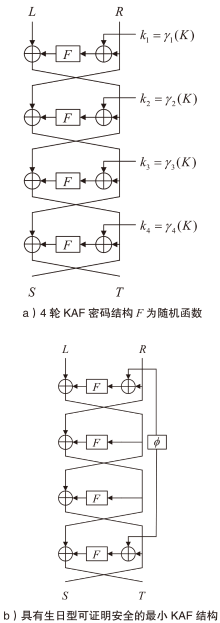
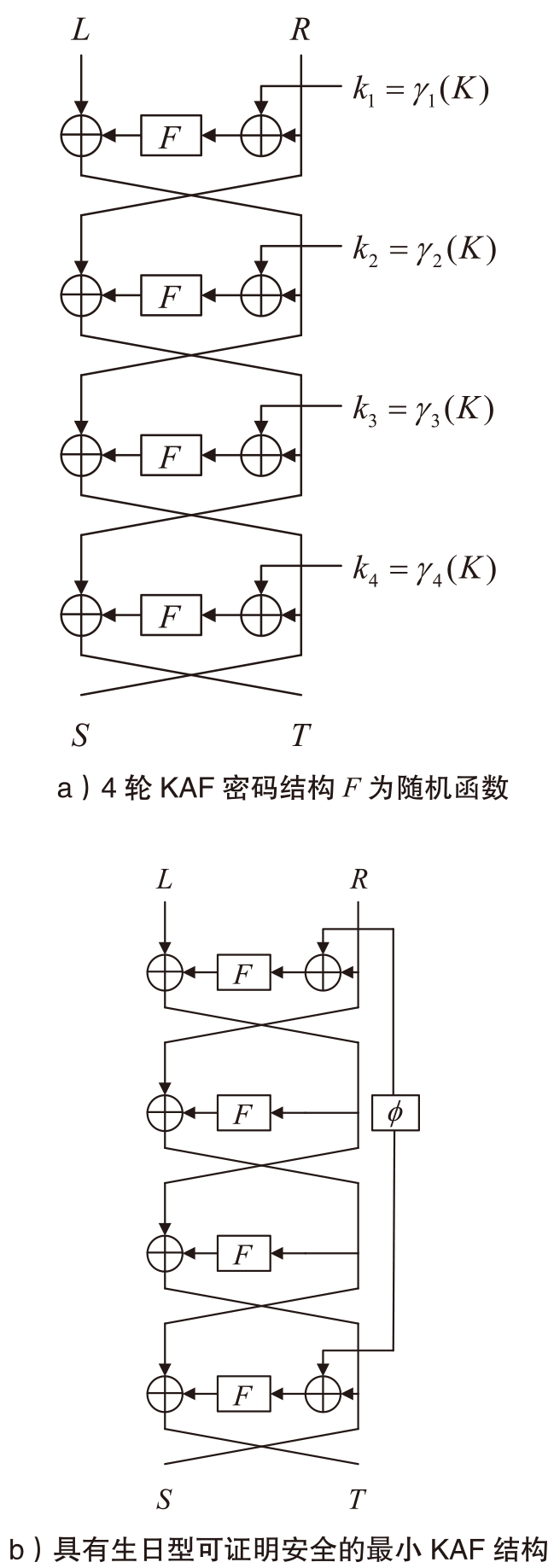
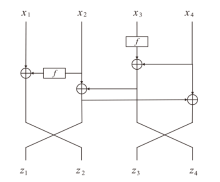
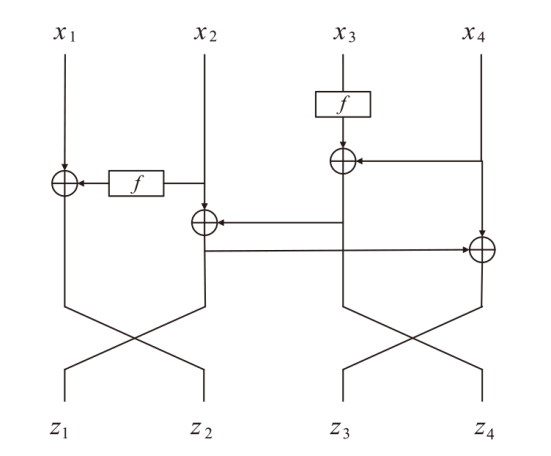
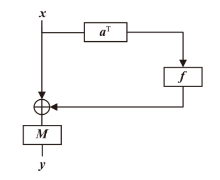
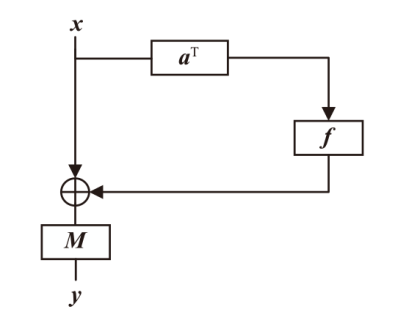
信息网络安全 ›› 2025, Vol. 25 ›› Issue (5): 722-731.doi: 10.3969/j.issn.1671-1122.2025.05.005
基于密码结构的正形置换研究
- 国防科技大学理学院,长沙 410073
-
收稿日期:2024-04-02出版日期:2025-05-10发布日期:2025-06-10 -
通讯作者:李康荃likangquan11@nudt.edu.cn -
作者简介:杨怡嘉(2000—),女,河南,硕士研究生,主要研究方向为密码分析|李康荃(1994—),男,江西,副教授,博士,主要研究方向为密码设计|孙兵(1981—),男,江苏,教授,博士,主要研究方向为密码分析 -
