信息网络安全 ›› 2023, Vol. 23 ›› Issue (4): 1-9.doi: 10.3969/j.issn.1671-1122.2023.04.001
基于强度导向的JavaScript代码协同混淆方法
- 北京理工大学计算机学院,北京 100081
-
收稿日期:2022-10-09出版日期:2023-04-10发布日期:2023-04-18 -
通讯作者:李元章 E-mail:popular@bit.edu.cn -
基金资助:国家自然科学基金(62072037)
A Collaborative Obfuscation Method for JavaScript Code Based on Intensity Orientation
LI Yuanzhang( ), MA Yujie, SUN Haipeng, ZHANG Zheng
), MA Yujie, SUN Haipeng, ZHANG Zheng
- School of Computer Science & Technology, Beijing Institute of Technology, Beijing 100081, China
-
Received:2022-10-09Online:2023-04-10Published:2023-04-18 -
Contact:LI Yuanzhang E-mail:popular@bit.edu.cn
摘要:
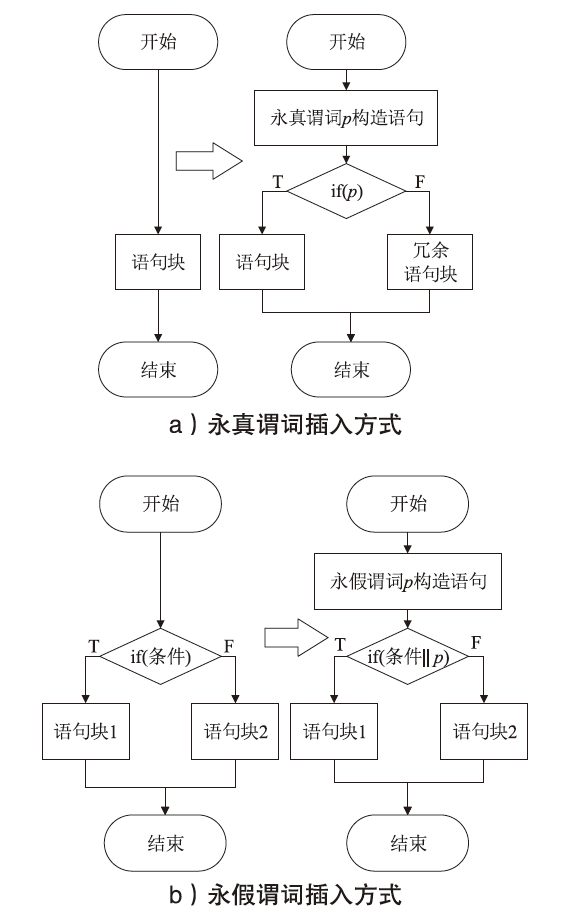
代码混淆是一种对软件代码的保护技术,通过提高代码逻辑的分析难度对软件进行加固。目前,针对代码混淆的研究主要集中在单一的新混淆方法的提出及其效果分析,针对多种混淆方法进行协同混淆的研究较少。针对此问题,文章提出一种基于强度导向的JavaScript代码协同混淆方法,首先对参与混淆的多种独立混淆方法进行强度评估;然后根据评估结果调整混淆方法的执行顺序,获得比单一的多方法叠加更好的混淆效果。实验结果表明,该方法能够以较低的代价获得更好的代码混淆效果。
中图分类号:
引用本文
李元章, 马煜杰, 孙海鹏, 张正. 基于强度导向的JavaScript代码协同混淆方法[J]. 信息网络安全, 2023, 23(4): 1-9.
LI Yuanzhang, MA Yujie, SUN Haipeng, ZHANG Zheng. A Collaborative Obfuscation Method for JavaScript Code Based on Intensity Orientation[J]. Netinfo Security, 2023, 23(4): 1-9.
