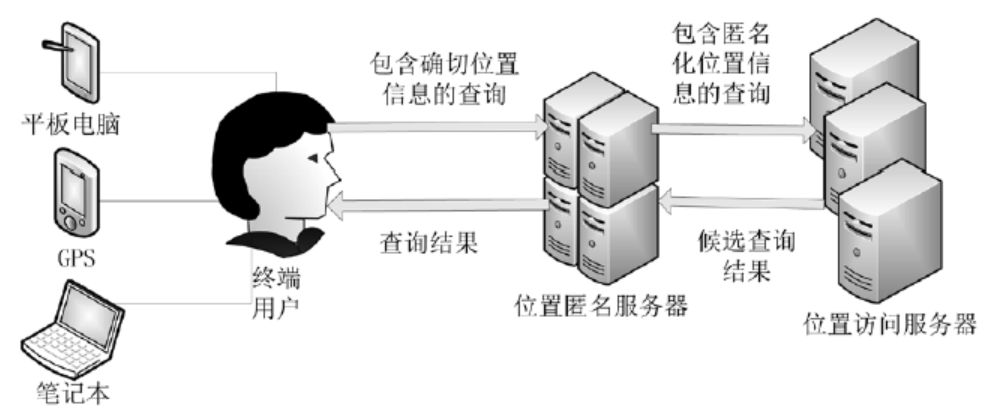
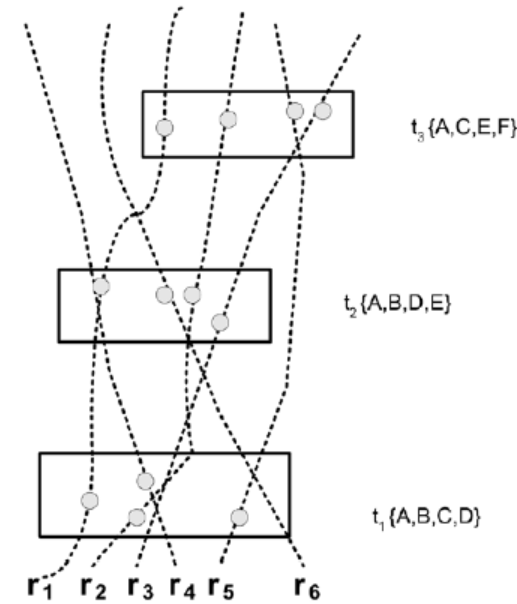
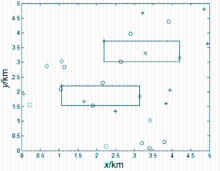
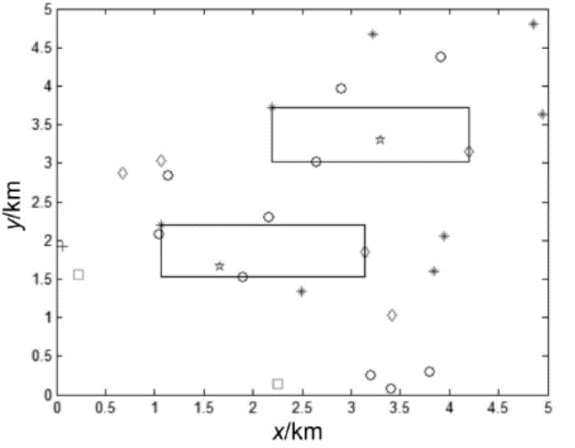
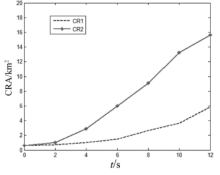
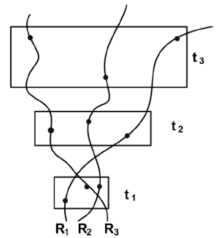
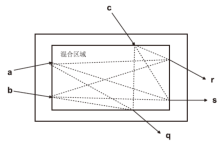
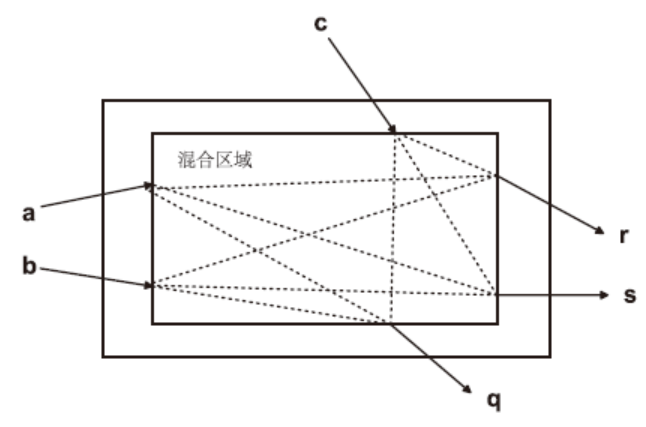
| [1] |
Junglas I A, Watson R T.Location-based services[J]. Communications of the ACM, 2008, 51(3): 65-69.
|
| [2] |
潘晓,肖珍,孟小峰.位置隐私研究综述[J]. 计算机科学与探索,2007,1(3):268-281.
|
| [3] |
Shanker P, Ganapathy V, Iftode L.Privately Querying Location Based Services with SybilQuery[M]. Orlando, USA: ACM Press, 2009.
|
| [4] |
Cornelius C, Kapadia A, Kotz D, et al. AnonySence: Privacy Aware People Centric Sensing[EB/OL]. , 2011-05-23.
|
| [5] |
Yiu M L, Jensen C S, Huang X, et al.Spacetwist: Managing the trade-offs among location privacy, query performance, and query accuracy in mobile services[C]//Data Engineering, 2008. ICDE 2008. IEEE 24th International Conference on. IEEE, 2008: 366-375.
|
| [6] |
Meyerowitz J, Roy Choudhury R.Hiding stars with fireworks: location privacy through camouflage[C]//Proceedings of the 15th annual international conference on Mobile computing and networking. ACM, 2009: 345-356.
|
| [7] |
Gruteser M, Grunwald D.Anonymous Usages of Location-based Services Through Spatial and Temporal Cloaking[M]. New York, USA:ACM Press,2003.
|
| [8] |
Samarati P, Sweeney L.Protecting Privacy When Disclosing Information: k-anonymity and Its Enforcement Through Generalization and Suppression[R]. SRI Computer Science Laboratory, Tech.Rep.:SRI-CLS-98-04, 1998.
|
| [9] |
赵泽茂,李林,张帆,等.基于分散子匿名区域的位置隐私保护方法[J].山东大学学报,2013,48(7):56-61.
|
| [10] |
Bereford A R, Stajano F.Mix Zones: User Privacy in Location-aware Service[M]. Orlando, USA: ACM Press, 2009.
|
| [11] |
Xu T, Cai Ying.Feeling-Based Location Privacy Protection for Location-Based Services[M] . Chicago, USA: ACM Press, 2009.
|
| [12] |
Sweeney L.K-anonymity: a model for protecting privacy[J].International Journal on Uncertainty, Fuzziness and Knowledge-Based Systems, 2002, 10(5): 557-570.
|
| [13] |
Mokbel M F, Chow C Y, Aref W G.The new Casper: Query Processing for Location Services without Compromising Privacy[M]. New York: ACM Press, 2006.
|
| [14] |
Chow C Y, Mokbel M F.Enabling Private Continuous Querues for Revealed User Locations[M]. Berlin, Heidelberg: Springer-Verlag, 2007.
|
| [15] |
Talukder N, Ahamed S I.Preventing Multi-Query Attack in Location-Based Services[M]. New York: ACM Press, 2010.
|
| [16] |
Freudiger J, Yaya M, Felegyhazi M, et al.Mix-zones for location privacy in vehicular networks[C]//Proceedings of the first international workshop on wireless networking for intelligent transportation system (Win-ITS), 2007.
|
| [17] |
ZHOU B, PEI J.The k-anonymity and l-diversity approaches for privacy preservation in social networks against neighborhood attacks[J]. Knowledge and Information Systems, 2011, 28(1): 47-77.
|