信息网络安全 ›› 2023, Vol. 23 ›› Issue (2): 1-10.doi: 10.3969/j.issn.1671-1122.2023.02.001
基于加权贝叶斯分类器的LTE接入网中间人攻击检测研究
- 1.中国科学院信息工程研究所,北京 100085
2.中国科学院大学网络空间安全学院,北京 100049
3.中电长城网际系统应用有限公司,北京 102209
-
收稿日期:2022-12-14出版日期:2023-02-10发布日期:2023-02-28 -
通讯作者:范伟 E-mail:fanwei@iie.ac.cn -
作者简介:彭诚(1994—),男,北京,博士研究生,主要研究方向为移动通信安全、通信协议分析、微弱信号检测与识别|范伟(1984—),男,北京,高级工程师,博士,主要研究方向为网络空间安全、微弱信号检测与识别、移动通信信号处理|朱大立(1972—),男,北京,高级工程师,博士,主要研究方向为网络空间安全、移动通信安全|杨芬(1989—),女,北京,工程师,本科,主要研究方向为网络空间安全、大数据安全 -
基金资助:国家重点研发计划(2019YFB1005204)
Research on Man-in-the-Middle Attack Detection in LTE Access Network Based on Weighted Bayesian Classifier
PENG Cheng1,2, FAN Wei1,2( ), ZHU Dali1,2, YANG Fen3
), ZHU Dali1,2, YANG Fen3
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100085, China
2. School of Cyber Security, University of Chinese Academy of Sciences, Beijing 100049, China
3. China Electronics Cyberspace Great Wall Co., Ltd., Beijing 102209, China
-
Received:2022-12-14Online:2023-02-10Published:2023-02-28 -
Contact:FAN Wei E-mail:fanwei@iie.ac.cn
摘要:
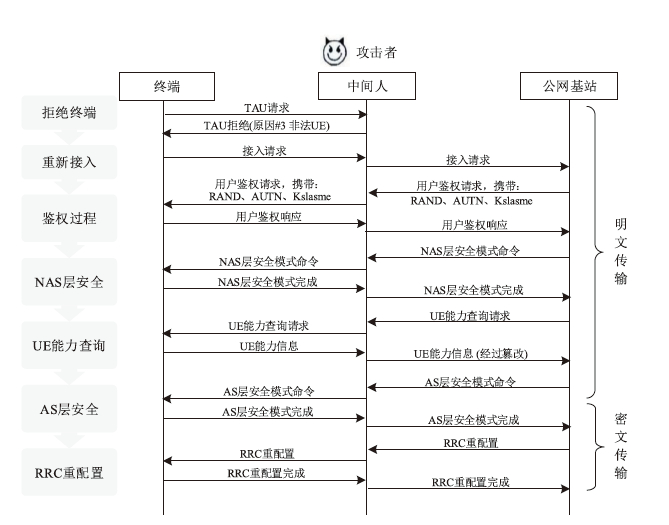
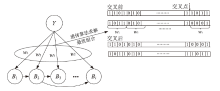
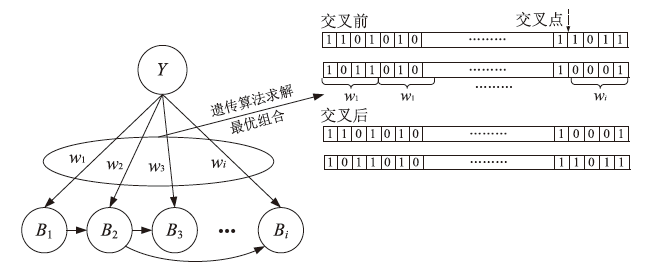
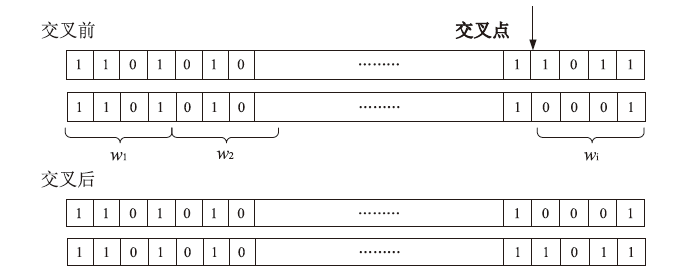
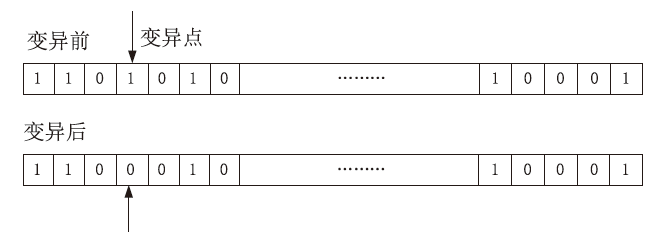
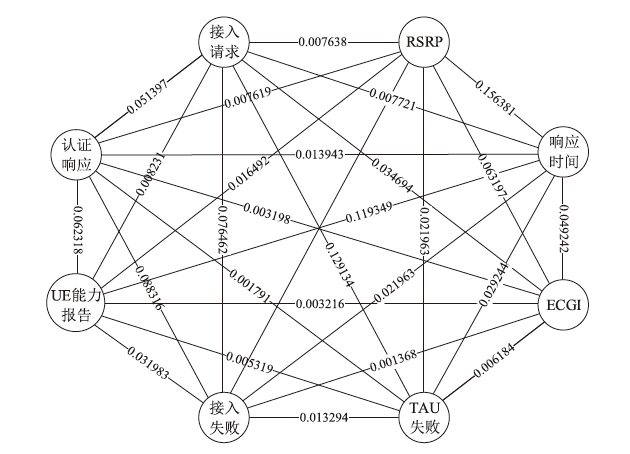
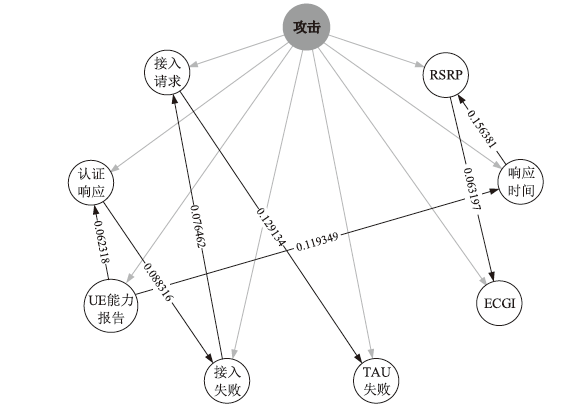
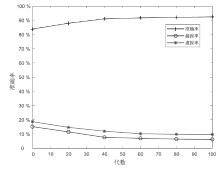
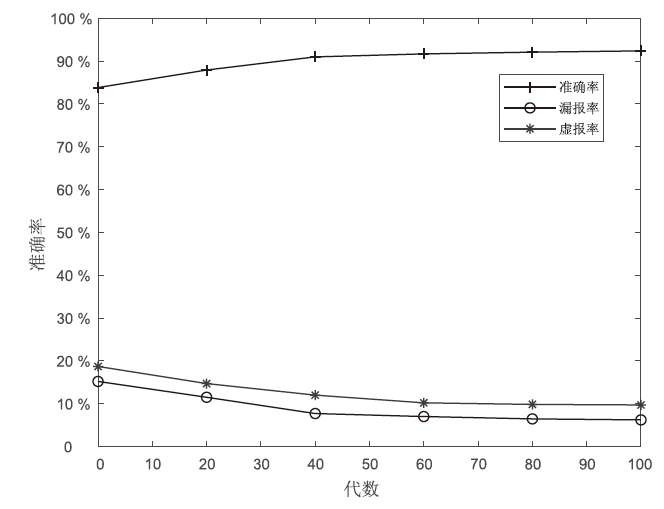
由于LTE接入网的开放特性,任何人都可以访问其空中接口,因此很容易受到攻击者的控制并遭受网络攻击。其中,中间人攻击是典型的攻击方式之一。文章以检测LTE接入网的中间人攻击为研究目的,以较容易受到中间人攻击的接入过程为研究对象,分析信令和参数变化,并提取8个具有可识别性的特征。由于每个特征对分类结果的影响不同,因此文章利用遗传算法在组合优化问题上的优势,求解加权贝叶斯分类器的权值最优组合,改进加权参数的计算方法,从信令和日志角度提出了一种中间人攻击检测算法。文章将所提基于加权贝叶斯分类器的检测算法与常用中间人检测方法进行对比验证,结果表明,该算法在准确率和漏报率指标上明显优于其他算法。
中图分类号:
引用本文
彭诚, 范伟, 朱大立, 杨芬. 基于加权贝叶斯分类器的LTE接入网中间人攻击检测研究[J]. 信息网络安全, 2023, 23(2): 1-10.
PENG Cheng, FAN Wei, ZHU Dali, YANG Fen. Research on Man-in-the-Middle Attack Detection in LTE Access Network Based on Weighted Bayesian Classifier[J]. Netinfo Security, 2023, 23(2): 1-10.
表1
UE能力等级与传输速率对应关系
| UE能力等级 | 协议版本 | 最高下行 速率/Mbps | 实现技术 |
|---|---|---|---|
| DL Category 0 | R12 | 1 | 1流 |
| DL Category 1 bis | R14 | 10 | 1流 |
| DL Category 4 | R14 | 150 | 2流 |
| DL Category 6 | R12 | 301 | 2流或4流,2载波聚合 |
| DL Category 7 | R12 | 301 | 2流或4流,2载波聚合 |
| DL Category 9 | R12 | 452 | 2流或4流,3载波聚合 |
| DL Category 10 | R12 | 452 | 2流或4流,3载波聚合 |
| DL Category 11 | R12 | 603 | 2流或4流,3载波聚合,256QAM |
| DL Category 12 | R12 | 603 | 2流或4流,3载波聚合,256QAM |
| [1] | 3GPP. 3GPP TS 33.401 Technical Specification Group Services and System Aspects; 3GPP System Architecture Evolution (SAE): Security architecture (Release17)[EB/OL]. (2022-06-17)[2022-11-14]. https://www.3gpp.org/ftp/Specs/archive/33_series/33.401. |
| [2] | LIAO Junkai, FENG Zhonghua. Security Threat Analysis of LTE Wireless Air Interface[J]. Communication Technology, 2017, 50(6): 1257-1263. |
| 廖竣锴, 冯中华. LTE无线空口安全威胁分析[J]. 通信技术, 2017, 50(6): 1257-1263. | |
| [3] | 3GPP. 3GPP TS 36.300 Technical Specification Group Radio Access Network; Evolved Universal Terrestrial Radio Access (E-UTRA) and Evolved Universal Terrestrial Radio Access Network (E-UTRAN)(Release16)[EB/OL]. (2021-12-23)[2022-11-14]. https://www.3gpp.org/ftp/Specs/archive/36_series/36.300. |
| [4] | ZHANG Lizhuo, JIA Weijia, SHENG Wen, et al. Man-in-the-Middle Attack on 3G-WLAN Interworking[C]// IEEE. 2010 International Conference on Communications and Mobile Computing. New York: IEEE, 2010: 121-125. |
| [5] | YU Bo. An Detection and Protection Method for Man-in the-Middle Attack in the Wireless Networks[D]. Beijing: Beijing University of Posts and Telecommunications, 2015. |
| 于波. 针对无线网络中间人攻击的检测与防御[D]. 北京: 北京邮电大学, 2015. | |
| [6] | LEI Yang. Based on Wireless Intrusion Prevention System’s Man in the Middle Attack Detection’s Design and Realization[D]. Wuhan: Huazhong University of Science and Technology, 2014. |
| 雷阳. 基于无线入侵防御系统的中间人攻击检测功能的设计与实现[D]. 武汉: 华中科技大学, 2014. | |
| [7] | MOHAPATRA S K, SWAIN B R, DAS P. Comprehensive Survey of Possible Security Issues on 4G Networks[J]. International Journal of Network Security & Its Applications, 2015, 7(2): 61-69. |
| [8] | WANG Qianran, HUANG Chengbin, WANG Jinhua. Research on Application Strategy of Confidentiality and Integrity Protection Algorithm on 5G Air Interface[C]// IEEE. 2022 International Conference on Networks, Communications and Information Technology (CNCIT). New York:IEEE, 2022: 161-165. |
| [9] | YU Jiaxin. Research on Network Intrusion Detection Algorithm Based on Active Learning[D]. Dalian: Liaoning Normal University, 2019. |
| 于佳鑫. 基于主动学习的网络入侵检测算法研究[D]. 大连: 辽宁师范大学, 2019. | |
| [10] | DU Jiang, LI Xinghui, HUANG Hua. A Study of Man-in-the-Middle Attack Based on SSL Certificate Interaction[C]// IEEE. International Conference on Instrumentation. New York: IEEE Computer Society, 2011: 445-228. |
| [11] | RAJVANSHI N, CHOWDHARY KR. Comparison of SVM and Naive Bayes Text Classification Algorithms Using WEKA[J]. International Journal of Engineering Research and Technology, 2017, 6(9): 141-143. |
| [12] | XUE Jiming. Bayes Classifier Based Network Intrusion Detection[C]// Chinese Society for Electrical Engineering. 2013 Annual Meeting of the Chinese Society of Electrical Engineering. Beijing: Chinese Society for Electrical Engineering, 2013: 833-838. |
| 薛集明. 基于贝叶斯分类的网络入侵检测[C]// 中国电机工程学会. 2013年中国电机工程学会年会论文集. 北京: 中国电机工程学会, 2013: 833-838. | |
| [13] | SUN Pengyu. Application Research on the Multi-Step Attack in Bayesian Network[D]. Changchun: Jilin University, 2011. |
| 孙鹏宇. 贝叶斯网络在多步攻击中应用研究[D]. 长春: 吉林大学, 2011. | |
| [14] | JOACHIMS T. Text Classification on with Support Vector Machine: Learning with Many Relevant Features[C]// Springer. 10th European Conference on Machine Learning (ECML). Berlin:Springer. 1998: 137-142. |
| [15] |
LI Ming, LIU Kefeng. Causality-Based Attribute Weighting via Information Flow and Genetic Algorithm for Naive Bayes Classifier[J]. IEEE Access, 2019, 7: 150630-150641.
