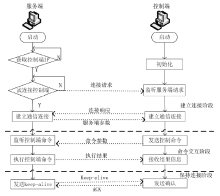
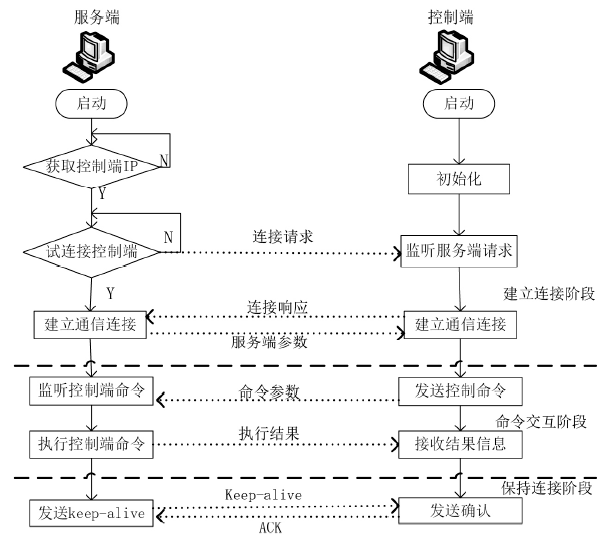
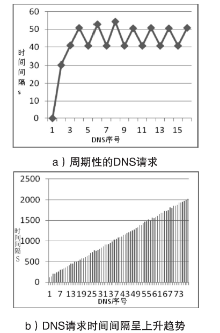
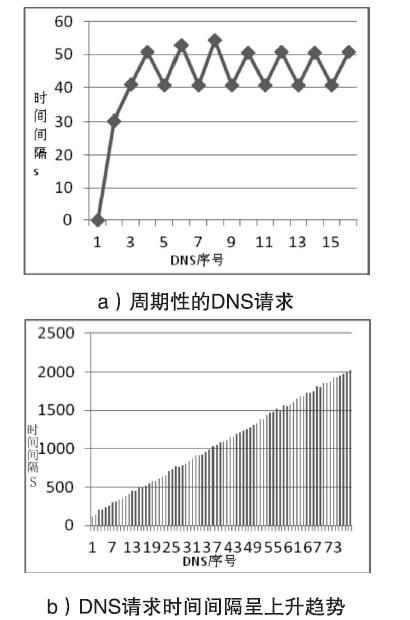
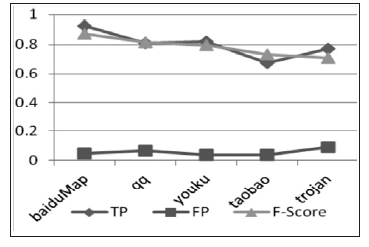
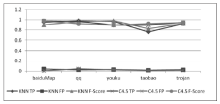
| [1] |
国家互联网应急中心.CNCERT互联网安全威胁报告[EB/OL]. .
|
| [2] |
Kolter J Z, Maloof M A.Learning to detect and classify malicious executables in the wild[J]. The Journal of Machine Learning Research, 2006,(7): 2721-2744.
|
| [3] |
Gao D, Reiter M K, Song D.Binhunt: Automatically finding semantic differences in binary programs[M]. Heidelberg: Springer Berlin, 2008.
|
| [4] |
Chen Q Z, Cheng R, Gu Y J.Classification algorithms of Trojan horse detection based on behavior[C]// International Conference on IEEE, 2009, (2): 510-513.
|
| [5] |
liu Yu feng, Zhang Li-wei, Liang Jian, et al. Detecting trojan horses based on system behavior using machine learning method[C]// Proceedings of the Ninth International Conference on Machine Learning and Cybernetics, Qingdao, 2010,(7):11-14 .
|
| [6] |
Bayer U, Comparetti P M, Hlauschek C, et al.Scalable, Behavior-Based Malware Clustering[C]//NDSS. 2009, (9): 8-11.
|
| [7] |
韩奕. 基于行为分析的恶意代码检测与评估研究[D].北京:北京交通大学,2014.
|
| [8] |
Kirda E, Kruegel C, Banks G, et al.Behavior-based Spyware Detection[C]// Usenix Security,2006.
|
| [9] |
商海波. 木马的行为分析及新型反木马策略的研究[D].杭州:浙江工业大学,2005.
|
| [10] |
Qin J, Yan H, Si Q, et al.A Trojan horse Detection Technology Based on Behavior Analysis[C]// Proceedings of Wireless Communications Networking and Mobile Computing (WiCOM), 2010 6th International Conference on,2010: 1-4.
|
| [11] |
Valenti S, Rossi D, Dainotti A, et al.Reviewing traffic classification[M]. Heidelberg: Springer Berlin ,2013.
|
| [12] |
Xue Y, Wang D, Zhang L.Traffic classification: Issues and challenges[C]//Computing, Networking and Communications (ICNC), 2013 International Conference on. IEEE, 2013: 545-549.
|
| [13] |
姚姜源. 基于网络通信内容的木马检测系统设计与实现[D].北京:北京交通大学,2009.
|
| [14] |
Myers A, Nystrom N, Zheng L, et al. Java Information flow [EB/OL]. .
|
| [15] |
Perdisci R, Lee W, Feamster N.Behavior clustering of Http-based malware and signature generation using malicious network traces [EB/OL]. ,2011.
|
| [16] |
Li S, Yun X, Zhang Y, et al.A General Framework of Trojan Communication Detection Based on Network Traces[C]//Networking, Architecture and Storage (NAS), 2012 IEEE 7th International Conference on. IEEE, 2012: 49-58.
|
| [17] |
Li S, Yun X C, Zhang Y Z, et al.A novel approach of detecting Trojan based on network behavior analysis[C]// Communication Technology (ICCT), 2012 IEEE 14th International Conference on. IEEE, 2012: 513-518.
|
| [18] |
Meng L, Liu S L, Liu L, et al.Trojan Rapid Detection Method Based on Heartbeat Behavior Analysis[J]. Computer Engineering, 2012, (14): 5.
|
| [19] |
孙海涛. 基于通信行为分析的木马检测技术[D].郑州:解放军信息工程大学,2011.
|
| [20] |
唐彰国,李焕洲,等.基于网络通信指纹的启发式木马识别系统[J]. 计算机工程,2011,(9): 119-122.
|
| [21] |
Xiaochen Zhang, Shengli Liu, et al.Trojan Detection Based on Network Flow Clustering[C]// 2012 Fourth International Conference on Mutimedia Information Networking and Security,2012.
|
| [22] |
Zhang J, Chen C, Xiang Y, et al.An effective network traffic classification method with unknown flow detection[J]. Network and Service Management, IEEE Transactions on, 2013, 10(2): 133-147.
|
| [23] |
Zhang J, Chen X, Xiang Y, et al. Robust Network Traffic Classification[J]. IEEE/ACM Trans. Netw,2014,pp(99):1-14.
|
 ), LI Jia2, LIN Shen-wen2
), LI Jia2, LIN Shen-wen2