信息网络安全 ›› 2025, Vol. 25 ›› Issue (5): 828-839.doi: 10.3969/j.issn.1671-1122.2025.05.014
基于小波分解与动态密集空洞卷积的双分支神经网络水印算法
李敬有1,2, 席晓天1,2( ), 魏荣乐1,2, 张光妲1,2
), 魏荣乐1,2, 张光妲1,2
- 1.齐齐哈尔大学计算机与控制工程学院,齐齐哈尔 161006
2.黑龙江省大数据网络安全检测分析重点实验室,齐齐哈尔 161006
-
收稿日期:2025-02-25出版日期:2025-05-10发布日期:2025-06-10 -
通讯作者:席晓天450839276@qq.com -
作者简介:李敬有(1974—),男,吉林,教授,硕士,CCF会员,主要研究方向为信息安全|席晓天(1997—),男,江苏,硕士研究生,主要研究方向为数字水印技术|魏荣乐(1999—),男,湖北,硕士研究生,主要研究方向为数字水印技术|张光妲(1975—),女,黑龙江,副教授,硕士,主要研究方向为网络与信息安全 -
基金资助:国家自然科学基金(42271409);黑龙江省省属高等学校基本科研业务费(145409441)
Double Branch Neural Network Watermarking Algorithm Based on Wavelet Decomposition and Dynamic Dense Dilated Convolution
LI Jingyou1,2, XI Xiaotian1,2( ), WEI Rongle1,2, ZHANG Guangda1,2
), WEI Rongle1,2, ZHANG Guangda1,2
- 1. School of Computer and Control Engineering, Qiqihar University, Qiqihar 161006, China
2. Heilongjiang Key Laboratory of Big Data Network Security Detection and Analysis, Qiqihar 161006, China
-
Received:2025-02-25Online:2025-05-10Published:2025-06-10
摘要:
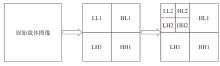
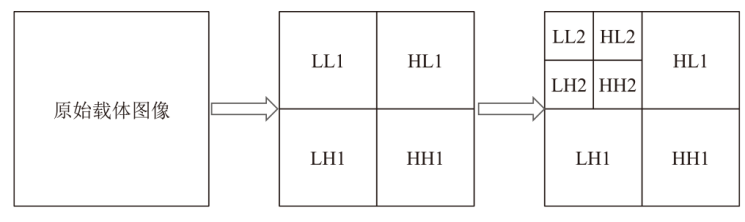
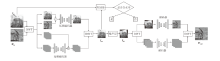
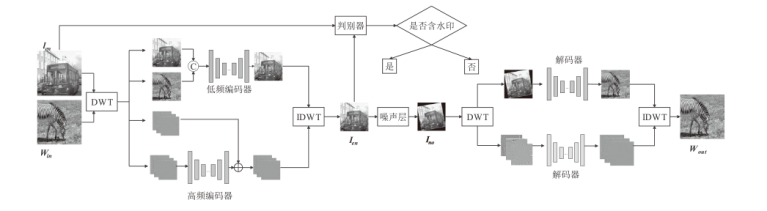
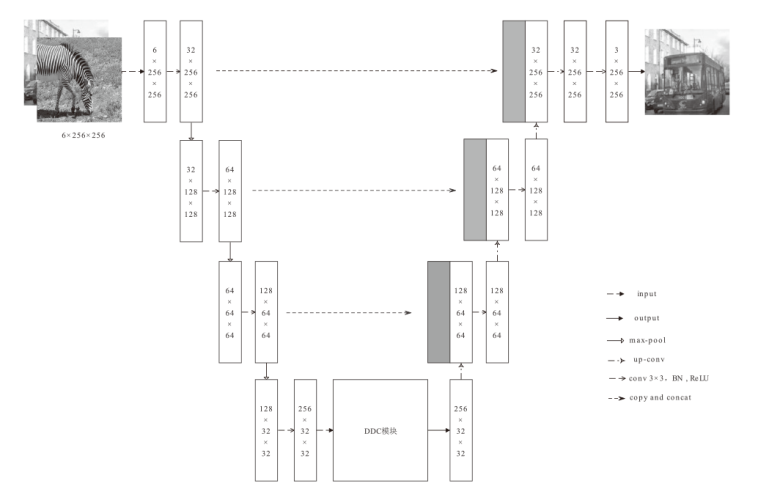
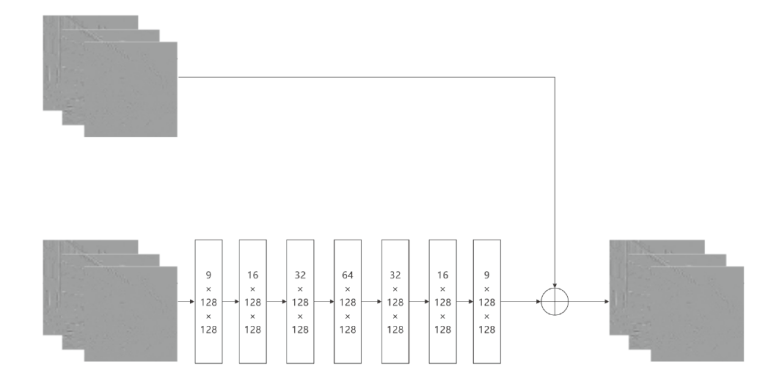
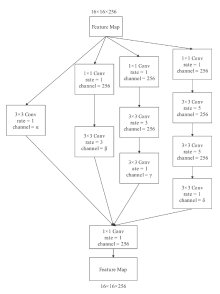
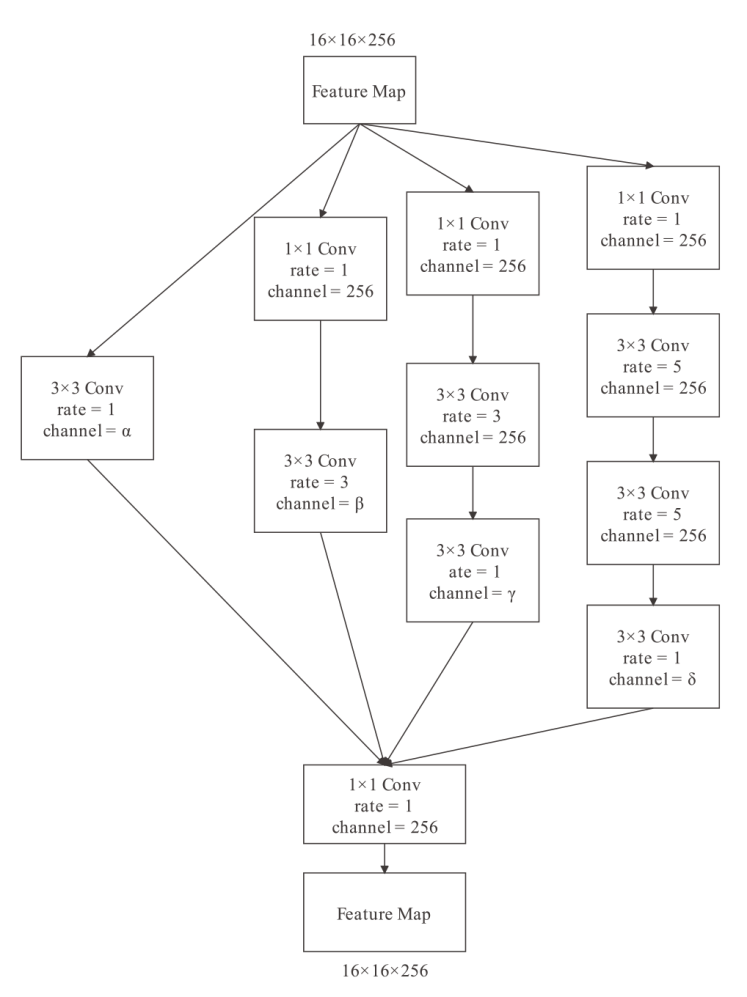
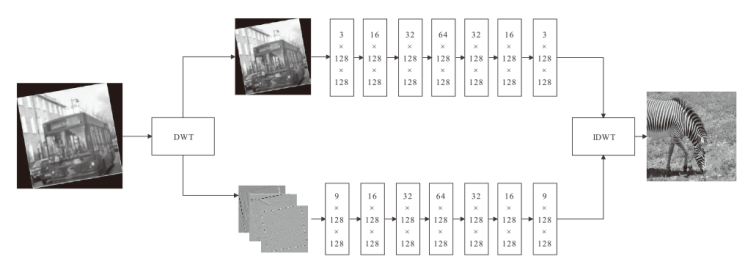
基于深度学习的数字水印算法主要倾向于向载体图像的中高频区域嵌入水印信息,只使用卷积神经网络将水印信息映射到载体图像的特征空间中,忽略了频域算法的作用。文章提出一种基于小波分解与动态密集空洞卷积的双分支神经网络水印算法,通过使用小波分解,更好地引导水印信息的嵌入和提取。该算法运用离散小波变换处理载体图像与水印图像,将其分解为高频信息和低频信息,再使用神经网络进行针对性学习,使用动态密集空洞卷积在减少神经网络层数的情况下,扩大感受野,增强捕捉全局信息的能力,也能避免使用过多的池化层影响重建图像的质量。实验表明,该算法拥有良好的不可见性和鲁棒性。
中图分类号:
引用本文
李敬有, 席晓天, 魏荣乐, 张光妲. 基于小波分解与动态密集空洞卷积的双分支神经网络水印算法[J]. 信息网络安全, 2025, 25(5): 828-839.
LI Jingyou, XI Xiaotian, WEI Rongle, ZHANG Guangda. Double Branch Neural Network Watermarking Algorithm Based on Wavelet Decomposition and Dynamic Dense Dilated Convolution[J]. Netinfo Security, 2025, 25(5): 828-839.
表6
鲁棒性实验数据
| 噪声类型 | ||||
|---|---|---|---|---|
| PSNR | SSIM | PSNR | SSIM | |
| 像素替换(p=0.4) | 38.69 | 0.9802 | 36.41 | 0.9785 |
| 高斯滤波(σ=10) | 40.28 | 0.9869 | 37.16 | 0.9867 |
| JPEG(QF=60) | 39.44 | 0.9712 | 37.11 | 0.9806 |
| 旋转(3°) | 38.71 | 0.9770 | 36.87 | 0.9761 |
| 平移(5像素) | 39.16 | 0.9795 | 35.84 | 0.9738 |
| 椒盐噪声(s=1%) | 40.10 | 0.9900 | 36.76 | 0.9904 |
| 中值滤波(ω=3) | 40.24 | 0.9847 | 37.08 | 0.9814 |
| 组合噪声 | 36.03 | 0.9662 | 32.57 | 0.9640 |
表8
鲁棒性对比实验
| 噪声类型 | 文献[18]算法 | 文献[19]算法 | 文献[20]算法 | 本文算法 | ||||
|---|---|---|---|---|---|---|---|---|
| PSNR | SSIM | PSNR | SSIM | PSNR | SSIM | PSNR | SSIM | |
| 像素替换(p=0.4) | 36.02 | 0.9719 | 36.37 | 0.9757 | 36.02 | 0.9720 | 36.41 | 0.9785 |
| 高斯滤波(σ=10) | 36.60 | 0.9724 | 36.69 | 0.9790 | 36.63 | 0.9725 | 37.16 | 0.9867 |
| JPEG(QF=60) | 35.10 | 0.9779 | 36.09 | 0.9800 | 36.23 | 0.9807 | 37.11 | 0.9806 |
| 旋转(3°) | 35.71 | 0.9741 | 35.61 | 0.9736 | 35.74 | 0.9749 | 36.87 | 0.9761 |
| 平移 (5像素) | 35.76 | 0.9726 | 35.20 | 0.9703 | 36.77 | 0.9731 | 35.84 | 0.9738 |
| 椒盐噪声(s=1%) | 36.41 | 0.9790 | 36.53 | 0.9788 | 36.44 | 0.9791 | 36.76 | 0.9804 |
| 中值滤波(ω=3) | 36.42 | 0.9758 | 36.55 | 0.9760 | 36.49 | 0.9757 | 37.08 | 0.9814 |
| 组合噪声 | 30.88 | 0.9557 | 30.82 | 0.9561 | 30.90 | 0.9589 | 32.57 | 0.9640 |
表10
鲁棒性消融实验1
| 噪声类型 | 变体1 | 变体2 | 本文算法 | |||
|---|---|---|---|---|---|---|
| PSNR | SSIM | PSNR | SSIM | PSNR | SSIM | |
| 像素替换(p=0.4) | 35.40 | 0.9779 | 35.19 | 0.9779 | 36.41 | 0.9785 |
| 高斯滤波(σ=10) | 35.81 | 0.9861 | 35.70 | 0.9861 | 37.16 | 0.9867 |
| JPEG(QF=60) | 35.76 | 0.9795 | 35.71 | 0.9804 | 37.11 | 0.9806 |
| 旋转(3°) | 35.48 | 0.9762 | 35.44 | 0.9757 | 36.87 | 0.9761 |
| 平移 (5像素) | 35.90 | 0.9739 | 35.87 | 0.9738 | 35.84 | 0.9738 |
| 椒盐噪声(s=1%) | 36.44 | 0.9904 | 36.45 | 0.9900 | 36.76 | 0.9904 |
| 中值滤波(ω=3) | 36.15 | 0.9813 | 36.63 | 0.9811 | 37.08 | 0.9814 |
| 组合噪声 | 31.06 | 0.9638 | 30.71 | 0.9614 | 32.57 | 0.9640 |
表11
鲁棒性消融实验2
| 噪声类型 | 变体3 | 变体4 | 本文算法 | |||
|---|---|---|---|---|---|---|
| PSNR | SSIM | PSNR | SSIM | PSNR | SSIM | |
| 像素替换(p=0.4) | 36.39 | 0.9785 | 36.41 | 0.9785 | 36.41 | 0.9785 |
| 高斯滤波(σ=10) | 36.83 | 0.9864 | 37.16 | 0.9867 | 37.16 | 0.9867 |
| JPEG(QF=60) | 37.10 | 0.9706 | 37.11 | 0.9806 | 37.11 | 0.9806 |
| 旋转(3°) | 36.61 | 0.9759 | 36.87 | 0.9761 | 36.87 | 0.9761 |
| 平移 (5像素) | 35.82 | 0.9738 | 35.83 | 0.9738 | 35.84 | 0.9738 |
| 椒盐噪声(s=1%) | 34.29 | 0.9860 | 36.76 | 0.9904 | 36.76 | 0.9904 |
| 中值滤波(ω=3) | 36.20 | 0.9810 | 37.10 | 0.9814 | 37.08 | 0.9814 |
