信息网络安全 ›› 2022, Vol. 22 ›› Issue (4): 67-76.doi: 10.3969/j.issn.1671-1122.2022.04.008
基于联邦随机森林的船舶AIS轨迹分类算法
- 1.战略支援部队信息工程大学,郑州 450001
2.锦州医科大学,锦州 121000
-
收稿日期:2021-10-29出版日期:2022-04-10发布日期:2022-05-12 -
通讯作者:徐敏 E-mail:powerhua@163.com -
作者简介:吕国华(1989—),男,吉林,硕士,主要研究方向为机器学习和隐私保护|胡学先(1982—),男,湖北,副教授,博士,主要研究方向为大数据安全和隐私保护|杨明(1994—),男,内蒙古,硕士研究生,主要研究方向为大数据安全和隐私保护|徐敏(1989—),女,辽宁,讲师,硕士,主要研究方向为教育与医疗数据 -
基金资助:国家自然科学基金(62172433);国家自然科学基金(61872449);国家自然科学基金(61772548)
Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest
LYU Guohua1, HU Xuexian1, YANG Ming1, XU Min2( )
)
- 1. Strategic Support Force Information Engineering University, Zhengzhou 450001, China
2. Jinzhou Medical University, Jinzhou 121000, China
-
Received:2021-10-29Online:2022-04-10Published:2022-05-12 -
Contact:XU Min E-mail:powerhua@163.com
摘要:
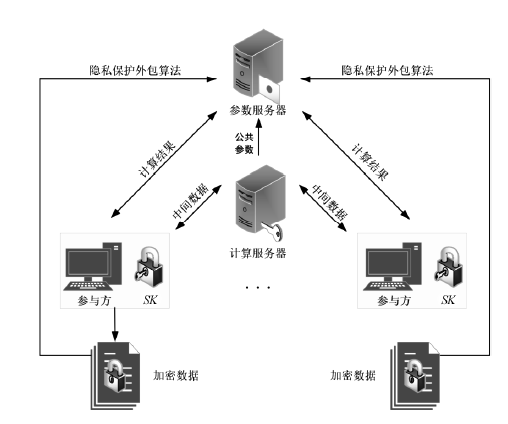
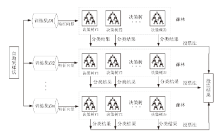
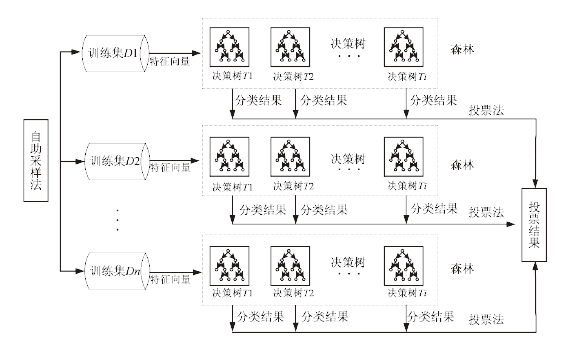
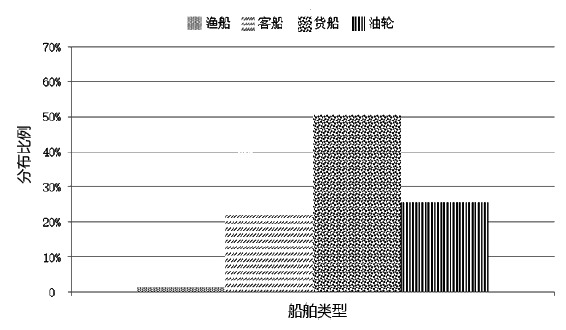
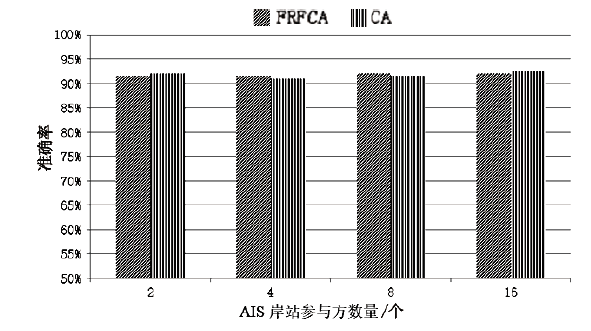
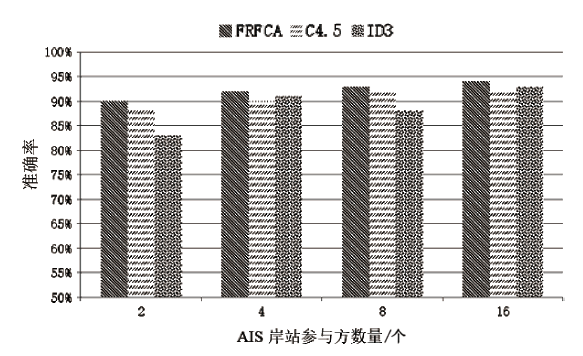
为了提升船舶AIS轨迹数据的分类效果、实现多权属数据安全联合数据挖掘,文章提出一种基于联邦随机森林的船舶AIS轨迹分类算法,利用BCP同态加密算法构造平均隐私保护协议,解决联邦学习中多参与方安全协同训练决策树问题。文章通过分析船舶AIS轨迹数据提取最优轨迹特征,并使用相应的特征向量作为联邦学习模型的输入,实现对渔船、客船、货船和油轮4类典型船舶的联邦分类。从准确性和有效性两方面进一步进行验证,结果表明该算法能够在保证数据隐私安全的前提下实现良好的分类效果,降低了参与方客户端的计算开销,实现多权属数据安全联合数据挖掘。同时,此研究成果可应用于船舶航迹模式识别和航迹分析预测等领域。
中图分类号:
引用本文
吕国华, 胡学先, 杨明, 徐敏. 基于联邦随机森林的船舶AIS轨迹分类算法[J]. 信息网络安全, 2022, 22(4): 67-76.
LYU Guohua, HU Xuexian, YANG Ming, XU Min. Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest[J]. Netinfo Security, 2022, 22(4): 67-76.
| [1] | LI Hongxiang, FANG Xun. Statistical Method Research of Vessel Traffic Flow Based on AIS[J]. Journal of Wuhan University of Technology, 2011, 35(4): 853-857. |
| 李红祥, 方逊. 基于AIS的船舶交通流量统计方法研究[J]. 武汉理工大学学报, 2011, 35(4): 853-857. | |
| [2] | CHRISTINA T P, ANNA R, JOUNI M. EU General Data Protection Regulation: Changes and Implications for Personal Data Collecting Companies[J]. Computer Law & Security Review, 2018, 34(1): 134-153. |
| [3] | MCMAHAN H B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[C]// AISTATS. 20th International Conference on Artificial Intelligence and Statistics. Massachusetts: PMLR, 2017: 1273-1282. |
| [4] | YANG Qiang, LIU Yang, CHENG Yong, et al. Federated Learning[M]. Beijing: Publishing House of Electronics Industry, 2020. |
| 杨强, 刘洋, 程勇, 等. 联邦学习[M]. 北京: 电子工业出版社, 2020. | |
| [5] | AGRAWAL R, SRIKANT R. Privacy Preserving Data Mining[C]// ACM. 2000 ACM SIGMOD International Conference on Management of Data. New York: ACM, 2000: 439-450. |
| [6] | ZHAN J, MATWIN S, CHANG Liwu. Privacy-Preserving Decision Tree Classification over Horizontally Partitioned Data[C]// ICEB. 5th International Conference on Electronic Business. Athens: ICEB, 2005: 470-476. |
| [7] |
EMEKCI F, SAHIN O D, AGRAWAL D, et al. Privacy Preserving Decision Tree Learning over Multiple Parties[J]. Data Knowledge Engineering, 2007, 63(2): 348-361.
doi: 10.1016/j.datak.2007.02.004 URL |
| [8] | VAIDYA J, CLIFTON C, KANTARCIOGLU M, et al. Privacy-Preserving Decision Trees over Vertically Partitioned Data[J]. ACM Transactions on Knowledge Discovery from Data, 2008, 2(3): 1-27. |
| [9] | WATSON G L, XIONG Di, ZHANG Lu, et al. Pandemic Velocity: Forecasting COVID-19 in the US with a Machine Learning and Bayesian Time Series Compartmental Model[EB/OL]. (2021-03-29)[2021-06-13]. https://pubmed.ncbi.nlm.nih.gov/33780443/ . |
| [10] | ENDER K, BEN G. Random Forests in Medical Image Computing[EB/OL]. (2019-10-25)[2021-01-22]. https://doi.org/10.1016/B978-0-12-816176-0.00024-7. |
| [11] | KRAUS P, MOHRDIECK C, SCHWENKER F. Ship Classification Based on Trajectory Data with Machine Learning Methods[EB/OL]. (2018-06-20)[2021-02-11]. https://ieeexplore.ieee.org/document/8448028 . |
| [12] | ZHANG Chengkai, BIN Junchi, PENG Xiang, et al. AIS Data Driven General Vessel Destination Prediction: A Random Forest Based Approach[EB/OL]. (2020-07-09)[2021-01-23]. https://www.sciencedirect.com/science/article/abs/pii/S0968090X20306446 . |
| [13] | YANG Qiang, LIU Yang, CHEN Tianjian, et al. Federated Machine Learning: Concept and Applications[J]. ACM Transactions on Intelligent Systems and Technology, 2019, 10(2): 1-19. |
| [14] |
BREIMAN L. Random Forests[J]. Machine Learning, 2001, 45(1): 5-32.
