信息网络安全 ›› 2024, Vol. 24 ›› Issue (8): 1152-1162.doi: 10.3969/j.issn.1671-1122.2024.08.002
基于改进鲸鱼算法优化SVM的软件缺陷检测方法
- 1.北京交通大学智能交通数据安全与隐私保护技术北京市重点实验室,北京 100044
2.北京交通大学国家经济安全预警工程北京实验室,北京 100044
3.北京交通大学詹天佑学院,北京 100044
-
收稿日期:2024-04-09出版日期:2024-08-10发布日期:2024-08-22 -
通讯作者:田晓清22140434@bjtu.edu.cn -
作者简介:杜晔(1978—),男,黑龙江,教授,博士,主要研究方向为网络行为异常检测、空天地信息一体化网络安全|田晓清(2001—),女,河北,硕士研究生,主要研究方向为软件缺陷检测、漏洞检测|李昂(2002—),男,内蒙古,主要研究方向为空天地信息一体化网络安全|黎妹红(1974—),男,湖北,副教授,博士,主要研究方向为保密技术、网络攻防 -
基金资助:国家重点研发计划(2022YFB3105105)
Software Defect Detection Method Based on Improved Whale Algorithm to Optimize SVM
DU Ye1,2, TIAN Xiaoqing1( ), LI Ang3, LI Meihong1,2
), LI Ang3, LI Meihong1,2
- 1. Beijing Key Laboratory of Security and Privacy In Intelligent Transportation, Beijing Jiaotong University, Beijing 100044, China
2. Beijing Laboratory of National Economic Security Early-Warning Engineering, Beijing Jiaotong University, Beijing 100044, China
3. Jeme Tienyow Honors College, Beijing Jiaotong University, Beijing 100044, China
-
Received:2024-04-09Online:2024-08-10Published:2024-08-22
摘要:
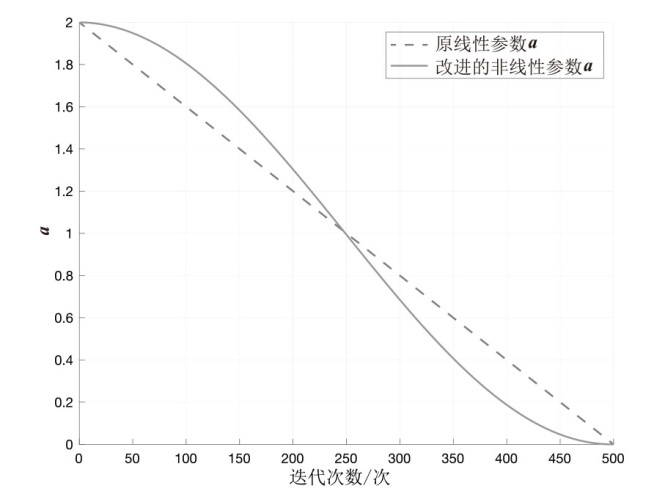
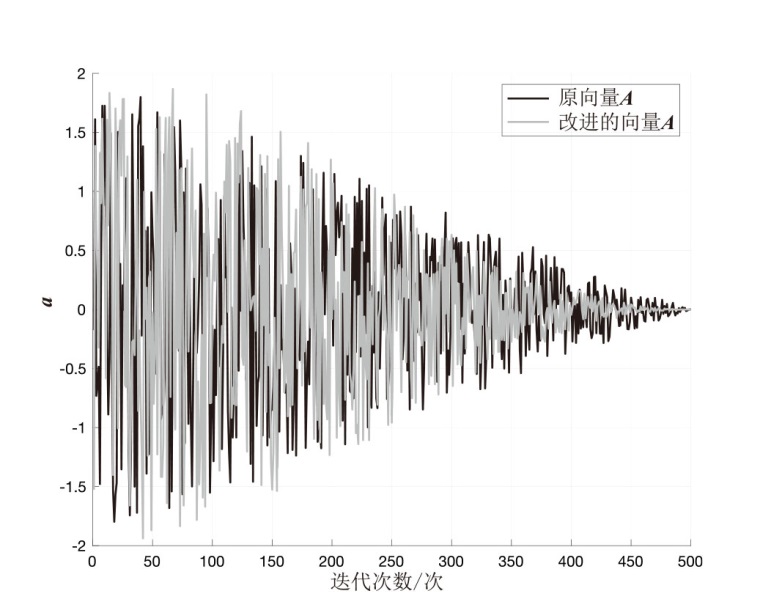
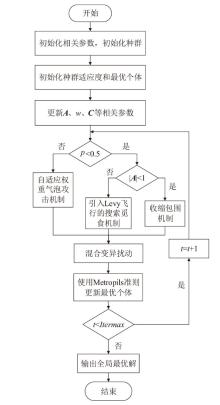
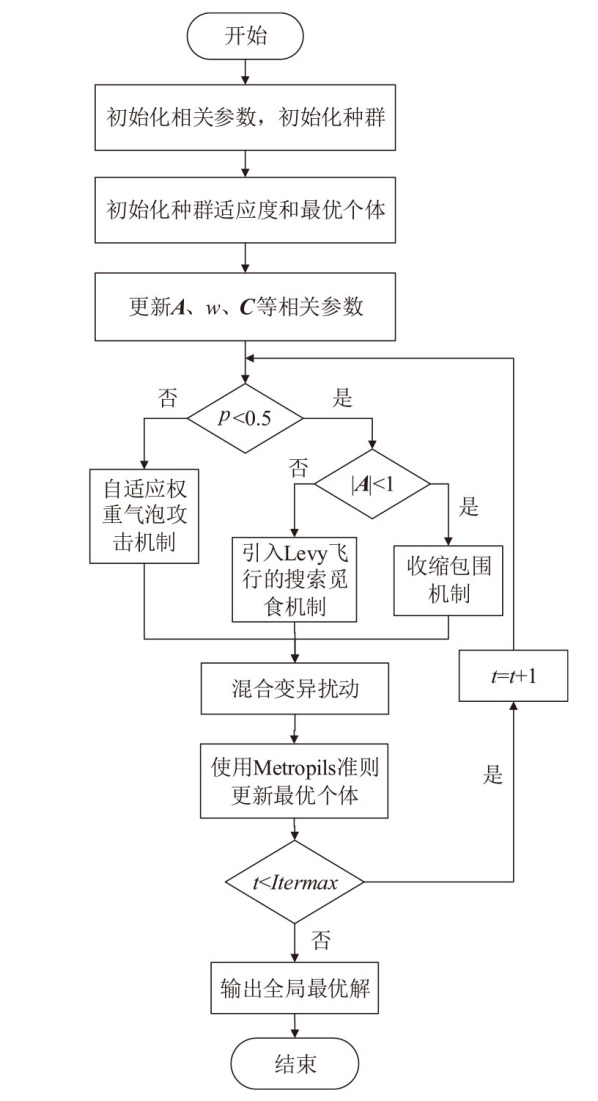
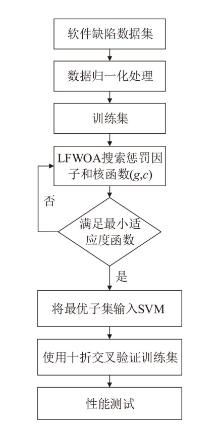
为解决传统支持向量机在软件缺陷检测中存在分类精度低、参数选择困难等问题,文章提出一种基于改进鲸鱼算法优化SVM的软件缺陷检测方法LFWOA-SVM。首先针对鲸鱼算法在求解过程中存在收敛速度慢、寻优效率低和局部最优解问题,基于Levy飞行策略优化鲸鱼觅食阶段,最大限度地实现搜索代理多样化,并利用混合变异扰动算子提高WOA的全局寻优能力;然后采用改进的鲸鱼算法LFWOA对SVM的惩罚因子和核函数参数进行优化,在获得最优参数的同时可有效检测软件缺陷。仿真实验表明,在6个基准测试函数中,LFWOA展现出更高的寻优速度和全局搜索能力;在8个公开软件缺陷数据集上进行测试显示,LFWOA-SVM方法能够有效提高分类性能和预测精度。
中图分类号:
引用本文
杜晔, 田晓清, 李昂, 黎妹红. 基于改进鲸鱼算法优化SVM的软件缺陷检测方法[J]. 信息网络安全, 2024, 24(8): 1152-1162.
