信息网络安全 ›› 2022, Vol. 22 ›› Issue (4): 7-19.doi: 10.3969/j.issn.1671-1122.2022.04.002
RISC-V架构上的时间侧信道静态检测研究
- 1.武汉大学国家网络安全学院,武汉 430064
2.武汉大学空天信息安全与可信计算教育部重点实验室,武汉 430064
3.北京航空航天大学网络空间安全学院,北京 100191
-
收稿日期:2021-12-28出版日期:2022-04-10发布日期:2022-05-12 -
通讯作者:黎聪 E-mail:licong.whu@foxmail.com -
作者简介:唐明(1976—),女,河南,教授,博士,主要研究方向为信息安全、密码芯片安全和侧信道|黎聪(1997—),男,贵州,硕士研究生,主要研究方向为应用密码学和微架构|李永波(1997—),男,河南,硕士研究生,主要研究方向为侧信道和体系结构安全|岳天羽(1998—),男,江苏,硕士研究生,主要研究方向为网络空间安全、复杂系统安全性 -
基金资助:国家自然科学基金(61972295);国家重点研究发展计划(2019YFB1706001)
Study on Static Detection of Timing Side Channel for RISC-V Architecture
TANG Ming1,2, LI Cong1,2( ), LI Yongbo1,2, YUE Tianyu3
), LI Yongbo1,2, YUE Tianyu3
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430064, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430064, China
3. School of Cyber Science and Technology, Beihang University, Beijing 100191, China
-
Received:2021-12-28Online:2022-04-10Published:2022-05-12 -
Contact:LI Cong E-mail:licong.whu@foxmail.com
摘要:
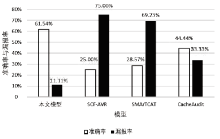
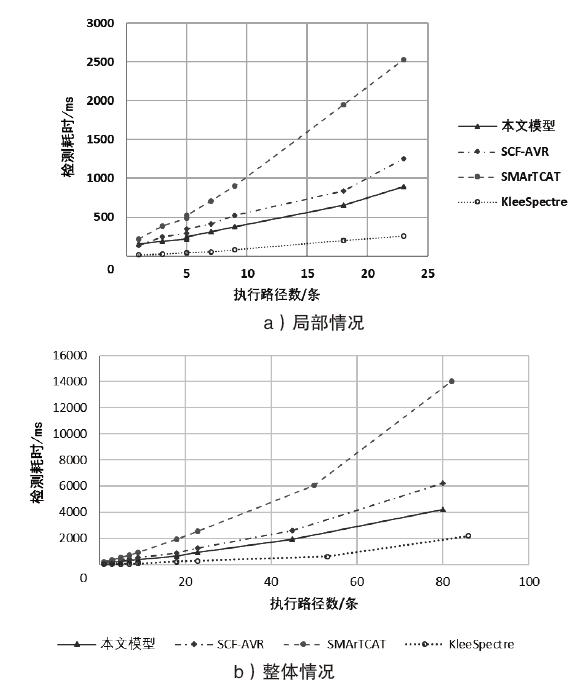
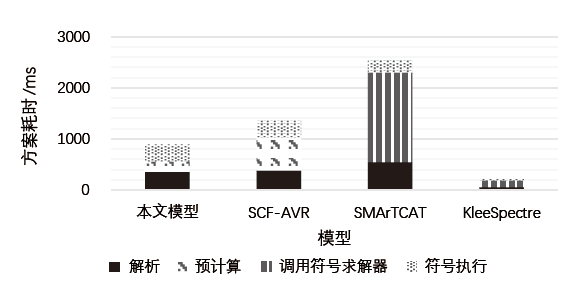
时间侧信道攻击对开源RISC-V架构的软件机密性有严重威胁,而目前对于RISC-V架构上的时间侧信道泄露静态检测的研究较为缺乏。文章评估了常见的时间侧信道泄露静态分析方法的适用范围和优缺点,根据RISC-V汇编语言的特点优化检测算法,针对RISC-V的64位通用指令集RV64G实现了结合信息流分析和简化符号执行理论的时间侧信道检测模型。文章对通用开源网络通信密码库OpenSSL和NaCl的AES、RSA等密码算法实现进行测试,测试结果表明,相较于现有工具中准确率最高的模型,文章所提模型在相同的测试向量下准确率提高了约17%,漏报率降低了约22%,加快了检测速度并在一定程度上缓解了路径爆炸问题,为RISC-V架构上侧信道攻击安全检测工具设计提供了参考。
中图分类号:
引用本文
唐明, 黎聪, 李永波, 岳天羽. RISC-V架构上的时间侧信道静态检测研究[J]. 信息网络安全, 2022, 22(4): 7-19.
TANG Ming, LI Cong, LI Yongbo, YUE Tianyu. Study on Static Detection of Timing Side Channel for RISC-V Architecture[J]. Netinfo Security, 2022, 22(4): 7-19.
表1
现有检测工具与本文模型的对比
| 工具名称 | 检测程序的语言 类型 | 覆盖时间 泄露种类 | 硬件架构 | 检测密码库 | 技术 路线 |
|---|---|---|---|---|---|
| 程序计数器 模型[ | C | 循环/分支 | 高级语言 检测 | 简化的C语言Demo | 信息流 分析 |
| SCF-AVR[ | AVR汇编 | 循环/分支 | AVR | µNaCl | 信息流 分析 |
| SMArTCAT[ | VEX(IR) | 循环/分支/Cache | ARM | OpenSSL | 符号 执行 |
| SCF-JAVA[ | Java | 循环/分支 | 高级语言 检测 | Java FlexiProvider/GNU Classpath | 信息流 分析 |
| CacheAudit[ | x86汇编 | Cache | x86 | PolarSSL | 抽象 解释 |
| KleeSpectre[ | LLVM(IR) | Spectre v1 | x86 | LibTom Crypt/OpenSSL | 符号 执行 |
| 本文模型 | RV64G 汇编 | 循环/分支/ Cache/浮点 | RISC-V | OpenSSL/NaCl | 信息流分析+简化符号执行 |
表3
RV64G寄存器级敏感信息传递与执行时间表
| 分类名称 | 指令原型 | 预估时钟周期 | 敏感信息传递流向 | 备注 |
|---|---|---|---|---|
| 寄存器 立即数 | instr rd, imm | 1 | rd → rd | — |
| 2寄存器 | instr rd, rs | 1 | rd&rs → rd | — |
| 2寄存器 立即数 | instr rd, rs, imm | 1 | rd&rs → rd | — |
| 2寄存器 间接跳转(LOAD/STORE) | load | 3 | rd&rs → rd | 取Cache miss时的周期 |
| store | 1 | 取Cache miss时的周期 | ||
| 3寄存器 | imul | 10 | rd&rs1&rs2 → rd | — |
| idiv(单字) | 34 | — | ||
| idiv(双字) | 66 | — | ||
| fadd, fmul, fmadd (单字) | 5 | — | ||
| fadd, fmul, fmadd (双字) | 7 | — | ||
| fdiv | 20 | — | ||
| fsqrt | 25 | — | ||
| instr rd, rs1, rs2 | 1 | 除特殊指令以外的3寄存器指令 | ||
| 4寄存器 | instr rd, rs1, rs2(rs3) | 1 | rd&rs1&rs2&rs3 → rd | — |
| 分支 | beq/bne/blt/bltu/bge/bgeu | 1 | 隐式污点传播规则 | — |
| 跳转 | jalr/jal | 1 | pass | 直接跳转指令不影响污点 传播 |
| 伪指令 | 转换为对应真指令后处理 | — | pass | — |
表4
rocketchip验证性实验复现漏洞
| 密码算法名称 | 泄露类型 | 泄露函数 | 复现泄露方法 |
|---|---|---|---|
| OpenSSL-AES | DF-Cache | aes_encrypt | S盒产生的泄露[ |
| OpenSSL-RSA | CF-BR | Modular_Exonentiation | 多次调用模幂函数Modular_Exonentiation导致循环控制流类时间泄露[ |
| OpenSSL-ECDSA | CF-BR | 蒙哥马利乘函数 | 利用ec2_GF2m_montegomery_multiply 函数恢复部分密钥[ |
| OpenSSL-BlowFish | DF-Cache | bf_encrypt | S盒产生的泄露[ |
| OpenSSL-RC2 | DF-Cache | RC2_set_key | 存在于密钥设置函数中的泄露,存在一个类似S盒的查找表 |
| OpenSSL-RC4 | DF-Cache | RC2_set_key | 来自加密函数RC4,存在一个类似S盒的查找表 |
| NaCl-AES | 无泄露 | 无 | 无 |
| NaCl-RSA | 无泄露 | 无 | 无 |
| Demo-AES | CF-LP | x2_time | 存在循环时间泄露的AES实现程序 |
| Demo-FP | DF-FP | Demo_FP | 目前主要复现的是针对Firefox等浏览器的隐私数据库的像素窃取攻击[ |
表5
不同模型的测试向量检出漏洞数比较
| 检测程序 | 本文 模型 | AVR 模型 | SMArTCAT模型 | CacheAudit模型 | 验证可利用漏洞数 |
|---|---|---|---|---|---|
| OpenSSL-AES | 2 | 2 | 1 | 1 | 1 |
| OpenSSL-RSA | 2 | 2 | 1 | 0 | 1 |
| OpenSSL-ECDSA | 2 | 5 | 4 | 1 | 2 |
| OpenSSL-BlowFish | 1 | 3 | 3 | 1 | 1 |
| OpenSSL-RC2 | 1 | 3 | 2 | 1 | 1 |
| OpenSSL-RC4 | 1 | 2 | 1 | 1 | 1 |
| NaCl-AES | 1 | 1 | 0 | 1 | 0 |
| NaCl-RSA | 1 | 1 | 1 | 2 | 0 |
| Demo-AES | 1 | 1 | 1 | 1 | 1 |
| Demo-FP | 1 | 0 | 0 | 0 | 1 |
| 总计 | 13 | 20 | 14 | 9 | 9 |
| [1] | KOCHER P, HORN J, FOGH A, et al. Spectre Attacks: Exploiting Speculative Execution[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 1-19. |
| [2] | LIPP M, SCHWARZ M, GRUSS D, et al. Meltdown: Reading Kernel Memory from User Space[C]// USENIX. 27th USENIX Security Symposium (USENIX Security18). Berkeley: USENIX, 2018: 973-990. |
| [3] | LE A T, DAO B A, SUZAKI K, et al. Experiment on Replication of Side Channel Attack via Cache of RISC-V Berkeley Out-of-Order Machine (BOOM) Implemented on FPGA[EB/OL]. (2020-05-26)[2021-08-21]. [2021-08-21]. https://carrv.github.io/2020/slides/CARRV2020_slides_2_Le.pdf . |
| [4] | GONZALEZ A, KORPAN B, ZHAO J, et al. Replicating and Mitigating Spectre Attacks on an Open Source RISC-V Microarchitecture[EB/OL]. (2019-06-22)[2021-09-11]. https://carrv.github.io/2019/papers/carrv2019_paper_5.pdf . |
| [5] | CAMPOS F, JELLEMA L, LEMMEN M, et al. Assembly or Optimized C for Lightweight Cryptography on RISC-V[C]// Springer. International Conference on Cryptology and Network Security. Heidelberg: Springer, 2020: 526-545. |
| [6] | AUJLA G S, CHAUDHARY R, KUMAR N, et al. SecSVA: Secure Storage, Verification, and Auditing of Big Data in the Cloud Environment[J]. IEEE Communications Magazine, 2018, 56(1): 78-85. |
| [7] | LE A T, HOANG T T, DAO B A, et al. A Real-Time Cache Side-Channel Attack Detection System on RISC-V Out-of-Order Processor[J]. IEEE ACCESS, 2021(9): 164597-164612. |
| [8] |
PISTOIA M, CHANDRA S, FINK S J, et al. A Survey of Static Analysis Methods for Identifying Security Vulnerabilities in Software Systems[J]. IBM Systems Journal, 2007, 46(2): 265-288.
doi: 10.1147/sj.462.0265 URL |
| [9] | MOLNAR D, PIOTROWSKI M, SCHULTZ D, et al. The Program Counter Security Model: Automatic Detection and Removal of Control-Flow Side Channel Attacks[C]// Springer. International Conference on Information Security and Cryptology. Heidelberg: Springer, 2005: 156-168. |
| [10] |
LUX A, STAROSTIN A. A Tool for Static Detection of Timing Channels in JAVA[J]. Journal of Cryptographic Engineering, 2011, 1(4): 303-313.
doi: 10.1007/s13389-011-0021-z URL |
| [11] | DEWALD F, MANTEL H, WEBER A. AVR Processors as a Platform for Language-Based Security[C]// Springer. European Symposium on Research in Computer Security. Heidelberg: Springer, 2017: 427-445. |
| [12] | KRAK R. Cycle-Accurate Timing Channel Analysis of Binary Code[D]. Enschede: University of Twente, 2017. |
| [13] | WANG F, SHOSHITAISHVILI Y. Angr-the Next Generation of Binary Analysis[C]// IEEE. 2017 IEEE Cybersecurity Development (SecDev). New York: IEEE, 2017: 8-9. |
| [14] | ASANOVIC K, AVIZIENIS R, BACHRACH J, et al. The Rocket Chip Generator[R]. Berkeley: University of California at Berkeley, UCB/EECS-2016-17, 2016. |
| [15] | ASANOVIC K, PATTERSON D A, CELIO C. The Berkeley Out-of-Order Machine (BOOM): An Industry-Competitive, Synthesizable, Parameterized RISC-V Processor[R]. Berkeley: University of California at Berkeley, UCB/EECS-2015-167, 2015. |
| [16] | DOYCHEV G, KÖPF B, MAUBORGNE L, et al. CacheAudit: A Tool for the Static Analysis of Cache Side Channels[J]. ACM Transactions on Information and System Security, 2015, 18(4): 1-32. |
| [17] | WANG Guanhua, CHATTOPADHYAY S, BISWAS A K, et al. KLEEspectre: Detecting Information Leakage through Speculative Cache Attacks via Symbolic Execution[J]. ACM Transactions on Software Engineering and Methodology (TOSEM), 2020, 29(3): 1-31. |
| [18] | CADAR C, DUNBAR D, ENGLER D R. Klee: Unassisted and Automatic Generation of High-Coverage Tests for Complex Systems Programs[C]// USENIX. 8th USENIX Conference on Operating Systems Design & Implementation (OSDI). Berkeley: USENIX, 2009. |
| [19] | ROSCOE A W, WOODCOCK J C P, WULF L. Non-Interference through Determinism[C]// Springer. European Symposium on Research in Computer Security. Heidelberg: Springer, 1994: 31-53. |
| [20] | BERNSTEIN D J. Cache-Timing Attacks on AES[EB/OL]. (2005-04-15)[2021-09-23]. https://www.researchgate.net/publication/228939782_Cache-timing_attacks_on_AES . |
| [21] | ANDRYSCO M, KOHLBRENNER D, MOWERY K, et al. On Subnormal Floating Point and Abnormal Timing[C]// On Subnormal Floating Point and Abnormal Timing[C]//IEEE. 2015 IEEE Symposium on Security and Privacy. New York: IEEE, 2015: 623-639. |
| [22] | WATERMAN A, LEE Y, PATTERSON D A, et al. The RISC-V Instruction Set Manual[R]. University of California at Berkeley, UCB/EECS-2014-54, 2014. |
| [23] |
JOHNSON D B. Finding All the Elementary Circuits of a Directed Graph[J]. SIAM Journal on Computing, 1975, 4(1): 77-84.
doi: 10.1137/0204007 URL |
| [24] |
TARJAN R. Depth-First Search and Linear Graph Algorithms[J]. SIAM Journal on Computing, 1972, 1(2): 146-160.
doi: 10.1137/0201010 URL |
| [25] | DIGILEN T. Xilinx Zedboard Document[EB/OL]. (2017-12-31)[2021-10-27]. http://www.digilentinc.com/Products/Detail.cfm?Prod=ZEDBOARD/ . |
| [26] | KOCHER P, HORN J, FOGH A, et al. Spectre Attacks: Exploiting Speculative Execution[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 1-19. |
| [27] | BRUMLEY B B, TUVERI N. Remote Timing Attacks are Still Practical[C]// Springer. European Symposium on Research in Computer Security. Heidelberg: Springer, 2011: 355-371. |
| [28] | FINKE T, GEBHARDT M, SCHINDLER W. A New Side-Channel Attack on RSA Prime Generation[C]// Springer. International Workshop on Cryptographic Hardware and Embedded Systems. Heidelberg: Springer, 2009: 141-155. |
| [29] | CAULIGI S, SOELLER G, BROWN F, et al. Fact: A Flexible, Constant-Time Programming Language[C]// IEEE. 2017 IEEE Cybersecurity Development (SecDev). New York: IEEE, 2017: 69-76. |
| [30] |
BRUMLEY D, BONEH D. Remote Timing Attacks are Practical[J]. Computer Networks, 2005, 48(5): 701-716.
doi: 10.1016/j.comnet.2005.01.010 URL |
| [31] |
WANG Wenbo, FAN Shuqin. Attacking OpenSSL ECDSA with a Small Amount of Side-Channel Information[J]. Science China Information Sciences, 2018, 61(3): 1-14.
doi: 10.1007/s11432-017-9235-7 URL |
| [32] | FUA P, LIS K. Comparing Python, Go, and C++ on the N-Queens Problem[EB/OL]. (2020-01-08)[2021-11-13]. https://arxiv.org/abs/2001.02491 . |
| [1] | 江皓臻, 江苾菲, 贺朗月, 单亦伟. 基于THD89的智能密码钥匙设计与实现[J]. 信息网络安全, 2021, 21(9): 40-45. |
| [2] | 吴志红, 赵建宁, 朱元, 陆科. 国密算法和国际密码算法在车载单片机上应用的对比研究[J]. 信息网络安全, 2019, 19(8): 68-75. |
| [3] | 邹翔, 陈兵. 基于国产密码算法的印章防伪技术研究[J]. 信息网络安全, 2019, 19(1): 76-82. |
| [4] | 王庆, 屠晨阳, shenjiahui@iie.ac.cn. 侧信道攻击通用框架设计及应用[J]. 信息网络安全, 2017, 17(5): 57-62. |
| [5] | 项川, 潘无穷, 黎火荣, 林璟锵. 支持商密算法TLS浏览器的设计与实现[J]. 信息网络安全, 2017, 17(4): 26-33. |
| [6] | 蔡林, 陈铁明. Android移动恶意代码检测的研究概述与展望[J]. 信息网络安全, 2016, 16(9): 218-222. |
| [7] | 陈庆;杨磊. SSL协议应用中安全技术问题探究[J]. , 2012, 12(4): 0-0. |
| [8] | 宋超臣;黄俊强;王大萌;段志鸣. 计算机漏洞安全检测技术综述[J]. , 2012, 12(1): 0-0. |
| [9] | 屠晨阳;荆继武;王雷;向继. HTTPS服务器密码算法测试工具设计与实现[J]. , 2011, 11(9): 0-0. |
| [10] | 李继中;舒辉. 密码算法识别技术研究[J]. , 2011, 11(11): 0-0. |
| [11] | 范永清. 密码学及其在现代通讯中的应用[J]. , 2009, 9(3): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||