, ZHANG Zhenyou, et al. Summary of Intrusion Detection Models Based on Deep Learning[J]. Computer Engineering and Applications, 2022, 58(6): 17-28.
doi: 10.3778/j.issn.1002-8331.2107-0084 |
|
张昊, 张小雨, 张振友, 等. 基于深度学习的入侵检测模型综述[J]. 计算机工程与应用, 2022, 58(6): 17-28.
doi: 10.3778/j.issn.1002-8331.2107-0084 |
|
| [8] |
LE T T H, KIM Y, KIM H. Network Intrusion Detection Based on Novel Feature Selection Model and Various Recurrent Neural Networks[J]. Applied Sciences, 2019, 9(7): 1-29.
doi: 10.3390/app9010001 URL |
| [9] | LI Xiangang, WU Xihong. Constructing Long Short-Term Memory Based Deep Recurrent Neural Networks for Large Vocabulary Speech Recognition[C]// IEEE. 2015 IEEE International Conference on Acoustics, Speech and Signal Processing(ICASSP). New York:IEEE, 2015: 4520-4524. |
| [10] | SINGH N B, SINGH M M, SARKAR A, et al. A Novel Wide & Deep Transfer Learning Stacked GRU Framework for Network Intrusion Detection[EB/OL]. (2021-09-10)[2023-09-26]. https://www.researchgate.net/publication/353138019_A_novel_wide_deep_transfer_learning_stacked_GRU_framework_for_network_intrusion_detection. |
| [11] | ZHANG Anlin, ZHANG Qikun, HUANG Daoying, et al. Intrusion Detection Model Based on CNN and BiGRU Fused Neural Network[J]. Journal of Zhengzhou University (Engineering Science), 2022, 43(3): 37-43. |
| 张安琳, 张启坤, 黄道颖, 等. 基于CNN与BiGRU融合神经网络的入侵检测模型[J]. 郑州大学学报(工学版), 2022, 43(3): 37-43. | |
| [12] | LIU Zhihui. Research on Network Intrusion Detection of Advanced Metering Infrastructure Based on Parallel CNN-GRU[D]. Dalian: Dalian University of Technology, 2022. |
| 刘智慧. 基于并行CNN-GRU的高级量测体系网络入侵检测研究[D]. 大连: 大连理工大学, 2022. | |
| [13] | IMRANA Y, XIANG Yanping, ALI L, et al. A Bidirectional LSTM Deep Learning Approach for Intrusion Detection[EB/OL]. (2021-12-05)[2023-09-26]. https://doi.org/10.1016/j.eswa.2021.115524. |
| [14] | YANG Shuaichuang, TAN Minsheng, XIA Shiying, et al. A Method of Intrusion Detection Based on Attention-LSTM Neural Network[C]// ACM. The 2020 5th International Conference on Machine Learning Technologies. New York: ACM, 2020: 46-50. |
| [15] | TAO Zhiyong, YAN Minghao, LIU Ying. Channel Coding Closed Set Recognition Based on Temporal Convolutional Networks[J]. Journal of Huazhong University of Science and Technology (Natural Science Edition), 2022, 50(3): 12-17. |
| 陶志勇, 闫明豪, 刘影. 基于时序卷积网络的信道编码闭集识别[J]. 华中科技大学学报(自然科学版), 2022, 50(3): 12-17. | |
| [16] | SARIKA C K, NISHTHA K. Analysis of KDD-Cup’99, NSL-KDD and UNSW-NB15 Datasets Using Deep Learning in IoT[J]. Procedia Computer Science, 2020(167): 1561-1573. |
| [17] | GEETA K, GULSHAN K. Analysis of Machine Learning Algorithms with Feature Selection for Intrusion Detection Using UNSW-NB15 Dataset[J]. International Journal of Network Security & Its Applications, 2021, 13(1): 21-31. |
| [18] | ACHARYA T, KHATRI I, ANNAMALAI A, et al. Efficacy of Machine Learning-Based Classifiers for Binary and Multi-Class Network Intrusion Detection[C]// IEEE. 2021 IEEE International Conference on Automatic Control & Intelligent Systems. New York: IEEE, 2021: 402-407. |
| [19] | WANG Xiaodan, WANG Peng, SONG Yafei, et al. HRRP Recognition of Midcourse Ballistic Targets Based on AF-BiTCN[EB/OL]. (2023-03-07)[2023-05-10]. https://doi.org/10.13700/j.bh.1001-5965.2023.0025. |
| 王晓丹, 王鹏, 宋亚飞, 等. 基于AF-BiTCN的弹道目标HRRP识别[EB/OL]. (2023-03-07)[2023-05-10]. https://doi.org/10.13700/j.bh.1001-5965.2023.0025. | |
| [20] | ZHU Mingkang. Human Action Recognition Algorithm Based on BiLSTM-Attention Model[J]. Advances in Laser and Optoelectronics, 2019, 56(15): 153-161. |
| 朱铭康. 基于Bi-LSTM-Attention模型的人体行为识别算法[J]. 激光与光电子学进展, 2019, 56(15): 153-161. | |
| [21] | XIE Xiaoyu. Research on Intrusion Detection Model Based on Convolutional Neural Network[D]. Nanjing: Nanjing University of Posts and Telecommunications, 2019. |
| 谢潇雨. 基于卷积神经网络的入侵检测模型研究[D]. 南京: 南京邮电大学, 2019. | |
| [22] | WANG Hui, CAO Zijian, HONG Bo. A Network Intrusion Detection System Based on Convolutional Neural Network[J]. Journal of Intelligent & Fuzzy Systems, 2020, 38(6): 7623-7637. |
| [23] | BAI Shaojie, KOLTER J Z, KOLTUN V. Trellis Networks for Sequence Modeling[EB/OL]. (2018-12-21)[2023-09-26]. https://github.com/locuslab/trellisnet. |
| [24] | ZHOU Haoyi, ZHANG Shanghang, PENG Jieqi, et al. Informer: Beyond Efficient Transformer for Long Sequence Time-Series Forecasting[EB/OL]. (2021-05-28)[2023-09-26]. https://www.xueshufan.com/publication/3111507638. |
| [25] | ZHAO Wentian, GAO Yanyun, JI Tingxiang, et al. Deep Temporal Convolutional Networks for Short-Term Traffic Flow Forecasting[J]. IEEE Access, 2019(7): 114496-114507. |
| [26] | BAI Shaojie, KOLTER J Z, KOLTUN V. An Empirical Evaluation of Generic Convolutional and Recurrent Networks for Sequence Modeling[EB/OL]. (2018-04-19)[2023-09-26]. https://arxiv.org/pdf/1803.01271.pdf. |
| [27] | SALIMANS T, KINGMA D P. Weight Normalization: A Simple Reparameterization to Accelerate Training of Deep Neural Networks[J]. Advances in Neural Information Processing Systems, 2016(29): 901-909. |
| [28] | SRIVASTAVA N, HINTON G E, KRIZHEVSKY A, et al. Dropout: A Simple Way to Prevent Neural Networks from Overfitting[J]. Journal of Machine Learning Research, 2014, 15(1): 1929-1958. |
| [29] | RAI K, DEVI M S, GULERIA A. Decision Tree Based Algorithm for Intrusion Detection[J]. International Journal of Advanced Networking and Applications, 2016, 7(4): 2828-2834. |
| [30] | XIA Jingming, LI Chong, TAN Ling, et al. Improved Intrusion Detection Method of Random Forest Classifier Network[J]. Computer Engineering and Design, 2019, 40(8): 2146-2150. |
| 夏景明, 李冲, 谈玲, 等. 改进的随机森林分类器网络入侵检测方法[J]. 计算机工程与设计, 2019, 40(8): 2146-2150. | |
| [31] | LI Jun, XIA Songzhu, LAN Haiyan, et al. Network Intrusion Detection Method Based on GRU-RNN[J]. Journal of Harbin Engineering University, 2021, 42(6): 879-884. |
| 李俊, 夏松竹, 兰海燕, 等. 基于GRU-RNN的网络入侵检测方法[J]. 哈尔滨工程大学学报, 2021, 42(6): 879-884. | |
| [32] | SHEN Jiquan, WEI Kun. CR-BiGRU Intrusion Detection Model Based on Residual Network[J]. Journal of Jilin University(Science Edition), 2023, 61(2): 353-361. |
| 沈记全, 魏坤. 融合残差网络的CR-BiGRU入侵检测模型[J]. 吉林大学学报(理学版), 2023, 61(2): 353-361. |
| [1] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [2] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [3] | 沈华, 田晨, 郭森森, 慕志颖. 基于对抗性机器学习的网络入侵检测方法研究[J]. 信息网络安全, 2023, 23(8): 66-75. |
| [4] | 彭翰中, 张珠君, 闫理跃, 胡成林. 联盟链下基于联邦学习聚合算法的入侵检测机制优化研究[J]. 信息网络安全, 2023, 23(8): 76-85. |
| [5] | 刘刚, 杨雯莉, 王同礼, 李阳. 基于云联邦的差分隐私保护动态推荐模型[J]. 信息网络安全, 2023, 23(7): 31-43. |
| [6] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [7] | 刘长杰, 石润华. 基于安全高效联邦学习的智能电网入侵检测模型[J]. 信息网络安全, 2023, 23(4): 90-101. |
| [8] | 高庆官, 张博, 付安民. 一种基于攻击图的高级持续威胁检测方法[J]. 信息网络安全, 2023, 23(12): 59-68. |
| [9] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [10] | 王华忠, 田子蕾. 基于改进CGAN算法的工控系统入侵检测方法[J]. 信息网络安全, 2023, 23(1): 36-43. |
| [11] | 刘翔宇, 芦天亮, 杜彦辉, 王靖翔. 基于特征选择的物联网轻量级入侵检测方法[J]. 信息网络安全, 2023, 23(1): 66-72. |
| [12] | 李季瑀, 付章杰, 张玉斌. 一种基于跨域对抗适应的图像信息隐藏算法[J]. 信息网络安全, 2023, 23(1): 93-102. |
| [13] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [14] | 张兴兰, 付娟娟. 基于辅助熵减的神经常微分方程入侵检测模型[J]. 信息网络安全, 2022, 22(6): 1-8. |
| [15] | 王浩洋, 李伟, 彭思维, 秦元庆. 一种基于集成学习的列车控制系统入侵检测方法[J]. 信息网络安全, 2022, 22(5): 46-53. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||