信息网络安全 ›› 2025, Vol. 25 ›› Issue (8): 1196-1207.doi: 10.3969/j.issn.1671-1122.2025.08.002
基于命名空间与文件系统代理的容器安全框架研究
路新喜1, 郭建伟2, 苑立娟3, 柳燕4, 徐彬彬4, 刘杨5( )
)
- 1.北京航空航天大学软件学院,北京 100191
2.北京市科学技术研究院,北京 100089
3.保定学院,保定 071000
4.北京智网数科技术有限公司,北京 102200
5.北京航空航天大学自动化科学与电气工程学院,北京 100191
-
收稿日期:2025-06-03出版日期:2025-08-10发布日期:2025-09-09 -
通讯作者:刘杨 E-mail:ylbuaa@163.com -
作者简介:路新喜(1978—),男,北京,副教授,博士,主要研究方向为智能软件和人工智能|郭建伟(1983—),男,北京,助理研究员,本科,主要研究方向为信息安全和系统建设|苑立娟(1980—),女,河北,高级实验师,硕士,主要研究方向为计算机应用|柳燕(1982—),女,江苏,高级经济师,硕士,主要研究方向为油气能源领域数字化与智能化|徐彬彬(1981—),女,辽宁,高级工程师,硕士,主要研究方向为油气能源领域数字化与智能化|刘杨(1983—),女,北京,副教授,博士,主要研究方向为多自主体系统、智能控制和鲁棒控制 -
基金资助:国家自然科学基金(62073020);保定市科技计划(2311ZN003)
Research on Container Security Framework Based on Namespace and Filesystem Proxy
LU Xinxi1, GUO Jianwei2, YUAN Lijuan3, LIU Yan4, XU Binbin4, LIU Yang5( )
)
- 1. School of Software, Beihang University, Beijing 100191, China
2. Beijing Academy of Science and Technology, Beijing 100089, China
3. Baoding University, Baoding 071000, China