DU Ye, TIAN Xiaoqing, LI Ang, LI Meihong. Software Defect Detection Method Based on Improved Whale Algorithm to Optimize SVM[J]. Netinfo Security, 2024, 24(8): 1152-1162.
表1
基准测试函数
| 类型 | 函数 | 维度 | 搜索 范围 | 理论 最优值 |
|---|---|---|---|---|
| 单峰 | 30 | [-100,100] | 0 | |
| 30 | [-30,30] | 0 | ||
| 30 | [-100,100] | 0 | ||
| 多峰 | 30 | [-32,32] | 0 | |
| 30 | [-600,600] | 0 | ||
| 30 | [-5.12,5.12] | 0 |
表3
基准测试函数寻优对比
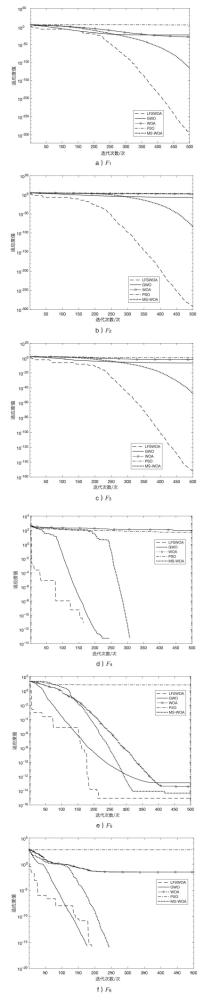
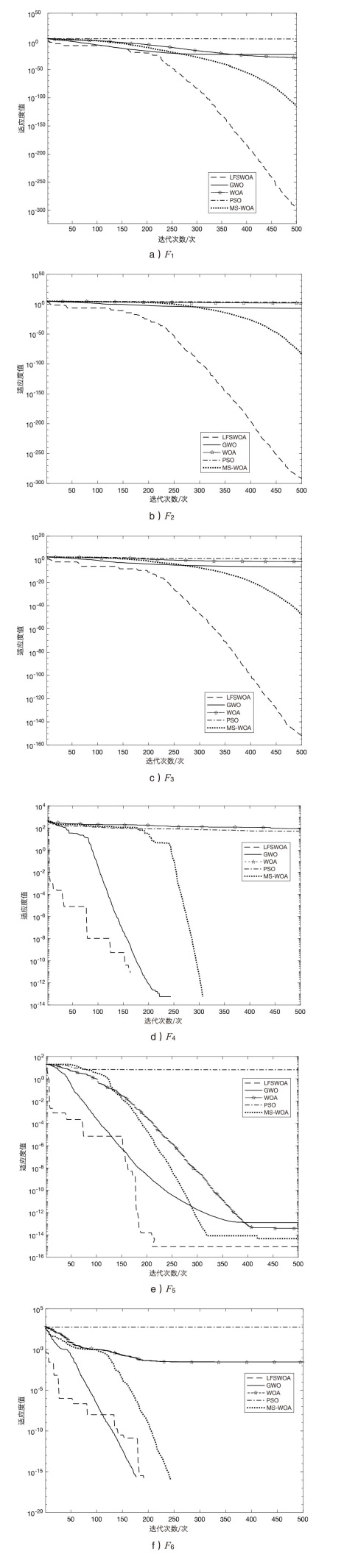
| 基准函数 | 算法 | 均值 | 标准差 | 最优解 |
|---|---|---|---|---|
| F1 | LFWOA | 0.0000E+00 | 0.0000E+00 | 0.0000E+00 |
| GWO | 1.1788E-27 | 1.4877E-27 | 2.8560E-29 | |
| WOA | 2.6161E-28 | 6.4843E-28 | 1.0315E-32 | |
| PSO | 8.4296E-01 | 3.6406E-01 | 2.2663E-01 | |
| MS-WOA | 0.0000E+00 | 0.0000E+00 | 0.0000E+00 | |
| F2 | LFWOA | 0.0000E+00 | 0.0000E+00 | 0.0000E+00 |
| GWO | 1.8138E-05 | 3.5241E-05 | 9.9501E-09 | |
| WOA | 6.6487E+02 | 6.8947E+02 | 2.3600E+01 | |
| PSO | 7.2326E+02 | 8.1981E+02 | 6.2506E+01 | |
| MS-WOA | 7.3821E-77 | 2.9200E-76 | 6.4254E-88 | |
| F3 | LFWOA | 0.0000E+00 | 0.0000E+00 | 0.0000E+00 |
| GWO | 6.7930E-07 | 6.7869E-07 | 4.9692E-08 | |
| WOA | 5.7282E-02 | 9.7826E-02 | 4.0602E-04 | |
| PSO | 3.7070E+00 | 1.3278E+00 | 1.5407E+00 | |
| MS-WOA | 8.7712E-48 | 2.8337E-47 | 1.2352E-52 | |
| F4 | LFWOA | 0.0000E+00 | 0.0000E+00 | 0.0000E+00 |
| GWO | 3.0885E+00 | 3.9162E+00 | 5.6843E-14 | |
| WOA | 6.2138E+01 | 4.2734E+01 | 1.9973E+00 | |
| PSO | 5.2677E+01 | 1.2228E+01 | 3.4609E+01 | |
| MS-WOA | 0.0000E+00 | 0.0000E+00 | 0.0000E+00 | |
| F5 | LFWOA | 0.0000E+00 | 0.0000E+00 | 8.8818E-16 |
| GWO | 5.6843E-14 | 5.6843E-14 | 7.5495E-14 | |
| WOA | 1.9973E+00 | 1.9973E+00 | 2.2204E-14 | |
| PSO | 3.4609E+01 | 3.4609E+01 | 3.3968E+00 | |
| MS-WOA | 0.0000E+00 | 0.0000E+00 | 8.8818E-16 | |
| F6 | LFWOA | 0.0000E+00 | 0.0000E+00 | 0.0000E+00 |
| GWO | 5.8887E-03 | 9.2274E-03 | 0.0000E+00 | |
| WOA | 2.4726E-03 | 6.7279E-03 | 0.0000E+00 | |
| PSO | 2.0872E+02 | 1.7547E+01 | 1.7169E+02 | |
| MS-WOA | 5.5940E-13 | 3.0640E-12 | 0.0000E+00 |
表4
各算法AUC
| 数据集 | SVM | WOA-SVM | PSO-SVM | LFWOA-SVM |
|---|---|---|---|---|
| MC2 | 0.538 | 0.600 | 0.567 | 0.638 |
| PC1 | 0.581 | 0.664 | 0.663 | 0.671 |
| MW1 | 0.500 | 0.643 | 0.639 | 0.643 |
| KC3 | 0.500 | 0.538 | 0.542 | 0.551 |
| PC3 | 0.757 | 0.762 | 0.675 | 0.764 |
| tomcat | 0.793 | 0.803 | 0.732 | 0.794 |
| jedit-4.2 | 0.706 | 0.801 | 0.726 | 0.804 |
| camel-1.6 | 0.611 | 0.631 | 0.597 | 0.673 |
| 均值 | 0.623 | 0.680 | 0.642 | 0.693 |
表5
各算法MCC
| 数据集 | SVM | PSO-SVM | WOA-SVM | LFWOA-SVM |
|---|---|---|---|---|
| MC2 | 0.077 | 0.364 | 0.311 | 0.386 |
| PC1 | 0.316 | 0.384 | 0.480 | 0.499 |
| MW1 | 0.039 | 0.381 | 0.312 | 0.468 |
| KC3 | 0.001 | 0.258 | 0.220 | 0.143 |
| PC3 | 0.003 | 0.202 | 0.205 | 0.324 |
| tomcat | 0.002 | 0.147 | 0.116 | 0.152 |
| jedit-4.2 | 0.220 | 0.401 | 0.411 | 0.415 |
| camel-1.6 | 0.042 | 0.149 | 0.175 | 0.181 |
| 均值 | 0.086 | 0.286 | 0.279 | 0.321 |
| [1] | LI Minglei, HUANG Hui, LU Yuliang. Test Case Generation Technology Based on Symbolic Divide and Conquer Zones for Vulnerability Mining[J]. Netinfo Security, 2020, 20 (5): 39-46. |
| 李明磊, 黄晖, 陆余良. 面向漏洞挖掘的基于符号分治区的测试用例生成技术[J]. 信息网络安全, 2020, 20(5): 39-46. | |
| [2] | ALSAEEDI A, KHAN M Z. Software Defect Prediction Using Supervised Machine Learning and Ensemble Techniques: A Comparative Study[J]. Journal of Software Engineering and Applications, 2019, 12(5): 85-100. |
| [3] | LI Sicong, WANG Jian, SONG Yafei, et al. Malicious Code Classification Method Based on BiTCN-DLP[J]. Netinfo Security, 2023, 23(11): 104-117. |
| 李思聪, 王坚, 宋亚飞, 等. 基于BiTCN-DLP的恶意代码分类方法[J]. 信息网络安全, 2023, 23(11): 104-117. | |
| [4] | GRAY D, BOWES D, DAVEY N, et al. Using the Support Vector Machine as a Classification Method for Software Defect Prediction with Static Code Metrics[C]// Springer. International Conference on Engineering Applications of Neural Networks. Heidelberg: Springer, 2009: 223-234. |
| [5] | YANG Zhanyu, LU Lu, ZOU Quanyi. Ensemble Kernel-Mapping-Based Ranking Support Vector Machine for Software Defect Prediction[J]. IEEE Transactions on Reliability, 2024, 73(1): 664-679. |
| [6] | RAJABI A, BOBBA R B. False Data Detection in Distributed Oscillation Mode Estimation Using Hierarchical K-Means[C]// IEEE. 2019 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm). New York: IEEE, 2019: 1-7. |
| [7] | CHATTERJEE S, MAJI B. A Bayesian Belief Network Based Model for Predicting Software Faults in Early Phase of Software Development Process[J]. Applied Intelligence, 48(6): 1-15. |
| [8] | MANJULA C, FLORENCE L. Deep Neural Network Based Hybrid Approach for Software Defect Prediction Using Software Metrics[EB/OL]. [2024-03-10]. https://link.springer.com/article/10.1007/s10586-018-1696-z. |
| [9] |
BORANDAG E, OZCIFT A, KILINC D, et al. Majority Vote Feature Selection Algorithm in Software Fault Prediction[J]. Computer Science and Information Systems, 2019, 16(2): 515-539.
doi: 10.2298/CSIS180312039B |
| [10] | GRAY D, BOWES D, DAVEY N, et al. Using the Support Vector Machine as a Classification Method for Software Defect Prediction with Static Code Metrics[C]// Springer. International Conference on Engineering Applications of Neural Networks. Heidelberg: Springer, 2009, 223-234. |
| [11] | REN Shengbing, LIAO Xiangdang. Software Defect Prediction Based on Cost-Sensitive Support Vector Machine[J]. Computer Engineering & Science, 2018, 40(10): 1787-1795. |
| 任胜兵, 廖湘荡. 基于代价敏感支持向量机的软件缺陷预测研究[J]. 计算机工程与科学, 2018, 40(10): 1787-1795. | |
| [12] | WANG Ruoping, CHEN Yan, WANG Dong, et al. Vehicle Interior Abnormal Noise Identification Method Based on Multi-Feature Extraction and Grey Wolf Algorithm Optimization SVM[J]. Computer Applications and Software, 2024, 41(3): 41-48. |
| 王若平, 陈严, 王东, 等. 基于多特征提取与灰狼算法优化SVM的车内异响识别方法[J]. 计算机应用与软件, 2024, 41(3): 41-48. | |
| [13] | AZZEH M, NASSIF A B, BANITAAN S. On Selection of Optimal Kernel Function for Software Defect Prediction[C]// IEEE. 2022 21st IEEE International Conference on Machine Learning and Applications(ICMLA). New York: IEEE, 2022: 1761-1768. |
| [14] | ZHANG Xinying, LI Bin, WU Yuanyuan. Malware Detection Based on Synchronization Optimizing Feature Selection and Support Vector Machine[J]. Computer Engineering and Design, 2024, 45(2): 467-476. |
| 张新英, 李彬, 吴媛媛. 针对恶意软件检测的特征选择与SVM协同优化[J]. 计算机工程与设计, 2024, 45(2): 467-476. | |
| [15] | FENG Zhang, PEI Dong, WANG Wei. Face Recognition by Support Vector Machine Optimized by an Improved Grey Wolf Algorithm[J]. Computer Engineering & Science, 2019, 41(6): 1057-1063. |
| 冯璋, 裴东, 王维. 基于改进灰狼算法优化支持向量机的人脸识别[J]. 计算机工程与科学, 2019, 41(6): 1057-1063. | |
| [16] | ZHANG Ran, LIU Min, PAN Zhihan, et al. Network Security Situation Assessment Based on Improved WOA-SVM[J]. IEEE Access, 2022, 10: 96273-96283. |
| [17] | ACHARYA S, SIVARAJAN G, KUMAR D V, et al. Modeling Combined Economic Emission Dispatch for Renewable Energy System via Levy-Based Glowworm Swarm Optimization[J]. Kybernetes, 2023, 52(9): 3315-3337. |
| [18] | MIRJALILI S, LEWIS A. The Whale Optimization Algorithm[J]. Advances in Engineering Software, 2016, 95: 51-67. |
| [19] |
WEI Zihui, LI Xiaoyang, WANG Le, et al. Improved TDOA Three-Dimensional Positioning Algorithm Based on Adaptive Levy Flight[J]. Journal of Hebei University(Natural Science Edition), 2023, 43(2): 207-215.
doi: 10.3969/j.issn.1000-1565.2023.02.013 |
|
韦子辉, 李小阳, 王勒, 等. 基于自适应Levy飞行改进的TDOA三维定位算法[J]. 河北大学学报(自然科学版), 2023, 43(2): 207-215.
doi: 10.3969/j.issn.1000-1565.2023.02.013 |
|
| [20] | MIRJALILI S, MIRJALILI S M, LEWIS A. Grey Wolf Optimizer[J]. Advances in Engineering Software, 2014, 69(3): 46-61. |
| [21] | OZCAN E, MOHAN C K. Particle Swarm Optimization: Surfing the Waves[C]// IEEE. The 1999 Congress on Evolutionary Computation-CEC99. New York: IEEE, 1999: 1939-1944. |
| [22] | HE Qing, WEI Kangyuan, XU Qinshuai. Improved Whale Optimization Algorithm Based on Mixed Strategy[J]. Computer Application Research, 2019, 36(12): 3647-3651, 3665. |
| 何庆, 魏康园, 徐钦帅. 基于混合策略改进的鲸鱼优化算法[J]. 计算机应用研究, 2019, 36(12): 3647-3651,3665. | |
| [23] | TANG Yu, DAI Qi, YANG Zhiwei, et al. Research on Software Defect Prediction Algorithm Based on Optimized Random Forest[J]. Computer Engineering and Science, 2023, 45(5): 830-839. |
| 唐宇, 代琪, 杨志伟, 等. 基于优化随机森林的软件缺陷预测算法研究[J]. 计算机工程与科学, 2023, 45(5): 830-839. | |
| [24] | MANCHALA P, BISI M. Diversity Based Imbalance Learning Approach for Software Fault Prediction Using Machine Learning Models[EB/OL]. [2024-03-20]. https://www.sciencedirect.com/science/article/abs/pii/S1568494622003660?via%3Dihub. |
| [25] | SHIRABAD J S, MENZIES T J. The PROMISE Repository of Software Engineering Databases[EB/OL]. [2024-03-20]. https://www.mendeley.com/catalogue/016e9979-cca5-3f49-a0ac-abc6a86570ef/. |
| [26] | SHEPPERD M, SONG Qinbao, SUN Zhongbin, et al. Data Quality: Some Comments on the NASA Software Defect Datasets[J]. IEEE Transactions on Software Engineering, 2013, 39(9): 1208-1215. |
| [27] |
XIONG Zhongmin, GUO Huaiyu, WU Yuexin. Review of Research on Missing Data Processing Methods[J]. Computer Engineering and Applications, 2021, 57(14): 27-38.
doi: 10.3778/j.issn.1002-8331.2101-0187 |
|
熊中敏, 郭怀宇, 吴月欣. 缺失数据处理方法研究综述[J]. 计算机工程与应用, 2021, 57(14): 27-38.
doi: 10.3778/j.issn.1002-8331.2101-0187 |
| [1] | 王华忠, 田子蕾. 基于改进CGAN算法的工控系统入侵检测方法[J]. 信息网络安全, 2023, 23(1): 36-43. |
| [2] | 任涛, 金若辰, 罗咏梅. 融合区块链与联邦学习的网络入侵检测算法[J]. 信息网络安全, 2021, 21(7): 27-34. |
| [3] | 刘奕, 李建华, 张一瑫, 孟涛. 基于特征属性信息熵的网络异常流量检测方法[J]. 信息网络安全, 2021, 21(2): 78-86. |
| [4] | 胡建伟, 赵伟, 闫峥, 章芮. 基于机器学习的SQL注入漏洞挖掘技术的分析与实现[J]. 信息网络安全, 2019, 19(11): 36-42. |
| [5] | 和湘, 刘晟, 姜吉国. 基于机器学习的入侵检测方法对比研究[J]. 信息网络安全, 2018, 18(5): 1-11. |
| [6] | 宋金伟, 杨进, 李涛. 基于加权支持向量机的Domain Flux僵尸网络域名检测方法研究[J]. 信息网络安全, 2018, 18(12): 66-71. |
| [7] | 苏静, 路文玲, 赵毅强, 史艳翠. 基于支持向量机的硬件木马检测建模与优化[J]. 信息网络安全, 2017, 17(8): 33-38. |
| [8] | 张谦, 高章敏, 刘嘉勇. 基于Word2vec的微博短文本分类研究[J]. 信息网络安全, 2017, 17(1): 57-62. |
| [9] | 宋伟, 杨培, 于京, 姜薇. 基于视觉语义概念的暴恐视频检测[J]. 信息网络安全, 2016, 16(9): 12-17. |
| [10] | 张晓惠, 林柏钢. 基于平衡二叉决策树SVM算法的物联网安全研究[J]. 信息网络安全, 2015, 15(8): 20-25. |
| [11] | 戚名钰, 刘铭, 傅彦铭. 基于PCA的SVM网络入侵检测研究[J]. 信息网络安全, 2015, 15(2): 15-18. |
| [12] | . 基于区域性构建支持向量机模型的空域水印算法[J]. , 2014, 14(2): 32-. |
| [13] | 晁沛;周亚建. 基于区域性构建支持向量机模型的空域水印算法[J]. , 2014, 14(2): 0-0. |
| [14] | 宋健豪;赵刚;宋君易. 基于离线检测的SVMNIDS模式研究[J]. , 2012, 12(9): 0-0. |
| [15] | 黄华军;钱亮;王耀钧. 基于异常特征的钓鱼网站URL检测技术[J]. , 2012, 12(1): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||