信息网络安全 ›› 2016, Vol. 16 ›› Issue (8): 24-31.doi: 10.3969/j.issn.1671-1122.2016.08.005
3GPP认证和密钥协商协议综述
- 1.西安邮电大学无线网络安全技术国家工程实验室,陕西西安 710121
2.中国科学院信息工程研究所信息安全国家重点实验室,北京 100093
-
收稿日期:2016-07-10出版日期:2016-08-20发布日期:2020-05-13 -
作者简介:作者简介: 赖成喆(1985—),男,陕西,讲师,博士,主要研究方向为无线网络安全;郑东(1964—),男,山西,教授,博士,主要研究方向为密码学和云计算安全。
-
基金资助:国家自然科学基金[61502386, 61472472, 61402366];陕西省国际科技合作与交流计划[2015KW-010]
Research on 3GPP Authentication and Key Agreement Protocols
Chengzhe LAI1,2( ), Dong ZHENG1
), Dong ZHENG1
- 1. National Engineering Laboratory for Wireless Security, Xi’an University of Posts and Telecommunications, Xi’an Shaanxi 710121, China
2. State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
-
Received:2016-07-10Online:2016-08-20Published:2020-05-13
摘要:
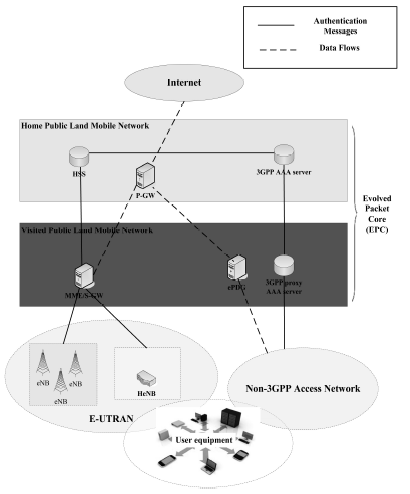
在移动通信标准化组织第三代合作伙伴计划(3GPP)制定的框架下,文章介绍了该框架的系统及安全架构。在此次基础上对3GPP的通信场景及其协议进行了分类,分别介绍了3种接入网类型——3GPP接入(3GPP Access)、可信非3GPP接入(Trusted non-3GPP Access)以及不可信非3GPP接入(Untrusted non-3GPP Access)下的认证和密钥协商协议。 此外,文章还介绍了面向机器类型通信的基于群组的安全协议;最后,指出了该领域未来的研究方向。
中图分类号:
引用本文
赖成喆, 郑东. 3GPP认证和密钥协商协议综述[J]. 信息网络安全, 2016, 16(8): 24-31.
Chengzhe LAI, Dong ZHENG. Research on 3GPP Authentication and Key Agreement Protocols[J]. Netinfo Security, 2016, 16(8): 24-31.
