信息网络安全 ›› 2024, Vol. 24 ›› Issue (6): 831-842.doi: 10.3969/j.issn.1671-1122.2024.06.002
SM9加密算法的颠覆攻击与改进
- 电子科技大学计算机科学与工程学院,成都 611731
-
收稿日期:2024-04-20出版日期:2024-06-10发布日期:2024-07-05 -
通讯作者:李发根fagenli@uestc.edu.cn -
作者简介:欧阳梦迪(1996—),女,四川,博士研究生,主要研究方向为抗大规模监控密码学|孙钦硕(2000—),男,辽宁,硕士研究生,主要研究方向为公钥密码学|李发根(1979—),男,四川,教授,博士,主要研究方向为公钥密码学 -
基金资助:国家自然科学基金(62272090)
Subversion Attacks and Countermeasures of SM9 Encryption
OUYANG Mengdi, SUN Qinshuo, LI Fagen( )
)
- Computer Science and Engineering College, University of Electronic Science and Technology of China, Chengdu 611731, China
-
Received:2024-04-20Online:2024-06-10Published:2024-07-05
摘要:
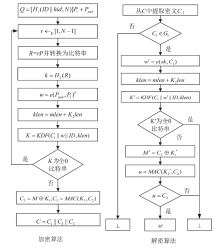
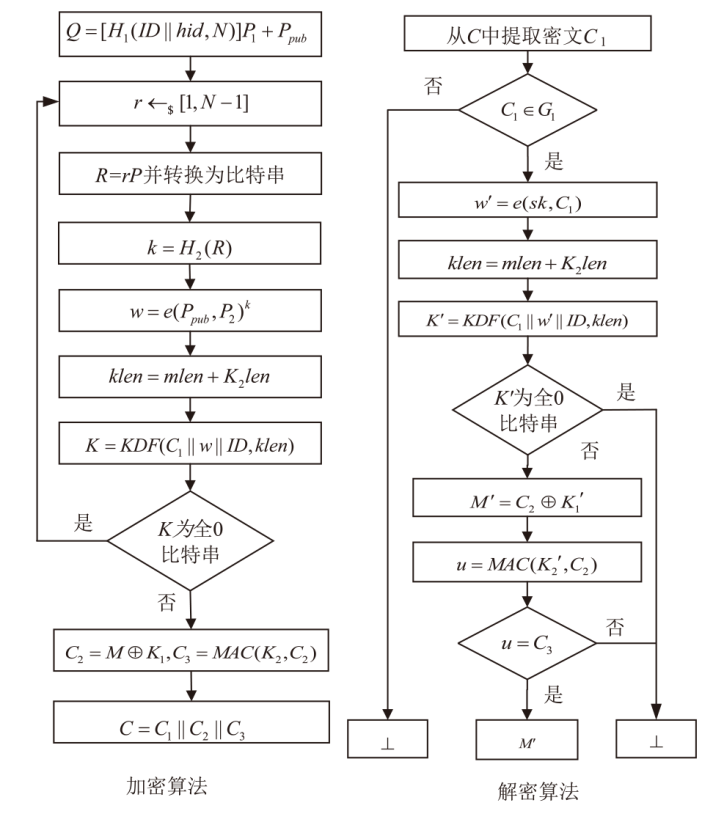
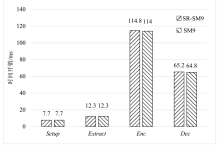
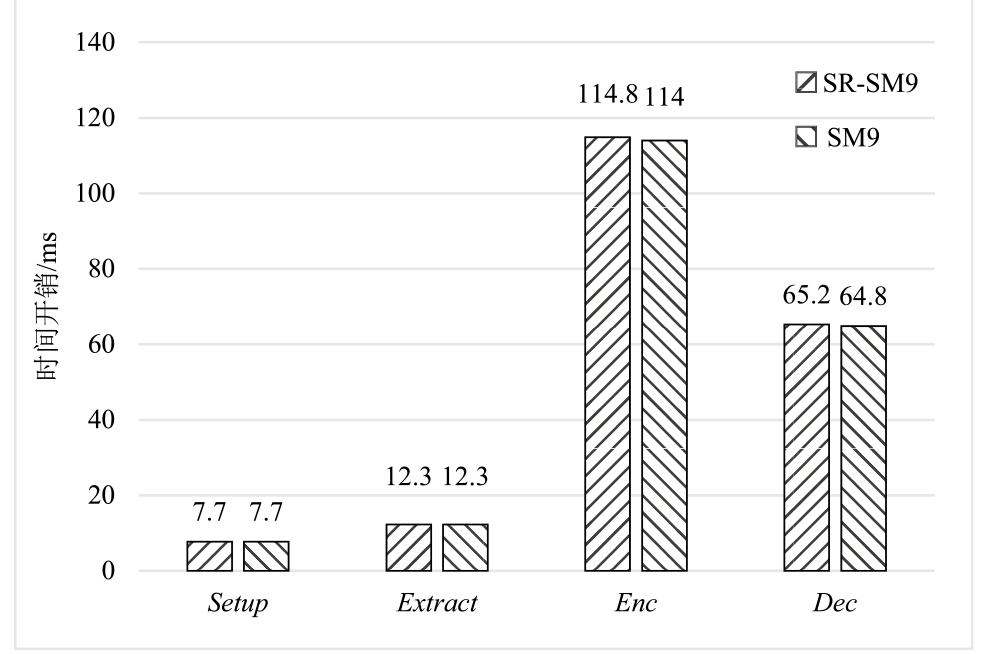
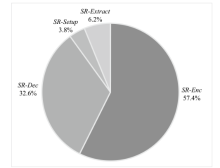
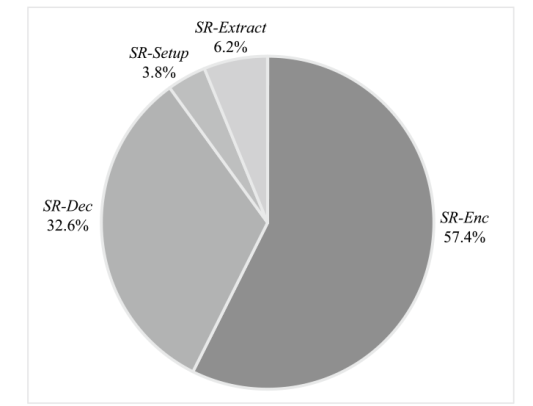
我国自主研发的基于标识的SM9加密算法已成功入选ISO/IEC国际标准,但敌手可以颠覆密码算法的组件,从而破坏算法的安全性,而SM9加密算法在设计之初并未考虑到此类攻击的存在。针对该问题,文章首先提出了基于标识加密(Identity Based Encryption,IBE)的颠覆攻击模型,并定义了明文可恢复性和不可检测性两个性质;然后提出了针对SM9加密算法的颠覆攻击,并发现敌手通过连续两个密文就能恢复明文;最后提出了抗颠覆的SM9加密算法(Subversion Resilient-SM9,SR-SM9),并证明其不仅满足适应性选择身份和密文攻击下的密文不可区分性,还能够抵抗颠覆攻击。文章基于gmalg库和Python语言测试了SR-SM9,测试结果显示,SR-SM9相比于SM9加密算法只增加0.6%的计算成本且未增加通信成本。
中图分类号:
引用本文
欧阳梦迪, 孙钦硕, 李发根. SM9加密算法的颠覆攻击与改进[J]. 信息网络安全, 2024, 24(6): 831-842.
OUYANG Mengdi, SUN Qinshuo, LI Fagen. Subversion Attacks and Countermeasures of SM9 Encryption[J]. Netinfo Security, 2024, 24(6): 831-842.
| [1] | SCHNEIER B, FREDRIKSON M, KOHNO T, et al. Surreptitiously Weakening Cryptographic Systems[EB/OL]. (2015-09-07)[2024-04-12]. https://eprint.iacr.org/2015/097. |
| [2] | WALD G. U.S. British Intelligence Mining Data from Nine U. S. Internet Companies[N]. Washington Post 2013-06-06(1). |
| [3] | DAVIS D. US Global Monitoring Action Record[N]. Xinhuanet, 2014-05-26(1). |
| [4] | YOUNG A, YUNG M. The Dark Side of “Black-Box” Cryptography or: Should We Trust Capstone?[C]// Springer. Advances in Cryptology-CRYPTO 1996. Heidelberg:Springer, 1996: 89-103. |
| [5] | YOUNG A. Kleptography: Using Cryptography against Cryptography[C]// Springer. Advances in Cryptology-EUROCRYPT 1997. Heidelberg:Springer, 1997: 62-74. |
| [6] | BELLARE M, PATERSON K G, ROGAWAY P. Security of Symmetric Encryption against Mass Surveillance[C]// Springer. Advances in Cryptology-CRYPTO 2014. Heidelberg: Springer, 2014: 1-19. |
| [7] | CHEN Rongmao, HUANG Xinyi, YUNG M. Subvert Kem to Break Dem: Practical Algorithm-Substitution Attacks on Public-Key Encryption[C]// Springer. Advances in Cryptology-ASIACRYPT 2020. Heidelberg: Springer, 2020: 98-128. |
| [8] | CHAKRABORTY S, MAGRI B, NIELSEN J B, et al. Universally Composable Subversion-Resilient Cryptography[C]// Springer. Advances in Cryptology-EUROCRYPT 2022. Heidelberg: Springer, 2022: 272-302. |
| [9] | ATENIESE G, MAGRI B, VENTURI D. Subversion-Resilient Signature Schemes[C]// Springer. Advances in Cryptology-EUROCRYPT 2022. Heidelberg: Springer, 2022: 272-302. |
| [10] | ARMOUR M, POETTERING B. Substitution Attacks against Message Authentication[J]. IACR Transactions on Symmetric Cryptology, 2019, 1(1): 152-168. |
| [11] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Advances in Cryptology-CRYPTO 1985. Heidelberg:Springer, 1985: 47-53. |
| [12] | SHANG Tao, ZHANG Feng, CHEN Xingyue, et al. Identity-Based Dynamic Data Auditing for Big Data Storage[J]. IEEE Transactions on Big Data, 2019, 7(6): 913-921. |
| [13] | LI Jiguo, HAO Yan, ZHANG Yichen. Efficient Identity-Based Provable Multi Copy Data Possession in Multi-Cloud Storage[J]. IEEE Transactions on Cloud Computing, 2019, 10(1): 356-365. |
| [14] | IEEE Std 1363.3-2013. Standard for Identity-Based Cryptographic Techniques Using Pairings[S]. New York: IEEE, 2013. |
| [15] | ISO/IEC 18033-5:2015. Information Technology-Security Techniques-Encryption Algorithms-Part 5: Identity-Based Ciphers[S]. New York: ISO/IEC, 2015. |
| [16] | GM/T0044-2016. SM9 Identity-Based Cryptographic Algorithm Part IV: Key Encapsulation Mechanism and Public Key Encryption Algorithm[S]. Beijing: Standards Press of China, 2016. |
| GM/T0044.4-2016. SM9标识密码算法第4部分:密钥封装机制和公钥加密算法[S]. 北京: 中国标准出版社, 2016. | |
| [17] | HUANG Xinyi, CHEN Rongmao, WANG Yi, et al. Key Exfiltration on SM2 Cryptographic Algorithms[J]. Journal of Cryptologic Research, 2021, 8(4): 684-698. |
| 黄欣沂, 陈荣茂, 王毅, 等. SM2密码算法密钥渗漏分析[J]. 密码学报, 2021, 8(4):684-698. | |
| [18] | DEGABRIELE J P, FARSHIM P, POETTERING B. A More Cautious Approach to Security Against Mass Surveillance[C]// Springer. In Fast Software Encryption-FSE. Heidelberg: Springer, 2015: 579-598. |
| [19] | BELLARE M, JAEGER J, KANE D. Mass-Surveillance without the State: Strongly Undetectable Algorithm-Substitution Attacks[C]// ACM. The 22nd ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2015: 1431-1440. |
| [20] | RUSSELL A, TANG Qiang, YUNG M, et al. Cliptography: Clipping the Power of Kleptographic Attacks[C]// Springer. Advances in Cryptology-ASIACRYPT 2016. Heidelberg: Springer, 2016: 34-64. |
| [21] | ARMOUR M, POETTERING B. Algorithm Substitution Attacks against Receivers[J]. International Journal of Information Security, 2022, 21(5): 1027-1050. |
| [22] | MIRONOV I, STEPHENS-DAVIDOWITZ N. Cryptographic Reverse Firewalls[C]// Springer. Advances in Cryptology-EUROCRYPT 2015. Heidelberg: Springer, 2015: 657-686. |
| [23] | SIMMONS G J. The Prisoners’ Problem and the Subliminal Channel[C]// Springer. Advances in Cryptology-CRYPTO 1984. Heidelberg:Springer, 1984: 51-67. |
| [24] | BERNDT S, LISKIEWICZ M. Algorithm Substitution Attacks from a Steganographic Perspective[C]// ACM. The 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1649-1660. |
| [25] | RUSSELL A, TANG Qiang, YUNG M, et al. Generic Semantic Security Against a Kleptographic Adversary[C]// ACM. The 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 907-922. |
| [26] | FISCHLIN M, MAZAHERI S. Self-Guarding Cryptographic Protocols Against Algorithm Substitution Attacks[C]// Springer. 2018 IEEE 31st Computer Security Foundations Symposium-CSF. Heidelberg: Springer, 2018: 76-90. |
| [27] | YAN Duli, YU Yong, LI Yannan, et al. Subversion Attack and Improvement of ECDSA Signature Scheme[J]. Journal of Software, 2023, 34(6): 2892-2905. |
| 严都力, 禹勇, 李艳楠, 等. ECDSA签名方案的颠覆攻击与改进[J]. 软件学报, 2023, 34(6):2892-2905. | |
| [28] | CHEN Rongmao, WANG Yi, HUANG Xinyi. RCCA-Secure Public-Key Encryption Based on SM2[J]. Science China: Information Sciences, 2023, 53(2): 266-281. |
| 陈荣茂, 王毅, 黄欣沂. 国密SM2加密算法的RCCA安全设计[J]. 中国科学:信息科学, 2023, 53(2):266-281. | |
| [29] | CHENG Zhaohui. Security Analysis of SM9 Key Agreement and Encryption[C]// Springer. Information Security and Cryptology:14th International Conference-Inscrypt 2018. Heidelberg: Springer, 2018: 14-17. |
| [30] | BENTAHAR K, FARSHIM P, MALONE-LEE J, et al. Generic Constructions of Identity-Based and Certificateless KEMs[J]. Journal of Cryptology, 2008, 21(1): 178-199. |
| [1] | 李增鹏, 王思旸, 王梅. 隐私保护近邻检测研究[J]. 信息网络安全, 2024, 24(6): 817-830. |
| [2] | 李强, 沈援海, 刘天旭, 黄晏瑜, 孙建国. 面向尺寸模式保护的高效对称可搜索加密方案[J]. 信息网络安全, 2024, 24(6): 843-854. |
| [3] | 杜育松, 江思维, 沈静, 张家豪. 一种抵御计时攻击的指数Bernoulli精确采样算法[J]. 信息网络安全, 2024, 24(6): 855-862. |
| [4] | 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. |
| [5] | 杨宇光, 刘冰心, 徐光宝, 姜东焕. 基于时间仓复用的高维量子密钥分发及应用[J]. 信息网络安全, 2024, 24(6): 879-892. |
| [6] | 丁勇, 罗世东, 杨昌松, 梁海. 基于SM9标识密码算法的可否认环签名方案[J]. 信息网络安全, 2024, 24(6): 893-902. |
| [7] | 叶清, 何俊霏, 杨智超. 基于格的可搜索公钥加密研究进展[J]. 信息网络安全, 2024, 24(6): 903-916. |
| [8] | 郭祥鑫, 林璟锵, 贾世杰, 李光正. 针对大语言模型生成的密码应用代码安全性分析[J]. 信息网络安全, 2024, 24(6): 917-925. |
| [9] | 白峻林, 尹华磊. 测量设备无关量子密钥分发中的改进型诱骗态方法[J]. 信息网络安全, 2024, 24(6): 926-936. |
| [10] | 胡丞聪, 胡红钢. 基于格的最优轮数口令认证秘密共享协议[J]. 信息网络安全, 2024, 24(6): 937-947. |
| [11] | 沈霞民, 熊涛, 李华, 沈璇. CLEFIA动态密码结构的零相关线性区分器构造研究[J]. 信息网络安全, 2024, 24(6): 948-958. |
| [12] | 朱敏, 肖昊. 一种面积高效的双态可配置NTT硬件加速器[J]. 信息网络安全, 2024, 24(6): 959-967. |
| [13] | 凌治, 杨明, 余江银. 基于IPFS和区块链技术的电力安全交易平台研究[J]. 信息网络安全, 2024, 24(6): 968-976. |
| [14] | 文伟平, 张世琛, 王晗, 时林. 基于虚拟机自省的Linux恶意软件检测方案[J]. 信息网络安全, 2024, 24(5): 657-666. |
| [15] | 李志华, 陈亮, 卢徐霖, 方朝晖, 钱军浩. 面向物联网Mirai僵尸网络的轻量级检测方法[J]. 信息网络安全, 2024, 24(5): 667-681. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||