4. Pipechina Digital Co., Ltd., Beijing 102200, China
5. School of Automation Science and Electrical Engineering, Beihang University, Beijing 100191, China
-
Received:2025-06-03Online:2025-08-10Published:2025-09-09
摘要:
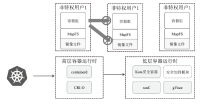
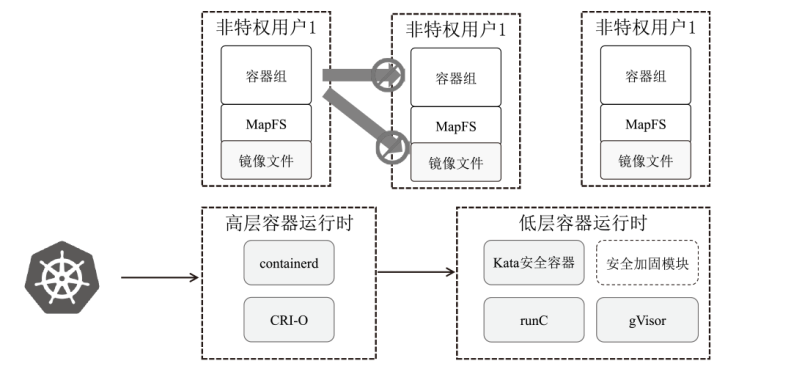
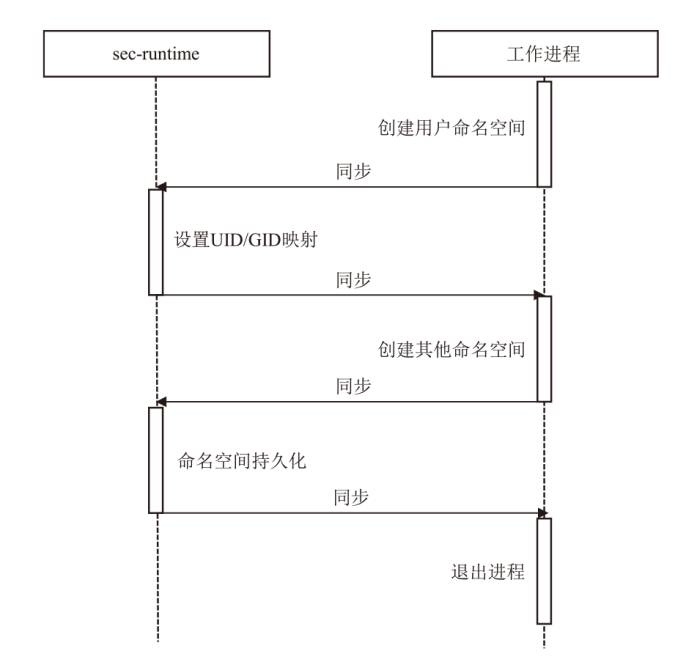
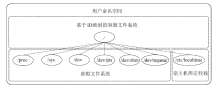
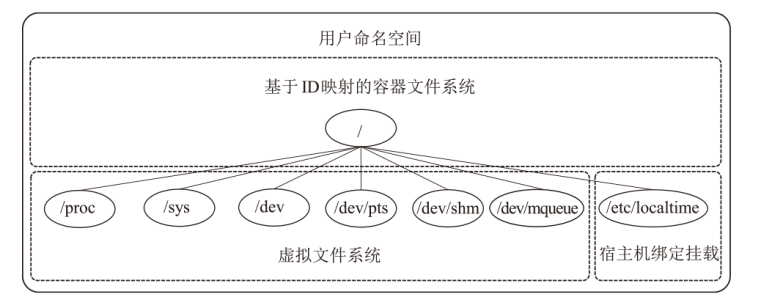
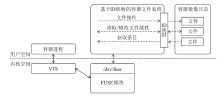
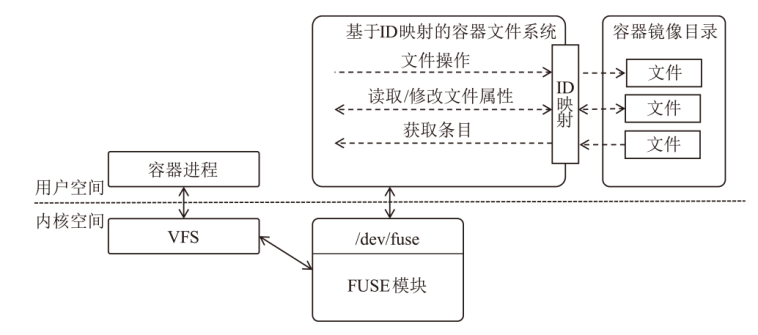
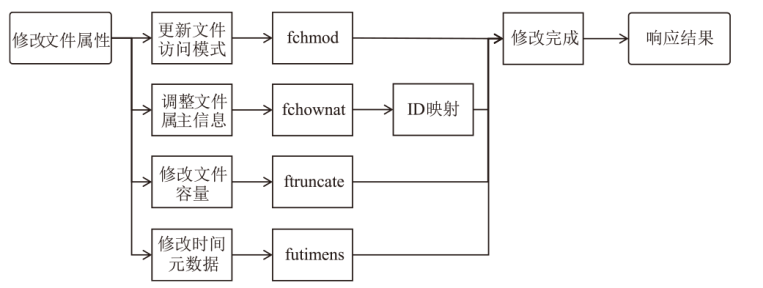
针对现有容器云平台在用户身份隔离与文件系统权限控制方面存在的安全缺陷,文章提出一种基于用户命名空间与用户态文件系统代理机制的容器安全加固框架SecPod。该框架以容器运行时为对象,采用容器UID/GID动态映射机制实现容器间身份隔离,并设计容器文件系统代理模块以虚拟化容器视图,对文件访问操作进行精细化权限管理。实验结果表明,SecPod在不影响容器兼容性的前提下,能够有效阻止多种典型的逃逸与提权攻击,显著提升了容器的隔离强度。
中图分类号:
引用本文
路新喜, 郭建伟, 苑立娟, 柳燕, 徐彬彬, 刘杨. 基于命名空间与文件系统代理的容器安全框架研究[J]. 信息网络安全, 2025, 25(8): 1196-1207.
LU Xinxi, GUO Jianwei, YUAN Lijuan, LIU Yan, XU Binbin, LIU Yang. Research on Container Security Framework Based on Namespace and Filesystem Proxy[J]. Netinfo Security, 2025, 25(8): 1196-1207.
表1
SecPod与主流容器安全方案对比结果
| 维度 | SecPod | 传统容器运行时(userns-remap) | gVisor | Kata Containers |
|---|---|---|---|---|
| UID/GID映射策略 | 每个容器独立UID/GID映射区间 | 多容器共享统一映射区间 | 由用户态内核管理,不直接依赖宿主UID映射 | 用户身份存在于独立的Guest OS中,与宿主机完全隔离 |
| 文件访问权限问题 | 通过FUSE实现虚拟化权限视图 | 需要通过chown破坏元数据 | 文件访问由用户态内核代理,虚拟化访问 | 通过Guest内核与虚拟化I/O 访问 |
| 隔离粒度 | 完全分离,最小权限 隔离 | 容器组间存在身份重叠 | 强(系统调用层面隔离) | 非常强(硬件层面隔离) |
| 宿主兼容性与 安全性 | 高(不需要修改宿主 文件) | 有影响(需修改宿主文件) | 安全性增强,但有性能开销和部分系统调用兼容性限制 | 安全性最强,但有额外启动延迟和资源开销 |
表3
漏洞利用情况
| 漏洞编号 | 漏洞类型 | 加固容器是否 可利用 | 原因分析/防护机制 |
|---|---|---|---|
| CVE-2019-5736 | runC执行劫持 | 否 | 用户命名空间阻断/proc/self/exe写入 |
| CVE-2022-0492 | Cgroup release_agent | 否 | 无权限写入cgroup配置目录 |
| CVE-2021-3156 | sudoedit提权 | 否 | 宿主sudoers.so无法加载 |
| CVE-2021-3493 | OverlayFS权限绕过 | 否 | 提权仅限在用户命名空间中,无法影响宿主机 |
| CVE-2020-14386 | AF_PACKET越界写 | 否 | 用户命名空间内无法执行特权操作 |
| CVE-2021-3490 | eBPF提权 | 否 | 用户命名空间限制了bpf()系统调用的权限,无法实现宿主级别提权 |
| [1] | JARKAS O, KO R, DONG Naipeng, et al. A Container Security Survey: Exploits, Attacks, and Defenses[J]. ACM Computing Surveys, 2025, 57(7): 1-36. |
| [2] | WANG Yazhe, REN Lei, FENG Dengguo, et al. Security Enhancements for New-Generation PLC of the Industrial Internet Integrating Sensing, Computing, Control and Intelligence: Trends and Perspectives[J]. Chinese Journal of Computers, 2025, 48(3): 738-762. |
| 王雅哲, 任磊, 冯登国, 等. 面向感算控智一体化融合的工业互联网新型PLC安全增强:趋势与展望[J]. 计算机学报, 2025, 48(3): 738-762. | |
| [3] | BIAN Manlin, WANG Liming. Analysis and Research on Vulnerability of Docker Container Isolation in Cloud Environment[J]. Netinfo Security, 2020, 20(7): 85-95. |
| 边曼琳, 王利明. 云环境下Docker容器隔离脆弱性分析与研究[J]. 信息网络安全, 2020, 20(7): 85-95. | |
| [4] | BARNAWI N, AITOOQ R, ALMUKAYNIZI M. Mitigating Container Escape Threats through Effective Countermeasures: A Survey[EB/OL]. (2024-08-19)[2025-02-15]. https://avestia.com/EECSS2024_Proceedings/files/paper/CIST/CIST_164.pdf. |
| [5] | NADGOWDA S, SUNEJA S, ISCI C. RECap: Run-Escape Capsule for on Demand Managed Service Delivery in the Cloud[EB/OL]. [2025-02-15]. https://www.usenix.org/system/files/conference/hotcloud18/hotcloud18-paper-nadgowda.pdf. |
| [6] | RunC-CVE-2019-5736[EB/OL]. [2025-02-15]. ttps://www.doc88.com/p-08973989221016.html. |
| [7] | SULTAN S, AHMAD I, DIMITRIOU T. Container Security: Issues, Challenges, and the Road Ahead[J]. IEEE Access, 2019, 7: 52976-52996. |
| [8] | ABBAS M, KHAN S, MONUM A, et al. PACED: Provenance-Based Automated Container Escape Detection[C]// IEEE. 2022 IEEE International Conference on Cloud Engineering. New York: IEEE, 2022: 261-272. |
| [9] | DEVI P V S, CHAKKARAVARTHY S S, KHAN M K. Container Security: Precaution Levels, Mitigation Strategies, and Research Perspectives[EB/OL]. (2023-09-22)[2025-02-15]. https://doi.org/10.1016/j.cose.2023.103490. |
| [10] | LEE K, KIM J, KWON I H, et al. Impact of Secure Container Runtimes on File I/O Performance in Edge Computing[EB/OL]. (2023-12-18)[2025-02-15]. https://doi.org/10.3390/app132413329. |
| [11] | COMBE T, MARTIN A, DI PO R. To Docker or not to Docker: A Security Perspective[J]. IEEE Cloud Computing, 2016, 3(5): 54-62. |
| [12] | PONTES R, CARVALHO P, MAIA F, et al. SafeFS: A Modular Architecture for Secure User-Space File Systems: One FUSE to Rule them All[EB/OL]. (2017-05-22)[2025-02-15]. https://dl.acm.org/doi/abs/10.1145/3078468.3078480. |
| [13] | REEVES M. Investigating Escape Vulnerabilities in Container Runtimes[D]. West Lafayette: Purdue University, 2021. |
| [14] | LI Yun, HUANG Chenlin, YUAN Lu, et al. ASPGen: An Automatic Security Policy Generating Framework for AppArmor[C]// IEEE. 2020 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking. New York: IEEE, 2020: 392-400. |
| [15] | BAKER S A, MOHAMMED H H, ALSAIF O I. Docker Container Security Analysis Based on Virtualization Technologies[EB/OL]. [2025-02-15]. https://www.nstl.gov.cn/paper_detail.html?id=62263f7377f8741360ca99b0009570ac. |
| [16] | LI Dong, YU Junqing, WEN Ruibin, et al. Endogenous Security Methods for Container Cloud Based on IPv6[J]. Netinfo Security, 2023, 23(12): 21-28. |
| 李冬, 于俊清, 文瑞彬, 等. 基于IPv6的容器云内生安全机制[J]. 信息网络安全, 2023, 23(12): 21-28. | |
| [17] | MINNA F, MASSACCI F. SoK: Run-Time Security for Cloud Microservices. Are We There Yet?[EB/OL]. (2023-01-24)[2025-02-15]. https://doi.org/10.1016/j.cose.2023.103119. |
| [18] | YOUNG E G, ZHU Pengfei, CARAZA-HARTER T, et al. The True Cost of Containing: A Gvisor Case Study[EB/OL]. [2025-02-15]. https://www.xueshufan.com/publication/2965859899. |
| [19] | AGACHE A, BROOKER M, IORDACHE A, et al. Firecracker: Lightweight Virtualization for Serverless Applications[EB/OL]. [2025-02-15]. https://www.xueshufan.com/publication/3010457348. |
| [20] | SOLTESZ S, PÖTZL H, FIUCZYNSKI M E, et al. Container-Based Operating System Virtualization[J]. ACM SIGOPS Operating Systems Review, 2007, 41(3): 275-287. |
| [21] | HOF A V, NIEH J. BlackBox: A Container Security Monitor for Protecting Containers on Untrusted Operating Systems[EB/OL]. (2022-07-11)[2025-02-15]. https://www.cs.columbia.edu/-nieh/pubs/osdi2022_blackbox.pdf. |
| [22] | HE Yi, GUO Ziyi, XING Yunlong, et al. Cross Container Attacks: The Bewildered eBPF on Clouds[EB/OL]. [2025-02-15].https://www.usenix.org/conference/usenixsecurity23/presentation/he. |
| [23] | SUN Yuqiong, SAFFORD D, ZOHAR M, et al. Security Namespace: Making Linux Security Frameworks Available to Containers[C]// USENIX. The 27th USENIX Security Symposium. Berkeley: USENIX, 2018: 1423-1439. |
| [24] | BORATE I, R K. Sandboxing in Linux: From Smartphone to Cloud[J]. International Journal of Computer Applications, 2016, 148(8): 1-8. |
| [25] | KAISER S, HAQ M S, TOSUN A Ş, et al. Container Technologies for ARM Architecture: A Comprehensive Survey of the State-of-the-Art[J]. IEEE Access, 2022, 10: 84853-84881. |
| [26] | HAYDEN M, CARBONE R. Securing Linux Containers[EB/OL]. (2015-07-26)[2025-02-15]. https://major.io/wp-content/uploads/2015/08/Securing-Linux-Containers-GCUX-Gold-Paper-Major-Hayden.pdf. |
| [27] | LI Zhi, LIU Weijie, WANG Xiaofeng, et al. Lost along the Way: Understanding and Mitigating Path-Misresolution Threats to Container Isolation[C]// ACM. The 2023 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2023: 3063-3077. |
| [1] | 黄轲, 李璇, 周庆飞, 尚科彤, 秦宇. 基于eBPF的容器运行时可信监控方案[J]. 信息网络安全, 2025, 25(2): 306-326. |
| [2] | 夏懿航, 张志龙, 王木子, 陈力波. 基于依赖关系的容器供应链脆弱性检测方法[J]. 信息网络安全, 2023, 23(2): 76-84. |
| [3] | 吴圣麟, 刘汪根, 严明, 吴杰. 基于无监督系统调用规则生成的容器云实时异常检测系统[J]. 信息网络安全, 2023, 23(12): 91-102. |
| [4] | 边曼琳, 王利明. 云环境下Docker容器隔离脆弱性分析与研究[J]. 信息网络安全, 2020, 20(7): 85-95. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||