基金资助:国家自然科学基金(62272470);国家自然科学基金(U2336209);国防科技大学科研计划(ZK22-14)
Research on Orthomorphic Permutations Based on Cryptographic Structure
YANG Yijia, LI Kangquan( ), SUN Bing
), SUN Bing
- College of Science, National University of Defense Technology, Changsha 410073, China
-
Received:2024-04-02Online:2025-05-10Published:2025-06-10
摘要:
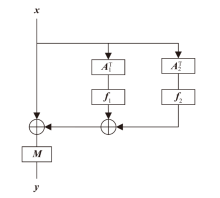
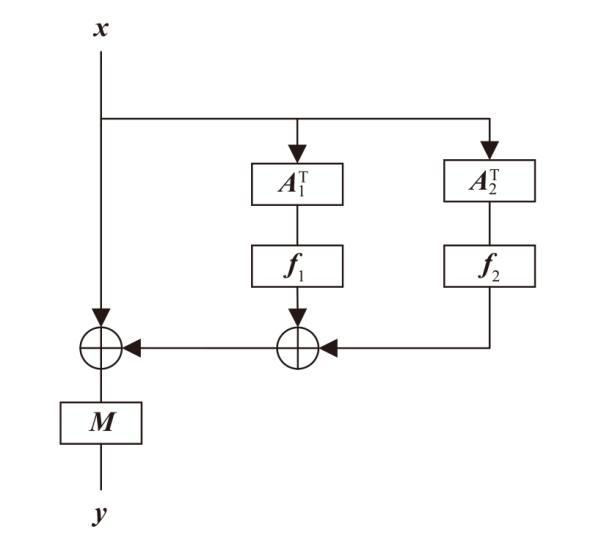
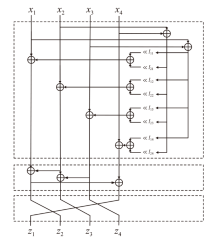
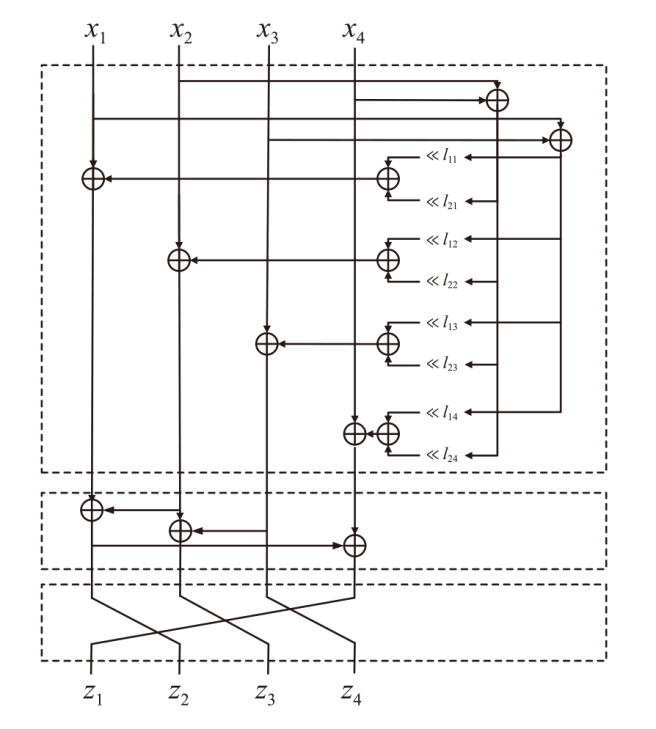
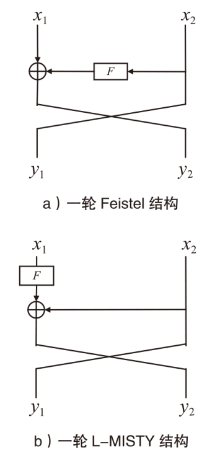
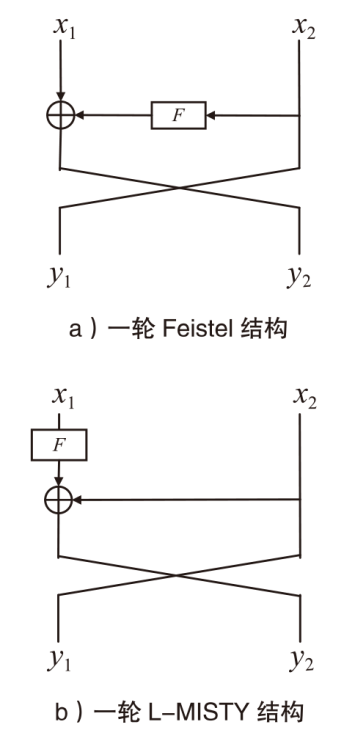
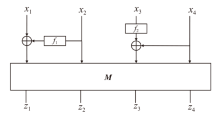
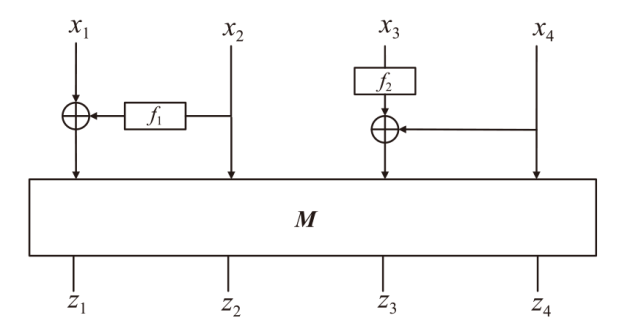
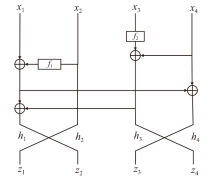
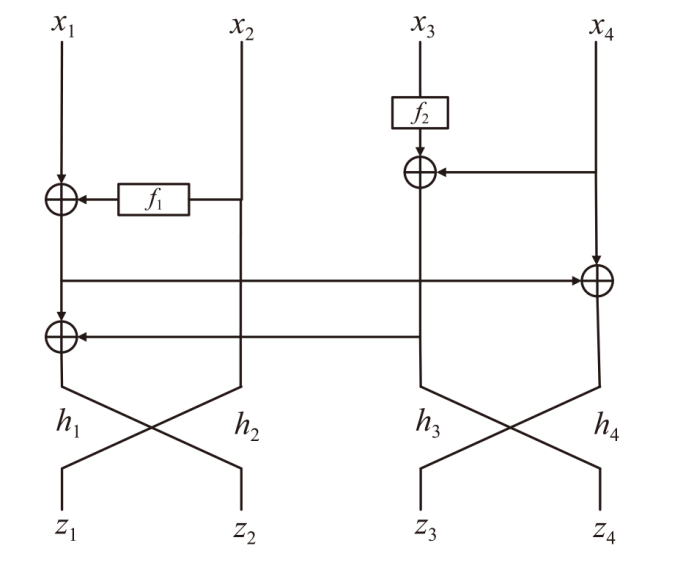
正形置换在密码和编码等领域具有广泛应用。文章利用密码结构对正形置换的构造进行研究,构造了偶特征扩域上基于两个轮函数的广义Feistel结构,在此基础上,利用矩阵的秩给出该变换为正形置换的条件。随后构造了两类偶特征扩域上的正形置换实例,第一类基于左移变换构造,第二类基于Feistel结构和L-MISTY结构构造。文章旨在构造遵循特定密码结构的正形置换,丰富正形置换的种类。
中图分类号:
引用本文
杨怡嘉, 李康荃, 孙兵. 基于密码结构的正形置换研究[J]. 信息网络安全, 2025, 25(5): 722-731.
YANG Yijia, LI Kangquan, SUN Bing. Research on Orthomorphic Permutations Based on Cryptographic Structure[J]. Netinfo Security, 2025, 25(5): 722-731.
| [1] | MANN H B. The Construction of Orthogonal Latin Squares[J]. The Annals of Mathematical Statistics, 1942, 13(4): 418-423. |
| [2] | PAIGE L. Complete Mappings of Finite Groups[J]. Pacific Journal of Mathematics, 1951, 1(1): 111-116. |
| [3] | NIEDERREITER H, ROBINSON K H. Complete Mappings of Finite Fields[J]. Journal of the Australian Mathematical Society, 1982, 33(2): 197-212. |
| [4] | MITTENTHAL L. Block Substitutions Using Orthomorphic Mappings[J]. Advances in Applied Mathematics, 1995, 16(1): 59-71. |
| [5] | VAUDENAY S. On the Lai-Massey Scheme[EB/OL]. [2024-01-15]. https://doi.org/10.1007/978-3-540-48000-6_2. |
| [6] | XIANG Shuang, TANG Yingqi, TONG Yan, et al. Cryptographic Analysis and Construction of Complete Permutations Using a Recursive Approach[J]. International Journal of Ad Hoc and Ubiquitous Computing, 2024, 45(2): 100-122. |
| [7] | WU Gaofei, FENG Keqin, LI Nian, et al. New Results on the-1 Conjecture on Cross-Correlation of M-Sequences Based on Complete Permutation Polynomials[J]. IEEE Transactions on Information Theory, 2023, 69(6): 4035-4044. |
| [8] | VISHWAKARMA C K, SINGH R P. Some Results on Complete Permutation Polynomials and Mutually Orthogonal Latin Squares[J]. Finite Fields and Their Applications, 2024, 93: 1-27. |
| [9] | LU Wei, WU Xia, WANG Yufei, et al. A General Construction of Regular Complete Permutation Polynomials[J]. Designs, Codes and Cryptography, 2023, 91(8): 2627-2647. |
| [10] | LU Wei, WU Xia, WANG Yufei, et al. Regular Complete Permutation Polynomials over Quadratic Extension Fields[J]. Designs, Codes and Cryptography, 2022, 90(3): 545-575. |
| [11] | MILEVA A, MARKOVSKI S. Quasigroup Representation of Some Feistel and Generalized Feistel Ciphers[EB/OL]. [2024-01-15]. https://doi.org/10.1007/978-3-642-37169-1_16. |
| [12] | MILEVA A, MARKOVSKI S. Quasigroup Representation of Some Lightweightblock Ciphers[J]. Quasigroups and Related Systems, 2014, 22(1): 267-276. |
| [13] | SUN Bing, LI Kangquan, GUO Jian, et al. New Constructions of Complete Permutations[J]. IEEE Transactions on Information Theory, 2021, 67(11): 7561-7567. |
| [14] | LIU Jingyan, XIAO Tongfei, NIE Shun, et al. Construction of Complete Permutation Polynomials Based on Cipher Structures[J]. Journal of Hubei University of Technology, 2022, 38(3): 54-58. |
| 刘静琰, 肖同飞, 聂顺, 等. 基于密码结构正形置换多项式的构造[J]. 湖北理工学院学报, 2022, 38(3): 54-58. | |
| [15] | XU Xiaofang, LI Chunlei, ZENG Xiangyong, et al. Constructions of Complete Permutation Polynomials[J]. Designs, Codes and Cryptography, 2018, 86(12): 2869-2892. |
| [16] | LIU Xiaochen, FENG Dengguo. Construction of S-Boxes with Some Cryptographic Properties[J]. Journal of Software, 2000, 11(10): 1299-1302. |
| 刘晓晨, 冯登国. 满足若干密码学性质的S- 盒的构造[J]. 软件学报, 2000, 11(10): 1299-1302. | |
| [17] | FENG Dengguo, FENG Xiutao, ZHANG Wentao, et al. Loiss: A Byte-Oriented Stream Cipher[EB/OL]. [2024-01-15]. https://doi.org/10.1007/978-3-642-20901-7_7. |
| [18] | FAN Yongqing. Cryptography and Applying in Modern Communication[J]. Netinfo Security, 2009, 9(3): 35-39. |
| 范永清. 密码学及其在现代通讯中的应用[J]. 信息网络安全, 2009, 9(3): 35-39. | |
| [19] | GUO Chun, WANG Lei. Revisiting Key-Alternating Feistel Ciphers for Shorter Keys and Multi-User Security[EB/OL]. (2018-10-27)[2024-01-15]. https://doi.org/10.1007/978-3-030-03326-2_8. |
| [20] | MITTENTHAL L. Nonlinear Dynamic Substitution Devices and Methods for Block Substitutions Employing Coset Decompositions and Direct Geometric Generation: US5647001[P]. 1997-07-08. |
| [21] | GU Dawu, XIAO Guozhen. An Improved Method of Constructing Nonlinear Orthomorphic Permutations with the Analysis of Its Property[J]. Journal of Xidian University, 1997, 24(4): 29-33. |
| 谷大武, 肖国镇. 一种改进的非线性正形置换构造方法及其性能分析[J]. 西安电子科技大学学报, 1997, 24(4): 29-33. | |
| [22] | FENG Dengguo, LIU Zhenhua. On the Construction of the Orthormophic Permutations[J]. Information Security and Communications Privacy, 1996(2): 61-64. |
| 冯登国, 刘振华. 关于正形置换的构造[J]. 通信保密, 1996(2): 61-64. | |
| [23] | XING Yusen, LIN Xiaodong, YANG Yixian, et al. Construction and Counting of Orthomorphic Permutation in Cryptosystem[J]. Journal on Communications, 1999, 20(2): 27-30. |
| 邢育森, 林晓东, 杨义先, 等. 密码体制中的正形置换的构造与计数[J]. 通信学报, 1999, 20(2): 27-30. | |
| [24] | DAI Zongduo, GOLOMB S W, GONG Guang. Generating All Linear Orthomorphisms without Repetition[J]. Discrete Mathematics, 1999, 205(1-3): 47-55. |
| [25] |
ZHENG Haoran, ZHANG Haimo, FAN Dong. Correction of a Construction Method of Orthomorphic Permutations and Improvement of Its Enumeration Lower Bound[J]. Journal on Communications, 2009, 30(12): 45-49.
doi: 1000-436X(2009)12-0045-05 |
|
郑浩然, 张海模, 樊东. 对一个正形置换构造方法的修正及其计数结果的改进[J]. 通信学报, 2009, 30(12): 45-49.
doi: 1000-436X(2009)12-0045-05 |
|
| [26] | DU Jiao, WEN Qiaoyan, ZHANG Jie, et al. Construction of Boolean Functions with Optimal Algebraic Immunity Based on the Maximal Linear Orthomorphic Permutations[C]// IEEE. Proceedings of 2011 International Conference on Computer Science and Network Technology. New York: IEEE, 2011: 1571-1575. |
| [27] | TONG Xiaojun, SU Yuyue, ZHANG Miao, et al. Lightweight Cipher Algorithm Based on Chaos and Improved Generalized Feistel Structure[J]. Netinfo Security, 2022, 22(8): 8-18. |
| 佟晓筠, 苏煜粤, 张淼, 等. 基于混沌和改进广义Feistel结构的轻量级密码算法[J]. 信息网络安全, 2022, 22(8): 8-18. |
| [1] | 沈霞民, 熊涛, 李华, 沈璇. CLEFIA动态密码结构的零相关线性区分器构造研究[J]. 信息网络安全, 2024, 24(6): 948-958. |
| [2] | 佟晓筠, 苏煜粤, 张淼, 王翥. 基于混沌和改进广义Feistel结构的轻量级密码算法[J]. 信息网络安全, 2022, 22(8): 8-18. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||