doi: 10.1109/ACCESS.2019.2947568 |
| [16] | MARYAM G, WITOLD K. Designing a Neural Network and a Genetic-Algorithm-Based Adaptive Wavelet for Internet Traffic Containing DDoS Attacks[C]// IEEE. 20th International Conference on Cognitive Informatics and Cognitive Computing. New York: IEEE, 2021: 173-180. |
| [17] | WANG Chunfeng, ZHANG Yonghong. Bayesian Network Structure Learning Based on Unconstrained Optimization and Genetic Algorithm[J]. Control and Decision, 2013, 28(4): 618-622. |
| 汪春峰, 张永红. 基于无约束优化和遗传算法的贝叶斯网络结构学习方法[J]. 控制与决策, 2013, 28(4): 618-622. | |
| [18] | SHAIK A, BORGAONKAR R, PARK S, et al. New Vulnerabilities in 4G and 5G Cellular Access Network Protocols: Exposing Device Capabilities[C]// ACM. 12th Conference Security and Privacy in Wireless and Mobile Networks. New York: ACM, 2019: 221-231. |
| [19] | 3GPP. 3GPP TS 36.306 Technical Specification Group Radio Access Network; Evolved Universal Terrestrial Radio Access (E-UTRA); User Equipment (UE) radio access capabilities (Release 17)[EB/OL]. (2022-04-13)[2022-11-14]. https://www.3gpp.org/ftp/Specs/archive/36_series/36.306. |
| [20] |
LEE J, CHUNG W, KIM E, et al. A New Genetic Approach for Structure Learning of Bayesian Networks: Matrix Genetic Algorithm[J]. International Journal of Control, Automation and Systems, 2010, 8(2): 398-407.
doi: 10.1007/s12555-010-0227-3 URL |
| [21] | LIAO Xingfa, CHEN Dezhao, HE Yijun. The Application of Genetic Algorithm to the Construction of Chemical Pattern Classifier[J]. Computers and Applied Chemistry, 2007, 27(5): 593-596. |
| 廖兴发, 陈德钊, 贺益君. 应用遗传算法构建化学模式分类器[J]. 计算机与应用化学, 2007, 27(5): 593-596. |
| [1] | 宋晶, 刁润, 周杰, 戚建淮. 工业控制系统功能安全和信息安全策略优化方法[J]. 信息网络安全, 2022, 22(11): 68-76. |
| [2] | 李彦霖, 蔡满春, 芦天亮, 席荣康. 遗传算法优化CNN的网站指纹攻击方法[J]. 信息网络安全, 2021, 21(9): 59-66. |
| [3] | 赵旭, 黄光球, 崔艳鹏, 王明明. 基于改进选择算子的NIDS多媒体包多线程择危处理模型[J]. 信息网络安全, 2018, 18(10): 45-50. |
| [4] | 郝文江;李思其;丁文纯. 遗传算法在社交网站数据分析中的应用[J]. , 2013, 13(2): 0-0. |
| [5] | 薛琴. BP神经网络在入侵检测系统中的应用研究[J]. , 2011, 11(11): 0-0. |
| [6] | 杨晓勇. 混沌遗传算法在优化问题中的应用[J]. , 2011, 11(10): 0-0. |
| [7] | 赵光耀;邹鹏;韩伟红. 基于遗传算法和LSSVM的网络安全事件发生频率预测[J]. , 2010, (10): 0-0. |
| [8] | 张宏宇;刘宝旭. 基于遗传算法的入侵检测特征选择[J]. , 2008, 8(10): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||