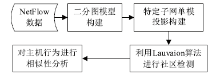
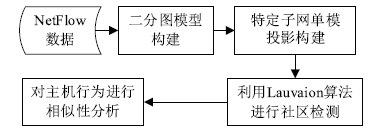
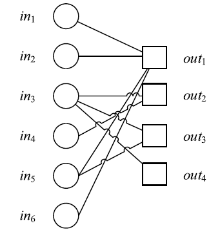
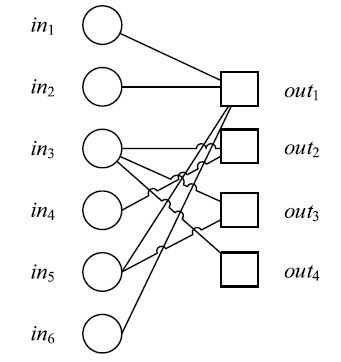
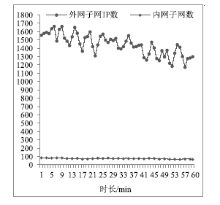
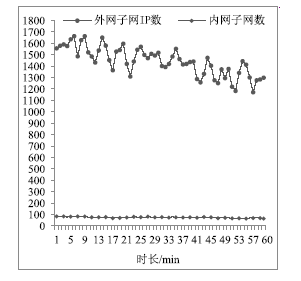
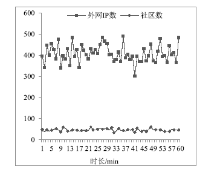
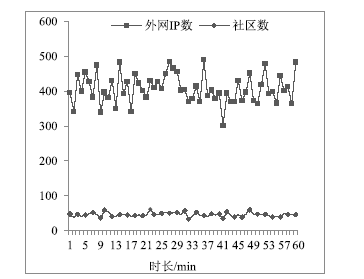
| [1] |
ILIOFOTOU M, GALLAGHER B, ELIASSI-RAD T, et al. Profiling-by-association: a Resilient Traffic Profiling Solution for the Internet Backbone[EB/OL]. , 2017-6-11.
|
| [2] |
KARAGIANNIS T, PAPAGIANNAKI K, TAFT N, et al.Profiling the End Host[C]// ACM. 8th International Conference on Passive and Active Network Measurement, April 5-6, 2007, Louvain-la-Neuve, Belgium. New York: ACM, 2007: 186-196.
|
| [3] |
LI Bingdong, GUNES M H, BEBIS G, et al.A Supervised Machine Learning Approach to Classify Host Roles on Line Using sFlow[C]// ACM. 1st Edition Workshop on High Performance and Programmable Networking, June 18, 2013, New York, USA. New York: ACM, 2013: 53-60.
|
| [4] |
HIMURA Y, FUKUDA K, CHO K, et al.Synoptic Graphlet: Bridging the Gap between Supervised and Unsupervised Profiling of Host-level Network Traffic[J]. IEEE/ACM Transactions on Networking, 2013, 21(4): 1284-1297.
|
| [5] |
DEWAELE G, HIMURA Y, BORGNAT P, et al.Unsupervised Host Behavior Classification from Connection Patterns[J]. International Journal of Network Management, 2010, 20(5): 317-337.
|
| [6] |
ZHANG Zhen, WANG Binqiang, CHEN Hongchang, et al.Internet Traffic Classification Based on Host Connection Graph[J]. Journal of Electronics & Information Technology, 2013, 35(4): 958-964.
|
| [7] |
BLONDEL V D, GUILLAUME J L, LAMBIOTTE R, et al.Fast Unfolding of Communities in Large Networks[J]. Journal of Statistical Mechanics: Theory and Experiment, 2008(10): 155-168.
|
| [8] |
REDDY P K, KITSUREGAWA M, SREEKANTH P, et al.A Graph Based Approach to Extract a Neighborhood Customer Community for Collaborative Filtering[C]// Springer. 2nd International Workshop on Databases in Networked Information Systems, December 16-18, 2002, Aizu, Japan. Heidelberg: Springer, 2002: 188-200.
|
| [9] |
CAI Jun, LIU Waixi. A New Method of Detecting Network Traffic Anomalies[EB/OL]. .
|
| [10] |
CHEN Zhengzhang, HENDRIX W, SAMATOVA N F.Community-based Anomaly Detection in Evolutionary Networks[J]. Journal of Intelligent Information Systems, 2012, 39(1): 59-85.
|
| [11] |
XU Kuai, WANG Feng, GU Lin.Behavior Analysis of Internet Traffic via Bipartite Graphs and One-mode Projections[J]. IEEE/ACM Transactions on Networking (TON), 2014, 22(3): 931-942.
|
| [12] |
XU Kuai, WANG Feng, GU Lin.Network-aware Behavior Clustering of Internet End Hosts[C]// IEEE. 2011 IEEE INFOCOM, April 10-15, 2011, Shanghai, China. New Jersey: IEEE, 2011: 2078-2086.
|
| [13] |
MU Xiangkun, WANG Jinsong, XUE Yufeng, et al.Abnormal Network Traffic Detection Approach Based on Alive Entropy[J]. Journal on Communications, 2013(S2): 51-57.
|
|
穆祥昆,王劲松,薛羽丰,等. 基于活跃熵的网络异常流量检测方法[J]. 通信学报, 2013(S2):51-57.
|
| [14] |
LI Tianfeng, YAO Xin, WANG Jinsong.Cloud Platform Based Real-time Monitoring of the Abnormal Traffic in Massive-scale Network[J]. Netinfo Security, 2014, 14(9): 1-5.
|
|
李天枫,姚欣,王劲松. 大规模网络异常流量实时云监测平台研究[J]. 信息网络安全,2014,14(9):1-5.
|
| [15] |
HUANG Fuhao.Design and Implementation of Microblog Interaction Platform Based on Storm[D]. Guangzhou: Sun Yak-Sen University, 2013.
|
|
黄馥浩. 基于Storm的微博互动平台的设计与实现[D]. 广州:中山大学,2013.
|
| [16] |
GU Wei.Research & Development of Distributed Stream Real-time Computing Framework[D]. Hangzhou: Zhejiang Sci-Tech University, 2013.
|
|
顾伟. 分布式流数据实时计算框架的研究和开发[D]. 杭州:浙江理工大学,2013.
|
| [17] |
YAO Xin, WANG Jinsong.Research of Apache Storm Based Real-time Traffic Monitoring System for Large-scale Network[J]. Journal of Tianjin University of Technology, 2016, 32(6): 25-29.
|
|
姚欣,王劲松. 基于Apache Storm的大规模网络流量实时监控系统研究[J]. 天津理工大学学报,2016,32(6):25-29.
|
 ), 南慧荣1,2,3, 张洪豪1,2,3
), 南慧荣1,2,3, 张洪豪1,2,3
 ), Huirong NAN1,2,3, Honghao ZHANG1,2,3
), Huirong NAN1,2,3, Honghao ZHANG1,2,3