信息网络安全 ›› 2024, Vol. 24 ›› Issue (11): 1739-1748.doi: 10.3969/j.issn.1671-1122.2024.11.013
基于布隆过滤器查找树的日志数据区块链溯源机制
- 中国刑事警察学院公安信息技术与情报学院,沈阳 110035
-
收稿日期:2024-04-25出版日期:2024-11-10发布日期:2024-11-21 -
通讯作者:罗文华luowenhua770404@126.com -
作者简介:张鹏(2001—),男,山东,硕士研究生,CCF会员,主要研究方向为网络安全执法|罗文华(1977—),男,辽宁,教授,硕士,主要研究方向为网络安全执法 -
基金资助:国家重点研发计划(2021YFC3301801)
Blockchain-Based Log Data Provenance Mechanism Using Bloom Filter Search Tree
- School of Public Security Information Technology and Intelligence, Criminal Investigation Police University of China, Shenyang 110035, China
-
Received:2024-04-25Online:2024-11-10Published:2024-11-21
摘要:
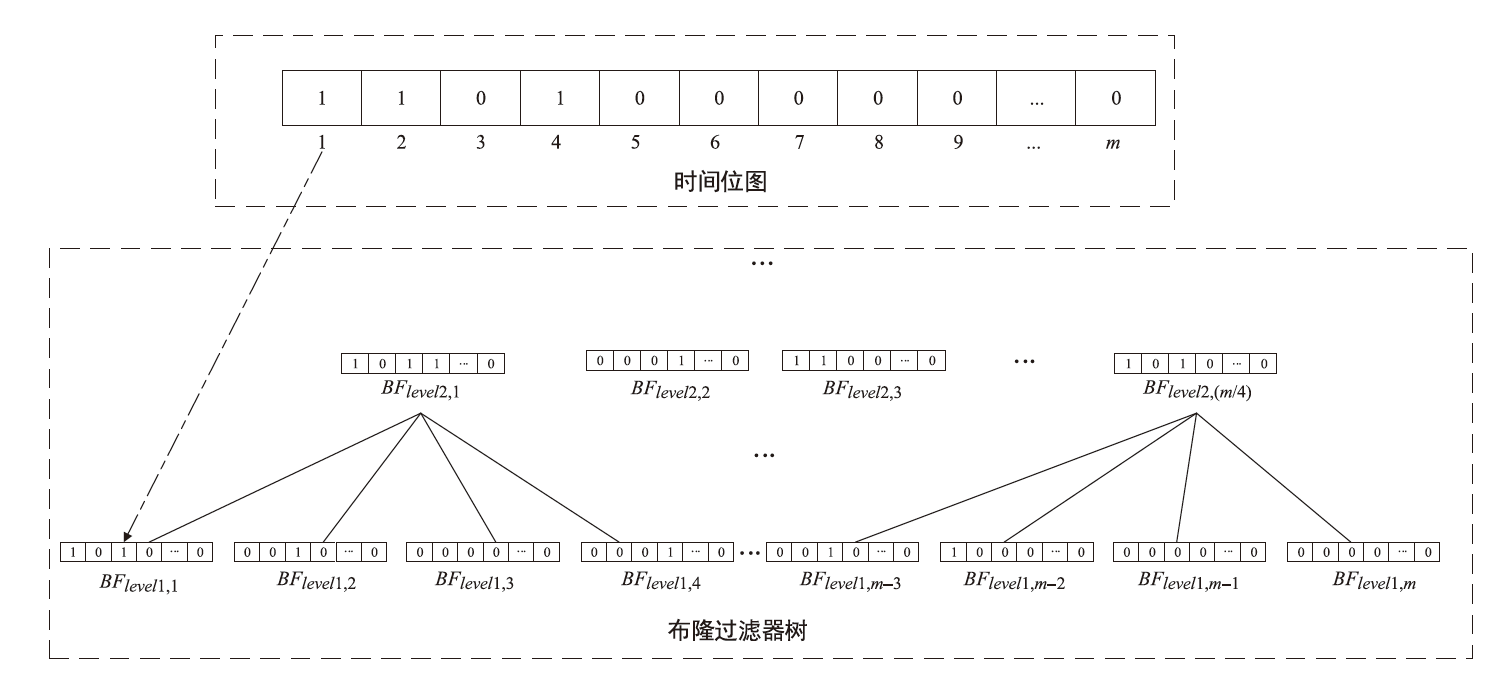
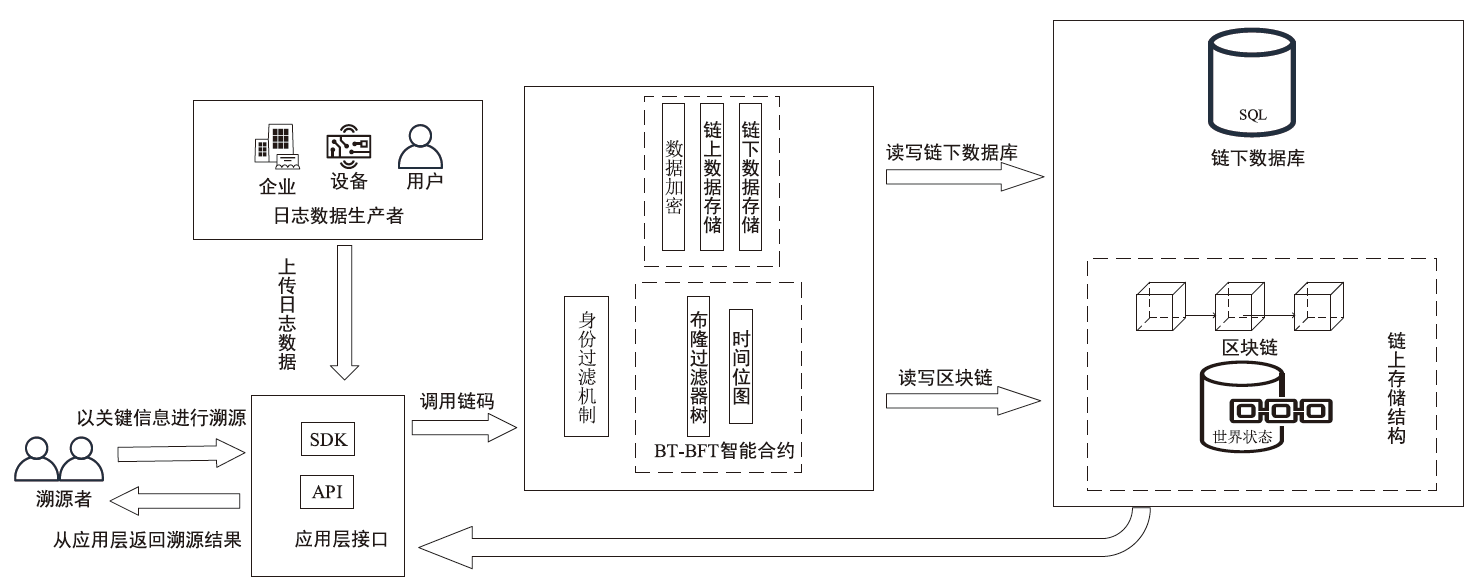
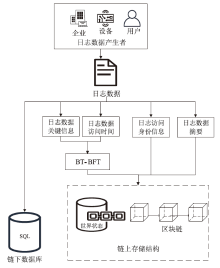
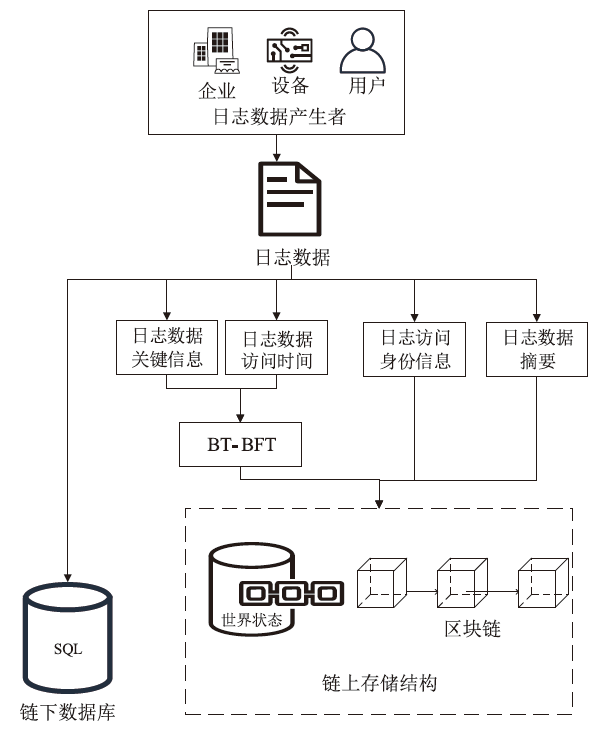
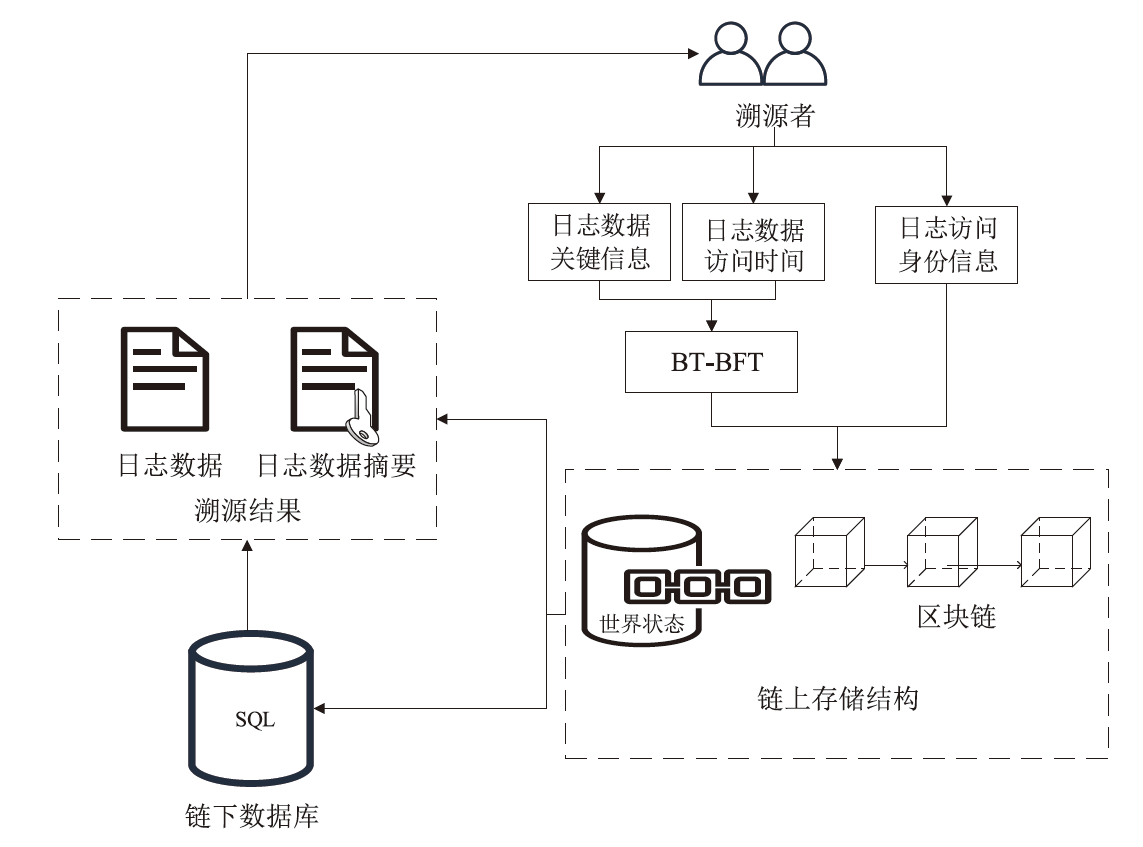
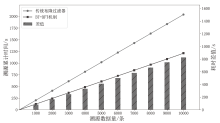
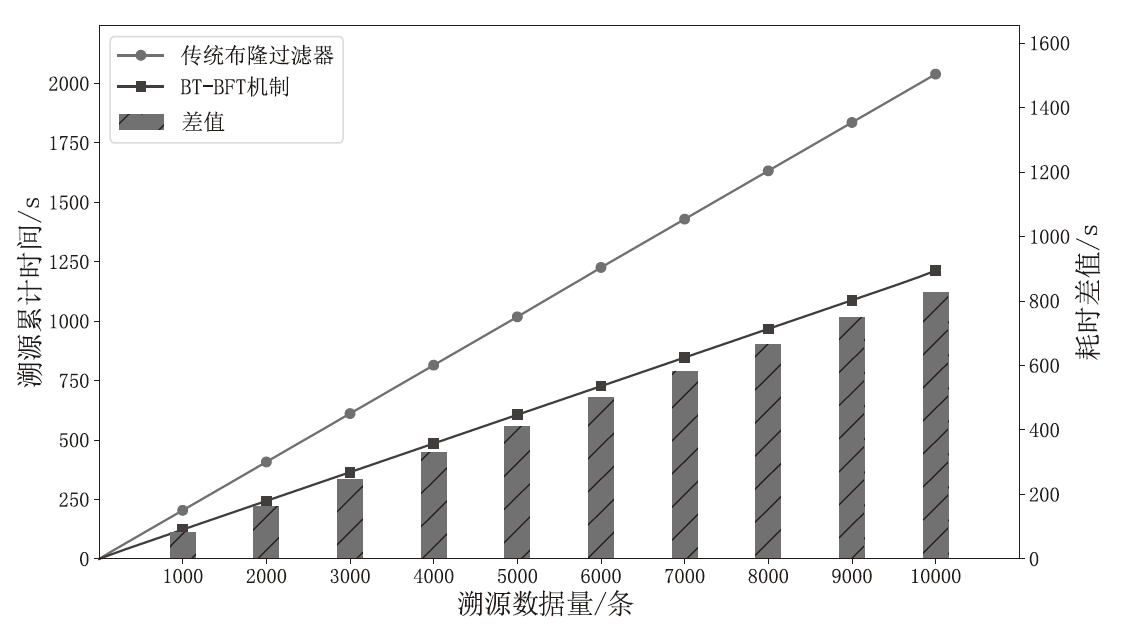
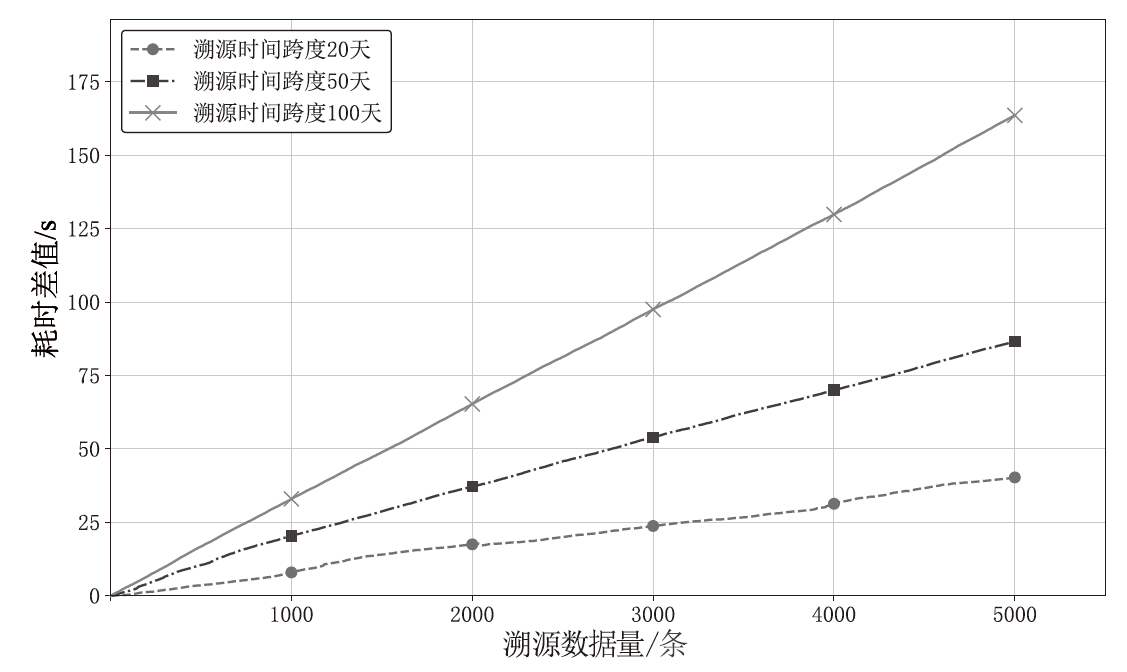
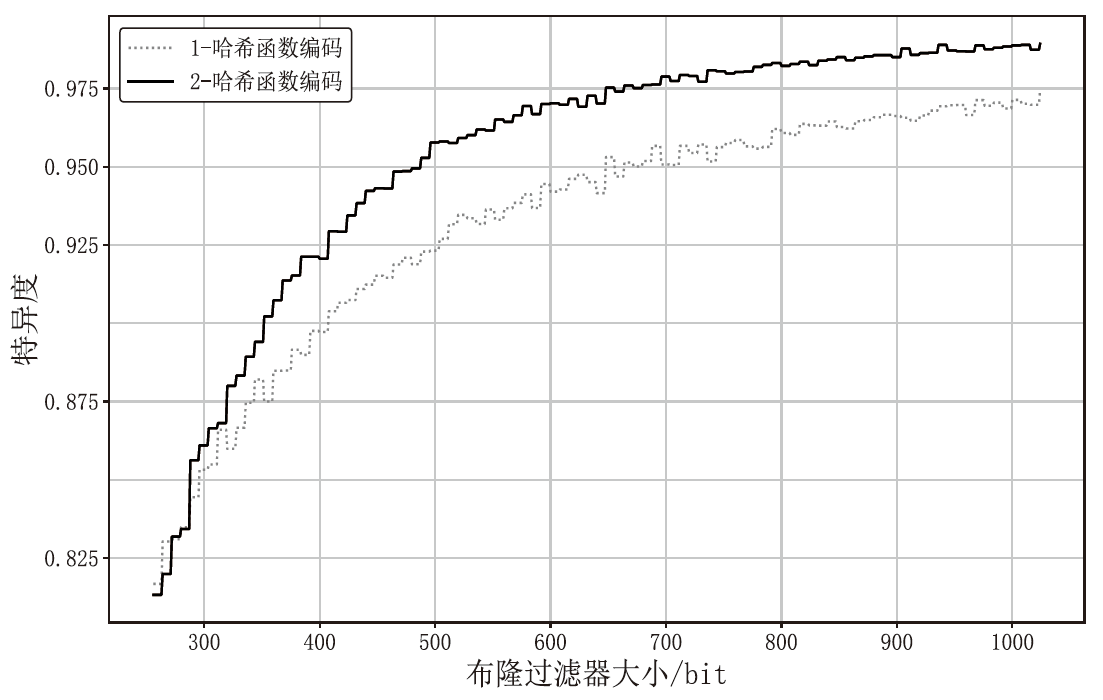
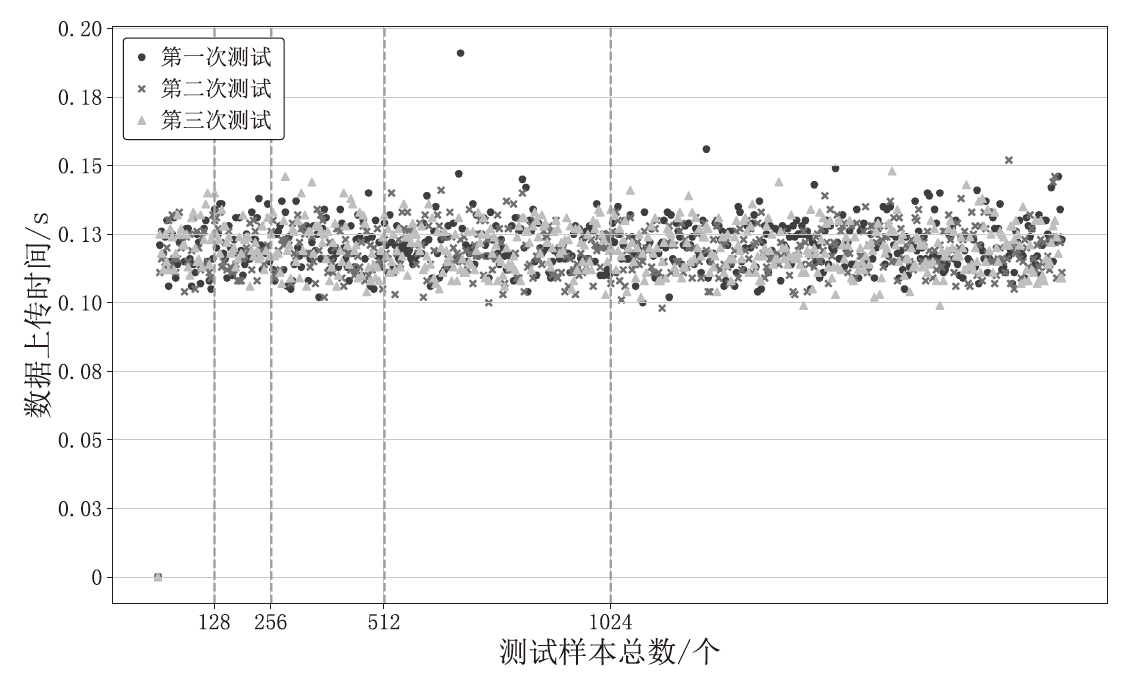
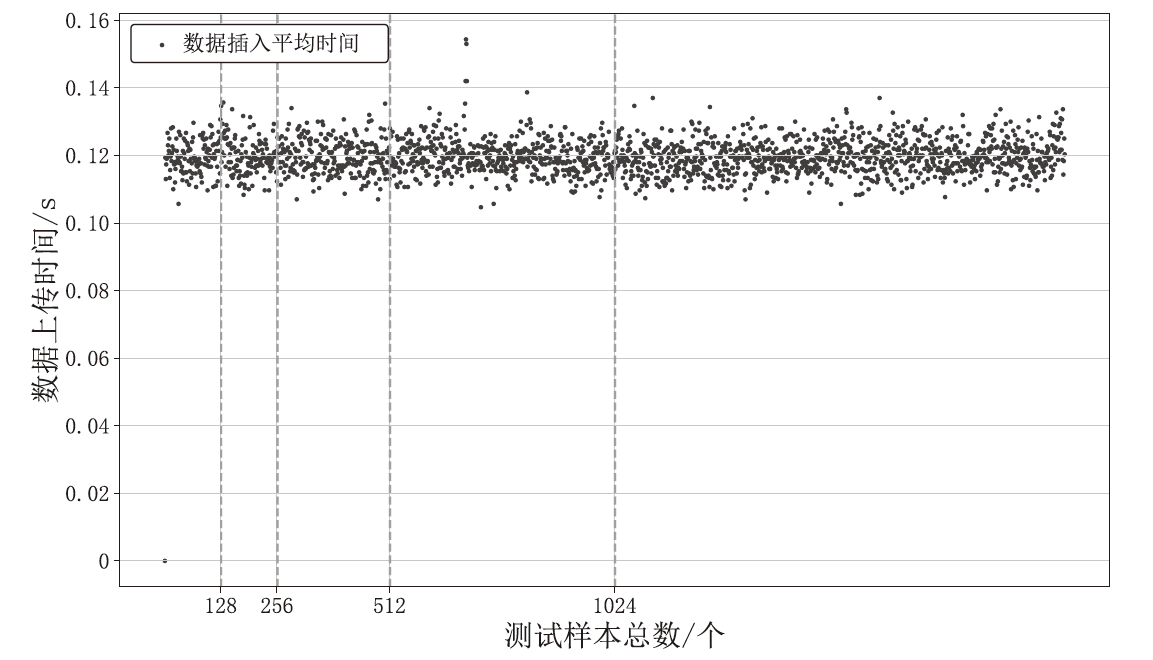
针对现有溯源机制在处理日志数据时的不足,文章提出一种基于布隆过滤器查找树的日志数据区块链溯源机制。该机制采用链上摘要与链下数据相结合的存储模式,以保证数据的安全性与隐私性。针对链上摘要,文章提出一种以访问时间为核心索引信息的BT-BFT机制,将时间戳通过位图进行索引,利用布隆过滤器实现日志数据分析粒度的刻画,并构造均衡分布的树状结构,从而高效映射和索引时间维度的数据。该机制通过智能合约的形式进行部署,有效排查非目标溯源节点,支持时间戳溯源和基于关键词的全时段溯源,并引入身份过滤机制,以应对布隆过滤器固有的冲突问题。实验结果表明,文章所提机制能够在保证数据安全的前提下,高效且准确地对时间敏感类数据进行溯源。
中图分类号:
引用本文
张鹏, 罗文华. 基于布隆过滤器查找树的日志数据区块链溯源机制[J]. 信息网络安全, 2024, 24(11): 1739-1748.
ZHANG Peng, LUO Wenhua. Blockchain-Based Log Data Provenance Mechanism Using Bloom Filter Search Tree[J]. Netinfo Security, 2024, 24(11): 1739-1748.
| [1] | QI Wenhao, SUN Meng, HOSSEINI S R A. Facilitating Big-Data Management in Modern Business and Organizations Using Cloud Computing: A Comprehensive Study[J]. Journal of Management & Organization, 2023, 29(4): 697-723. |
| [2] | DUGGINENI S. Impact of Controls on Data Integrity and Information Systems[J]. Science and Technology, 2023, 13(2): 29-35. |
| [3] | SUN Nan, DING Ming, JIANG Jiaojiao, et al. Cyber Threat Intelligence Mining for Proactive Cybersecurity Defense: A Survey and New Perspectives[J]. IEEE Communications Surveys & Tutorials, 2023, 25(3): 1748-1774. |
| [4] | YANG Lisheng, LUO Wenhua. Data Poisoning Defense Based on Sample Distribution Characteristics[J]. Application Research of Computers, 2023, 40(9): 2845-2850. |
| 杨立圣, 罗文华. 基于样本分布特征的数据投毒防御[J]. 计算机应用研究, 2023, 40(9):2845-2850. | |
| [5] | SQUAREPANTS S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2024-03-01]. https://bitcoin.org/en/bitcoin-paper. |
| [6] | YANG Lisheng, LUO Wenhua. Tri-BERT-SENet: Multi-feature Fusion for Malicious Webpage Detection[J]. Small Micro Computer Systems, 2023, 44(4): 875-880. |
| 杨立圣, 罗文华. Tri-BERT-SENet:融合多特征的恶意网页识别[J]. 小型微型计算机系统, 2023, 44(4): 875-880. | |
| [7] | LIU Aodi, DU Xuehui, WANG Na, et al. Research Progress on Blockchain System Security Technolog[J]. Chinese Journal of Computers, 2024, 47(3): 608-646. |
| 刘敖迪, 杜学绘, 王娜, 等. 区块链系统安全防护技术研究进展[J]. 计算机学报, 2024, 47(3): 608-646. | |
| [8] | SI Honghao, NIU Baoning. Research on Blockchain Data Availability and Storage Scalability[EB/OL]. (2023-06-12)[2024-03-01]. https://doi.org/10.3390/fi15060212. |
| [9] | XU Yang, XIAO Shihao, WANG Huiling, et al. Redactable Blockchain-Based Secure and Accountable Data Management[J]. IEEE Transactions on Network and Service Management, 2024, 21(2): 1764-1776. |
| [10] | SARANYA R, MURUGAN A. A Systematic Review of Enabling Blockchain in Healthcare System: Analysis, Current Status, Challenges and Future Direction[J]. Materials Today: Proceedings, 2023, 80(3): 3010-3015. |
| [11] | RAIMUNDO R, ROSÁRIO A. Blockchain System in the Higher Education[J]. European Journal of Investigation in Health, Psychology and Education, 2021, 11(1): 276-293. |
| [12] | ZHOU Yuanjian, QIN Dongmei, LIU Yining, et al. Design of Electronic Warehouse Receipts System Based on Blockchain[J]. Netinfo Security, 2019, 19(6): 84-90. |
| 周元健, 秦冬梅, 刘忆宁, 等. 基于区块链的可信仓单系统设计[J]. 信息网络安全, 2019, 19(6): 84-90. | |
| [13] | DARAGHMI E Y, DARAGHMI Y A, YUAN S M. MedChain: A Design of Blockchain-Based System for Medical Records Access and Permissions Management[J]. IEEE Access, 2019, 7(1): 164595-164613. |
| [14] |
XIE Rongna, LI Hui, SHI Guozhen, et al. Blockchain-Based Access Control Mechanism for Data Traceability[J]. Journal on Communications, 2020, 41(12): 82-93.
doi: 10.11959/j.issn.1000-436X.2020232 |
|
谢绒娜, 李晖, 史国振, 等. 基于区块链的可溯源访问控制机制[J]. 通信学报, 2020, 41(12): 82-93.
doi: 10.11959/j.issn.1000-436X.2020232 |
|
| [15] | POURMAJIDI W, MIRANSKYY A. Logchain: Blockchain-Assisted Log Storage[C]// IEEE. 2018 IEEE 11th International Conference on Cloud Computing. New York: IEEE, 2018: 978-982. |
| [16] | YANG Xinting, LI Mengqi, YU Huajing, et al. A Trusted Blockchain-Based Traceability System for Fruit and Vegetable Agricultural Products[J]. IEEE Access, 2021, 9(1): 36282-36293. |
| [17] | SHEKHTMAN L, WAISBARD E. EngraveChain: A Blockchain-Based Tamper-Proof Distributed Log System[J]. Future Internet, 2021, 13(6): 143-157. |
| [18] | REN Hao, XU Guowen, QI Han, et al. PriFR: Privacy-Preserving Large-Scale File Retrieval System via Blockchain for Encrypted Cloud Data[C]// IEEE. 2023 IEEE 9th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS). New York: IEEE, 2023: 16-23. |
| [19] | YAO Zhongming, XIN Junchang, HAO Kun, et al. Learned-Index-Based Semantic Keyword Query on Blockchain[J]. Mathematics, 2023, 11(9): 1-19. |
| [20] | BLOOM B H. Space/Time Trade-Offs in Hash Coding with Allowable Errors[J]. Communications of the ACM, 1970, 13(7): 422-426. |
| [21] | AIGISSINOVA A, LE H H, YOKOTA H. Evaluation of the Performance of Secure Keyword Search Using Bit-String Signatures in the Blockchain[J]. DEIM Forum, 2020, E1(5): 1-8. |
| [22] | XU Gang, YUN Fan, XU Shiyuan, et al. A Blockchain-Based Log Storage Model with Efficient Query[J]. Soft Computing, 2023, 27(19): 13779-13787. |
| [23] |
LYU Jianfu, LAI Yingxu, LIU Jing. Log Security Storage and Retrieval Based on Combination of on-Chain and off-Chain[J]. Computer Science, 2020, 47(3): 298-303.
doi: 10.11896/jsjkx.190200298 |
|
吕建富, 赖英旭, 刘静. 基于链上链下相结合的日志安全存储与检索[J]. 计算机科学, 2020, 47(3): 298-303.
doi: 10.11896/jsjkx.190200298 |
|
| [24] | ZHU Jieming, HE Shilin, HE Pinjia, et al. Loghub: A Large Collection of System Log Datasets for AI-Driven Log Analytics[C]// IEEE. 2023 IEEE 34th International Symposium on Software Reliability Engineering (ISSRE). New York: IEEE, 2023: 355-366. |
| [1] | 余礼苏, 李彪, 姚元志, 温家进, 黎子鹏, 王振. 区块链辅助无人机移动边缘计算系统的性能优化[J]. 信息网络安全, 2024, 24(9): 1432-1443. |
| [2] | 吕秋云, 周凌飞, 任一支, 周士飞, 盛春杰. 一种全生命周期可控的公共数据共享方案[J]. 信息网络安全, 2024, 24(8): 1291-1305. |
| [3] | 张继威, 王文俊, 牛少彰, 郭向阔. 区块链扩展解决方案:ZK-Rollup综述[J]. 信息网络安全, 2024, 24(7): 1027-1037. |
| [4] | 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. |
| [5] | 凌治, 杨明, 余江银. 基于IPFS和区块链技术的电力安全交易平台研究[J]. 信息网络安全, 2024, 24(6): 968-976. |
| [6] | 田钊, 牛亚杰, 佘维, 刘炜. 面向车联网的车辆节点信誉评估方法[J]. 信息网络安全, 2024, 24(5): 719-731. |
| [7] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [8] | 胡海洋, 刘畅, 王栋, 魏旭. 基于区块链的清洁能源数据溯源机制[J]. 信息网络安全, 2024, 24(4): 626-639. |
| [9] | 薛茗竹, 胡亮, 王明, 王峰. 基于联邦学习和区块链技术的TAP规则处理系统[J]. 信息网络安全, 2024, 24(3): 473-485. |
| [10] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [11] | 何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238. |
| [12] | 兰浩良, 王群, 徐杰, 薛益时, 张勃. 基于区块链的联邦学习研究综述[J]. 信息网络安全, 2024, 24(11): 1643-1654. |
| [13] | 王南, 袁也, 杨浩然, 文周之, 苏明, 刘晓光. 环保大数据在区块链中的隐私计算[J]. 信息网络安全, 2024, 24(10): 1515-1527. |
| [14] | 吴昊天, 李一凡, 崔鸿雁, 董琳. 基于零知识证明和区块链的联邦学习激励方案[J]. 信息网络安全, 2024, 24(1): 1-13. |
| [15] | 朱郭诚, 何德彪, 安浩杨, 彭聪. 基于区块链和SM9数字签名的代理投票方案[J]. 信息网络安全, 2024, 24(1): 36-47. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||