信息网络安全 ›› 2023, Vol. 23 ›› Issue (2): 76-84.doi: 10.3969/j.issn.1671-1122.2023.02.009
基于依赖关系的容器供应链脆弱性检测方法
- 1.上海交通大学网络信息中心,上海 200240
2.上海交通大学电子信息与电气工程学院,上海 200240
3.北京计算机技术及应用研究所,北京 100854
-
收稿日期:2022-11-08出版日期:2023-02-10发布日期:2023-02-28 -
通讯作者:陈力波 E-mail:bob777@sjtu.edu.cn -
作者简介:夏懿航(1996—),男,浙江,助理工程师,硕士,主要研究方向为Web安全|张志龙(1981—),男,江苏,高级工程师,博士研究生,主要研究方向为网络空间安全|王木子(1990—),男,北京,工程师,本科,主要研究方向为计算机软件工程|陈力波(1985—),男,江西,工程师,硕士,主要研究方向为网络与系统安全。 -
基金资助:国家重点研发计划(2022QY1702);国家广播电视总局实验室项目(TXX20200001ZSB001)
Dependency-Based Vulnerability Detection Method in Container Supply Chain
XIA Yihang1, ZHANG Zhilong2, WANG Muzi3, CHEN Libo2( )
)
- 1. Network & Information Center, Shanghai Jiao Tong University, Shanghai 200240, China
2. School of Electronic Information and Electrical Engineering, Shanghai Jiao Tong University, Shanghai 200240, China
3. Beijing Institute of Computer Technology and Applications, Beijing 100854, China
-
Received:2022-11-08Online:2023-02-10Published:2023-02-28 -
Contact:CHEN Libo E-mail:bob777@sjtu.edu.cn
摘要:
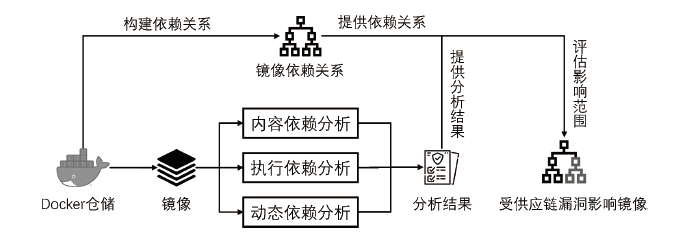
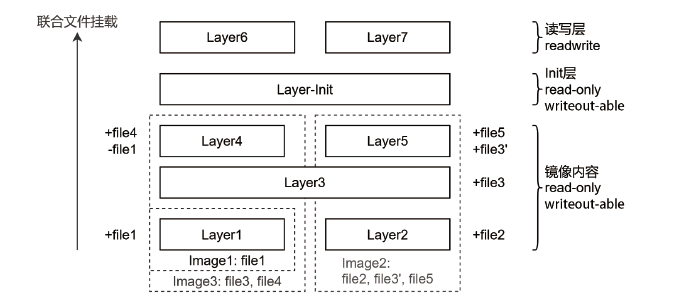
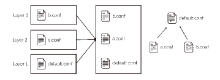
容器作为一种轻量化隔离方法,具有方便部署、易于移植等特点,近年来发展很快。容器的隔离性阻碍了内部软件成分被外部检测工具所获知,导致软件成分分析、安全评估等无法有效开展,阻碍了软件供应链安全检测。为了解决此问题,文章提出基于依赖关系的容器供应链脆弱性检测方法,区别于利用分析工具在容器运行时进行检测的方法,该方法以镜像为粒度,利用不同镜像中各个层之间的相关性,在解构镜像的基础上提取基于镜像依赖关系形成的软件供应链,能够检测到镜像内容依赖、执行配置依赖和动态构建依赖等多个维度导致的供应链安全问题。实验结果表明,文章所提方法在应对软件供应链的安全威胁时能发挥很好的检测作用,高效地发现了公开容器仓储(如Docker Hub)中存在的大量供应链安全隐患。
中图分类号:
引用本文
夏懿航, 张志龙, 王木子, 陈力波. 基于依赖关系的容器供应链脆弱性检测方法[J]. 信息网络安全, 2023, 23(2): 76-84.
XIA Yihang, ZHANG Zhilong, WANG Muzi, CHEN Libo. Dependency-Based Vulnerability Detection Method in Container Supply Chain[J]. Netinfo Security, 2023, 23(2): 76-84.
表1
受Log4Shell漏洞影响的官方镜像仓库
| 镜像仓库 | 修复版本 | 下载量/次 |
|---|---|---|
| couchbase | 7.0.3 | 50?106 |
| elasticsearch | 6.8.22, 7.16.2 | 500?106 |
| flink | 1.11.6, 1.12.7, 1.13.5, 1.14.2 | 50?106 |
| geonetwork | 3.10.10 | 1?106 |
| lightstreamer | 未知 | 5?106 |
| logstash | 6.8.22, 7.16.2 | 100?106 |
| neo4j | 4.4.2 | 100?106 |
| solr | 8.11.1 | 100?106 |
| sonarqube | 8.9.5, 9.2.2 | 500?106 |
| storm | 未知 | 5?106 |
表4
对部分恶意镜像影响范围的分析结果
| 镜像名 | 下载量/次 | 下游镜像数量/个 |
|---|---|---|
| thanhcongnhe/thanhcongnhe:latest | 10?106 | 0 |
| masterroshi/monero-miner:latest | 10?106 | 7 |
| masterroshi/aeon-miner:latest | 10?106 | 7 |
| masterroshi/xmrig-alpine:latest | 5?106 | 7 |
| masterroshi/electroneum-miner:latest | 5?106 | 7 |
| tempsbro/tempsbro1:latest | 1?106 | 0 |
| perfectweb/cryptonight:xmrig-v6.3.5 | 1?106 | 0 |
| metachain/miner-docker:latest | 1?106 | 0 |
| cnu015/vinnutech:mynanolatest | 1?106 | 0 |
| bartslaman/minerrig:latest | 1?106 | 0 |
| aasmuk13/xmr-miner-cpu:latest | 1?106 | 0 |
| brannondorsey/alpine-xmrig:latest | 1?106 | 1 |
| [1] | BAVOTA G, CANFORA G, DI P M, et al. The Evolution of Project Inter-Dependencies in a Software Ecosystem: the Case of Apache[C]// IEEE. 2013 IEEE International Conference on Software Maintenance. New York: IEEE, 2013: 280-289. |
| [2] | HE Xixun, ZHANG Yuqing, LIU Qixu. Survey of Software Supply Chain Security[J]. Journal of Cyber Security, 2020, 5(1): 57-73. |
| [3] | GADGE A. Is Open Source Software More Secure Than the Commercial Software?[EB/OL]. (2022-06-16)[2022-10-17]. https://www.ashnik.com/is-open-source-software-more-secure-than-the-commercial-software. |
| [4] | ELLISON R J, WOODY C. Supply-Chain Risk Management: Incorporating Security into Software Development[C]// IEEE. 2010 43rd Hawaii International Conference on System Sciences. New York: IEEE, 2010: 1-10. |
| [5] | LI Qiang, SONG Jinke, TAN Dawei, et al. Pdgraph: A Large-Scale Empirical Study on Project Dependency of Security Vulnerabilities[C]// IEEE. 2021 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). New York:IEEE, 2021: 161-173. |
| [6] | Apache Log4j. Apache Log4j Security Vulnerabilities[EB/OL]. (2022-09-13)[2022-10-17]. https://logging.apache.org/log4j/2.x/security.html. |
| [7] | RED Hat. What is CI/CD?[EB/OL]. (2022-05-11)[2022-10-17]. https://www.redhat.com/en/topics/devops/what-is-ci-cd. |
| [8] | Docker. Develop Faster Run Anywhere[EB/OL]. (2022-10-25)[2022-10-30]. https://www.docker.com. |
| [9] | Sysdig. Sysdig 2021 Container Security and Usage Report: Shifting Left is Not Enough[EB/OL]. (2021-01-13)[2022-10-17]. https://sysdig.com/blog/sysdig-2021-container-security-usage-report. |
| [10] | Banyanops. Banyan Collector: A Framework to Peek Inside Containers[EB/OL]. (2019-08-24)[2022-10-17]. https://github.com/banyanops/collector. |
| [11] | ROBIO E G. Dagda[EB/OL]. (2021-07-28)[2022-10-17]. https://github.com/eliasgranderubio/dagda. |
| [12] | Quay. Clair[EB/OL]. (2022-10-28)[2022-10-30]. https://github.com/quay/clair. |
| [13] | SHU Rui, GU Xiaohui, ENCK W. A Study of Security Vulnerabilities on Docker Hub[C]// ACM. 7th ACM on Conference on Data and Application Security and Privacy. New York: ACM, 2017: 269-280. |
| [14] | KWON S, LEE J H. Divds: Docker Image Vulnerability Diagnostic System[J]. IEEE Access, 2020(8): 42666-42673. |
| [15] | LIU Peiyu, JI Shouling, FU Lirong, et al. Understanding the Security Risks of Docker Hub[C]// Springer. European Symposium on Research in Computer Security. Berlin:Springer, 2020: 257-276. |
| [16] | Sonatype. 2021 State of the Software Supply Chain Report[EB/OL]. (2021-08-01)[2022-10-17]. https://www.sonatype.com/resources/state-of-the-software-supply-chain-2021. |
| [17] | ZIMMERMANN M, STAICU C A, TENNY C, et al. Small World with High Risks: A Study of Security Threats in the Npm Ecosystem[C]// USENIX. 28th USENIX Security Symposium (USENIX Security 19). Berkeley:USENIX, 2019: 995-1010. |
| [18] | OHM M, PLATE H, SYKOSCH A, et al. Backstabber’s Knife Collection: A Review of Open Source Software Supply Chain Attacks[C]// Springer. International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment. Berlin:Springer, 2020: 23-43. |
| [19] | VU D L, MASSACCI F, PASHCHENKO I, et al. Lastpymile: Identifying the Discrepancy Between Sources and Packages[C]// ACM. 29th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering. New York: ACM, 2021: 780-792. |
| [20] | CONTRAST Security. The Contrast Secure Code Platform[EB/OL]. (2022-02-15)[2022-10-17]. https://www.contrastsecurity.com. |
| [21] | MEND. Your Code We Cure[EB/OL]. (2022-05-25)[2022-10-17]. https://www.mend.io. |
| [22] | Sonatype. Code Smarter Fix Faster Be Secure[EB/OL]. (2021-06-30)[2022-10-17]. https://www.sonatype.com. |
| [23] | Docker. Generate the SBOM for Docker Images[EB/OL]. (2022-04-06)[2022-10-17]. https://docs.docker.com/engine/sbom/. |
| [24] | Anchore. Syft[EB/OL]. (2022-10-29)[2022-10-31]. https://github.com/anchore/syft. |
| [25] | Anchore. Grype[EB/OL]. (2022-10-28)[2022-10-31]. https://github.com/anchore/grype. |
| [26] | Snyk. Snyk CLI[EB/OL]. (2022-10-27)[2022-10-31]. https://github.com/snyk/cli. |
| [27] | SHUBHAM S. Apache Log4j: Return of the JNDI[EB/OL]. (2021-12-25)[2022-10-17]. https://dev.to/shubhamsah/apache-log4j-return-of-the-jndi-292o. |
| [28] | XMIRROR, ISC, China Telecom Research Institute. White Paper on Software Supply Chain Security Governance and Operation(2022)[EB/OL]. (2022-08-19)[2022-10-17]. https://www.xmirror.cn/resurce/Uploads/upfile/20220819/62ff585edcb2a.pdf. |
| 悬镜安全, ISC, 中国电信研究院. 软件供应链安全治理与运营白皮书 (2022)[EB/OL]. (2022-08-19)[2022-10-17]. https://www.xmirror.cn/resurce/Uploads/upfile/20220819/62ff585edcb2a.pdf. | |
| [29] | CHEN Libo, XIA Yihang, MA Zhenbang, et al. SEAF: A Scalable, Efficient, and Application-Independent Framework for Container Security Detection[EB/OL]. (2022-10-14)[2022-10-17]. https://www.sciencedirect.com/science/article/pii/S221421262200196X. |
| [1] | 边曼琳, 王利明. 云环境下Docker容器隔离脆弱性分析与研究[J]. 信息网络安全, 2020, 20(7): 85-95. |
| [2] | 范红, 邵华, 李海涛. 物联网安全技术实现与应用[J]. 信息网络安全, 2017, 17(9): 38-41. |
| [3] | 姚永锋;梅瑞;梅越. 基于DPI的数据内容安全检测算法优化与实现[J]. , 2013, 13(7): 0-0. |
| [4] | 范渊;凌霄. Android程序安全检测模型[J]. , 2013, 13(10): 0-0. |
| [5] | 韦兴军;唐志斌;袁建国. 可重构UTM报文安全检测引擎设计[J]. , 2013, 13(10): 0-0. |
| [6] | 高志新;徐御;金铭彦;盛璐. 关于云计算安全及检测要求的探讨[J]. , 2012, 12(Z): 0-0. |
| [7] | 王希忠;曲家兴;黄俊强;马春光. 网络数据库安全检测与管理程序设计实现[J]. , 2012, 12(2): 0-0. |
| [8] | 李炳龙;姜皇勤;龙腾. 基于交换分区主机行为安全检测系统设计与实现[J]. , 2010, (2): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||