信息网络安全 ›› 2015, Vol. 15 ›› Issue (2): 57-65.doi: 10.3969/j.issn.1671-1122.2015.02.010
基于特征分析和行为监控的未知木马检测系统研究与实现
- 1.北京大学软件与微电子学院,北京 102600
2.洛阳电子装备试验中心,河南洛阳 471003
Research and Implementation on Unknown Trojan Detection System Based on Feature Analysis and Behavior Monitoring
HAO Zeng-shuai1, GUO Rong-hua2, WEN Wei-ping1( ), MENG Zheng1
), MENG Zheng1
- 1. School of Software & Microelectronics, Peking University, Beijing 102600, China
2.LEETC, Luoyang Henan 471003, China
摘要:
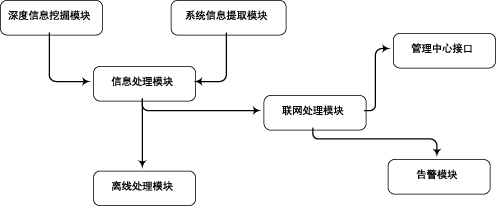
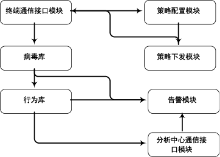
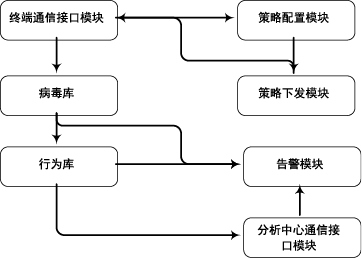
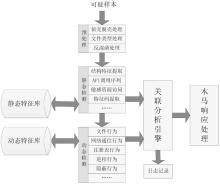
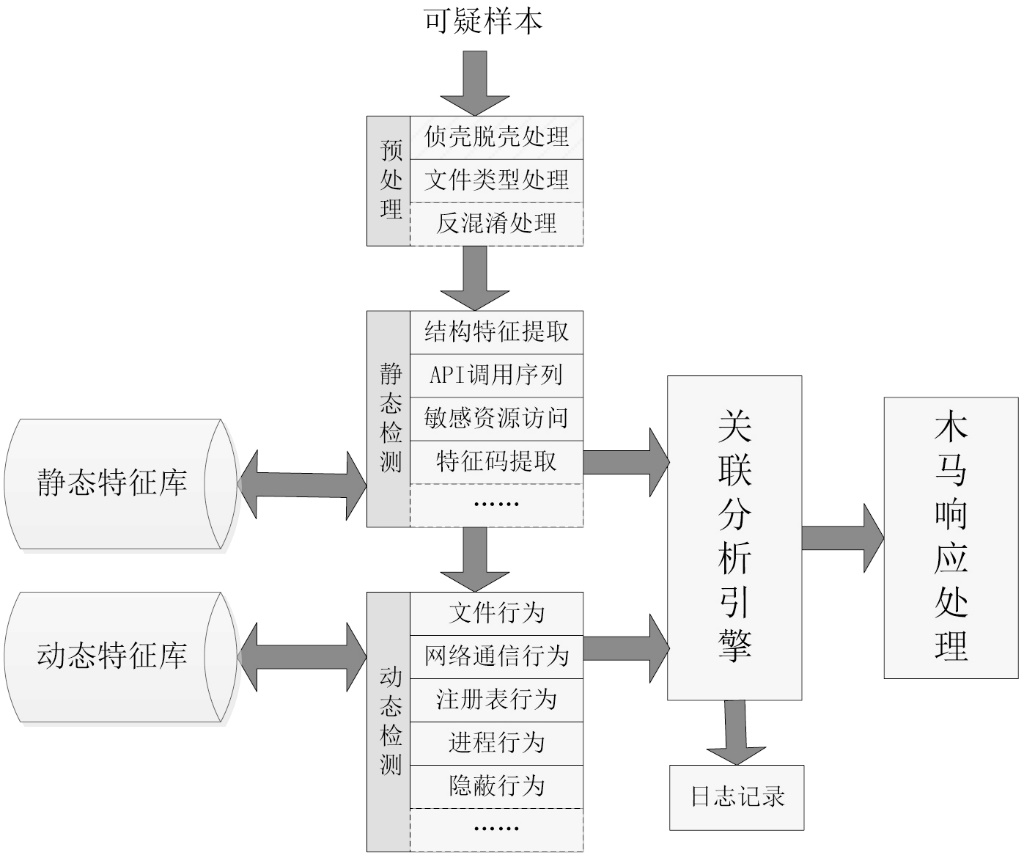
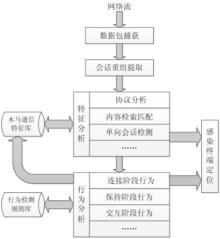
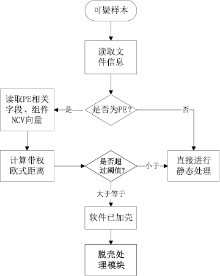
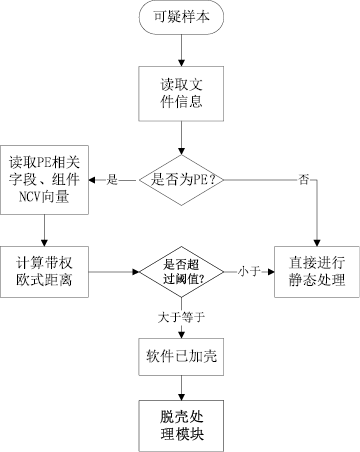
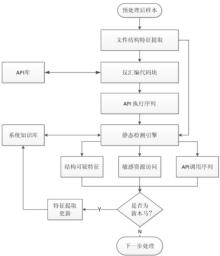
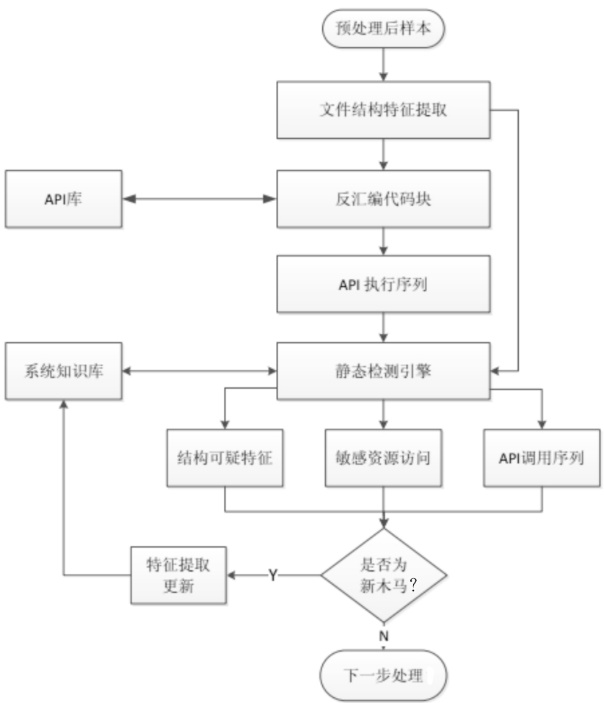
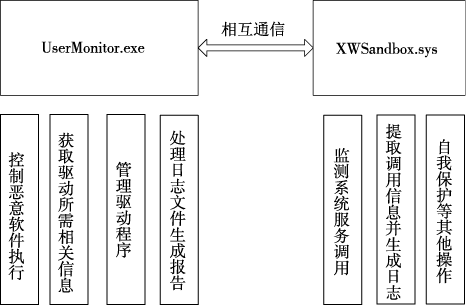
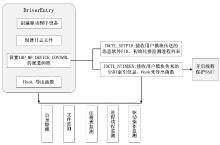
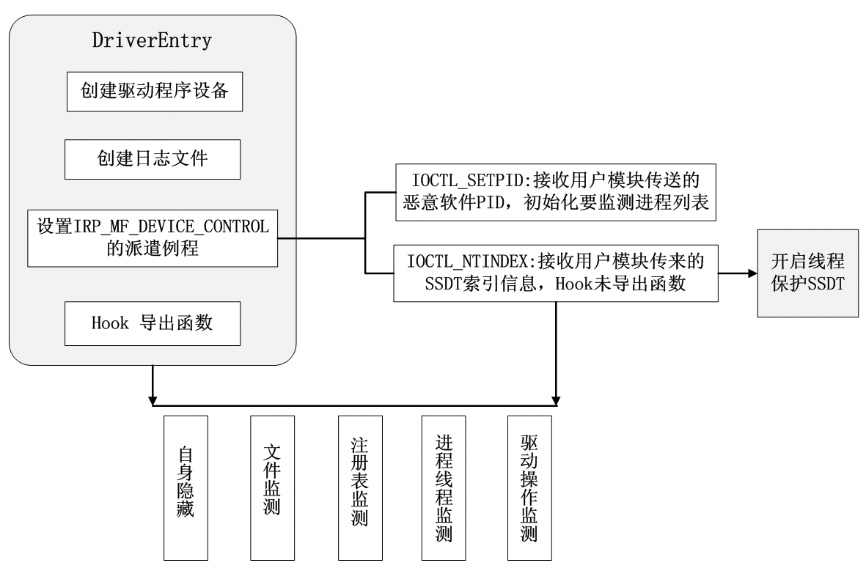
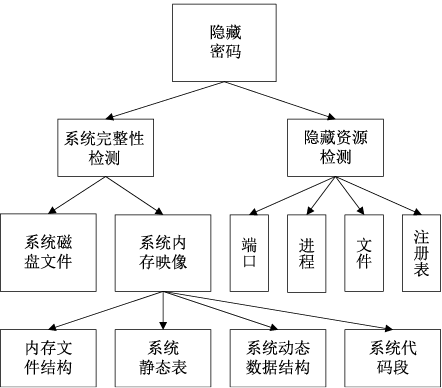
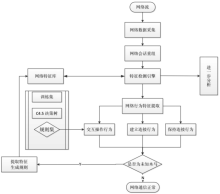
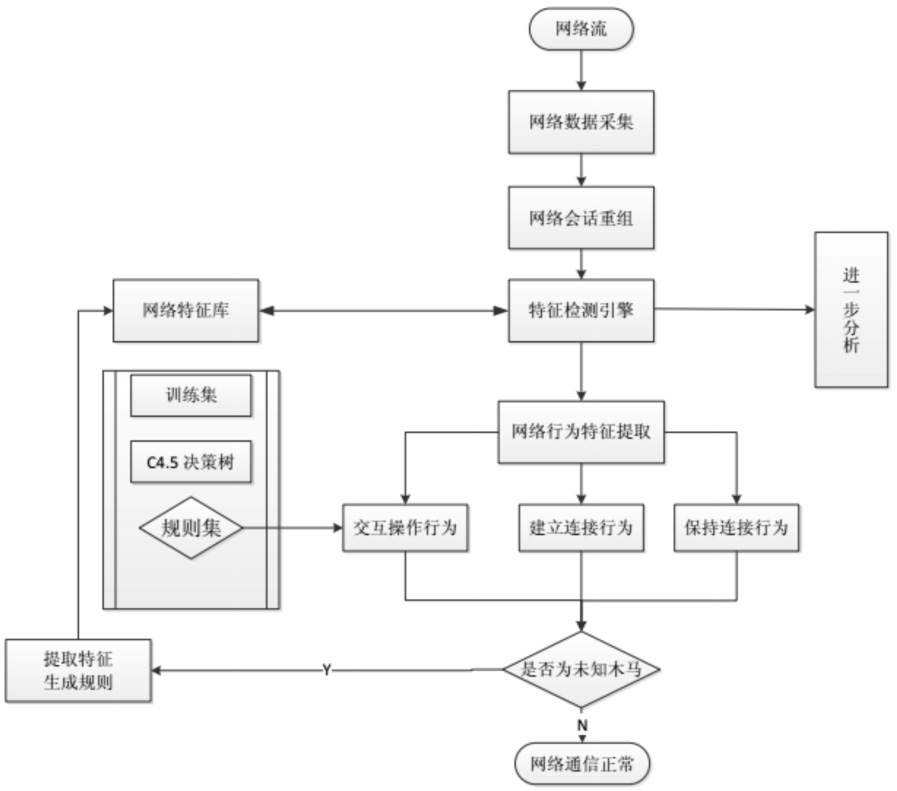
木马是以盗取用户个人信息和文件数据,甚至是以远程控制用户计算机为主要目的并尽可能隐藏自身的恶意程序。近年来,随着黑客行为的职业化、利益化和集团化,网络入侵与攻击手段日新月异,木马等恶意代码已成为我国网络安全的重要威胁。现阶段,木马检测通常依赖于病毒软件的检测能力,防病毒软件一般采用特征码比对和行为识别的方式进行木马查杀,这种方式需要防病毒软件拦截木马样本进行分析,提取木马样本,对木马特种库进行升级后对木马进行识别,滞后性很强,无法对新出现的或无已知特征的木马进行查杀。文章对木马反杀毒技术、隐藏技术、突破主动防御技术进行探讨,并以此为基础,提出基于特征分析和行为监控的木马检测技术,完成了未知木马检测系统的设计与实现,能够在一定程度上弥补现有防病毒软件及安全措施只能查杀和监测已知木马而不能识别和查杀未知木马的不足。
中图分类号: