信息网络安全 ›› 2015, Vol. 15 ›› Issue (1): 24-31.doi: 10.3969/j.issn.1671-1122.2015.01.005
一种路由设备服务可信属性定义方法与可信路由协议设计
- 清华大学计算机科学与技术系,北京100084
ZHAO Yu-dong( ), XU Ke, ZHU Liang
), XU Ke, ZHU Liang
- Department of Computer Science and Technology, Tsinghua University, Beijing 100084, China
摘要:
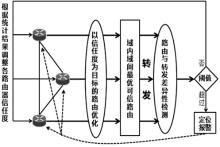
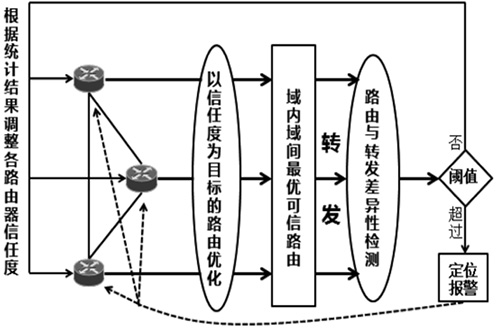
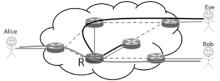
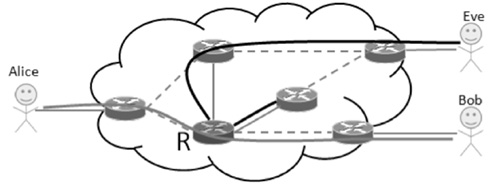
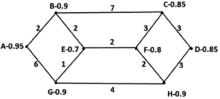
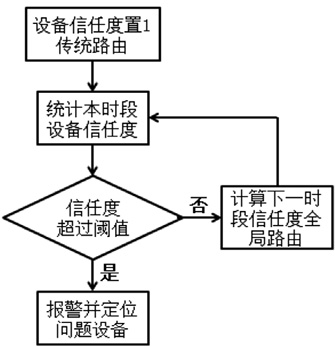
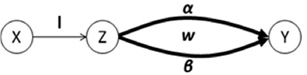
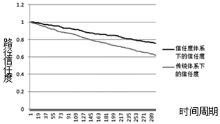
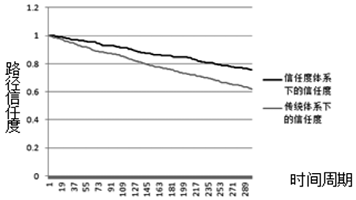
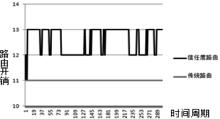
受主观意志和研发能力影响,路由设备生产商难以严格按其对用户承诺提供路由产品,导致设备及其组件中可能存在漏洞与后门,这将给核心网络带来严重的安全威胁。文章为此提出一种路由设备服务可信属性的定义和动态测量方法,并设计相应的可信路由协议,以优化核心网络服务可信属性,促进网络信息传输安全。文章首先分析核心网络范围内网络服务可信属性与信息传输安全的关系,论证通过量化路由设备服务可信属性,同时基于该属性设计可信路由协议,可实现设备资源受限条件下信息传输安全效益的最大化。其次引入“信任度”的概念定义路由设备服务可信属性,在设计基于设备信任度和当前互联网在用路由协议的域内域间可信路由协议的基础上,理论证明上述协议下最优可信路由的存在。接着提出一种基于分组可信路由与实际转发路径一致性检测的路由设备信任度动态量化技术。最后构造可信路由网络模型,检测可信路由协议的安全效益及其对传统路由开销的影响,结果显示可信路由可显著增加信息传输的安全性,其带来的传统路由开销的增长及路由变化的频率与幅度可容忍。
中图分类号: