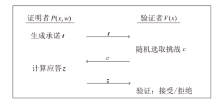
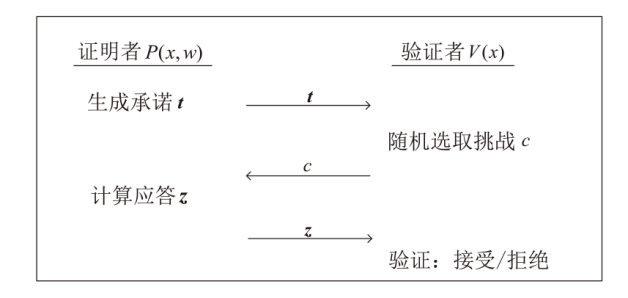
信息网络安全 ›› 2025, Vol. 25 ›› Issue (5): 679-688.doi: 10.3969/j.issn.1671-1122.2025.05.001
基于格的零知识证明综述
- 1.西安电子科技大学广州研究院,广州 510555
2.华润智算科技(广东)有限公司,深圳 518260
-
收稿日期:2024-11-22出版日期:2025-05-10发布日期:2025-06-10 -
通讯作者:潘静panjing@xidian.edu.cn -
作者简介:潘静(1989—),男,云南,讲师,博士,主要研究方向为格密码及隐私保护密码技术|李博逊(2002—),男,河北,硕士研究生,主要研究方向为隐私保护密码技术|万贝琳(2002—),女,湖北,硕士研究生,主要研究方向为隐私保护密码技术|钟焰涛(1980—),男,江西,高级工程师,博士,主要研究方向为密码学及隐私计算技术 -
基金资助:国家自然科学基金(62302376);国家重点研发计划(2023YFB3105902);中央高校基本科研业务费(XJSJ23103);深圳市科技重大专项(202307064)
An Overview on Lattice-Based Zero-Knowledge Proofs
PAN Jing1( ), LI Boxun1, WAN Beilin1, ZHONG Yantao2
), LI Boxun1, WAN Beilin1, ZHONG Yantao2
- 1. Guangzhou Institute of Technology, Xidian University, Guangzhou 510555, China
2. China Resources Intelligent Computing Technology (Guangdong) Co., Ltd., Shenzhen 518260, China
-
Received:2024-11-22Online:2025-05-10Published:2025-06-10
摘要:
量子计算的加速发展以及社会各界对隐私保护的日益重视,引发了对后量子零知识证明技术的研究热潮。文章聚焦于基于格的零知识证明的研究。首先,系统介绍了基于格的零知识证明的研究现状;然后,根据底层使用的关键技术对主流的基于格的零知识证明协议进行分类与总结,并深入分析3种经典协议的设计原理和性能表现;最后,简要讨论基于格的零知识证明未来可能的研究热点和发展方向。
中图分类号:
引用本文
潘静, 李博逊, 万贝琳, 钟焰涛. 基于格的零知识证明综述[J]. 信息网络安全, 2025, 25(5): 679-688.
PAN Jing, LI Boxun, WAN Beilin, ZHONG Yantao. An Overview on Lattice-Based Zero-Knowledge Proofs[J]. Netinfo Security, 2025, 25(5): 679-688.
表1
符号说明
| 符号 | 说明 |
|---|---|
| 素数 | |
| 模 | |
| 多项式环,其中 | |
| 表示向量(若无特殊说明,如 | |
| 表示矩阵,默认属于 | |
| 所有向量元素绝对值的最大值 | |
| 从有限集合 |
表1
| [1] | GOLDWASSER S, MICALI S, RACKOFF C. The Knowledge Complexity of Interactive Proof-Systems(Extended Abstract)[C]// ACM. 17th Annual ACM Symposium on Theory of Computing-STOC 1985. New York:ACM, 1985: 297-304. |
| [2] | GOLDREICH O, MICALI S, WIQDERSON A. How to Prove all NP Statements in Zero-Knowledge, and a Methodology of Cryptographic Protocol Design[C]// Springer. The 6th Annual International Cryptology Conference-CRYPTO1986. Heidelberg: Springer, 1986: 171-185. |
| [3] | GROTH J, OSTROVSKY T, SAHAI A. Non-Interactive Zaps and New Techniques for NIZK[C]// Springer. 26th Annual International Cryptology Conference-CRYPTO 2006. Heidelberg: Springer, 2006: 97-111. |
| [4] | JENS Groth. On the Size of Pairing-Based Non-Interactive Arguments[C]// Springer. 35th Annual International Conference on the Theory and Applications of Cryptographic Techniques-EUROCRYPT 2016. Heidelberg: Springer, 2016: 305-326. |
| [5] | GOLDREICH O, GOLDWASSER S. On the Limits of Non-Approximability of Lattice Problems[C]// ACM. 13th Annual ACM Symposium on the Theory of Computing-STOC 1998. New York:ACM, 1998: 1-9. |
| [6] | MICCIANCIO D, VADHAN S P. Statistical Zero-Knowledge Proofs with Efficient Provers: Lattice Problems and More[C]// Springer. 23th Annual International Cryptology Conference-CRYPTO 200. Heidelberg:Springer, 2003: 282-298. |
| [7] | PEIKERT C, VAIKUNTANATHAN V. Noninteractive Statistical Zero-Knowledge Proofs for Lattice Problems[C]// Springer. 28th Annual International Cryptology Conference-CRYPTO 2008. Heidelberg: Springer, 2008: 536-557. |
| [8] | KAWACHI A, TANAKA K, XAGAWA K. Concurrently Secure Identification Schemes Based on the Worst-Case Hardness of Lattice Problems[C]// Springer. 24th International Conference on the Theory and Application of Cryptology and Information Security-ASIACRYPT 2008. Heidelberg: Springer, 2018: 372-389. |
| [9] | LING San, NGUYEN K, STEHLÉ D, et al. Improved Zero-Knowledge Proofs of Knowledge for the ISIS Problem, and Applications[C]// Springer. 16th International Conference on Theory and Practice of Public Key Cryptography-PKC 2013. Heidelberg: Springer, 2013: 107-124. |
| [10] | ZHANG Yupeng, GENKIN D, KATZ J, et al. vSQL: Verifying Arbitrary SQL Queries over Dynamic Outsourced Databases[C]// IEEE. 38th IEEE Symposium on Security and Privacy-SP 2017. New York: IEEE, 2017: 863-880. |
| [11] | YANG Rupeng, AU M H, ZHANG Zhenfei, et al. Efficient Lattice-Based Zero-Knowledge Arguments with Standard Soundness: Construction and Applications[C]// Springer. 39th Annual International Cryptology Conference-CRYPTO 2019. Heidelberg: Springer, 2019: 147-175. |
| [12] | LIBERT B, LING San, MOUHARTEM F, et al. Signature Schemes with Efficient Protocols and Dynamic Group Signatures from Lattice Assumptions[C]// Springer. 22th International Conference on the Theory and Application of Cryptology and Information Security-ASIACRYPT 2016. Heidelberg: Springer, 2016: 373-403. |
| [13] | LING San, NGUYEN K, WANG Huaxiong, et al. Lattice-Based Group Signatures: Achieving Full Dynamicity with Ease[C]// Springer. 15th International Conference on Applied Cryptography and Network Security-ACNS 2017. Heidelberg: Springer, 2017: 293-312. |
| [14] | LIBERT B, LING San, MOUHARTEM F, et al. Zero-Knowledge Arguments for Matrix-Vector Relations and Lattice-Based Group Encryption[C]// Springer. 22th International Conference on the Theory and Application of Cryptology and Information Security-ASIACRYPT 2016. Heidelberg: Springer, 2016: 101-131. |
| [15] | LYUBASHEVSKY V. Fiat-Shamir with Aborts: Applications to Lattice and Factoring Based Signatures[C]// Springer. 15th International Conference on the Theory and Application of Cryptology and Information Security-ASIACRYPT 2009. Heidelberg: Springer, 2009: 598-616. |
| [16] | LYUBASHEVSKY V. Lattice Signatures without Trapdoors[C]// Springer. The 31th Annual International Conference on the Theory and Applications of Cryptographic Techniques-EUROCRYPT 2012. Heidelberg: Springer, 2012: 738-755. |
| [17] | BENHAMOUDA F, CAMENISCH J, KRENN S, et al. Better Zero-Knowledge Proofs for Lattice Encryption and Their Application to Group Signatures[C]// Springer. The 20th International Conference on the Theory and Application of Cryptology and Information Security-ASIACRYPT 2014. Heidelberg: Springer, 2014: 551-572. |
| [18] | BAUM C, DAMGÅRD I, LYUBASHEVSKY V, et al. More Efficient Commitments from Structured Lattice Assumptions[C]// Springer. The 11th International Conference on Security and Cryptography for Networks-SCN 2018. Heidelberg: Springer, 2018: 368-385. |
| [19] | ESGIN M F, STEINFELD R, LIU J K, et al. Lattice-Based Zero-Knowledge Proofs: New Techniques for Shorter and Faster Constructions and Applications[C]// Springer. 39th Annual International Cryptology Conference-CRYPTO 2019. Heidelberg: Springer, 2019: 115-146. |
| [20] | BOOTLE J, LYUBASHEVSKY V, SEILER G. Algebraic Techniques for Short(er) Exact Lattice-Based Zero-Knowledge Proofs[C]// Springer. The 39th Annual International Cryptology Conference-CRYPTO 2019. Heidelberg: Springer, 2019: 176-202. |
| [21] | ATTEMA T, LYUBASHEVSKY V, SEILER G. Practical Product Proofs for Lattice Commitments[C]// Springer. The 40th Annual International Cryptology Conference CRYPTO 2020. Heidelberg: Springer, 2020: 470-499. |
| [22] | ESGIN M F, NGUYEN N K, SEILER G. Practical Exact Proofs from Lattices: New Techniques to Exploit Fully-Splitting Rings[C]// Springer. The 26th International Conference on the Theory and Application of Cryptology and Information Security-ASIACRYPT 2020. Heidelberg: Springer, 2020: 259-288. |
| [23] | LYUBASHEVSKY V, NGUYEN N K, SEILER G. Shorter Lattice-Based Zero-Knowledge Proofs via One-Time Commitments[C]// Springer. The 24th International Conference on Theory and Practice of Public Key Cryptography-PKC 2021. Heidelberg: Springer, 2021: 215-241. |
| [24] | KIM D, LEE D, SEO J, et al. Toward Practical Lattice-Based Proof of Knowledge from Hint-MLWE[C]// Springer. The 43th Annual International Cryptology Conference CRYPTO-2023. Heidelberg: Springer, 2023: 549-580. |
| [25] | ESGIN M F, STEINFELD R, LIU Dongxi, et al. Efficient Hybrid Exact/Relaxed Lattice Proofs and Applications to Rounding and VRFs[C]// Springer. The 43th Annual International Cryptology Conference-CRYPTO 2023. Heidelberg: Springer, 2023: 484-517. |
| [26] | GOLDREICH O. Zero-Knowledge Twenty Years after Its Invention[EB/OL]. (2020-05-11)[2024-11-20]. https://dblp.org/rec/journals/iacr/Goldreich02a.html. |
| [27] | LI Feng, MCMILLIN B M. A Survey on Zero-Knowledge Proofs[J]. Advances in Computers, 2014(94): 25-69. |
| [28] | LI Weihan, ZHANG Zongyang, ZHOU Zibo, et al. An Overview on Succinct Non-Interactive Zero-Knowledge Proofs[J]. Journal of Cryptologic Research, 2022, 9(3): 379-447. |
| [29] | ZHANG Zongyang, ZHOU Zibo, DENG Yi. A Survey on Recursive and Composite Techniques of Zero-Knowledge Proofs[J]. Chinese Journal of Computers, 2024, 47(10): 2466-2490. |
| [30] | BAUM C, DITTMER S, SCHOLL P, et al. Sok: Vector OLE-Based Zero-Knowledge Protocols[J]. Designs, Codes and Cryptography, 2023(91): 3527-3561. |
| [31] | SUN Xiaoqiang, YU F R, ZHANG Peng, et al. A Survey on Zero-Knowledge Proof in Blockchain[J]. IEEE Network, 2021(35): 198-205. |
| [32] | BLUM M, FELDMAN P, MICALI S. Non-Interactive Zero-Knowledge and Its Applications (Extended Abstract)[C]// ACM. The 20th Annual ACM Symposium on Theory of Computing-STOC 1988. New York: ACM, 1988: 103-112. |
| [33] | FIAT A, SHAMIR A. How to Prove Yourself: Practical Solutions to Identification and Signature Problems[C]// Springer. The 6th Annual International Cryptology Conference CRYPTO 1986. Heidelberg:Springer, 1986: 186-194. |
| [34] | FEIGE U, FIAT A, SHAMIR A. Zero-Knowledge Proofs of Identity[C]// ACM. The 19th Annual ACM Symposium on Theory of Computing-STOC 1987. New York:ACM, 1987: 210-217. |
| [35] | BEN-SASSON E, CHIESA A, GARMAN C, et al. Zerocash: Decentralized Anonymous Payments from Bitcoin[C]// IEEE. The 35th IEEE Symposium on Security and Privacy-SP 2014. New York: IEEE, 2014: 459-474. |
| [36] | GUILLOU L C, QUISQUATER J. A “Paradoxical” Indentity-Based Signature Scheme Resulting from Zero-Knowledge[C]// Springer. The 8th Annual International Cryptology Conference-CRYPTO 1988. Heidelberg:Springer, 1988: 216-231. |
| [37] | STERN J. A New Paradigm for Public Key Identification[J]. IEEE Transactions on Information Theory, 1996, 42(6): 1757-1768. |
| [38] | LIBERT B, LING S, NGUYEN K, et al. Lattice-Based Zero-Knowledge Arguments for Integer Relations[C]// Springer. The 38th Annual International Cryptology Conference-CRYPTO 2018. Heidelberg: Springer, 2018: 700-732. |
| [39] | LYUBASHEVSKY V, NGUYEN N K, PLANÇON M. Lattice-Based Zero-Knowledge Proofs and Applications:Shorter, Simpler, and More General[C]// Springer. The 42th Annual International Cryptology Conference-CRYPTO 2022. Heidelberg: Springer, 2022: 71-101. |
| [1] | 杜育松, 江思维, 沈静, 张家豪. 一种抵御计时攻击的指数Bernoulli精确采样算法[J]. 信息网络安全, 2024, 24(6): 855-862. |
| [2] | 叶清, 何俊霏, 杨智超. 基于格的可搜索公钥加密研究进展[J]. 信息网络安全, 2024, 24(6): 903-916. |
| [3] | 胡海洋, 刘畅, 王栋, 魏旭. 基于区块链的清洁能源数据溯源机制[J]. 信息网络安全, 2024, 24(4): 626-639. |
| [4] | 吴昊天, 李一凡, 崔鸿雁, 董琳. 基于零知识证明和区块链的联邦学习激励方案[J]. 信息网络安全, 2024, 24(1): 1-13. |
| [5] | 赖成喆, 赵益宁, 郑东. 基于同态加密的隐私保护与可验证联邦学习方案[J]. 信息网络安全, 2024, 24(1): 93-105. |
| [6] | 刘芹, 王卓冰, 余纯武, 王张宜. 面向云安全的基于格的高效属性基加密方案[J]. 信息网络安全, 2023, 23(9): 25-36. |
| [7] | 俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52. |
| [8] | 张晓旭, 石润华. EHR系统中一种验证外包加密数据正确性的访问控制方案[J]. 信息网络安全, 2023, 23(5): 85-94. |
| [9] | 王勇, 陈莉杰, 钟美玲. 基于零知识证明的区块链方案研究进展[J]. 信息网络安全, 2022, 22(12): 47-56. |
| [10] | 陶云亭, 孔凡玉, 于佳, 徐秋亮. 抗量子格密码体制的快速数论变换算法研究综述[J]. 信息网络安全, 2021, 21(9): 46-51. |
| [11] | 李鱼, 韩益亮, 李喆, 朱率率. 基于LWE的抗量子认证密钥交换协议[J]. 信息网络安全, 2020, 20(10): 92-99. |
| [12] | 马利民, 张伟, 刘熙尧. 一种安全的无线体域网医疗信息管理系统研究与设计[J]. 信息网络安全, 2019, 19(5): 38-46. |
| [13] | 张敏, 许春香, 黄闽英. 远程医疗环境下面向多服务器的轻量级多因子身份认证协议研究[J]. 信息网络安全, 2019, 19(10): 42-49. |
| [14] | 江明明, 赵利军, 王艳, 王保仓. 面向云数据共享的量子安全的无证书双向代理重加密[J]. 信息网络安全, 2018, 18(8): 17-24. |
| [15] | 刘川葆, 陈明志, 林伟宁, 冯映燕. HCE模式下一种基于零知识证明的身份认证方法[J]. 信息网络安全, 2017, 17(6): 68-74. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||