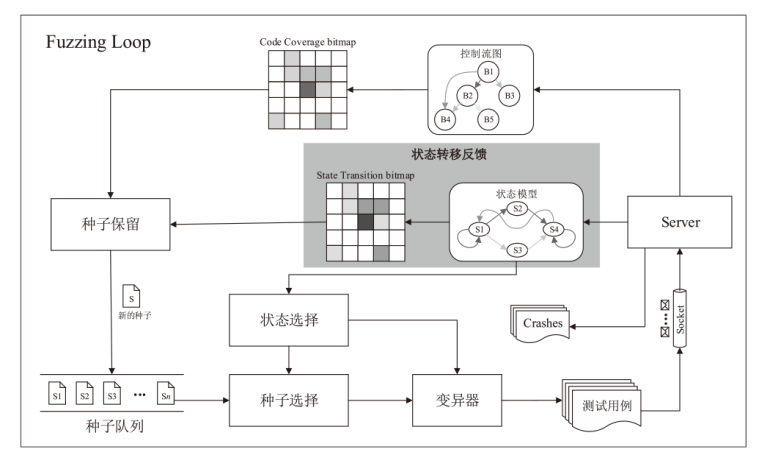
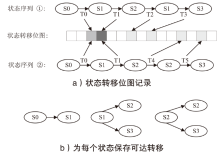
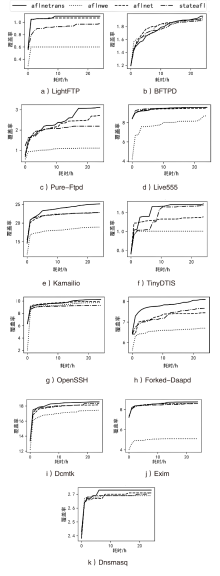
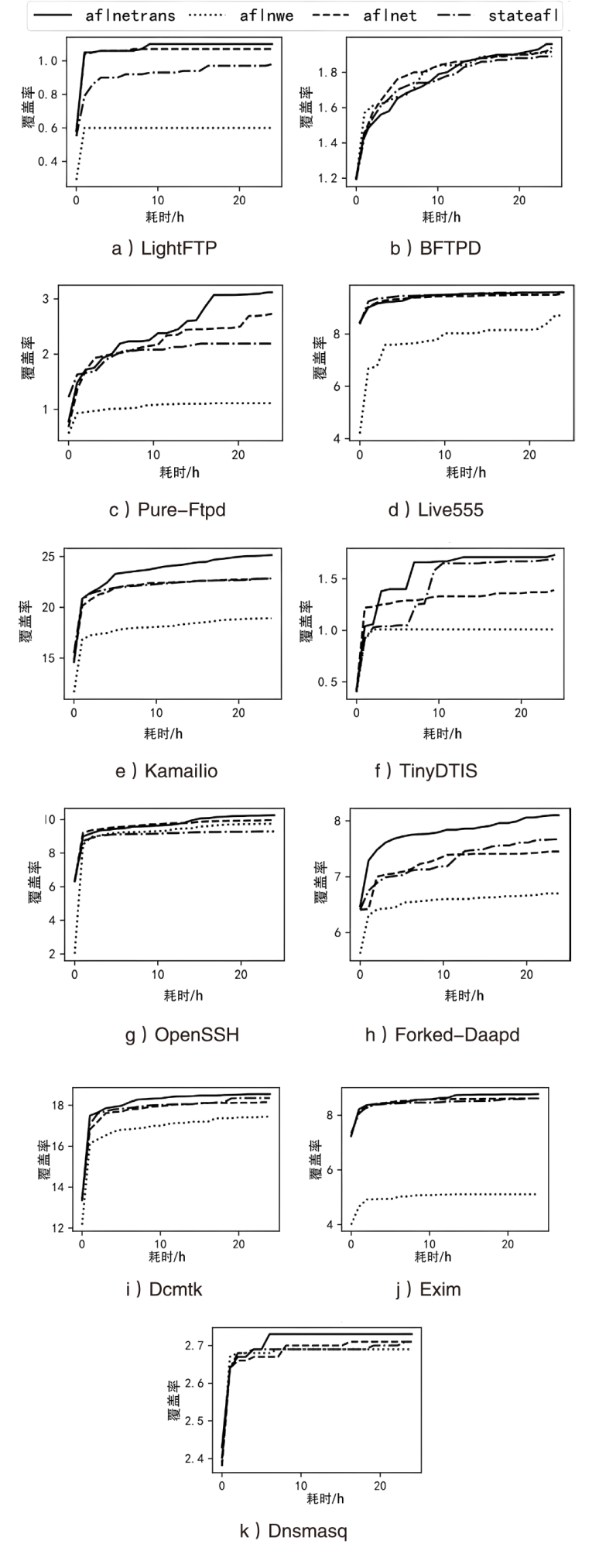
信息网络安全 ›› 2024, Vol. 24 ›› Issue (1): 121-132.doi: 10.3969/j.issn.1671-1122.2024.01.012
AFLNeTrans:状态间关系感知的网络协议模糊测试
- 四川大学网络空间安全学院,成都 610065
-
收稿日期:2023-09-04出版日期:2024-01-10发布日期:2024-01-24 -
通讯作者:贾鹏 E-mail:pengjia@scu.edu.cn -
作者简介:洪玄泉(1999—),男,广西,硕士研究生,主要研究方向为二进制安全|贾鹏(1988—),男,河南,副教授,博士,CCF会员,主要研究方向为漏洞挖掘和软件动静态分析|刘嘉勇(1962—),男,四川,教授,博士,主要研究方向为网络应用安全和信息内容安全 -
基金资助:国家重点研发计划(2021YFB3101803)
AFLNeTrans: Fuzzing of Protocols with State Relationship Awareness
HONG Xuanquan, JIA Peng( ), LIU Jiayong
), LIU Jiayong
- School of Cyber Science and Engineering, Sichuan University, Chengdu 610065, China
-
Received:2023-09-04Online:2024-01-10Published:2024-01-24 -
Contact:JIA Peng E-mail:pengjia@scu.edu.cn
摘要:
网络协议是现代通信系统中不可缺少的部分,其实现程序的安全性不容忽视。模糊测试已经成为现代漏洞挖掘的主流方式,并在软件安全领域中取得了较大的成功。网络协议模糊测试通常指对网络协议实现程序进行模糊测试,然而传统模糊测试在此类程序的测试上仍存在一些问题。首先,由于网络协议实现程序中不同状态对应不同代码,传统灰盒模糊测试中使用的代码覆盖不能表示网络协议实现程序的内部状态。其次现有灰盒协议模糊器中的状态引导机制依赖于代码覆盖率,不能很好地挖掘网络协议实现程序的状态间关系。对此,文章提出了一种由协议状态间关系和程序代码覆盖率共同引导模糊测试过程从而提升模糊测试效果的模糊器AFLNeTrans,其利用状态间关系作为主要引导机制,引导模糊测试快速探索协议实现程序更多的状态空间,并在Profuzzbench上对其进行了评估实验。实验结果表明,AFLNeTrans在发现状态转移数量上有较明显的提升,并且在代码覆盖率和unique_crash数量上相比现有工具也有提升。
中图分类号:
引用本文
洪玄泉, 贾鹏, 刘嘉勇. AFLNeTrans:状态间关系感知的网络协议模糊测试[J]. 信息网络安全, 2024, 24(1): 121-132.
HONG Xuanquan, JIA Peng, LIU Jiayong. AFLNeTrans: Fuzzing of Protocols with State Relationship Awareness[J]. Netinfo Security, 2024, 24(1): 121-132.
表2
AFLNET和AFLNeTrans在24 h内平均状态转移的数量
| 软件 | AFLNET | AFLNeTrans |
|---|---|---|
| LightFTP | 316 | 336 (6.3%↑) |
| BFTPD | 296 | 310(4.7%↑) |
| Pure-Ftpd | 377 | 415(10.1%↑) |
| Live555 | 95 | 105 (10.3%↑) |
| Kamailio | 154 | 343 (122.7%↑) |
| TinyDTLS | 3 | 3(-) |
| OpenSSH | 2105 | 2296(9.1%↑) |
| Forked-Daapd | 34 | 65(91.2%↑) |
| Dcmtk | 3 | 3(-) |
| Exim | 55 | 73(32.7%↑) |
| Dnsmasq | 4826 | 7325(51.8%↑) |
| 共计 | 8264 | 11274(36.4%↑) |
表3
4个模糊器在24 h内unique_crash的数量
| 软件 | AFLNET/个 | AFLNWE/个 | StateAFL/个 | AFLNeTrans/个 |
|---|---|---|---|---|
| LightFTP | 0 | 0(-) | 0 | 0(-) |
| BTFPD | 33 | 38(15.2↑) | 40(21.2%↑) | 47(42.4%↑) |
| Pure-Ftpd | 0 | 0(-) | 0(-) | 0(-) |
| Live555 | 160 | 95(40.6%↓) | 207(29.4%↑) | 165(3.12%↑) |
| Kamailio | 1 | 0(100%↓) | 0(100%↓) | 6(500%↑) |
| TinyDTLS | 33 | 23(30.3%↓) | 35(6.1%↑) | 47(42.4%↑) |
| OpenSSH | 0 | 0(-) | 0(-) | 0(-) |
| Forked-daapd | 0 | 0(-) | 0(-) | 0(-) |
| Dcmtk | 14 | 0(100%↓) | 17(21.4%↑) | 20(42.9%↑) |
| Exim | 0 | 0(-) | 0(-) | 0(-) |
| Dnsmasq | 40 | 35(12.5%↓) | 45(12.5%↑) | 46(15.0%↑) |
| 共计 | 281 | 191(39.2%↓) | 344(22.4%↑) | 331(17.8%↑) |
| [1] | LIU Jian, SU Purui, YANG Min, et al. Software and Cyber Security-A Survey[J]. Journal of Software, 2018, 29(1): 42-68. |
| 刘剑, 苏璞睿, 杨珉, 等. 软件与网络安全研究综述[J]. 软件学报, 2018, 29(1): 42-68. | |
| [2] | BEYONDT. Microsoft Vulnerabilities Report 2023[EB/OL]. [2023-08-26]. https://assets.beyondtrust.com/assets/documents/2023-Microsoft-Vulnerability-Report_BeyondTrust.pdf. |
| [3] | CARVALHO M, DeMott J, FORD R, et al. Heartbleed 101[J]. IEEE Security & Privacy, 2014, 12(4): 63-67. |
| [4] | GOODIN D. NSA-Leaking Shadow Brokers Just Dumped Its Most Damaging Release Yet[EB/OL]. (2017-04-15) [2023-08-26]. https://arstechnica.com/security/2017/04/nsa-leaking-shadow-brokers-just-dumped-its-most-damaging-release-yet/. |
| [5] | MICHAL Z. AFL(American Fuzzy Lop)[EB/OL]. [2023-08-26] https://github.com/google/AFL. |
| [6] | LLVM Organization. Libfuzzer- A Library for Coverage-Guided Fuzz Testing[EB/OL]. [2023-08-26]. https://llvm.org/docs/LibFuzzer.html. |
| [7] | GOOGLE Inc. HonggFuzz: A Security-Oriented, Feedback-Driven, Evolutionary, Easy-to-Use Fuzzer with Interesting Analysis Options[EB/OL]. [2023-08-26]. https://github.com/google/honggfuzz. |
| [8] | MICHAEL E. Peach Fuzzing Platform[EB/OL]. [2023-08-26]. https://gitlab.com/peachtech/peach-fuzzer-community. |
| [9] | JTPEREYDA. Boofuzz: Network Protocol Fuzzing for Humans[EB/OL]. [2023-08-26]. https://github.com/jtpereyda/boofuzz. |
| [10] | PHAM V, BÖHME M, ROYCHOUDHURY A. AFLNet: A Greybox Fuzzer for Network Protocols[C]// IEEE. 2020 IEEE 13th International Conference on Software Testing, Validation and Verification (ICST). New York: IEEE, 2020: 460-465. |
| [11] | WIKIPEDIA. Multi-Armed Bandit Problem[EB/OL]. [2023-08-26]. https://en.wikipedia.org/wiki/Multi-armed_bandit. |
| [12] | KULESHOV V, PRECUP D. Algorithms for Multi-Armed Bandit Problems[EB/OL]. (2014-02-25) [2023-08-26]. https://doi.org/10.48550/arXiv.1402.6028. |
| [13] | BÖHME M, PHAM V T, ROYCHOUDHURY A. Coverage-Based Greybox Fuzzing as Markov Chain[C]// ACM. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 1032-1043. |
| [14] | GAN Shuitao, ZHANG Chao, QIN Xiaojun, et al. Collafl: Path Sensitive Fuzzing[C]// IEEE. 2018 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2018: 679-696. |
| [15] | LYU Chenyang, JI Shouling, ZHANG Chao, et al. MOPT: Optimized Mutation Scheduling for Fuzzers[C]// USENIX. USENIX Security Symposium. New York: USENIX Association, 2019: 1949-1966. |
| [16] | WANG Yanhao, JIA Xiangkun, LIU Yuwei, et al. Not All Coverage Measurements Are Equal: Fuzzing by Coverage Accounting for Input Prioritization[C]// USENIX. Network and Distributed System Security 2020 (NDSS 2020). New York: USENIX Association, 2020: 1-20. |
| [17] | GAN Shuitao, ZHANG Chao, CHEN Peng, et al. GREYONE: Data Flow Sensitive Fuzzing[C]// USENIX. USENIX Security Symposium. New York: USENIX Association, 2020: 2577-2594. |
| [18] | YUN I, LEE S, XU Meng, et al. QSYM: A Practical Concolic Execution Engine Tailored for Hybrid Fuzzing[C]// USENIX. 27th USENIX Security Symposium (USENIX Security 2018). New York: USENIX Association, 2018: 745-761. |
| [19] | CORNELIUS A, SERGEJ S, ALI A, et al. Ijon: Exploring Deep State Spaces via Fuzzing[C]// IEEE. 2020 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2020: 1597-1612. |
| [20] | PEDRAM A. Sulley: A Pure-Python Fully Automated and Unattended Fuzzing Framework[EB/OL]. (2019-02-15) [2023-08-26]. https://github.com/OpenRCE/sulley. |
| [21] | THUAN P. AFLNWE[EB/OL]. (2020-10-01) [2023-08-26]. https://github.com/thuanpv/aflnwe. |
| [22] | LIU Dongge, PHAM V T, ERNST G, et al. State Selection Algorithms and Their Impact on The Performance of Stateful Network Protocol Fuzzing[C]// IEEE. 2022 IEEE International Conference on Software Analysis, Evolution and Reengineering (SANER). New York: IEEE, 2022: 720-730. |
| [23] |
NATELLA R. StateAFL: Greybox Fuzzing for Stateful Network Servers[J]. Empirical Software Engineering, 2022, 27(7): 1-12.
doi: 10.1007/s10664-021-10043-z |
| [24] |
LI Junqiang, LI Senyi, SUN Gang, et al. SNPSFuzzer: A Fast Greybox Fuzzer for Stateful Network Protocols Using Snapshots[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2673-2687.
doi: 10.1109/TIFS.2022.3192991 URL |
| [25] | ANDRONIDIS A, CADAR C. SnapFuzz: High-Throughput Fuzzing of Network Applications[C]// ACM. Proceedings of the 31st ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2022: 340-351. |
| [26] | BA J, BÖHME M, MIRZAMOMEN Z, et al. Stateful Greybox Fuzzing[C]// USENIX. 31st USENIX Security Symposium (USENIX Security 22). New York: USENIX Association, 2022: 3255-3272. |
| [27] | QIN Shisong, HU Fan, MA Zheyu, et al. NSFuzz: Towards Efficient and State-Aware Network Service Fuzzing[J]. ACM Transactions on Software Engineering and Methodology, 2023, 32(6): 1-26. |
| [28] | WUNDER M, LITTMAN M L, BABES M. Classes of Multiagent Q-learning Dynamics with Epsilon-greedy Exploration[C]// ICML. Proceedings of the 27th International Conference on Machine Learning (ICML-10). New York: ICML, 2010: 1167-1174. |
| [29] | LIU Yahui, CAO Buyang, LI Hehua. Improving Ant Colony Optimization Algorithm with Epsilon Greedy and Levy Flight[J]. Complex & Intelligent Systems, 2021, 7: 1711-1722. |
| [30] | NATELLA R, PHAM V T. PROFUZZBENCH: A Benchmark for Stateful Protocol Fuzzing[C]// ACM. Proceedings of the 30th ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2021: 662-665. |
| [31] | HFIREF0X. LightFTP[EB/OL]. (2023-07-22) [2023-08-26]. https://github.com/hfiref0x/LightFTP. |
| [32] | ROMAN G. Live555[EB/OL]. (2023-06-15) [2023-08-26]. https://github.com/rgaufman/live555. |
| [33] | DANIEL M. Kamailio-The Open Source SIP Server for Large VoIP and Real-time Communication Platforms[EB/OL].(2023-06-15) [2023-08-26]. https://github.com/rgaufman/live555. |
| [34] | CONTIKI. TinyDTLS[EB/OL]. (2022-09-13) [2023-08-26]. https://github.com/eclipse/tinydtls. |
| [35] | JESSEFRGSMITH. BFTPD[EB/OL]. [2023-08-26]. https://bftpd.sourceforge.net/index.html. |
| [36] | FRANK D. Pure-Ftpd[EB/OL]. (2022-10-01) [2023-08-26]. https://github.com/jedisct1/pure-ftpd. |
| [37] | DAMIEN M. OpenSSH-Portable[EB/OL]. [2023-08-26]. https://github.com/openssh/openssh-portable. |
| [38] | EJURGENSEN. Forked-Daapd[EB/OL]. [2023-08-26]. https://github.com/owntone/owntone-server. |
| [39] | RIESMEIER J. Dcmtk[EB/OL]. [2023-08-26]. https://github.com/Exim/exim. |
| [40] | PHIL P. Exim[EB/OL]. [2023-08-26]. https://github.com/Exim/exim. |
| [41] | SIMON K. Dnsmasq[EB/OL]. [2023-08-26]. https://thekelleys.org.uk/dnsmasq/. |
| [42] | SEREBRYANY K, BRUENING D, POTAPENKO A, et al. Addresssanitizer: A Fast Address Sanity Checker[C]// USENIX. USENIX Annual Technical Conference 2012. New York: USENIX Association, 2012: 1-10. |
| [1] | 王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16. |
| [2] | 钟远鑫, 刘嘉勇, 贾鹏. 基于动态时间切片和高效变异的定向模糊测试[J]. 信息网络安全, 2023, 23(8): 99-108. |
| [3] | 吴佳明, 熊焰, 黄文超, 武建双. 一种基于距离导向的模糊测试变异方法[J]. 信息网络安全, 2021, 21(10): 63-68. |
| [4] | 段斌, 李兰, 赖俊, 詹俊. 基于动态污点分析的工控设备硬件漏洞挖掘方法研究[J]. 信息网络安全, 2019, 19(4): 47-54. |
| [5] | 周悦, 王威, 郭剑虹, 何泾沙. 基于云平台的防御性软件测试服务系统[J]. 信息网络安全, 2018, 18(12): 46-53. |
| [6] | 王夏菁, 胡昌振, 马锐, 高欣竺. 二进制程序漏洞挖掘关键技术研究综述[J]. 信息网络安全, 2017, 17(8): 1-13. |
| [7] | 齐健, 陈小明, 游伟青. 基于fuzzing测试的网络协议安全评估方法研究[J]. 信息网络安全, 2017, 17(3): 59-65. |
| [8] | 郭亮, 罗森林, 潘丽敏. 编码函数交叉定位网络协议测试数据生成方法研究[J]. 信息网络安全, 2016, 16(3): 8-14. |
| [9] | 冯济舟, 田明辉. 软件潜在安全性缺陷测试案例的研究及思考[J]. 信息网络安全, 2015, 15(6): 85-90. |
| [10] | . 网络协议分析系统的设计与实现[J]. , 2014, 14(7): 48-. |
| [11] | . 基于模糊测试的网络协议自动化漏洞挖掘工具设计与实现[J]. , 2014, 14(6): 23-. |
| [12] | 张??尹毅峰;黄新彭;甘勇. 网络隐蔽通道的研究与实现[J]. , 2013, 13(7): 0-0. |
| [13] | 王昱镔;高博;程楠;吴薇. 软件测试中的信息安全问题[J]. , 2013, 13(5): 0-0. |
| [14] | 王学;李学新;周智鹏;袁耀文. S2E测试平台及并行性能分析[J]. , 2012, 12(7): 0-0. |
| [15] | 林炜. 两种软件测试方法的比较和改进[J]. , 2012, 12(7): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||