doi: 10.1023/A:1010933404324 URL |
| [15] | QUINLAN J. C4.5: Programms for Machine Learning[M]. San Francisco: Morgan Kaufmann Publishers, 1995. |
| [16] | BRESSON E, CATALANO D, POINTCHEVAL D. A Simple Public-Key Cryptosystem with a Double Trapdoor Decryption Mechanism and its Applications[C]// ASIACRYPT. 9th International Conference on the Theory and Application of Cryptology and Information Security. Berlin: LNCS, 2003: 37-54. |
| [17] |
PETER A, TEWS E, KATZENBEISSER S. Efficiently Outsourcing Multiparty Computation under Multiple Keys[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(12): 2046-2058.
doi: 10.1109/TIFS.2013.2288131 URL |
| [18] | LIU Yang, KANG Yan, ZHANG Xinwei, et al. Asymmetrical Vertical Federated Learning[EB/OL]. (2020-06-11)[2021-01-18]. https://arxiv.org/pdf/2004.07427.pdf . |
| [19] | JAGANNATHAN G, WRIGHT R N. Privacy-Preserving Distributed K-Means Clustering over Arbitrarily Partitioned Data[C]// ACM. 11th ACM SIGKDD International Conference on Knowledge Discovery in Data Mining. New York: ACM, 2005: 593-599. |
| [20] |
LI Ye, WANG Xuan, YAO Lin, et al. Outsourced Privacy-Preserving C4.5 Decision Tree Algorithm over Horizontally and Vertically Partitioned Dataset among Multiple Parties[J]. Cluster Computing, 2019, 22(1): 1581-1593.
doi: 10.1007/s10586-017-1019-9 URL |
| [21] | WANG Weigang, CHU Xiumin, JIANG Zhonglian, et al. Classification of Ship Trajectory Based on the Weighted Naive Bayes Algorithm[J]. Navigation of China, 2020, 43(4): 20-26. |
| 王维刚, 初秀民, 蒋仲廉, 等. 基于加权朴素贝叶斯的船舶轨迹分类算法[J]. 中国航海, 2020, 43(4): 20-26. |
| [1] | 白宏鹏, 邓东旭, 许光全, 周德祥. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. |
| [2] | 徐硕, 张睿, 夏辉. 基于数据属性修改的联邦学习隐私保护策略[J]. 信息网络安全, 2022, 22(1): 55-63. |
| [3] | 路宏琳, 王利明, 杨婧. 一种新的参数掩盖联邦学习隐私保护方案[J]. 信息网络安全, 2021, 21(8): 26-34. |
| [4] | 任涛, 金若辰, 罗咏梅. 融合区块链与联邦学习的网络入侵检测算法[J]. 信息网络安全, 2021, 21(7): 27-34. |
| [5] | 蔡满春, 王腾飞, 岳婷, 芦天亮. 基于ARF的Tor网站指纹识别技术[J]. 信息网络安全, 2021, 21(4): 39-48. |
| [6] | 林文兵, 张敏情, 周能, 孔咏骏. 基于同态加密的密文域可逆信息隐藏技术研究[J]. 信息网络安全, 2021, 21(4): 73-80. |
| [7] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [8] | 夏喆, 罗宾, 徐桂彬, 肖新秀. 智能电网中支持细粒度访问控制的隐私保护数据聚合方案[J]. 信息网络安全, 2021, 21(11): 28-39. |
| [9] | 徐国天. 基于异常加密流量标注的Android恶意进程识别方法研究[J]. 信息网络安全, 2020, 20(7): 30-41. |
| [10] | 李宁波, 周昊楠, 车小亮, 杨晓元. 云环境下基于多密钥全同态加密的定向解密协议设计[J]. 信息网络安全, 2020, 20(6): 10-16. |
| [11] | 周昊楠, 李宁波, 车小亮, 杨晓元. 基于素数幂次阶分圆多项式环的多密钥全同态方案[J]. 信息网络安全, 2020, 20(5): 83-87. |
| [12] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [13] | 傅智宙, 王利明, 唐鼎, 张曙光. 基于同态加密的HBase二级密文索引方法研究[J]. 信息网络安全, 2020, 20(4): 55-64. |
| [14] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [15] | 宋鑫, 赵楷, 张琳琳, 方文波. 基于随机森林的Android恶意软件检测方法研究[J]. 信息网络安全, 2019, 19(9): 1-5. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||