信息网络安全 ›› 2016, Vol. 16 ›› Issue (7): 29-34.doi: 10.3969/j.issn.1671-1122.2016.07.005
主机资源远程控制系统研究与设计
赵俭1, 张畅1, 汶向东2
- 1.解放军信息工程大学,河南郑州 450000
2.陕西省行政学院,陕西西安 710068
Research and Design of Remote Control System of Host Resources
Jian ZHAO1, Chang ZHANG1, Xiangdong WEN2
- 1. The PLA Information Engineering University, Zhengzhou Henan 450000, China
2. Shaanxi Academy of Governance, Xi’an Shaanxi 710068, China
摘要:
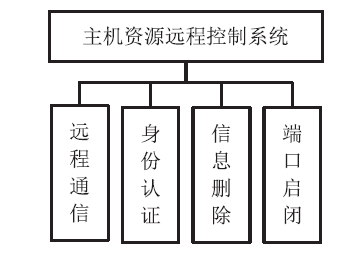
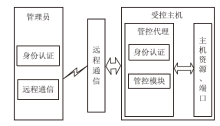
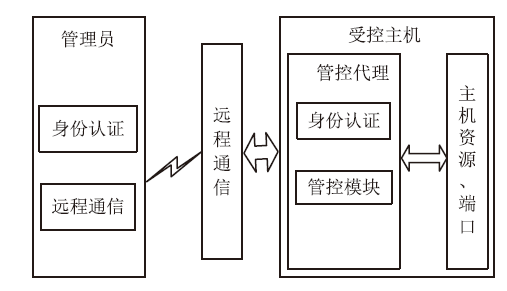
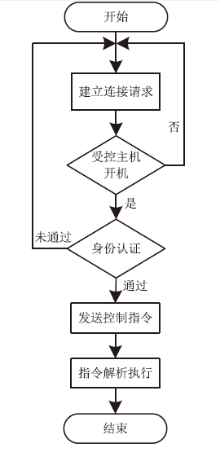
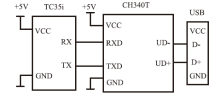
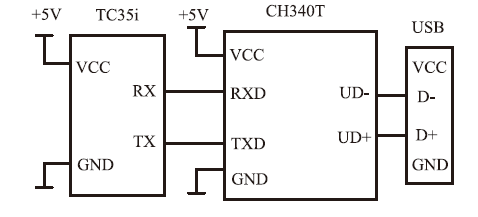
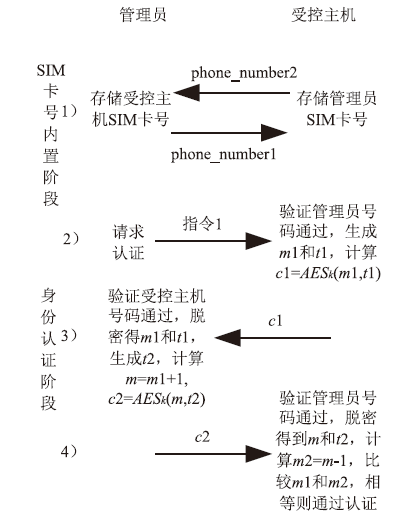
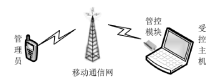
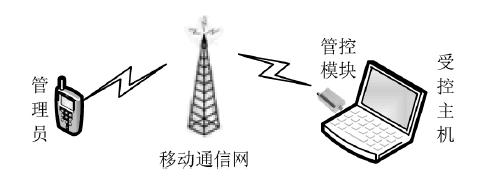
主机资源的安全可控越来越受到人们的重视,尤其是在主机被盗、丢失等情况下,如何进行远程控制确保主机资源的安全是亟待解决的问题。针对这一现实需求,文章在分析了远程控制和主机文件安全删除两个方面的国内外研究现状的基础上,设计实现了一个主机资源远程控制系统,给出系统功能结构和工作流程,详细介绍了基于远程通信模块的硬件平台和管控指令的传输、安全身份认证、主机资源管控等控制软件的设计实现方法,并进行了系统功能测试和分析。该系统基于移动通信模块和主机资源管控代理实现,将通信模块内置于受控主机并通过USB接口与主机进行连接,受控主机运行管控代理软件,管理员的控制指令以短消息的形式发送。为增强系统的安全性,管控代理在接收到控制指令后需向管理员进行身份认证,通过认证后,管控代理执行管控指令,实施如删除敏感文件、关闭主机端口等操作。经实验验证,该系统达到了设计要求,可有效提高主机资源安全管理水平,大大降低主机失控可能造成的安全威胁。
中图分类号: