信息网络安全 ›› 2017, Vol. 17 ›› Issue (2): 22-28.doi: 10.3969/j.issn.1671-1122.2017.02.004
一种基于指令虚拟化的代码保护模型
- 1.北方工业大学信息安全实验室,北京100144
2.中国科学院计算技术研究所,北京 100190
A Code Protection Model Based on Instruction Virtualization
Chunlai DU1,2, Dandan KONG1( ), Jingzhong WANG1, Xingbang TAN1
), Jingzhong WANG1, Xingbang TAN1
- 1. Information Security Lab, North China University of Technology, Beijing 100144, China
2. Institute of Computing Technology, Chinese Academy of Science, Beijing 100191, China
摘要:
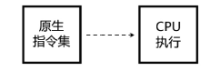
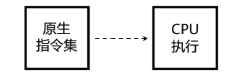
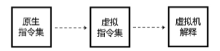
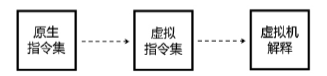
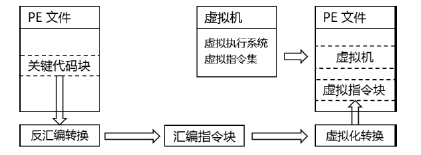
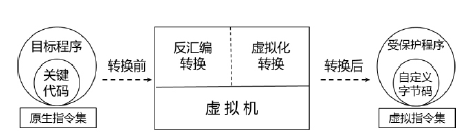
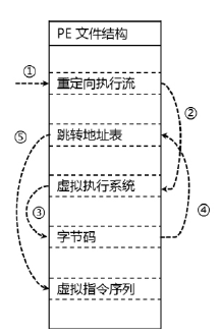
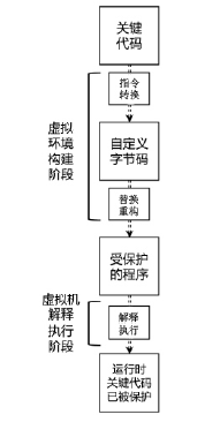
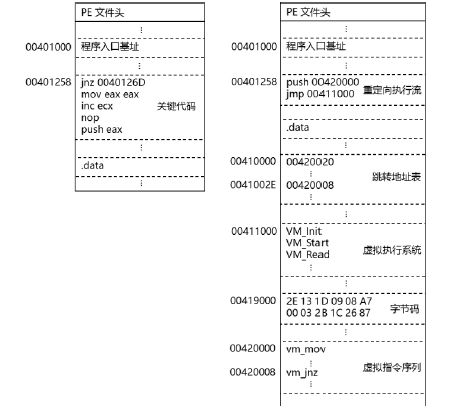
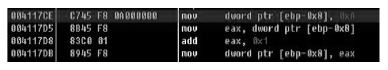
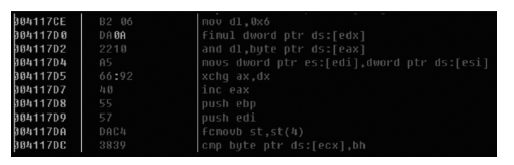
当前软件的破解与盗版不仅给使用者带来巨大安全隐患,同时也给软件开发者造成巨大损失。为了对抗逆向工程对软件进行分析、破解,增加攻击者对代码的逆向分析难度,需要一种有效的方法对代码进行保护。指令虚拟化是使用自定义的虚拟指令集替换原生指令集以达到软件保护目的的技术。针对目前的软件保护问题,文章提出一种基于指令虚拟化的代码防护模型,使用自定义的虚拟指令集替换受保护的原生指令,虚拟重构解释执行原关键代码,剥离原生指令与上下文环境之间的显式关联。实验表明,该模型能够有效对抗逆向分析,达到保护软件代码的目的。
中图分类号: