信息网络安全 ›› 2024, Vol. 24 ›› Issue (9): 1458-1469.doi: 10.3969/j.issn.1671-1122.2024.09.013
基于多门控混合专家模型的网络异常流量识别与防御模型
- 1.上海开放大学,上海 200433
2.上海教育软件发展有限公司,上海 200082
-
收稿日期:2024-06-02出版日期:2024-09-10发布日期:2024-09-27 -
通讯作者:黄河俊aachouchou@163.com -
作者简介:郭永进(1969—),男,河南,硕士,主要研究方向为大数据分析、网络安全|黄河俊(1978—),男,浙江,硕士,主要研究方向为机器学习、网络安全
Anomaly Traffic Identification and Defense Model in Networks Based on the Multi-Gate Mixture of Experts
GUO Yongjin1,2, HUANG Hejun1,2( )
)
- 1. Shanghai Open University, Shanghai 200433, China
2. Shanghai Education Software Development Company, Shanghai 200082, China
-
Received:2024-06-02Online:2024-09-10Published:2024-09-27
摘要:
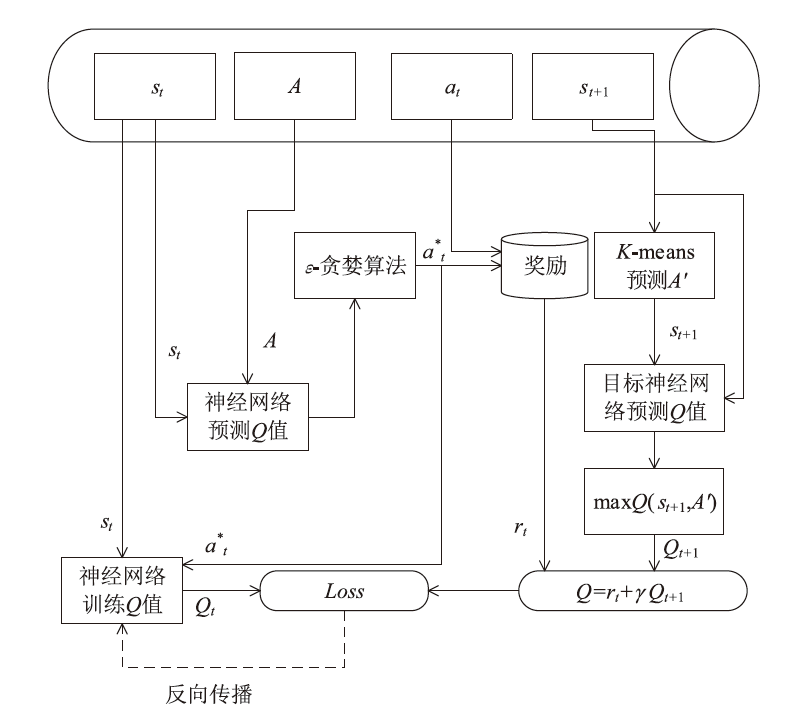
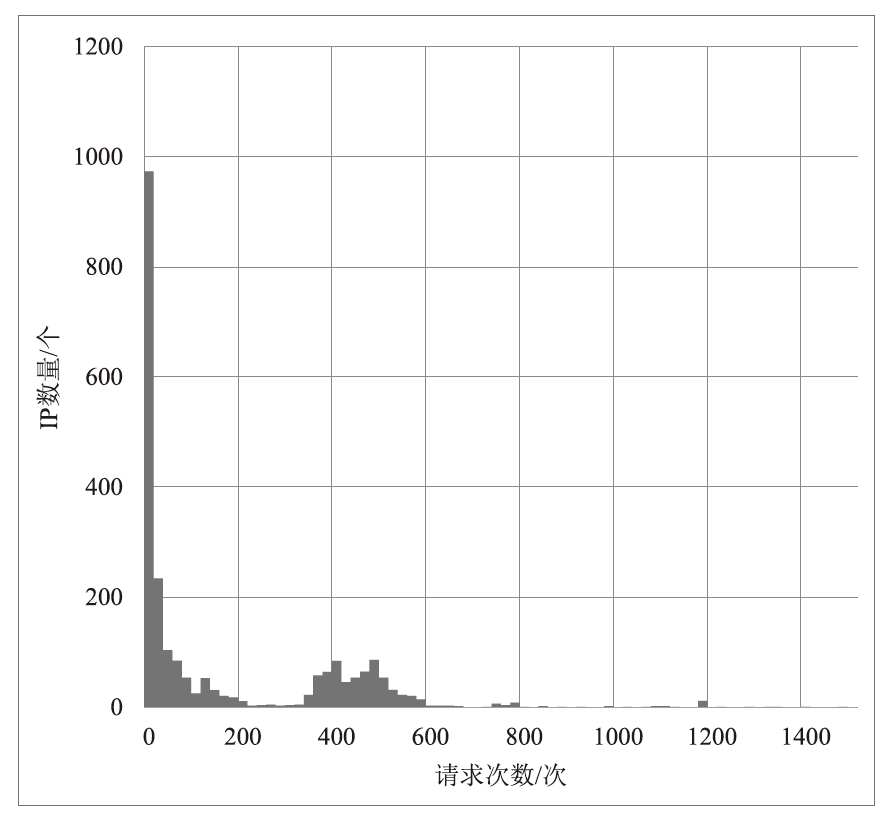
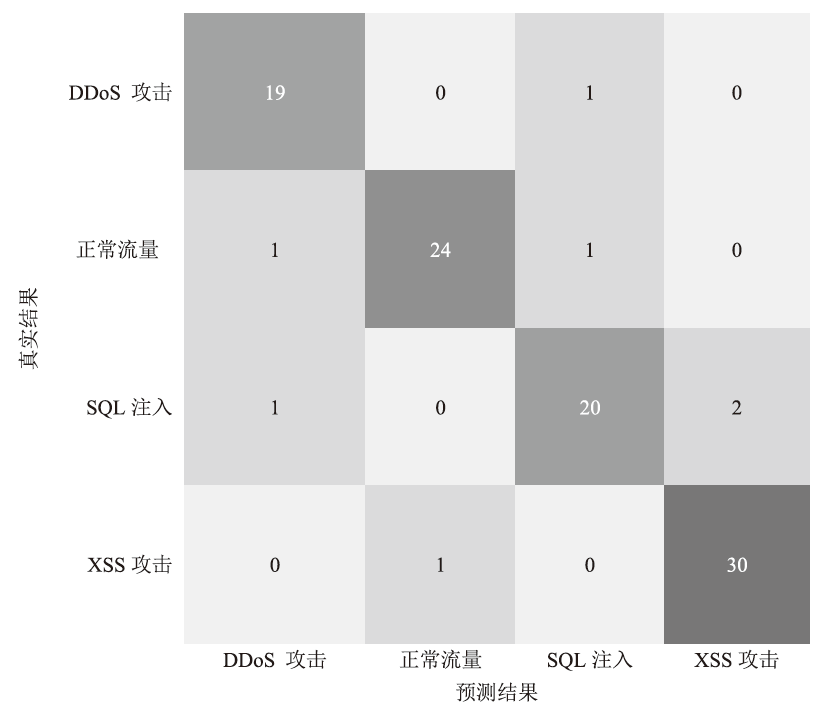
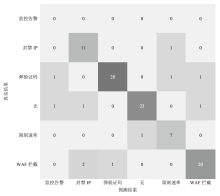
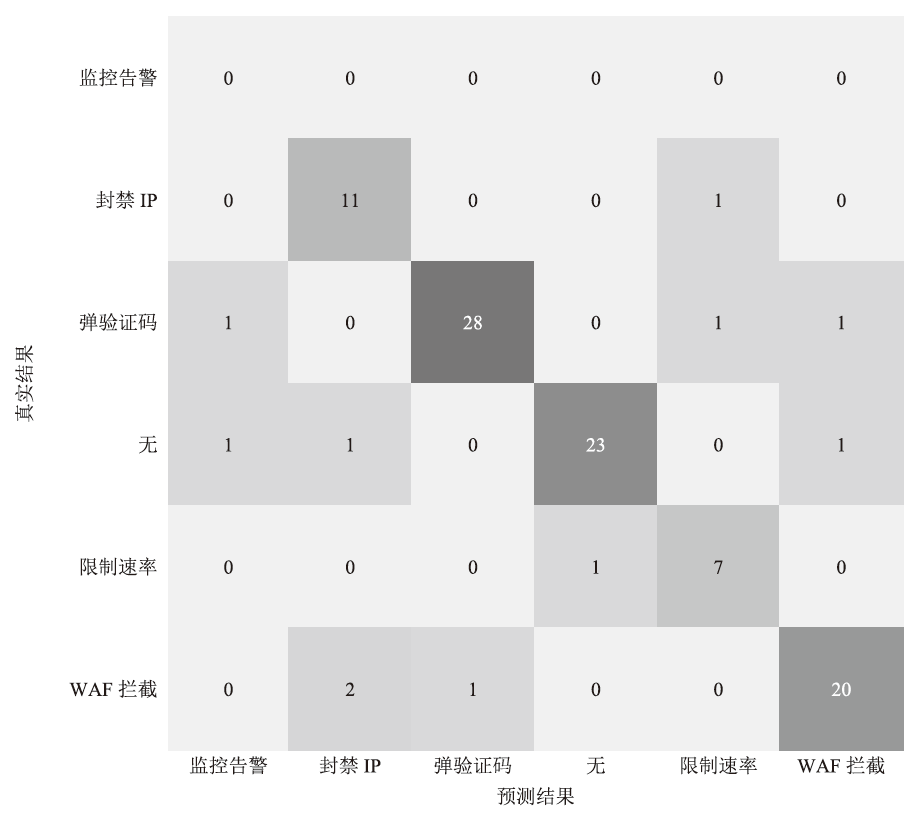
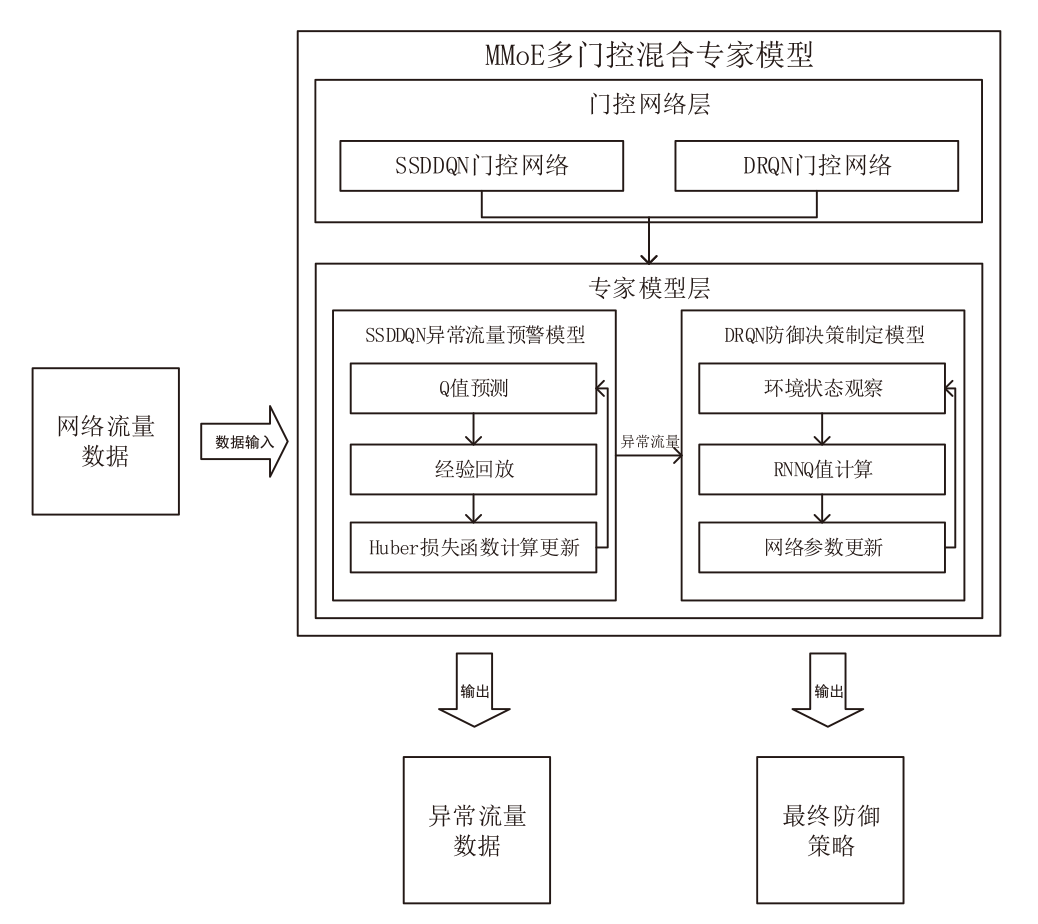
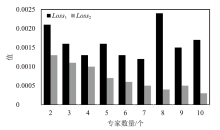
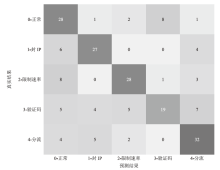
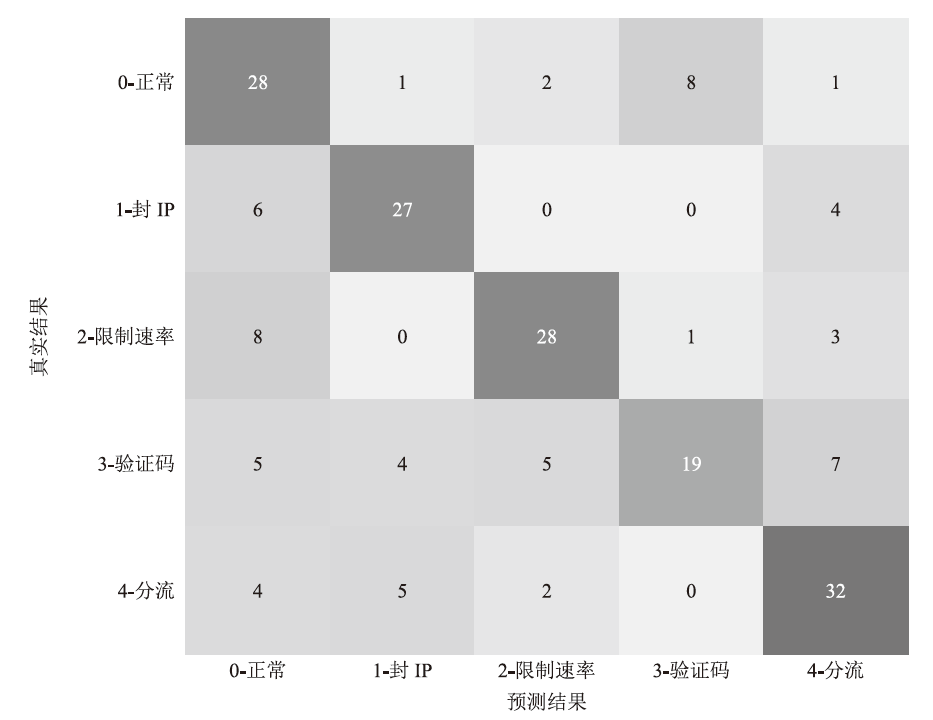
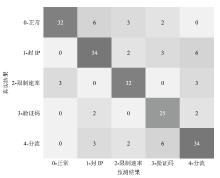
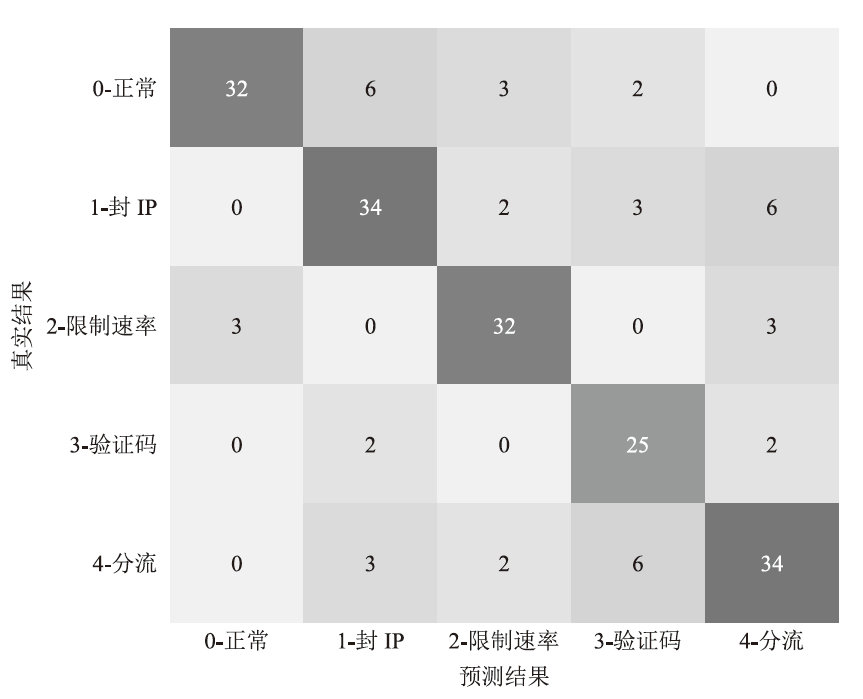
文章提出一种基于多门控混合专家模型的网络异常流量识别与防御模型,该模型适用于业务高峰期间混杂攻击流量的场景。首先,多门控混合专家模型对网络流量进行实时监测和异常识别,区分由业务需求导致的正常流量峰值和异常流量,减少误报,系统将检测到的异常流量作为输入,生成针对性的防御策略。然后,多门控混合专家模型对异常流量识别和防御策略生成专家模型进行协调,提高系统的识别精准度和策略生成的有效性。在实际业务场景中获取的数据集上的实验结果表明,该模型识别准确率和防御效果优于主流的机器学习模型,能够准确识别出混杂在业务高峰期间的异常攻击流量,并生成合适的防御策略。
中图分类号:
引用本文
郭永进, 黄河俊. 基于多门控混合专家模型的网络异常流量识别与防御模型[J]. 信息网络安全, 2024, 24(9): 1458-1469.
GUO Yongjin, HUANG Hejun. Anomaly Traffic Identification and Defense Model in Networks Based on the Multi-Gate Mixture of Experts[J]. Netinfo Security, 2024, 24(9): 1458-1469.
表1
特征及含义
| 特征 | 含义 |
|---|---|
| ip_ua_unique_path_cnt_w | 窗口内相同IP、UA(User-Agent)的情况下path的去重数量 |
| ip_unique_ua_cnt_w | 窗口内相同IP情况下遍历不同UA的去重数量 |
| ip_cnt_w | 窗口内IP数量 |
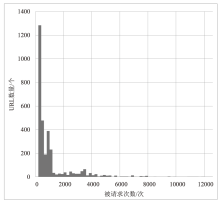
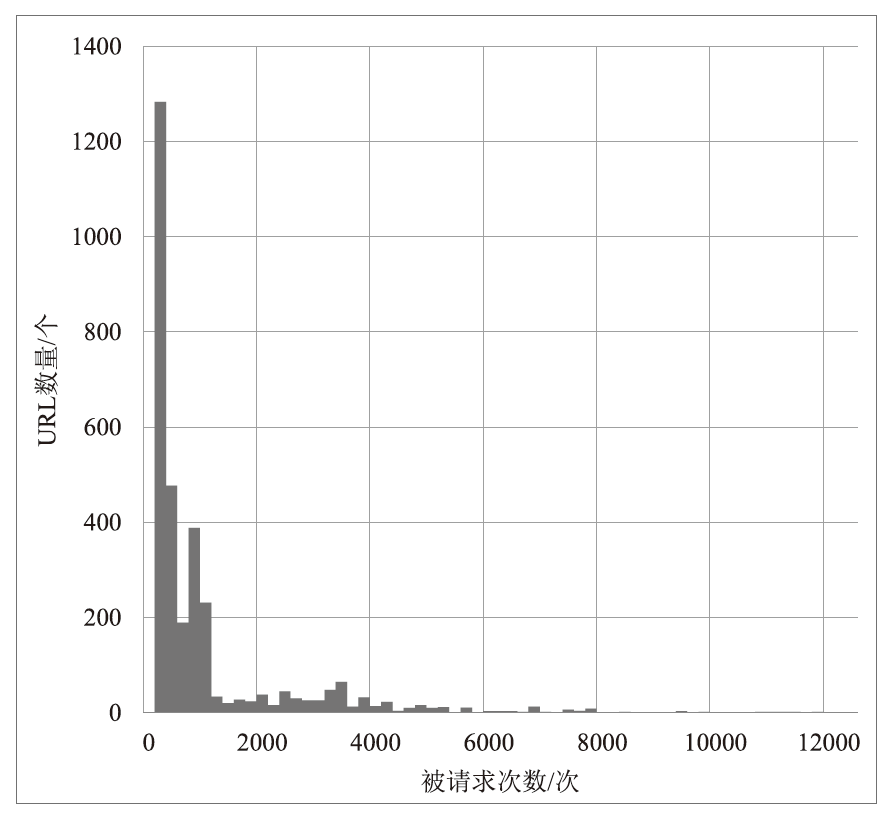
| url_cnt_w | 窗口内URL数量 |
| ip_ua_cnt_w | 窗口内IP和UA的组合数量 |
| ip_url_cnt_w | 窗口内IP和URL的组合数量 |
| ip_ua_url_cnt_w | 窗口内IP、UA和URL的组合数量 |
| url_unique_ip_cnt_w | 窗口内同一URL下IP的去重数量 |
| ip_34xx_cnt_w | 窗口内同一IP下状态码为401/403/404的数量 |
| ip_url_unique_ua_cnt_w | 窗口内同一IP和URL下UA的去重数量 |
| ip_req_mean_w | 窗口内同一IP下请求包大小均值 |
| [1] | PRICE-WILLIAMS M, HEARD N, RUBIN-DELANCHY P. Detecting Weak Dependence in Computer Network Traffic Patterns by Using Higher Criticism[J]. Journal of the Royal Statistical Society Series C, 2019, 68(3): 641-655. |
| [2] | WAN Jiafu, CHEN Baotong, IMRAN M, et al. Toward Dynamic Resources Management for IoT-Based Manufacturing[J]. IEEE Communications Magazine, 2018, 56(2): 52-59. |
| [3] | TIAN Zhihong, SHI Wei, WANG Yuhang, et al. Real-Time Lateral Movement Detection Based on Evidence Reasoning Network for Edge Computing Environment[J]. IEEE Transactions on Industrial Informatics, 2019, 15(7): 4285-4294. |
| [4] | VAN HASSELT H, GUEZ A, SILVER D. Deep Reinforcement Learning with Double Q-Learning[EB/OL]. (2015-12-08)[2024-05-11]. http://arxiv.org/abs/1509.06461v3. |
| [5] | CHOI H, KIM M, LEE G, et al. Unsupervised Learning Approach for Network Intrusion Detection System Using Autoencoders[J]. The Journal of Supercomputing, 2019, 75(9): 5597-5621. |
| [6] | AHMED M, SERAJ R, ISLAM S M S. The k-Means Algorithm: A Comprehensive Survey and Performance Evaluation[EB/OL]. (2020-08-07)[2024-05-11]. https://doi.org/10.3390/electronics9081295. |
| [7] | HAUSKNECHT M, STONE P, RAMANI D. Deep Recurrent Q-Learning for Partially Observable MDPS[EB/OL]. [2024-05-11]. https://arxiv.org/abs/1507.06527v4. |
| [8] | WANG Ke, STOLFO S J. Anomalous Payload-Based Network Intrusion Detection[EB/OL]. [2024-05-11]. https://wenku.baidu.com/view/8b5063a2284ac850ad02429f.html?fr=xueshu&_wkts_=1724600629659&needWelcomeRecommand=1. |
| [9] | KIM M S, KONG H J, HONG S C, et al. A Flow-Based Method for Abnormal Network Traffic Detection[C]// IEEE. 2004 IEEE/IFIP Network Operations and Management Symposium. New York: IEEE, 2004: 599-612. |
| [10] | QIAO Yiguo, XIN Xuezhu, BIN Yu, et al. Anomaly Intrusion Detection Method Based on HMM[J]. Electronics Letters, 2002, 38(13): 663-664. |
| [11] | LEI Yang. Network Anomaly Traffic Detection Algorithm Based on SVM[C]// IEEE. 2017 International Conference on Robots & Intelligent System (ICRIS). New York: IEEE, 2017: 217-220. |
| [12] | KONG Lingjing, HUANG Guowei, WU Keke. Identification of Abnormal Network Traffic Using Support Vector Machine[C]// IEEE. 2017 18th International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT). New York: IEEE, 2017: 288-292. |
| [13] | JIANG Wei, FANG Binxing, TIAN Zhihong, et al. Research on Defense Strategies Selection Based on Attack-Defense Stochastic Game Model[J]. Journal of Computer Research & Development, 2010, 47(10): 1714-1723. |
| [14] | WEI Longfei, SARWAT A I, SAAD W, et al. Stochastic Games for Power Grid Protection against Coordinated Cyber-Physical Attacks[J]. IEEE Transactions on Smart Grid, 2018, 9(2): 684-694. |
| [15] | WATKINS C, DAYAN P. Q-Learning[J]. Machine Learning, 1992, 8(3-4): 279-292. |
| [16] | NGUYEN T T, REDDI V J. Deep Reinforcement Learning for Cyber Security[J]. IEEE Transactions on Neural Networks and Learning Systems, 2023, 34(8): 3779-3795. |
| [17] | EGHTESAD T, VOROBEYCHIK Y, LASZKA A. Adversarial Deep Reinforcement Learning Based Adaptive Moving Target Defense[C]// Srpinger. International Conference on Decision and Game Theory for Security. Heidelberg: Springer, 2020: 58-79. |
| [18] | CASGRAIN P, NING B, JAIMUNGAL S. Deep Q-Learning for Nash Equilibria: Nash-DQN[EB/OL]. [2024-05-11]. https://arxiv.org/abs/1904.10554v2. |
| [19] | SHEN Sheng, HOU Le, ZHOU Yanqi, et al. Mixture-of-Experts Meets Instruction Tuning: A Winning Combination for Large Language Models[EB/OL]. [2024-05-11]. https://arxiv.org/pdf/2305.14705. |
| [20] | SHAZEER N, MIRHOSEINI A, MAZIARZ K, et al. Outrageously Large Neural Networks: The Sparsely-Gated Mixture-of-Experts Layer[EB/OL]. [2024-05-11]. https://arxiv.org/abs/1701.06538v1. |
| [21] | LEPIKHIN D, LEE H, XU Yuanzhong, et al. GShard: Scaling Giant Models with Conditional Computation and Automatic Sharding[EB/OL]. [2024-05-11]. https://arxiv.org/pdf/2006.16668. |
| [1] | 李娇, 张玉清, 吴亚飚. 面向网络安全关系抽取的大语言模型数据增强方法[J]. 信息网络安全, 2024, 24(10): 1477-1483. |
| [2] | 王强, 刘奕智, 李涛, 贺小川. 网络流量密态匿迹与体系对抗综述[J]. 信息网络安全, 2024, 24(10): 1484-1492. |
| [3] | 沈钦涛, 梁瑞刚, 王宝林, 张倞诚, 陈恺. 基于动态执行日志和反向分析的漏洞成因分析技术[J]. 信息网络安全, 2024, 24(10): 1493-1505. |
| [4] | 魏金侠, 黄玺章, 付豫豪, 李婧, 龙春. 基于全局特征学习的挖矿流量检测方法[J]. 信息网络安全, 2024, 24(10): 1506-1514. |
| [5] | 王南, 袁也, 杨浩然, 文周之, 苏明, 刘晓光. 环保大数据在区块链中的隐私计算[J]. 信息网络安全, 2024, 24(10): 1515-1527. |
| [6] | 张子涵, 赖清楠, 周昌令. 深度学习框架模糊测试研究综述[J]. 信息网络安全, 2024, 24(10): 1528-1536. |
| [7] | 王亚欣, 张健. 基于少样本命名实体识别技术的电子病历指纹特征提取[J]. 信息网络安全, 2024, 24(10): 1537-1543. |
| [8] | 张展鹏, 王鹃, 张冲, 王杰, 胡宇义. 基于图同构网络的高效Web模糊测试技术研究[J]. 信息网络安全, 2024, 24(10): 1544-1552. |
| [9] | 萨其瑞, 尤玮婧, 张逸飞, 邱伟杨, 马存庆. 联邦学习模型所有权保护方案综述[J]. 信息网络安全, 2024, 24(10): 1553-1561. |
| [10] | 陈婧, 张健. 基于知识蒸馏的无数据个性化联邦学习算法[J]. 信息网络安全, 2024, 24(10): 1562-1569. |
| [11] | 芦效峰, 程天泽, 龙承念. 基于随机游走的图神经网络黑盒对抗攻击[J]. 信息网络安全, 2024, 24(10): 1570-1577. |
| [12] | 吴立钊, 汪晓丁, 徐恬, 阙友雄, 林晖. 面向半异步联邦学习的防御投毒攻击方法研究[J]. 信息网络安全, 2024, 24(10): 1578-1585. |
| [13] | 姚萌萌, 王宇, 洪瑜平. 基于递归认证测试的SIP协议形式化分析[J]. 信息网络安全, 2024, 24(10): 1586-1594. |
| [14] | 赵戈, 郑扬, 陶泽林. 面向智能可穿戴设备的系统风险评估分析[J]. 信息网络安全, 2024, 24(10): 1595-1603. |
| [15] | 何开宇, 王彬, 于哲, 陈方. ARP欺骗攻击与硬件防御研究[J]. 信息网络安全, 2024, 24(10): 1604-1610. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||