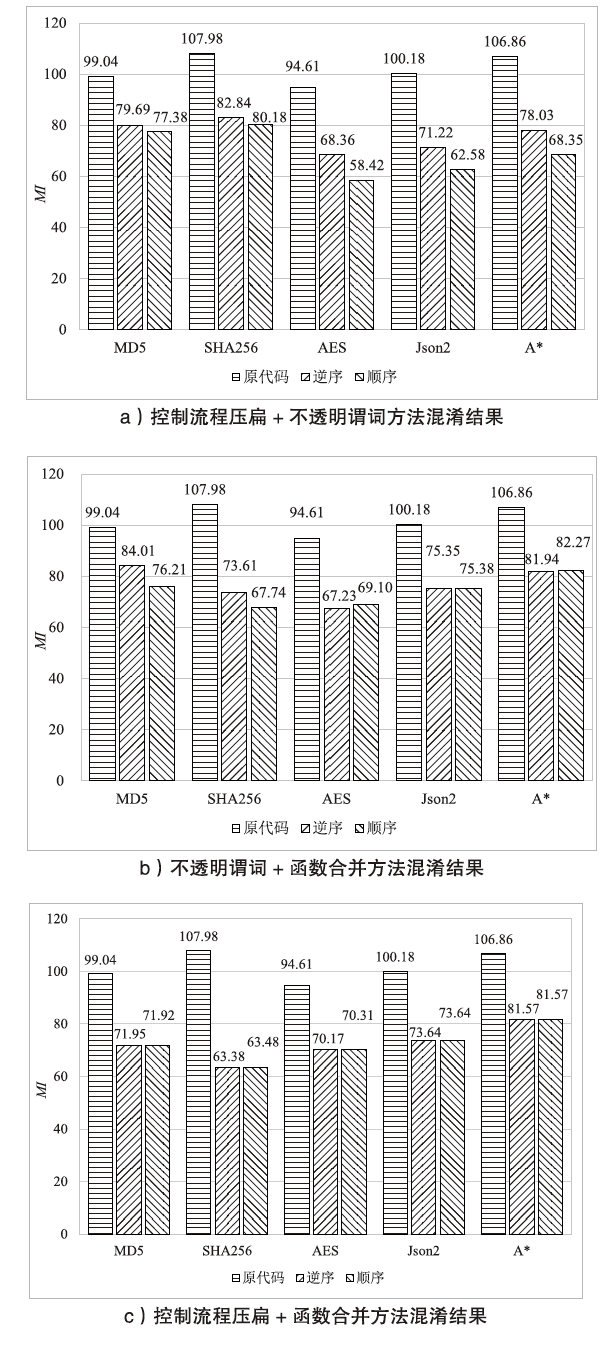
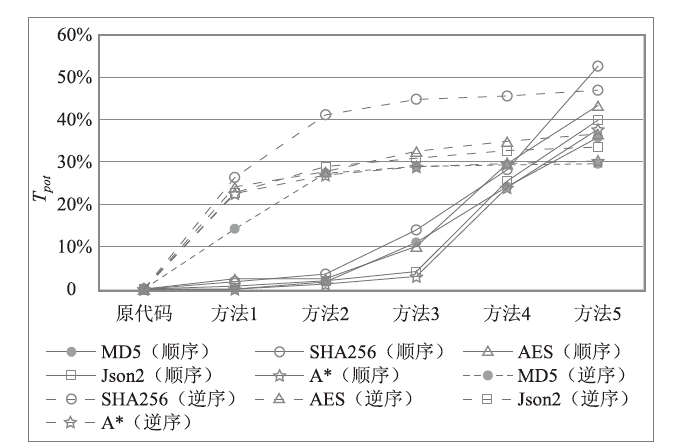
表4
混淆方法的强度评估结果
| MD5 | SHA256 | AES | JSON2 | A* | ||
|---|---|---|---|---|---|---|
| 原代码 | MI | 99.04 | 107.98 | 94.61 | 100.18 | 106.86 |
| Tpot | — | — | — | — | — | |
| 常量合并 | MI | 99.02 | 106.11 | 91.77 | 99.52 | 106.84 |
| Tpot | 0.02% | 1.73% | 3.00% | 0.66% | 0.01% | |
| 代码重排序 | MI | 97.34 | 105.99 | 92.29 | 98.92 | 103.65 |
| Tpot | 1.72% | 1.84% | 2.45% | 1.26% | 3.00% | |
| 不透明谓词 | MI | 89.26 | 95.16 | 79.63 | 82.67 | 89.39 |
| Tpot | 9.87% | 11.87% | 15.83% | 17.48% | 16.35% | |
| 函数合并 | MI | 85.22 | 79.57 | 90.00 | 97.96 | 105.93 |
| Tpot | 13.95% | 26.31% | 4.87% | 2.22% | 0.87% | |
| 控制流程压扁 | MI | 84.97 | 90.50 | 71.81 | 77.36 | 82.75 |
| Tpot | 14.21% | 16.19% | 24.10% | 22.78% | 22.56% | |
| [1] |
BUONAMICI F, CARFAGNI M, FURFERI R, et al. Reverse Engineering Modeling Methods and Tools: A Survey[J]. Computer-Aided Design and Applications, 2018, 15(3): 443-464.
doi: 10.1080/16864360.2017.1397894 URL |
| [2] | GU Weiwei, HUANG Guifang, LIAO Maodong. The Application of Obfuscation in Cryptographic Protocols[J]. Netinfo Security, 2017, 17(9): 81-84. |
| 顾微微, 黄桂芳, 廖茂东. 代码混淆在密码协议中的应用[J]. 信息网络安全, 2017, 17(9):81-84. | |
| [3] | PAN Yan, ZHU Yuefei, LIN Wei. Code Obfuscation Based on Instructions Swapping[J]. Journal of Software, 2019, 30(6): 1778-1792. |
| 潘雁, 祝跃飞, 林伟. 基于指令交换的代码混淆方法[J]. 软件学报, 2019, 30(6):1778-1792. | |
| [4] |
KIPERBERG M, LEON R, RESH A, et al. Hypervisor-Based Protection of Code[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(8): 2203-2216.
doi: 10.1109/TIFS.10206 URL |
| [5] |
CHEN Yaoyang, CHEN Wei. Control Flow Obfuscation Technology Based on Implicit Jump[J]. Computer Engineering and Applications, 2021, 57(20): 125-132.
doi: 10.3778/j.issn.1002-8331.2007-0109 |
|
陈耀阳, 陈伟. 采用隐式跳转的控制流混淆技术[J]. 计算机工程与应用, 2021, 57(20):125-132.
doi: 10.3778/j.issn.1002-8331.2007-0109 |
|
| [6] |
XIONG Wenjie, SCHALLER A, KATZENBEISSER S, et al. Software Protection Using Dynamic PUFs[J]. IEEE Transactions on Information Forensics and Security, 2019, 15: 2053-2068.
doi: 10.1109/TIFS.10206 URL |
| [7] | WEN Weiping, FANG Ying, YE He, et al. A Code Obfuscation System Against Symbolic Execution Attacks[J]. Netinfo Security, 2021, 21(7): 17-26. |
| 文伟平, 方莹, 叶何, 等. 一种对抗符号执行的代码混淆系统[J]. 信息网络安全, 2021, 21(7):17-26. | |
| [8] |
CHEN Zhe, JIA Chunfu, ZONG Nan, et al. Branch Obfuscation Using Random Forest[J]. Acta Electronica Sinica, 2018, 46(10): 2458-2466.
doi: 10.3969/j.issn.0372-2112.2018.10.020 |
|
陈喆, 贾春福, 宗楠, 等. 随机森林在程序分支混淆中的应用[J]. 电子学报, 2018, 46(10):2458-2466.
doi: 10.3969/j.issn.0372-2112.2018.10.020 |
|
| [9] | FANG Hui, WU Yongdong, WANG Shuhong, et al. Multi-Stage Binary Code Obfuscation Using Improved Virtual Machine[C]// Springer. International Conference on Information Security. Heidelberg: Springer, 2011: 168-181. |
| [10] |
KUANG Kaiyuan, TANG Zhanyong, GONG Xiaoqing, et al. Enhance Virtual-Machine-Based Code Obfuscation Security through Dynamic Bytecode Scheduling[J]. Computers & Security, 2018, 74: 202-220.
doi: 10.1016/j.cose.2018.01.008 URL |
| [11] |
WANG Huaijin, WANG Shuai, XU Dongpeng, et al. Generating Effective Software Obfuscation Sequences with Reinforcement Learning[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 19(3): 1900-1917.
doi: 10.1109/TDSC.2020.3041655 URL |
| [12] | LIU Han, SUN Chengnian, SU Zhendong, et al. Stochastic Optimization of Program Obfuscation[C]// IEEE. 2017 IEEE/ACM 39th International Conference on Software Engineering(ICSE). New York: IEEE, 2017: 221-231. |
| [13] | COLLBERG C, THOMBORSON C, LOW D. A Taxonomy of Obfuscating Transformations[R]. New Zealand: The University of Auckland, TR148, 1997. |
| [14] | QU Jun, HE Yuan. Research on Reverse Analysis of Android Application Based on Control Flow Obfuscation Resistance Algorithm[J]. Netinfo Security, 2020, 20(S1): 71-74. |
| 瞿俊, 何源. 基于控制流混淆抵御算法的Android应用程序逆向分析研究[J]. 信息网络安全, 2020, 20(S1):71-74. | |
| [15] | BALACHANDRAN V, KEONG N W, EMMANUEL S. Function Level Control Flow Obfuscation for Software Security[C]// IEEE. 2014 8th International Conference on Complex, Intelligent and Software Intensive Systems. New York: IEEE, 2014: 133-140. |
| [16] | SU Qing. Research on Code Protection Technology in Malicious Controlled Environment[D]. Guangzhou: Guangdong University of Technology, 2018. |
| 苏庆. 恶意受控环境下的代码保护技术研究[D]. 广州: 广东工业大学, 2018. | |
| [17] |
SU Qing, SUN Jintian. Research on Opaque Predicate Obfuscation Technique Based on Chaotic Opaque Expression[J]. Computer Science, 2017, 44(12): 114-119.
doi: 10.11896/j.issn.1002-137X.2017.12.022 |
|
苏庆, 孙金田. 基于混沌不透明表达式的不透明谓词混淆技术研究[J]. 计算机科学, 2017, 44(12):114-119.
doi: 10.11896/j.issn.1002-137X.2017.12.022 |
|
| [18] | TAN Junjun. Research and Implementation of Code Obfuscation System Based on Chaotic Opaque Predicate in Java[D]. Xi’an: Shaanxi Normal University, 2018. |
| 谭俊俊. Java基于混沌不透明谓词代码混淆系统的研究与实现[D]. 西安: 陕西师范大学, 2018. | |
| [19] |
EBERT C, CAIN J, ANTONIOL G, et al. Cyclomatic Complexity[J]. IEEE Software, 2016, 33(6): 27-29.
doi: 10.1109/MS.52 URL |
| [20] | ANUGRAH I G, SARNO R, ANGGRAINI R N E. Decomposition Using Refined Process Structure Tree(RPST) and Control Flow Complexity Metrics[C]// IEEE. 2015 International Conference on Information & Communication Technology and Systems(ICTS). New York: IEEE, 2015: 203-208. |
| [21] | MUBARAK A, COUNSELL S, HIERONS R M. An Evolutionary Study of Fan-in and Fan-out Metrics in OSS[C]// IEEE. 2010 4th International Conference on Research Challenges in Information Science(RCIS). New York: IEEE, 2010: 473-482. |
| [22] |
MUNSON J C, KOHSHGOFTAAR T M. Measurement of Data Structure Complexity[J]. Journal of Systems and Software, 1993, 20(3): 217-225.
doi: 10.1016/0164-1212(93)90065-6 URL |
| [23] | KENCANA G H, SALEH A, DARWITO H A, et al. Comparison of Maintainability Index Measurement from Microsoft CodeLens and Line of Code[C]// IEEE. 2020 7th International Conference on Electrical Engineering, Computer Sciences and Informatics(EECSI). New York: IEEE, 2020: 235-239. |
| [24] | CHEN C, ALFAYEZ R, SRISOPHA K, et al. Why is It Important to Measure Maintainability and What are the Best Ways to do It?[C]// IEEE. 2017 IEEE/ACM 39th International Conference on Software Engineering Companion(ICSE-C). New York: IEEE, 2017: 377-378. |
| [25] | SJØBERG D I K, ANDA B, MOCKUS A. Questioning Software Maintenance Metrics: A Comparative Case Study[C]// IEEE. The 2012 ACM-IEEE International Symposium on Empirical Software Engineering and Measurement. New York: IEEE, 2012: 107-110. |
| [26] |
MALHOTRA R, CHUG A. Software Maintainability: Systematic Literature Review and Current Trends[J]. International Journal of Software Engineering and Knowledge Engineering, 2016, 26(8): 1221-1253.
doi: 10.1142/S0218194016500431 URL |
| [27] | HARIPRASAD T, VIDHYAGARAN G, SEENU K, et al. Software Complexity Analysis Using Halstead Metrics[C]// IEEE. 2017 International Conference on Trends in Electronics and Informatics(ICEI). New York: IEEE, 2017: 1109-1113. |
| [1] | 文伟平, 方莹, 叶何, 陈夏润. 一种对抗符号执行的代码混淆系统[J]. 信息网络安全, 2021, 21(7): 17-26. |
| [2] | 顾微微, 黄桂芳, 廖茂东. 代码混淆在密码协议中的应用[J]. 信息网络安全, 2017, 17(9): 81-84. |
| [3] | 文伟平, 张汉, 曹向磊. 基于Android可执行文件重组的混淆方案的设计与实现[J]. 信息网络安全, 2016, 16(5): 71-77. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||