| 组合噪声 | 31.49 | 0.9638 | 32.58 | 0.9640 | 32.57 | 0.9640 |
表12
泛化能力消融实验
| 算法 | ||||
|---|---|---|---|---|
| PSNR | SSIM | PSNR | SSIM | |
| 变体1 | 38.24(↓0.82) | 0.9871(↓0.0002) | 34.59(↓0.89) | 0.9860(↓0.0007) |
| 变体2 | 40.58(↓0.79) | 0.9904(↓0.0002) | 38.67(↓0.80) | 0.9887(↓0.0005) |
| 变体3 | 39.26(↓2.26) | 0.9972(↓0.0037) | 36.82(↓2.31) | 0.9824(↓0.0046) |
| 变体4 | 40.44(↓0.85) | 0.9906(↓0.0002) | 38.63(↓0.86) | 0.9884(↓0.0006) |
| 本文算法 | 40.48(↓0.86) | 0.9904(↓0.0003) | 39.49(↓0.89) | 0.9893(↓0.0007) |
| [1] | CHENG Bin, ZHANG Bo. Application of Robust Digital Watermarking Technology in Image Copyright Disputes[EB/OL]. (2021-04-01)[2025-02-20]. https://dx.doi.org/10.1088/1742-6596/1883/1/012124. |
| [2] | SOUNDRAPANDIYAN R, RAJENDIRAN K, GURUNATHAN A, et al. Analysis of DWT-DCT Watermarking Algorithm on Digital Medical Imaging[EB/OL]. [2025-02-20]. https://pubmed.ncbi.nlm.nih.gov/38162418/. |
| [3] | CAO Fang, GUO Daidou, WANG Tianjun, et al. Universal Screen-Shooting Robust Image Watermarking with Channel-Attention in DCT Domain[EB/OL]. (2023-10-06)[2025-02-20]. https://www.sciencedirect.com/science/article/abs/pii/S0957417423025642?via%3Dihub. |
| [4] | BALUJA S. Hiding Images in Plain Sight: Deep Steganography[J]. Advances in Neural Information Processing Systems, 2017, 30: 2066-2076. |
| [5] | ZHU Jiren, KAPLAN R, JOHNSON J, et al. HIDDEN: Hiding Data with Deep Networks[C]// Springer. Proceedings of the European Conference on Computer Vision (ECCV). Heidelberg: Springer, 2018: 657-672. |
| [6] | TANCIK M, MILDENHALL B, NG R. StegaStamp: Invisible Hyperlinks in Physical Photographs[C]// IEEE. 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2020: 2117-2126. |
| [7] | ZHU Liuhao, ZHAO Yi, FANG Yixiang, et al. A Novel Robust Digital Image Watermarking Scheme Based on Attention U-Net++ Structure[J]. The Visual Computer, 2024, 40(12): 8791-8807. |
| [8] | ZHANG Chaoning, BENZ P, KARJAUV A, et al. UDH: Universal Deep Hiding for Steganography, Watermarking, and Light Field Messaging[J]. Advances in Neural Information Processing Systems, 2020, 33: 10223-10234. |
| [9] | JING Junpeng, DENG Xin, XU Mai, et al. HiNet: Deep Image Hiding by Invertible Network[C]// IEEE. 2021 IEEE/CVF International Conference on Computer Vision (ICCV). New York: IEEE, 2021: 4713-4722. |
| [10] | GIRI K J, QUADRI S M K, BASHIR R, et al. DWT Based Color Image Watermarking: A Review[J]. Multimedia Tools and Applications, 2020, 79(43): 32881-32895. |
| [11] | CHANG Shiyu, ZHANG Yang, HAN Wei, et al. Dilated Recurrent Neural Networks[J]. Advances in Neural Information Processing Systems, 2017, 30: 76-86. |
| [12] | YU F, KOLTUN V. Multi-Scale Context Aggregation by Dilated Convolutions[EB/OL]. (2016-04-30)[2025-02-20]. https://arxiv.org/abs/1511.07122. |
| [13] | WANG Panqu, CHEN Pengfei, YUAN Ye, et al. Understanding Convolution for Semantic Segmentation[C]// IEEE. 2018 IEEE Winter Conference on Applications of Computer Vision (WACV). New York: IEEE, 2018: 1451-1460. |
| [14] | SZEGEDY C, LIU Wei, JIA Yangqing, et al. Going Deeper with Convolutions[C]// IEEE. 2015 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2015: 1-9. |
| [15] | HAN Yizeng, HUANG Gao, SONG Shiji, et al. Dynamic Neural Networks: A Survey[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2021, 44(11): 7436-7456. |
| [16] | ALMOHAMMAD A, GHINEA G. Stego Image Quality and the Reliability of PSNR[C]// IEEE. 2010 2nd International Conference on Image Processing Theory, Tools and Applications. New York: IEEE, 2010: 215-220. |
| [17] |
WANG Zhou, BOVIK A C, SHEIKH H R, et al. Image Quality Assessment: From Error Visibility to Structural Similarity[J]. IEEE Transactions on Image Processing, 2004, 13(4): 600-612.
doi: 10.1109/tip.2003.819861 pmid: 15376593 |
| [18] | LUO Xiyang, ZHAN Ruohan, CHANG Huiwen, et al. Distortion Agnostic Deep Watermarking[C]// IEEE. 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2020: 13548-13557. |
| [19] | DING Weiping, MING Yurui, CAO Zehong, et al. A Generalized Deep Neural Network Approach for Digital Watermarking Analysis[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2021, 6(3): 613-627. |
| [20] | BALUJA S. Hiding Images within Images[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2019, 42(7): 1685-1697. |
| [21] | DUAN Xintao, WU Guoming, LI Chun, et al. DUIANet: A Double Layer U-Net Image Hiding Method Based on Improved Inception Module and Attention Mechanism[EB/OL]. (2023-12-23)[2025-02-20]. https://doi.org/10.1016/j.jvcir.2023.104035. |
| [1] | 尚雯, 王宏霞. 基于指纹的5G通信说话人身份追踪方案[J]. 信息网络安全, 2021, 21(3): 79-86. |
| [2] | 肖迪, 马青青, 王兰, 向艳萍. 基于稀疏表示的云协助安全数字水印技术[J]. 信息网络安全, 2017, 17(1): 1-7. |
| [3] | 吴潇, 常成, 覃文杰, 程久军. 基于RFID和数字水印技术的标签防伪验证方法[J]. 信息网络安全, 2015, 15(8): 26-34. |
| [4] | 牟群刚, 蒋天发, 刘晶. 基于量子Haar小波变换的图像水印算法[J]. 信息网络安全, 2015, 15(6): 55-60. |
| [5] | 刘丽;周亚建. 二维条码数字水印技术研究[J]. , 2014, 14(1): 0-0. |
| [6] | 白丹;梁祝荣;何冰. 一种基于Matlab图形用户界面的数字水印系统[J]. , 2012, 12(6): 0-0. |
| [7] | 朱建忠;姚志强. 基于Asmuth-Bloom门限方案的小波域数字水印技术[J]. , 2012, 12(12): 0-0. |
| [8] | 晏燕;李琦峰;陈海燕;蔺莹. 四叉树分解的图像认证水印算法[J]. , 2012, 12(11): 0-0. |
| [9] | 刘艮;蒋天发. 同态加密技术及其在物联网中的应用研究[J]. , 2011, 11(5): 0-0. |
| [10] | 蒋天发;王理;蒋巍;熊祥光. 基于小波的二值图像盲数字水印的研究[J]. , 2009, 9(7): 0-0. |
| [11] | 熊祥光;蒋天发. 密码学在数字水印技术中的应用研究[J]. , 2009, 9(4): 0-0. |
| [12] | 赵圆圆;刘金根. 基于数字水印和加密技术的DRM系统模型设计[J]. , 2009, 9(12): 0-0. |
| [13] | 李敏;费耀平. 数字水印技术及其在电子政务安全领域的应用[J]. , 2006, 6(3): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||