信息网络安全 ›› 2024, Vol. 24 ›› Issue (10): 1604-1610.doi: 10.3969/j.issn.1671-1122.2024.10.015
ARP欺骗攻击与硬件防御研究
- 1.河南省计量测试科学研究院,郑州 450008
2.郑州大学国家超级计算郑州中心,郑州 450001
-
收稿日期:2024-06-05出版日期:2024-10-10发布日期:2024-09-27 -
通讯作者:于哲,13501015514@139.com -
作者简介:何开宇(1971—),男,河南,高级工程师,主要研究方向为计量技术及管理、电子与机械|王彬(1988—),男,河南,硕士,主要研究方向为数字集成电路设计、网络安全|于哲(1976—),男,北京,副研究员,博士,主要研究方向为集成电路设计、网络与存储安全、密码算法|陈方(1989—),男,湖北,工程师,主要研究方向为数字集成电路、网络安全
Research on ARP Spoofing Attack and Hardware Defense
HE Kaiyu1, WANG Bin2, YU Zhe2( ), CHEN Fang2
), CHEN Fang2
- 1. Henan Institute of Metrology and Testing Science, Zhengzhou 450008, China
2. National Supercomputing Center in Zhengzhou, Zhengzhou University, Zhengzhou 450001, China
-
Received:2024-06-05Online:2024-10-10Published:2024-09-27
摘要:
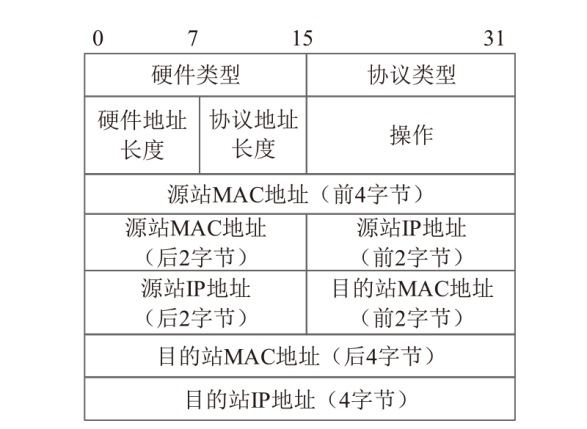
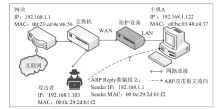
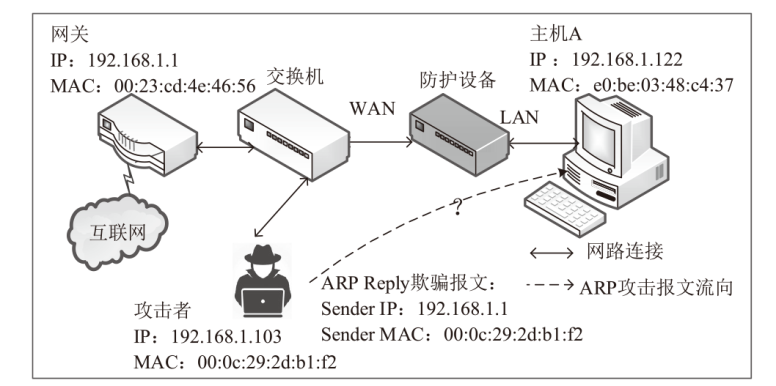
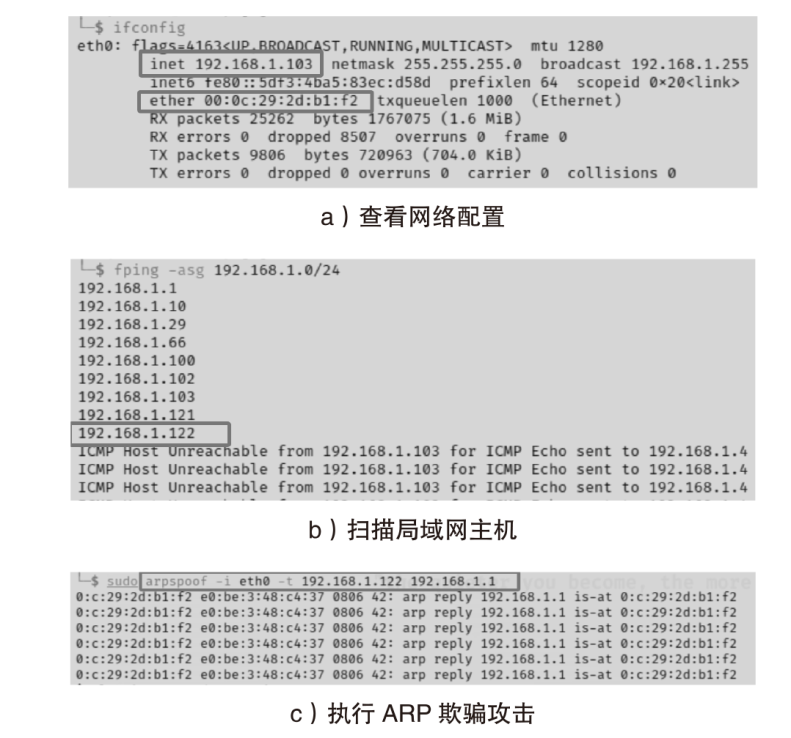
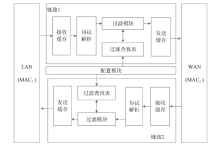
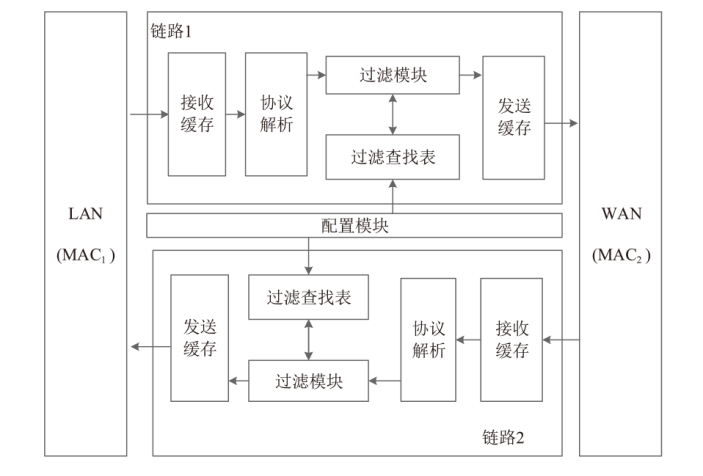
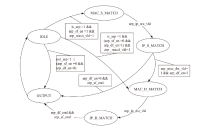
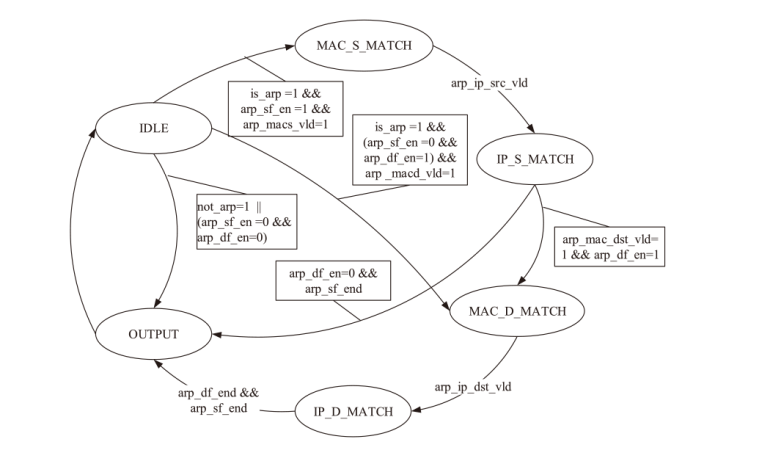
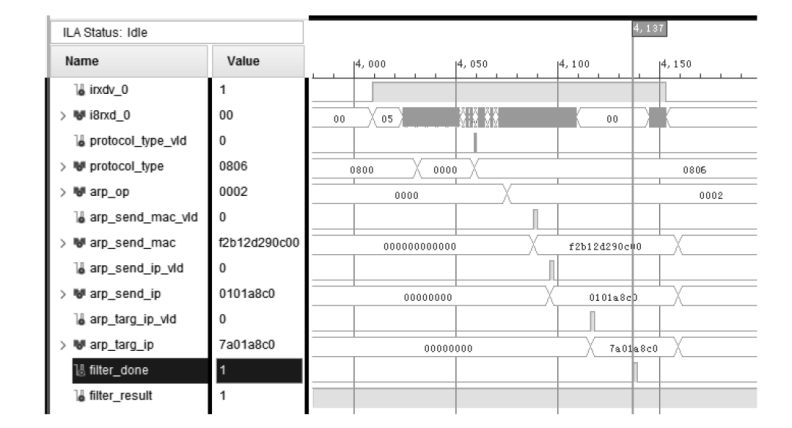
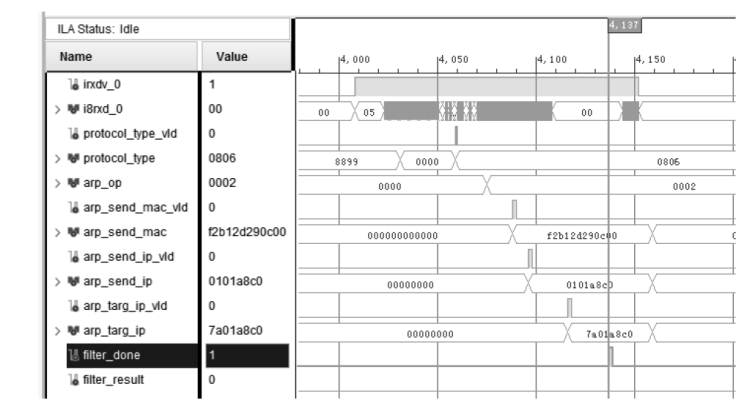
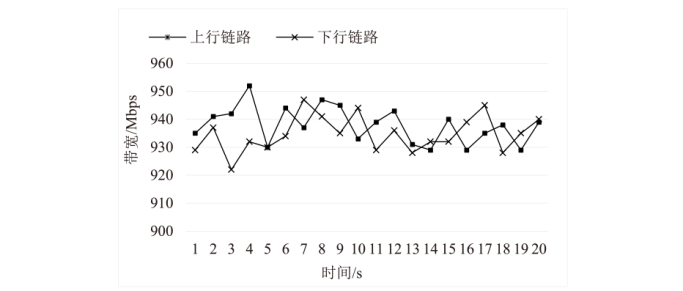
针对现有ARP欺骗攻击防御手段配置繁琐、成本高昂等问题,文章设计了基于FPGA的硬件防御设备并在真实网络环境中进行了测试。首先搭建真实的局域网环境,利用arpspoof工具对局域网中的目标主机实施ARP欺骗攻击;然后设计了基于FPGA平台的网络安全防御设备,通过对上下行链路中的网络报文进行解析,并与设置的安全防御策略相应报文的字段进行比对过滤,实现对ARP欺骗报文的识别与过滤;最后将网络安全防御设备接入局域网,并通过VIVADO的ILA抓取ARP欺骗攻击报文的相关字段波形。波形数据表明,网络安全防御设备可有效识别ARP欺骗攻击报文的MAC地址和IP地址等内容并实施有效拦截,同时可对接入系统的网络链路带宽、攻击拦截率和被攻击主机系统资源使用率进行统计。
中图分类号:
引用本文
何开宇, 王彬, 于哲, 陈方. ARP欺骗攻击与硬件防御研究[J]. 信息网络安全, 2024, 24(10): 1604-1610.
HE Kaiyu, WANG Bin, YU Zhe, CHEN Fang. Research on ARP Spoofing Attack and Hardware Defense[J]. Netinfo Security, 2024, 24(10): 1604-1610.
| [1] | ZHANG Feng, YU Xiumin, BAO Juan. Research on Campus Network Preventing ARP Spoofing[J]. Journal of Dalian University, 2019, 40(3): 10-14. |
| 张峰, 于秀敏, 包娟. 高校校园网防ARP欺骗的研究[J]. 大连大学学报, 2019, 40(3):10-14. | |
| [2] | QIU Hong, SHI Junyu, TU Qiuyue. A Brief Analysis of ARP Attack and Protection in LAN[J]. Computer & Network, 2021, 47(1): 56-59. |
| 仇虹, 施俊宇, 涂秋月. 浅析局域网内ARP攻击与防护[J]. 计算机与网络, 2021, 47(1):56-59. | |
| [3] | LIU Lang. Analysis and Practice of ARP Virus Spoofing[J]. Network Security and Informatization, 2022(10): 153-155. |
| 刘浪. 关于ARP病毒欺骗的分析与实践[J]. 网络安全和信息化, 2022(10):153-155. | |
| [4] | LIN Chenyu, CHEN Jun. ARP Protocol Analysis and Research on Attack and Defense Technology[J]. Journal of Xiangyang Polytechnic, 2023, 22(3): 104-109. |
| 林晨钰, 陈俊. ARP协议分析及攻防技术研究[J]. 襄阳职业技术学院学报, 2023, 22(3):104-109. | |
| [5] |
XIA Jing, CAI Zhiping, HU Gang, et al. An Active Defense Solution for ARP Spoofing in OpenFlow Network[J]. Chinese Journal of Electronics, 2019, 28(1): 172-178.
doi: 10.1049/cje.2017.12.002 |
| [6] | FIESSLER A, LORENZ C, HAGER S, et al. HyPaFilter+: Enhanced Hybrid Packet Filtering Using Hardware Assisted Classification and Header Space Analysis[J]. IEEE/ACM Transactions on Networking, 2017, 25(6): 3655-3669. |
| [7] | TANG Dengping, WANG Jin, XIAO Guangdi. ARP Protocol Principle Simulation Experiment Design and Implementation[J]. Laboratory Research and Exploration, 2016, 35(12): 126-129. |
| 唐灯平, 王进, 肖光娣. ARP协议原理仿真实验的设计与实现[J]. 实验室研究与探索, 2016, 35(12):126-129. | |
| [8] | WANG Yongsheng. ARP Attack Principle and Defense Measures[J]. Digital Technology & Application, 2020, 38(2): 181-182. |
| 汪永生. ARP攻击原理与防御措施[J]. 数字技术与应用, 2020, 38(2):181-182. | |
| [9] | ZHOU Chuang, WANG Honglin. ARP Spoofing Prevention Technology Based on SDN[J]. Journal of Chongqing University of Science and Technology (Natural Sciences Edition), 2019, 21(1): 100-103. |
| 周创, 王红林. 基于SDN的ARP欺骗防范技术[J]. 重庆科技学院学报(自然科学版), 2019, 21(1):100-103. | |
| [10] | KE Cai. Analysis and Research of Network Monitoring Based on ARP Spoofing[J]. Electronic Design Engineering, 2020, 28(13): 124-127. |
| 柯采. 基于ARP欺骗的网络监听分析与研究[J]. 电子设计工程, 2020, 28(13):124-127. | |
| [11] | MORSY S M, NASHAT D. D-ARP: An Efficient Scheme to Detect and Prevent ARP Spoofing[J]. IEEE Access, 2022, 10: 49142-49153. |
| [12] | HU Zhiming. Research on Man-in-the-Middle Attack and Defense Technology Based on ARP Deception[J]. Information Technology and Informatization, 2020(12): 111-114. |
| 胡志明. 基于ARP欺骗的中间人攻击与防御技术研究[J]. 信息技术与信息化, 2020(12):111-114. | |
| [13] | ZHAO Jing. Research on Man-in-the-Middle Attacks Based on ARP Deception and Countermeasures[J]. Network Security Technology & Application, 2021(3): 6-8. |
| 赵菁. 基于ARP欺骗的中间人攻击及防范对策研究[J]. 网络安全技术与应用, 2021(3):6-8. | |
| [14] | LI Zhaobin, MAO Fangyi, WANG Yaojun, et al. Application of Scapy in Network Equipment Safety Testing[J]. Journal of Beijing Electronic Science and Technology Institute, 2016, 24(4): 73-77. |
| 李兆斌, 茅方毅, 王瑶君, 等. Scapy在网络设备安全性测试中的应用[J]. 北京电子科技学院学报, 2016, 24(4):73-77. | |
| [15] | BIAN Zhonghao, TIAN Ye, SI Yi, et al. Hardware Circuit Design of Network Acceleration Card Based on FPGA[J]. Communications Technology, 2021, 54(6): 1521-1528. |
| 卞中昊, 田野, 司艺, 等. 基于FPGA的多端口网络协议解析加速卡硬件电路设计[J]. 通信技术, 2021, 54(6):1521-1528. | |
| [16] | QU Chenxin, DI Zhixiong, TIAN Shuo, et al. Design and Implementation of Ethernet MAC Layer Switch Based on FPGA[J]. Information Technology and Informatization, 2021(5): 217-219. |
| 屈晨昕, 邸志雄, 田硕, 等. 基于FPGA的以太网MAC层交换机设计与实现[J]. 信息技术与信息化, 2021(5):217-219. | |
| [17] | REN Yongfeng, SHANG Chenyang. Design of Gigabit Ethernet Interface IP Core Based on FPGA[J]. Microcontrollers & Embedded Systems, 2022, 22(11): 49-53. |
| 任勇峰, 尚辰阳. FPGA千兆以太网接口的IP核设计[J]. 单片机与嵌入式系统应用, 2022, 22(11):49-53. |
| [1] | 问闻, 刘钦菊, 邝琳, 任雪静. 隐私保护体系下网络威胁情报共享的研究现状和方案设计[J]. 信息网络安全, 2024, 24(7): 1129-1137. |
| [2] | 张长琳, 仝鑫, 佟晖, 杨莹. 面向网络安全领域的大语言模型技术综述[J]. 信息网络安全, 2024, 24(5): 778-793. |
| [3] | 杨志鹏, 刘代东, 袁军翼, 魏松杰. 基于自注意力机制的网络局域安全态势融合方法研究[J]. 信息网络安全, 2024, 24(3): 398-410. |
| [4] | 李娇, 张玉清, 吴亚飚. 面向网络安全关系抽取的大语言模型数据增强方法[J]. 信息网络安全, 2024, 24(10): 1477-1483. |
| [5] | 付静. 水利关键信息基础设施安全保护探索与实践[J]. 信息网络安全, 2023, 23(8): 121-127. |
| [6] | 孙珵珵. 网络安全治理对策研究[J]. 信息网络安全, 2023, 23(6): 104-110. |
| [7] | 王晓狄, 黄诚, 刘嘉勇. 面向网络安全开源情报的知识图谱研究综述[J]. 信息网络安全, 2023, 23(6): 11-21. |
| [8] | 李冬, 于俊清, 文瑞彬, 谢一丁. 基于IPv6的容器云内生安全机制[J]. 信息网络安全, 2023, 23(12): 21-28. |
| [9] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [10] | 孙鹏宇, 谭晶磊, 李晨蔚, 张恒巍. 基于时间微分博弈的网络安全防御决策方法[J]. 信息网络安全, 2022, 22(5): 64-74. |
| [11] | 金波, 唐前进, 唐前临. CCF计算机安全专业委员会2022年网络安全十大发展趋势解读[J]. 信息网络安全, 2022, 22(4): 1-6. |
| [12] | 李莉, 李泽群, 李雪梅, 史国振. 基于交叉耦合电路的物理不可克隆函数FPGA实现[J]. 信息网络安全, 2022, 22(3): 53-61. |
| [13] | 陈妍, 韦湘, 陆臻. 云计算环境下网络安全产品检测方法研究[J]. 信息网络安全, 2022, 22(12): 1-6. |
| [14] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [15] | 白宏鹏, 邓东旭, 许光全, 周德祥. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||