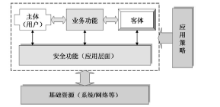
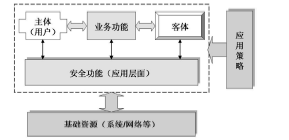
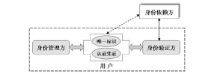
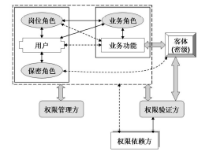
| [1] |
YODER J, BARCALOW J. Architectural Patterns for Enabling Application Security[EB/OL]. https://www.researchgate.net/publication/2428026_Architectural_Patterns_for_Enabling_Application_Security,2016-1-15.
|
| [2] |
ISO/IEC 7498-2. Information Technology - Open Systems Interconnection - Basic Reference Model: Part 2: Security Architecture 7498-2. Information Technology - Open Systems Interconnection - Basic Reference Model: Part 2: Security Architecture[S]. New York : ISO, 1996.
|
| [3] |
胡晓晔. 统一身份认证系统用户信息远程调用与管理[J]. 西安工业大学学报,2015,35(9): 715-719.
|
| [4] |
张明德,郑雪峰,吕述望,等. 应用安全中身份认证建模及推理方法[J]. 小型微型计算机系统, 2012,33(4): 754-758.
|
| [5] |
张明德,郑雪峰,吕述望,等. 身份认证可信度研究[J]. 计算机科学,2011,38(11): 43-47.
|
| [6] |
邢彬,刘吉强,韩臻. 一种可信计算平台完整性度量的新模型[J]. 信息网络安全,2016(6):8-14.
|
| [7] |
RFC 2459. Internet X.509 Public Key Infrastructure Certificate and CRL Profile[S]. New York: ISOC, 1999.
|
| [8] |
王冠,袁华浩. 基于可信根服务器的虚拟TCM密钥管理功能研究[J]. 信息网络安全,2016(4):17-22.
|
| [9] |
ZHANG M D, ZHENG X F, YANG W S,et al.Research on Model of Trust Degrees for PKI[C]//IAS 2009.2009 Fifth International Conference on Information Assurance and Security,August 18-20,2009,Xi'An,China.New York:IEEE,2009: 647-650.
|
| [10] |
张明德,郑雪峰,吕述望. 改进的PKI可信度模型[J]. 小型微型计算机系统,2012,33(2):370-375.
|
| [11] |
ZHANG M D, ZHENG X F, LV S,et al.Improved Approach on Modeling and Reasoning about PKI/WPKI[C]//IEEE.6th IEEE International Conference on Wireless Communications, Networking and Mobile Computing,September 23-25,2010,Chengdu,China.New York:IEEE,2010:1-4.
|
| [12] |
BELL D, LAPADULA L J.Secure Computer Systems: Mathematical Foundations[R]. Bedford: MITRE Corporation, TR2547, 1973.
|
| [13] |
王贵林,卿斯汉,倪情珍,等. 安全计算机系统的Bell-LaPadula形式化模型[J]. 计算机科学,2001,28(12):89-92.
|
| [14] |
BIBA K J.Integrity Considerations for Secure Computer System[R]. Bedford: PSAF Electronic System Division, ESD-76-372, 1977.
|
| [15] |
LI N, BYON J W, BERTINOE. A Critique of the ANSI Standard on Role-Based Access Control[J]. IEEE Security and Privacy, 2007, 5(6): 41-49.
|
| [16] |
KERN A, KUHLMANN M,KUROPKA R,et al.A Meta Model for Authorizations in Application Security Systems and their Integration into RBAC Administration[C]//ACM. 9th ACM symposium on Access control models and technologies,June 2-4, 2004,Yorktown Heights, New York, USA.New York:ACM,2004:87-96.
|
| [17] |
RFC 3281. An Internet Attribute Certificate Profile for AuthorizationFC 3281. An Internet Attribute Certificate Profile for Authorization[S]. New York: ISOC, 2002.
|
| [18] |
李守鹏,孙红波. 信息系统安全模型研究[J]. 电子学报,2003,31(10): 1491-1495.
|
| [19] |
张明德,郑雪峰,蔡翌. 应用安全模型研究[J]. 信息网络安全,2012(8): 121-125.
|