| [1] | 黄韬,刘韵洁,张智江.LTE/SAE移动通信网络技术 [M].北京:人民邮电出版社, 2009. |
| [2] | 卢建军. 基于物联网的工业化与信息化模式研究[J]. 西安邮电学院学报, 2010, 15(6): 64-67. |
| [3] | 赵小强,雷雪,冯勋. 基于ZigBee/3G的物联网网关系统[J]. 西安邮电大学学报, 2015, 20(1): 24-29. |
| [4] | GILANI S. The Promise of M2M: How Pervasive Connected Machines are Fueling the Next Wireless Revolution [EB/OL]. , 2016-06-15. |
| [5] | 3GPP. TR .23.888 V1.4.0 System Improvements for Machine-Type Communications[S]. Sophia Antipolis Valbonne:3rd Generation Partnership Project, 2011. |
| [6] | 郑东, 赵庆兰, 张应辉. 密码学综述[J]. 西安邮电大学学报,2013,18(6): 1-10. |
| [7] | CHADCHAN S M, AKKI C B.3GPP LTE/SAE: An Overview[J]. International Journal of Computer and Electrical Engineering, 2010, 2(5): 806. |
| [8] | 3GPP. TS. 33.401 V12.5.0 System Architecture Evolution (SAE); Security architecture[S]. Sophia Antipolis Valbonne:3rd Generation Partnership Project, 2012. |
| [9] | DORASWAMY N, HARKINS D.IPSec: the New Security Standard for the Internet, Intranets, and Virtual Private Networks[M]. New Jersey: Prentice Hall Professional, 2003. |
| [10] | TTC.TR 29.060 V11.3.0 GPRS Tunnelling Protocol (GTP) across the Gn and Gp interface [EB/OL]. . |
| [11] | 3GPP. TR 29.275 v. 11.3.0 Proxy Mobile IPv6 (PMIPv6) based Mobility and Tunnelling protocols[S]. Sophia Antipolis Valbonne:3rd Generation Partnership Project, 2012. |
| [12] | Network Working Group.RFC 4187 Extensible Authentication Protocol Method for 3rd Generation Authentication and Key Agreement (EAP-AKA)[S]. Finland:Internet Engineering Task Force, 2006. |
| [13] | Network Working Group.RFC 5448 Improved Extensible Authentication Protocol Method for 3rd Generation Authentication and Key Agreement (EAP-AKA)[S]. Finland:Internet Engineering Task Force, 2009. |
| [14] | KOIEN G M.An Introduction to Access Security in UMTS[J]. IEEE Wireless Communications, 2004, 11(1): 8-18. |
| [15] | 3GPP. TS 21.133 V4.1.0 3G Security; Security Threats and Requirements[S]. Sophia Antipolis Valbonne:3rd Generation Partnership Project, 2001. |
| [16] | ZHANG M X, FANG Y G.Security Analysis and Enhancements of 3GPP Authentication and Key Agreement protocol[J]. IEEE Trans. Wirel. Commun, 2005, 4(2): 734-742. |
| [17] | JUANG W, WU J.Efficient 3GPP Authentication and Key Agreement with Robust User Privacy Protection[C]//IEEE. International Conference on IEEE Wireless Communications and Networking, March 11-15, 2007, Hong Kong, China. New York: IEEE, 2007: 2722-2727. |
| [18] | OU H, HWANG M, JAN J.A Cocktail Protocol with the Authentication and Key Greement on the UMTS[J]. J. Syst. Softw, 2010, 83(2): 316-325. |
| [19] | WU S H, ZHU Y F, PU Q.Security Analysis of a Cocktail Protocol with the Authentication and Key Agreement on the UMTS[J]. IEEE Commun. Lett, 2010, 14(4): 366-368. |
| [20] | HUANG Y L, SHEN C Y, SHIEH S W.S-AKA: a Provable and Secure Authentication Key Agreement Protocol for UMTS Networks[J]. IEEE Trans. Veh. Technol, 2011, 60(9): 4509-4519. |
| [21] | LIN Y, CHEN Y.Reducing Authentication Signaling Traffic in Third-generation Mobile Network[J]. IEEE Transaction on Wireless Communications, 2003, 2(3): 493-501. |
| [22] | HUANG C, LI J.Authentication and Key Agreement Protocol for UMTS with Low Bandwidth Consumption[C]// IEEE. 19th IEEE International Conference on Advanced Information Networking and Applications (AINA), March 28-30, 2005, Taiwan, China. New York: IEEE, 2005: 392-397. |
| [23] | AL-SARAIREH J, YOUSEF S.A New Authentication Protocol for UMTS Mobile Networks[J]. EURASIP Journal of Wireless Communications and Networking, 2006, 2006(4): 1-10. |
| [24] | LEE C, CHEN C, OU H, et al.Extension of an Efficient 3GPP Authentication and Key Agreement Protocol[J]. Wireless Personal Communications 2013, 68(3):861-872. |
| [25] | 陆蜂,郑康锋,钮心忻,等. 3GPP认证与密钥协商协议安全性分析[J]. 软件学报, 2010, 21(7): 1768-1782. |
| [26] | JIANG Y X, LIN C, SHEN X, et al.Mutual Authentication and Key Exchange Protocols for Roaming Services in Wireless Mobile Networks[J]. IEEE Trans. Wireless Commun, 2006, 5(9): 2569-2577. |
| [27] | SHI M H, RUTAGEMWA H, SHEN X, et al.A Service-agentbased Roaming Architecture for WLAN/Cellular Integrated Networks[J]. IEEE Trans. Veh. Technol., 2007, 56(5): 3168-3181. |
| [28] | YANG G M, HUANG Q, WONG D S, et al.Universal Authentication Protocols for Anonymous Wireless Communications[J]. IEEE Trans. Wireless Commun, 2010, 9(1): 168-174. |
| [29] | HE Daojing, BU Jiajun, CHAN S, et al.Privacy-preserving Universal Authentication Protocol for Wireless Communications[J]. IEEE Trans. Wireless Commun, 2011, 10(2): 431-436. |
| [30] | CHUANG M, LEE J, CHEN M.SPAM: A Secure Password Authentication Mechanism for Seamless Handover in Proxy Mobile IPv6 Networks[J].IEEE Systems Journal, 2013, 7(1): 102-113. |
| [31] | WAN Z, REN K, PRENEEL B.A Secure Privacy-preserving Roaming Protocol Based on Hierarchical Identity-based Encryption for Mobile Networks[C]// ACM. ACM Conference on Wireless Network Security, WISEC 2008, March 31-April, Alexandria. New York: ACM,2008:62-67. |
| [32] | KIM Y, REN W, JO J, et al.SFRIC: A Secure Fast Roaming Scheme in Wireless LAN Using ID-based Cryptography[C]// IEEE. IEEE ICC, June 24-28, 2007, Glasgow. New York: IEEE, 2007: 1570-1575. |
| [33] | REN J, HARN L.An Efficient Threshold Anonymous Authentication Scheme for Privacy-preserving Communications[J]. IEEE Trans. Wireless Commun, 2013, 12(3): 1018-1025. |
| [34] | LAI C Z, LI H, LIANG X H, et al.CPAL: A Conditional Privacy-preserving Authentication with Access Linkability for Roaming Service[J]. IEEE Internet of Things Journal, 2014, 1(1): 46-57. |
| [35] | MUN H, HAN K, KIM K.3G-WLAN Interworking: Security Analysis and New Authentication and Key Agreement Based on EAP-AKA[C]//IEEE. IEEE Wireless Telecommunications Symposium WTS, April 22-24, 2009, Prague. New York: IEEE, 2009: 1-8. |
| [36] | NTANTOGIAN C, XENAKIS C.One-pass EAP-AKA Authentication in 3GWLAN Integrated Networks[J]. Wirel. Pers. Commun, 2009, 48(4): 569-584. |
| [37] | AHMAVAARA K, HAVERINEN H, PICHNA R.Interworking Architecture between 3GPP and WLAN Systems[J]. IEEE Commun Mag, 2003, 41(11): 74-81. |
| [38] | PRASITHSANGAREE P, KRISHNAMURTHY P.A New Authentication Mechanism for Loosely Coupled 3G-WLAN Integrated Networks[C]// IEEE. IEEE Vehicular Technology Conference, May 17-19, 2004, Seoul. New York: IEEE, 2004: 2998-3003. |
| [39] | SHIDHANI A, LEUNG V.Fast and Secure Reauthentications for 3GPP Subscribers during WiMAX-WLAN Handovers[J]. IEEE Trans. Dependable Secur. Comput, 2011, 8(5) : 699-713. |
| [40] | OTHMEN S, ZARAI F, OBAIDAT M.et al.Re-authentication Protocol from WLAN to LTE (ReP WLAN-LTE)[C]// IEEE. IEEE Global Communication Conference (GLOBECOM), December 9-13, 2013, Atlanta. New York: IEEE, 2013: 1446-1451. |
| [41] | Network Working Group.RFC 4423 Host Identity Protocol (HIP) Architecture[S]. California:Internet Engineering Task Force, 2006. |
| [42] | RFC 5201 Host Identity Protocol[S].California: Internet Engineering Task Force, 2008. |
| [43] | MOSKOWITZ R. HIP Diet EXchange (DEX), IETF Internet Draft (Work in Progress), draft-moskowitz-hip-rg-dex-06 [EB/OL]. , 2016-06-15. |
| [44] | CHEN Y W, WANG J T, CHI K H, et al.Group-based Authentication and Key Agreement[J]. Wirel. Pers. Commun, 2012, 62(4): 965-979. |
| [45] | LAI C Z, LI H, LI X Q, et al.A Novel Group Access Authentication and Key Agreement Protocol for Machine-type Communication[J].Transactions on Emerging Telecommunications Technologies, 2015, 26(3): 414-431. |
| [46] | LAI C Z, LI H, LU R, et al.SE-AKA: A Secure and Efficient Group Authentication and Key Agreement Protocol for LTE Networks[J]. Computer Networks, 2013, 57(17) : 3492-3510. |
| [47] | JIANG R, LAI C, LUO J, et al.EAP-Based Group Authentication and Key Agreement Protocol for Machine-Type Communications[J].International Journal of Distributed Sensor Networks, 2013, 2013(6): 1-14. |
| [48] | YANG T T, LAI C Z, LU R, et al.EAPSG: Efficient Authentication Protocol for Secure Group Communications in Maritime Wideband Communication Networks[J]. Peer-to-Peer Networking and Applications, 2014, 7(1): 1-13. |
| [49] | HUANG J, YEH L, CHIEN H.ABAKA: An Anonymous Batch Authenticated and Key Agreement Scheme for Value-Added Services in Vehicular Ad Hoc Networks[J]. IEEE Transactions on Vehicular Technology, 2011, 60(1): 248-262. |
| [50] | CAO J, MA M D, LI H.A Group-based Authentication and Key Agreement for MTC in LTE Networks[C]//IEEE. IEEE Global Communications Conference (GLOBECOM), December 3-7, 2012, Anaheim. New York: IEEE, 2012: 1017-1022. |
| [51] | LAI C Z, LI H, LU R, et al.SEGR: A Secure and Efficient Group Roaming Scheme for Machine to Machine Communications between 3GPP and WiMAX Networks[C]// IEEE. IEEE International Conference on Communication, June 10-14, 2014, Sydney. New York: IEEE, 2014: 1011-1016. |
| [52] | LAI C Z, LU R, ZHENG D, et al.GLARM: Group-based Lightweight Authentication Scheme for Resource-constrained Machine to Machine Communications[J]. Computer Networks, 2016: 66-81. |
| [53] | DIFFIE W, HELLMAN M.New Directions in Cryptography[J]. IEEE Transactions on Information Theory, 1976, 22(6): 644-654. |
| [54] | GARG S, GENTRY C, HALEVI S.Candidate Multilinear Maps from Ideal Lattices[C]// Springer. International Association for Cryptologic Research. Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 26-30, 2013, Athens. Berlin Heidelberg:Springer , 2013: 1-17. |
| [55] | HU Y P, JIA H W.Cryptanalysis of GGH Map[C]// International Association for Cryptologic Research. Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 8-12, 2016, Vienna. Berlin Heidelberg:Springer , 2016: 537-565. |
| [1] | 李赓;赵玉萍;孙春来;肖如吾. CDD无线通信网络安全研究[J]. , 2013, 13(10): 0-0. |
| [2] | 任伟. 无线网络安全问题初探[J]. , 2012, 12(1): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||