信息网络安全 ›› 2014, Vol. 14 ›› Issue (11): 70-73.doi: 10.3969/j.issn.1671-1122.2014.11.012
二阶SQL注入攻击防御模型
- 杭州电子科技大学通信工程学院,浙江杭州 310008
Second-order SQL Injection Attack Defense Model
TIAN Yu-jie( ), ZHAO Ze-mao, ZHANG Hai-chuan, LI Xue-shuang
), ZHAO Ze-mao, ZHANG Hai-chuan, LI Xue-shuang
- Department of Communication Engineering, Hangzhou Dianzi University, Hangzhou Zhejiang 310008, China
摘要:
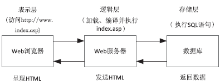
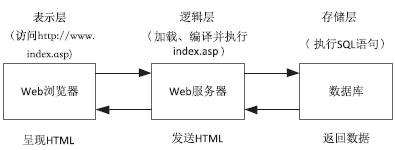
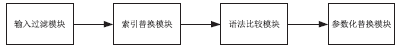
随着互联网技术的快速发展, Web应用程序的使用也日趋广泛,其中基于数据库的Web应用程序己经广泛用于企业的各种业务系统中。然而由于开发人员水平和经验参差不齐,使得Web应用程序存在大量安全隐患。影响Web应用程序安全的因素有很多,其中SQL注入攻击是最常见且最易于实施的攻击, 且SQL注入攻击被认为是危害最广的。因此,做好SQL注入攻击的防范工作对于保证Web应用程序的安全十分关键, 如何更有效地防御 SQL 注入攻击成为重要的研究课题。SQL注入攻击利用结构化查询语言的语法进行攻击。传统的SQL注入攻击防御模型是从用户输入过滤和SQL语句语法比较的角度进行防御,当数据库中的恶意数据被拼接到动态SQL语句时,就会导致二阶SQL注入攻击。文章在前人研究的基础上提出了一种基于改进参数化的二阶SQL注入攻击防御模型。该模型主要包括输入过滤模块、索引替换模块、语法比较模块和参数化替换模块。实验表明,该模型对于二阶SQL注入攻击具有很好的防御能力。
中图分类号: