信息网络安全 ›› 2023, Vol. 23 ›› Issue (7): 44-52.doi: 10.3969/j.issn.1671-1122.2023.07.005
面向区块链金融的抗量子属性基门限环签密方案
- 1.西安邮电大学网络空间安全学院,西安 710121
2.暨南大学网络空间安全学院,广州 510632
-
收稿日期:2023-03-27出版日期:2023-07-10发布日期:2023-07-14 -
通讯作者:俞惠芳 yuhuifang@xupt.edu.cn -
作者简介:俞惠芳(1972—),女,青海,教授,博士,CCF高级会员,主要研究方向为密码理论与信息安全|乔一凡(1997—),男,陕西,硕士研究生,主要研究方向为格密码理论与区块链隐私保护|孟茹(1993—),女,陕西,博士研究生,主要研究方向为密码理论与身份认证 -
基金资助:陕西省自然科学基础研究重点项目(2020JZ-54)
Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance
YU Huifang1( ), QIAO Yifan1, MENG Ru2
), QIAO Yifan1, MENG Ru2
- 1. School of Cyberspace Security, Xi’an University of Posts & Telecommunications, Xi’an 710121, China
2. School of Cyberspace Security, Jinan University, Guangzhou 510632, China
-
Received:2023-03-27Online:2023-07-10Published:2023-07-14
摘要:
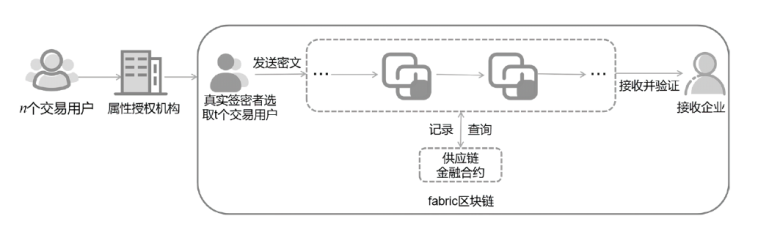
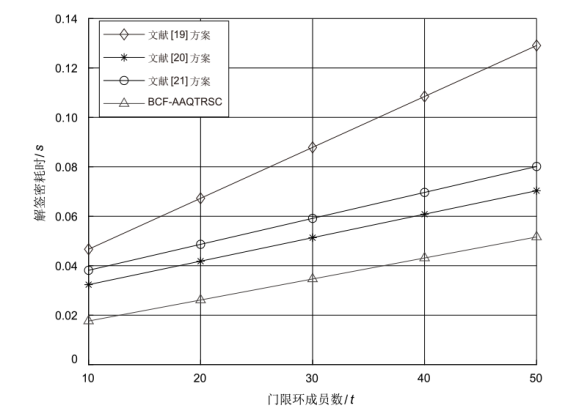
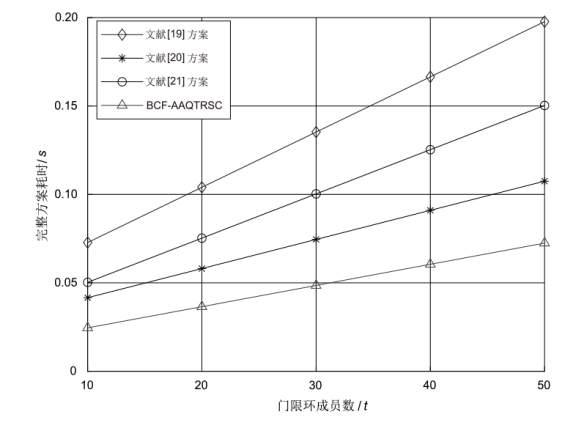
针对区块链金融系统中用户访问控制粒度较粗、交易数据流向不受控制、数据在公有链上传输时易受窃听等问题,文章提出适用于区块链金融的抗量子属性基门限环签密方案(BCF-AAQTRSC)。BCF-AAQTRSC利用多属性机构使任何用户都可创建属性并授权不同用户,在保证区块链访问控制灵活性的同时很好保护了区块链访问控制的安全性。BCF-AAQTRSC在实现中心权力分散的同时满足用户隐私数据的保密性、不可伪造性和匿名性。BCF-AAQTRSC通过NTRU格构造系统参数、主控密钥与用户私钥,使用消息块共享技术与填充排列技术构造密文,使方案的安全性和计算效率得到极大提高,适用于高存储效率的区块链金融应用场景中。
中图分类号:
引用本文
俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52.
YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance[J]. Netinfo Security, 2023, 23(7): 44-52.
| [1] | CHAUM D. Blind Signatures for Untraceable Payments[C]// Springer. Advances in Cryptology: Proceedings of Crypto 82. Berlin:Springer, 1983: 199-203. |
| [2] | KUMAR M, KATTI C P, SAXENA P C. An Untraceable Identity-Based Blind Signature Scheme Without Pairing for E-Cash Payment System[C]// Springer.Ubiquitous Communications and Network Computing: First International Conference. Berlin: Springer, 2018: 67-78. |
| [3] | ZHUANG Lishuang, CHEN Jie, WANG Qiyu. Lattice-Based Linkable Threshold Ring Signature in e-Voting[J]. Journal of Cryptologic Research, 2021, 8(3): 402-416. |
|
庄立爽, 陈杰, 王启宇. 电子投票协议下的基于格的可链接门限环签名[J]. 密码学报, 2021, 8(3): 402-416.
doi: 10.13868/j.cnki.jcr.000447 |
|
| [4] | TIAN Guohua, HU Yunhan, CHEN Xiaofeng. A Survey on Attack and Defense of Block-Chain System[J]. Journal of Software, 2021, 32(5): 1495-1525. |
| 田国华, 胡云瀚, 陈晓峰. 区块链系统攻击与防御技术研究进展[J]. 软件学报, 2021, 32(5): 1495-1525. | |
| [5] | NIU Shufen, WANG Caifen. Homomorphic Signature Algorithm for Multi-Source Linear Network Coding[J]. Computer Engineering, 2012, 38(2): 126-128. |
|
牛淑芬, 王彩芬. 多源线性网络编码的同态签名算法[J]. 计算机工程, 2012, 38(2): 126-128.
doi: 10.3969/j.issn.1000-3428.2012.02.040 |
|
| [6] |
WANG Zhiwei, FAN Jiaxing. Flexible Threshold Ring Signature in Chronological Order for Privacy Protection in Edge Computing[J]. IEEE Transactions on Cloud Computing, 2020, 10(2): 1253-1261.
doi: 10.1109/TCC.2020.2974954 URL |
| [7] | SUN Yiru, ZHENG Weiming. An Identity-Based Ring Signcryption Scheme in Ideal Lattice[J]. Journal of Network Intelligence, 2018, 3(3): 152-161. |
| [8] | NAYAK S K, MOHANTY S, MAJHI B. CLB-ECC: Certificateless Blind Signature Using ECC[J]. Journal of Information Processing Systems, 2017, 13(4): 970-986. |
| [9] |
ISLAM S H, AMIN R, BISWAS G P, et al. Provably Secure Pairing-Free Identity-Based Partially Blind Signature Scheme and Its Application in Online e-Cash System[J]. Arabian Journal for Science and Engineering, 2016, 41: 3163-3176.
doi: 10.1007/s13369-016-2115-5 URL |
| [10] | AJTAI M, KUMAR R, SIVAKUMAR D. Sampling Short Lattice Vectors and the Closest Lattice Vector Problem[C]// IEEE. Proceedings 17th IEEE Annual Conference on Computational Complexity. New York: IEEE, 2002: 53-57. |
| [11] |
TIAN Juanhong, ZHANG Jianzhong, LI Yanping. A Quantum Multi-Proxy Blind Signature Scheme Based On Genuine Four-Qubit Entangled State[J]. International Journal of Theoretical Physics, 2016, 55(2): 809-816.
doi: 10.1007/s10773-015-2719-7 URL |
| [12] |
WANG Shanping, MA Rui, ZHANG Yaling, et al. Ring Signature Scheme Based on Multivariate Public Key Cryptosystems[J]. Computers & Mathematics with Applications, 2011, 62(10): 3973-3979.
doi: 10.1016/j.camwa.2011.09.052 URL |
| [13] |
LIU Xiaoqian, ZHAO Yiming. Variant Scheme of Ring Signature Based on Multivariate Public Key Cryptosystems[J]. Computer Engineering, 2015, 41(2): 96-99.
doi: 10.3969/j.issn.1000-3428.2015.02.019 |
| [14] | GUO Qiuling, XIANG Hong, CAI Bin, et al. Threshold Ring Signature Scheme Based on Multivariate Public Key Cryptosystems[J]. Journal of Cryptologic Research, 2018, 5(2): 140-150. |
|
郭秋玲, 向宏, 蔡斌, 等. 基于多变量公钥密码体制的门限环签名方案[J]. 密码学报, 2018, 5(2): 140-150.
doi: 10.13868/j.cnki.jcr.000226 |
|
| [15] | YU Huifang, YANG Bo. Low-Computation Certificateless Hybrid Signcryption Scheme[J]. Frontiers of Information Technology & Electronic Engineering, 2017, 18(7): 928-940. |
| [16] |
YU Huifang, WANG Weike, ZHANG Qi. Certificateless Anti-Quantum Ring Signcryption for Network Coding[J]. Knowledge-Based Systems, 2022, 235: 107655.
doi: 10.1016/j.knosys.2021.107655 URL |
| [17] | CHEN Hu, HU Yupu, LIAN Zhizhu, et al. Efficient Certificateless Encryption Schemes from Lattices[J]. Journal of Software, 2015, 27(11): 2884-2897. |
| 陈虎, 胡予濮, 连至助, 等. 有效的格上无证书加密方案[J]. 软件学报, 2015, 27(11): 2884-2897. | |
| [18] | YU Huifang, WANG Ning. Certificateless Network Coding Proxy Signatures from Lattice[J]. Frontiers of Computer Science, 2023, 17(5): 1-8. |
| [19] |
CAI Ying, ZHANG Hao, FANG Yuguang. A Conditional Privacy Protection Scheme Based on Ring Signcryption for Vehicular Ad Hoc Networks.[J]. IEEE Internet of Things Journal, 2020, 8(1): 647-656.
doi: 10.1109/JIoT.6488907 URL |
| [20] |
CHEN Zhen, ZHANG Wenfang, WANG Xiaomin. Attribute-Based Alterable Threshold Ring Signature Scheme with Conspiracy Attack Immunity[J]. Journal on Communications, 2015, 36(12): 212-222.
doi: 10.11959/j.issn.1000-436x.2015330 |
|
陈桢, 张文芳, 王小敏. 基于属性的抗合谋攻击可变门限环签名方案[J]. 通信学报, 2015, 36(12): 212-222.
doi: 10.11959/j.issn.1000-436x.2015330 |
|
| [21] | SUN Hua, WANG Aimin, ZHENG Xuefeng. Provably Secure Identity-Based Threshold Ring Signcryption Scheme in Standard Model[J]. Computer Science, 2013, 40(5): 131-135. |
| 孙华, 王爱民, 郑雪峰. 标准模型下可证安全的基于身份的门限环签密方案[J]. 计算机科学, 2013, 40(5): 131-135. |
| [1] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [2] | 杜卫东, 李敏, 韩益亮, 王绪安. 基于密文转换的高效通用同态加密框架[J]. 信息网络安全, 2023, 23(4): 51-60. |
| [3] | 尹曙, 陈兴蜀, 朱毅, 曾雪梅. 基于字符空间构造的域名匿名化算法[J]. 信息网络安全, 2023, 23(4): 80-89. |
| [4] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [5] | 李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44. |
| [6] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [7] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [8] | 于晶, 袁曙光, 袁煜琳, 陈驰. 基于k匿名数据集的鲁棒性水印技术研究[J]. 信息网络安全, 2022, 22(9): 11-20. |
| [9] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [10] | 秦宝东, 余沛航, 郑东. 基于双陷门同态加密的决策树分类模型[J]. 信息网络安全, 2022, 22(7): 9-17. |
| [11] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 22(3): 78-84. |
| [12] | 王思蝶, 马兆丰, 罗守山, 徐单恒. 面向异构多链的区块链链上数据隐私保护方案[J]. 信息网络安全, 2022, 22(12): 67-75. |
| [13] | 张学旺, 姚亚宁, 黎志鸿, 张豪. 基于联盟链和Asmuth-Bloom秘密共享算法的数据共享方案[J]. 信息网络安全, 2022, 22(11): 17-23. |
| [14] | 晏燕, 张雄, 冯涛. 大数据统计划分发布的等比差分隐私预算分配方法[J]. 信息网络安全, 2022, 22(11): 24-35. |
| [15] | 梁广俊, 辛建芳, 倪雪莉, 马卓. 智能音箱安全与取证研究[J]. 信息网络安全, 2022, 22(10): 108-113. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||