信息网络安全 ›› 2023, Vol. 23 ›› Issue (4): 90-101.doi: 10.3969/j.issn.1671-1122.2023.04.010
基于安全高效联邦学习的智能电网入侵检测模型
- 华北电力大学控制与计算机工程学院,北京 102206
-
收稿日期:2022-12-10出版日期:2023-04-10发布日期:2023-04-18 -
通讯作者:石润华 E-mail:rhshi@ncepu.edu.cn -
作者简介:刘长杰(1996—),男,河北,硕士研究生,主要研究方向为联邦学习、入侵检测|石润华(1974—),男,安徽,教授,博士,主要研究方向为量子信息安全。 -
基金资助:国家自然科学基金(61772001)
A Smart Grid Intrusion Detection Model for Secure and Efficient Federated Learning
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2022-12-10Online:2023-04-10Published:2023-04-18 -
Contact:SHI Runhua E-mail:rhshi@ncepu.edu.cn
摘要:
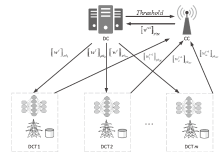
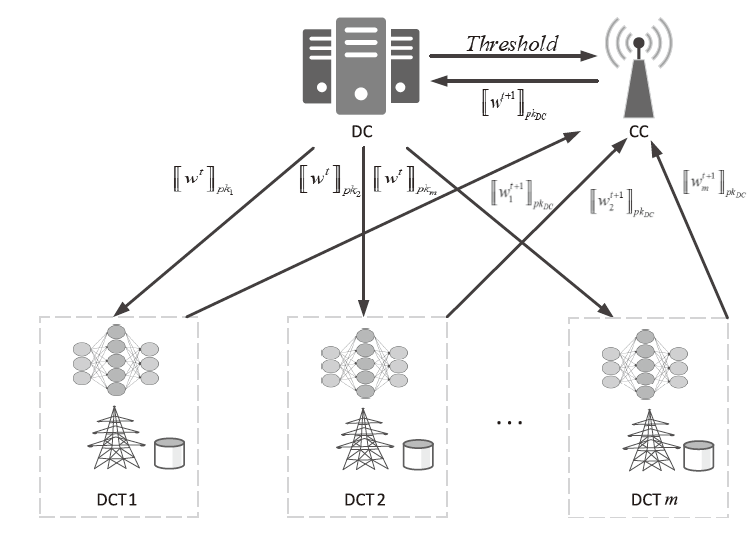
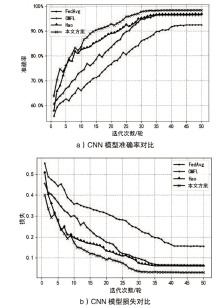
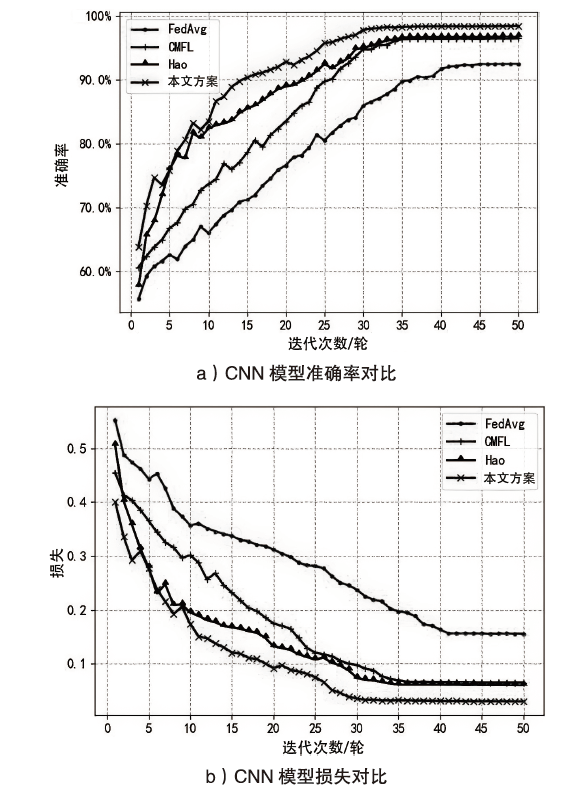
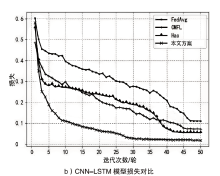
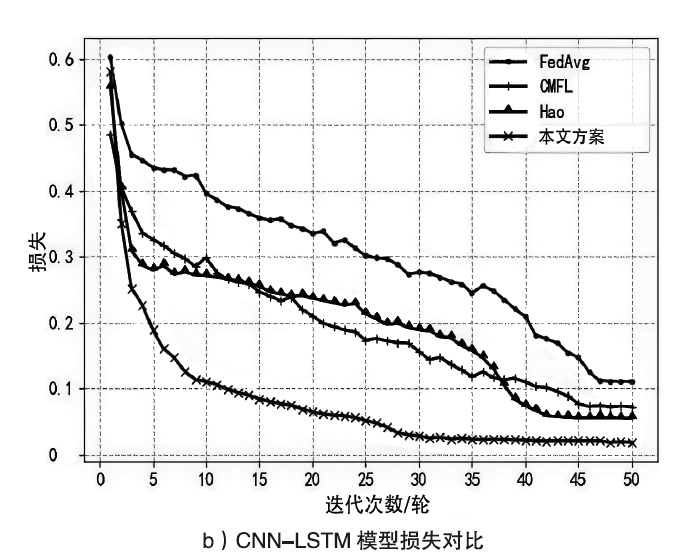
智能电网的快速发展使得电力传输更加高效,而电网系统和信息通信技术的高度集成也使电力系统面临更多的网络威胁。入侵检测作为一种检测网络攻击的有效方法受到了广泛关注,现有的检测方案大多基于强有力的假设:单个机构高质量的攻击示例足够多并且愿意分享他们的数据。然而,实际生活中单个机构所产生的数据不仅数量很少而且具有各自特点,这些机构通常并不愿意分享他们的数据,而使用单一机构的数据并不足以训练出一个高准确率的通用检测模型。鉴于此,文章提出一种安全高效的智能电网入侵检测方法。具体来说,首先引入联邦学习框架协同训练一个通用的入侵检测模型,以保护本地数据的安全并间接扩充数据量;然后设计了一个安全的通信协议,来保护训练过程中模型参数的安全性,防止攻击者窃听对其进行推理攻击;最后通过选择良好客户端进行全局聚合,在保证模型快速收敛的同时减少参与者的数量以降低通信带宽。实验结果表明,在保证模型收敛的情况下,文章所提模型提高了入侵检测的准确率,保护了数据隐私,同时降低了通信成本。
中图分类号:
引用本文
刘长杰, 石润华. 基于安全高效联邦学习的智能电网入侵检测模型[J]. 信息网络安全, 2023, 23(4): 90-101.
LIU Changjie, SHI Runhua. A Smart Grid Intrusion Detection Model for Secure and Efficient Federated Learning[J]. Netinfo Security, 2023, 23(4): 90-101.
表1
NSL-KDD数据集
| 标签 类型 | 标签描述 | 包含的具体攻击类型 | 训练集 | 测试集 |
|---|---|---|---|---|
| Normal | 正常流量数据 | Normal | 67343 | 9711 |
| DoS | 拒绝服务攻击 | neptune、back、land、pod、teardrop、smurf | 45927 | 5741 |
| Probe | 端口监视或扫描活动 | nmap、ipsweep、satan、portsweep | 11656 | 1106 |
| R2L | 来自远程主机的未授权非法访问 | imap、ftp_write、warezmaster、warezclient、multihop、guess_password、phf、spy | 995 | 2199 |
| U2R | 未授权的本地超级用户特权非法访问 | buffer_overflow、loadmodule、rootkit、perl | 52 | 37 |
| [1] | FARHANGI H. The Path of the Smart Grid[J]. IEEE Power and Energy Magazine, 2009, 8(1): 18-28. |
| [2] | TAN Song, DE D, SONG Wenzhan, et al. Survey of Security Advances in Smart Grid: A Data Driven Approach[J]. IEEE Communications Surveys & Tutorials, 2016, 19(1): 397-422. |
| [3] | SONG Chuanhe, SUN Yingying, HAN Guangjie, et al. Intrusion Detection Based on Hybrid Classifiers for Smart Grid[EB/OL]. (2021-06-06)[2022-08-30]. https://doi.org/10.1016/j.compeleceng.2021.107212. |
| [4] |
SINIOSOGLOU I, RADOGLOU-GRAMMATIKIS P, EFST-ATHOPOULOS G, et al. A Unified Deep Learning Anomaly Detection and Classification Approach for Smart Grid Environments[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1137-1151.
doi: 10.1109/TNSM.2021.3078381 URL |
| [5] | KHAN S, KIFAYAT K, KASHIF BASHIR A, et al. Intelligent Intrusion Detection System in Smart Grid Using Computational Intelligence and Machine Learning[EB/OL]. (2020-08-03)[2022-08-30]. https://onlinelibrary.wiley.com/doi/10.1002/ett.4062. |
| [6] |
LIANG Wei, LI K C, LONG Jing, et al. An Industrial Network Intrusion Detection Algorithm Based on Multifeature Data Clustering Optimization Model[J]. IEEE Transactions on Industrial Informatics, 2019, 16(3): 2063-2071.
doi: 10.1109/TII.9424 URL |
| [7] | NAZIR A, KHAN R A. A Novel Combinatorial Optimization Based Feature Selection Method for Network Intrusion Detection[EB/OL]. (2020-12-31)[2022-08-30]. https://doi.org/10.1016/j.cose.2020.102164. |
| [8] | LIU Jingmei, GAO Yuanbo, HU Fengjie. A Fast Network Intrusion Detection System Using Adaptive Synthetic Oversampling and LightGBM[EB/OL]. (2021-06-30)[2022-08-30]. https://doi.org/10.1016/j.cose.2021.102289. |
| [9] | MELIS L, SONG Congzheng, CRISTOFARO D E, et al. Exploiting Unintended Feature Leakage in Collaborative Learning[C]// IEEE.2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 691-706. |
| [10] | KONEČNÝ J, Mcmahan H B, YU F X, et al. Federated Learning: Strategies for Improving Communication Efficiency[EB/OL]. (2017-10-30)[2022-08-30]. https://doi.org/10.48550/arXiv.1610.05492. |
| [11] |
LI Beibei, WU Yuhao, SONG Jiarui, et al. DeepFed: Federated Deep Learning for Intrusion Detection in Industrial Cyber-Physical Systems[J]. IEEE Transactions on Industrial Informatics, 2020, 17(8): 5615-5624.
doi: 10.1109/TII.2020.3023430 URL |
| [12] |
SUN C, CARDENAS D J S, HAHN A, et al. Intrusion Detection for Cybersecurity of Smart Meters[J]. IEEE Transactions on Smart Grid, 2020, 12(1): 612-622.
doi: 10.1109/TSG.5165411 URL |
| [13] |
SHONE N, NGOC T N, PHAI V D, et al. A Deep Learning Approach to Network Intrusion Detection[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2018, 2(1): 41-50.
doi: 10.1109/TETCI.2017.2772792 URL |
| [14] |
KUKKALA V K, THIRULOGA S V, PASRICHA S. Indra: Intrusion Detection Using Recurrent Autoencoders in Automotive Embedded Systems[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2020, 39(11): 3698-3710.
doi: 10.1109/TCAD.43 URL |
| [15] |
UPADHYAY D, MANERO J, ZAMAN M, et al. Gradient Boosting Feature Selection with Machine Learning Classifiers for Intrusion Detection on Power Grids[J]. IEEE Transactions on Network and Service Management, 2020, 18(1): 1104-1116.
doi: 10.1109/TNSM.4275028 URL |
| [16] |
LI Fangyu, LI Qi, ZHANG Jinan, et al. Detection and Diagnosis of Data Integrity Attacks in Solar Farms Based on Multilayer Long Short-Term Memory Network[J]. IEEE Transactions on Power Electronics, 2020, 36(3): 2495-2498.
doi: 10.1109/TPEL.63 URL |
| [17] |
ISMAIL M, SHAABAN M F, NAIDU M, et al. Deep Learning Detection of Electricity Theft Cyber-Attacks in Renewable Distributed Generation[J]. IEEE Transactions on Smart Grid, 2020, 11(4): 3428-3437.
doi: 10.1109/TSG.5165411 URL |
| [18] | IMRANA Y, XIANG Yanping, ALI L, et al. A Bidirectional LSTM Deep Learning Approach for Intrusion Detection[EB/OL]. (2021-12-15)[2022-08-30]. https://doi.org/10.1016/j.eswa.2021.115524. |
| [19] | GE Mengmeng, SYED N F, FU Xiping, et al. Towards a Deep Learning-Driven Intrusion Detection Approach for Internet of Things[EB/OL]. (2021-02-26)[2022-08-30]. https://doi.org/10.1016/j.comnet.2020.107784. |
| [20] | NISHIO T, YONETANI R. Client Selection for Federated Learning with Heterogeneous Resources in Mobile Edge[C]// IEEE. 2019 IEEE International Conference on Communications (ICC2019). New York: IEEE, 2019: 1-7. |
| [21] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network[J]. Netinfo Security, 2020, 20(4): 47-54. |
| 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. | |
| [22] |
RAHMAN S A, TOUT H, TALHI C, et al. Internet of Things Intrusion Detection: Centralized, On-Device, or Federated Learning?[J]. IEEE Network, 2020, 34(6): 310-317.
doi: 10.1109/MNET.65 URL |
| [23] | ZHAO Ruijie, YIN Yue, SHI Yong, et al. Intelligent Intrusion Detection Based on Federated Learning Aided Long Short-Term Memory[EB/OL]. (2020-10-26)[2022-08-30]. https://doi.org/10.1016/j.phycom.2020.101157. |
| [24] |
ABDULRAHMAN S, TOUT H, MOURAD A, et al. FedMCCS: Multicriteria Client Selection Model for Optimal IoT Federated Learning[J]. IEEE Internet of Things Journal, 2020, 8(6): 4723-4735.
doi: 10.1109/JIoT.6488907 URL |
| [25] |
LI Beiei, WU Yuhao, SONG Jiarui, et al. DeepFed: Federated Deep Learning for Intrusion Detection in Industrial Cyber-Physical Systems[J]. IEEE Transactions on Industrial Informatics, 2020, 17(8): 5615-5624.
doi: 10.1109/TII.2020.3023430 URL |
| [26] | MAN Dapeng, ZENG Fanyi, YANG Wu, et al. Intelligent Intrusion Detection Based on Federated Learning for Edge-Assisted Internet of Things[EB/OL]. (2020-10-05)[2022-08-30]. https://doi.org/10.1155/2021/9361348. |
| [27] | LI Tian, SAHU A K, TALWALKAR A, et al. Federated Learning: Challenges, Methods, and Future Directions[J]. IEEE Signal Processing magazine, 2020, 37(3): 50-60. |
| [28] | MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[EB/OL]. (2017-02-28)[2022-08-30]. https://doi.org/10.48550/arXiv.1602.05629. |
| [29] | ZHANG Tong. Solving Large Scale Linear Prediction Problems Using Stochastic Gradient Descent Algorithms[EB/OL]. (2004-06-08)[2022-08-30]. https://hdl.handle.net/1783.1/98398. |
| [30] | PAILLIER P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 1999: 223-238. |
| [31] | MELIS L, SONG Congzheng, CRISTOFARO E D, et al. Exploiting Unintended Feature Leakage in Collaborative Learning[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 691-706. |
| [32] |
WANG Liwei, ZHANG Yan, FENG Jufu. On the Euclidean Distance of Images[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2005, 27(8): 1334-1339.
pmid: 16119271 |
| [33] | SITIKHU P, PAHI K, THAPA P, et al. A Comparison of Semantic Similarity Methods for Maximum Human Interpretability[C]// IEEE. 2019 Artificial Intelligence for Transforming Business and Society (AITB). New York: IEEE, 2019: 1-4. |
| [34] | ASAD M, MOUSTAFA A, ASLAM M. CEEP-FL: A Comprehensive Approach for Communication Efficiency and Enhanced Privacy in Federated Learning[EB/OL]. (2021-06-08)[2022-08-30]. https://doi.org/10.1016/j.asoc.2021.107235. |
| [35] |
WANG Tian, LIU Yan, ZHENG Xi, et al. Edge-Based Communication Optimization for Distributed Federated Learning[J]. IEEE Transactions on Network Science and Engineering, 2021, 9(4): 2015-2024.
doi: 10.1109/TNSE.2021.3083263 URL |
| [36] | HAO Shaochen, WEI Zizuan, MA Yao, et al. Network Intrusion Detection Model Based on Efficient Federation Learning Algorithm[EB/OL]. (2022-06-01)[2022-08-30]. http://kns.cnki.net/kcms/detail/51.1307.TP.20220531.1833.011.html. |
| 郝劭辰, 卫孜钻, 马垚, 等. 基于高效联邦学习算法的网络入侵检测模型[EB/OL]. (2022-06-01)[2022-08-30]. http://kns.cnki.net/kcms/detail/51.1307.TP.20220531.1833.011.html. |
| [1] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [2] | 王华忠, 田子蕾. 基于改进CGAN算法的工控系统入侵检测方法[J]. 信息网络安全, 2023, 23(1): 36-43. |
| [3] | 刘翔宇, 芦天亮, 杜彦辉, 王靖翔. 基于特征选择的物联网轻量级入侵检测方法[J]. 信息网络安全, 2023, 23(1): 66-72. |
| [4] | 刘忻, 李韵宜, 王淼. 一种基于机密计算的联邦学习节点轻量级身份认证协议[J]. 信息网络安全, 2022, 22(7): 37-45. |
| [5] | 张兴兰, 付娟娟. 基于辅助熵减的神经常微分方程入侵检测模型[J]. 信息网络安全, 2022, 22(6): 1-8. |
| [6] | 王浩洋, 李伟, 彭思维, 秦元庆. 一种基于集成学习的列车控制系统入侵检测方法[J]. 信息网络安全, 2022, 22(5): 46-53. |
| [7] | 吕国华, 胡学先, 杨明, 徐敏. 基于联邦随机森林的船舶AIS轨迹分类算法[J]. 信息网络安全, 2022, 22(4): 67-76. |
| [8] | 冯景瑜, 时翌飞, 王腾. 智能电网中抗主次合谋攻击的群智频谱感知加固方案[J]. 信息网络安全, 2022, 22(3): 1-9. |
| [9] | 银鹰, 周志洪, 姚立红. 基于LSTM的CAN入侵检测模型研究[J]. 信息网络安全, 2022, 22(12): 57-66. |
| [10] | 白宏鹏, 邓东旭, 许光全, 周德祥. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. |
| [11] | 徐硕, 张睿, 夏辉. 基于数据属性修改的联邦学习隐私保护策略[J]. 信息网络安全, 2022, 22(1): 55-63. |
| [12] | 何红艳, 黄国言, 张炳, 贾大苗. 基于极限树特征递归消除和LightGBM的异常检测模型[J]. 信息网络安全, 2022, 22(1): 64-71. |
| [13] | 刘烁, 张兴兰. 基于双重注意力的入侵检测系统[J]. 信息网络安全, 2022, 22(1): 80-86. |
| [14] | 路宏琳, 王利明, 杨婧. 一种新的参数掩盖联邦学习隐私保护方案[J]. 信息网络安全, 2021, 21(8): 26-34. |
| [15] | 李群, 董佳涵, 关志涛, 王超. 一种基于聚类分类的物联网恶意攻击检测方法[J]. 信息网络安全, 2021, 21(8): 82-90. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||