信息网络安全 ›› 2024, Vol. 24 ›› Issue (12): 1871-1881.doi: 10.3969/j.issn.1671-1122.2024.12.006
一种针对碰撞攻击的白盒SM4改进方案
- 1.西安电子科技大学通信工程学院,西安 710071
2.河南省网络密码技术重点实验室,郑州 450001
3.陕西师范大学计算机科学学院,西安 710119
-
收稿日期:2024-02-04出版日期:2024-12-10发布日期:2025-01-10 -
通讯作者:陈杰jchen@mail.xidian.edu.cn -
作者简介:李科慧(1999—),女,辽宁,硕士研究生,主要研究方向为白盒密码的设计与安全性分析|陈杰(1979—),女,湖南,副教授,博士,主要研究方向为密码算法的设计与分析、白盒密码的设计与安全性分析|刘君(1993—),女,陕西,讲师,博士,主要研究方向为白盒密码算法的设计与分析 -
基金资助:国家自然科学基金(62302285);河南省网络密码技术重点实验室研究课题(LNCT2022-A08)
A White-Box Improvement Scheme of SM4 for Collision Attack
LI Kehui1, CHEN Jie1,2( ), LIU Jun3
), LIU Jun3
- 1. School of Telecommunications Engineering, Xidian University, Xi’an 710071, China
2. Henan Key Laboratory of Network Cryptography Technology, Zhengzhou 450001, China
3. School of Computer Science, Shaanxi Normal University, Xi’an 710119, China
-
Received:2024-02-04Online:2024-12-10Published:2025-01-10
摘要:
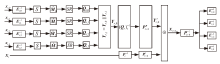
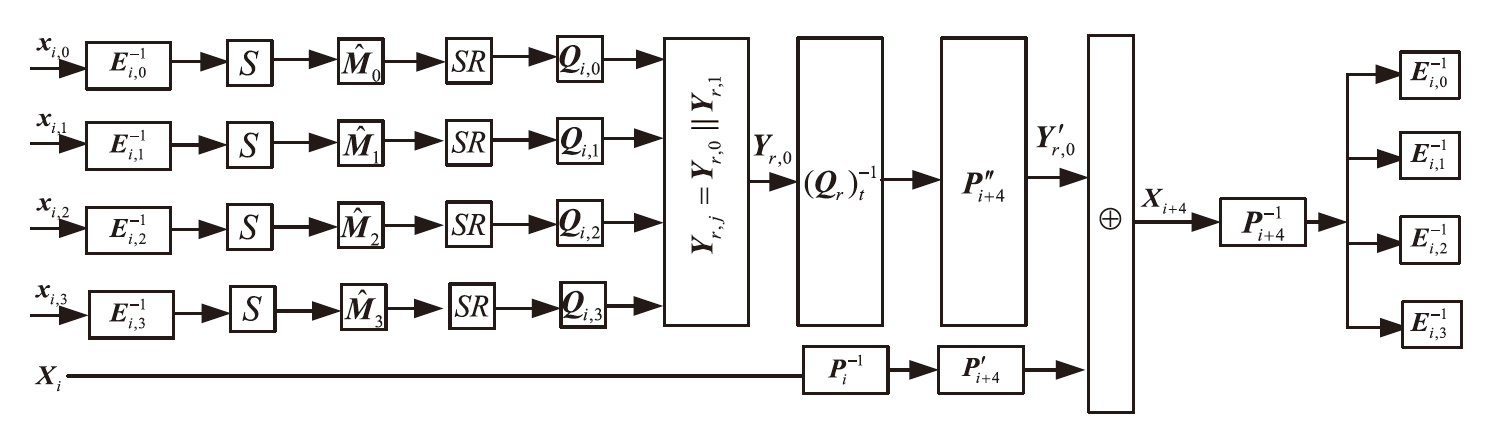
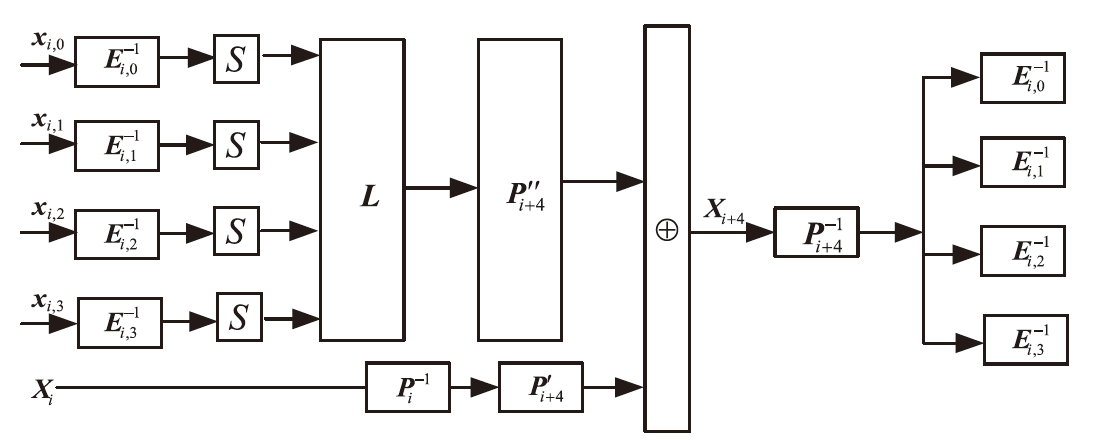
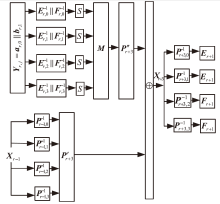
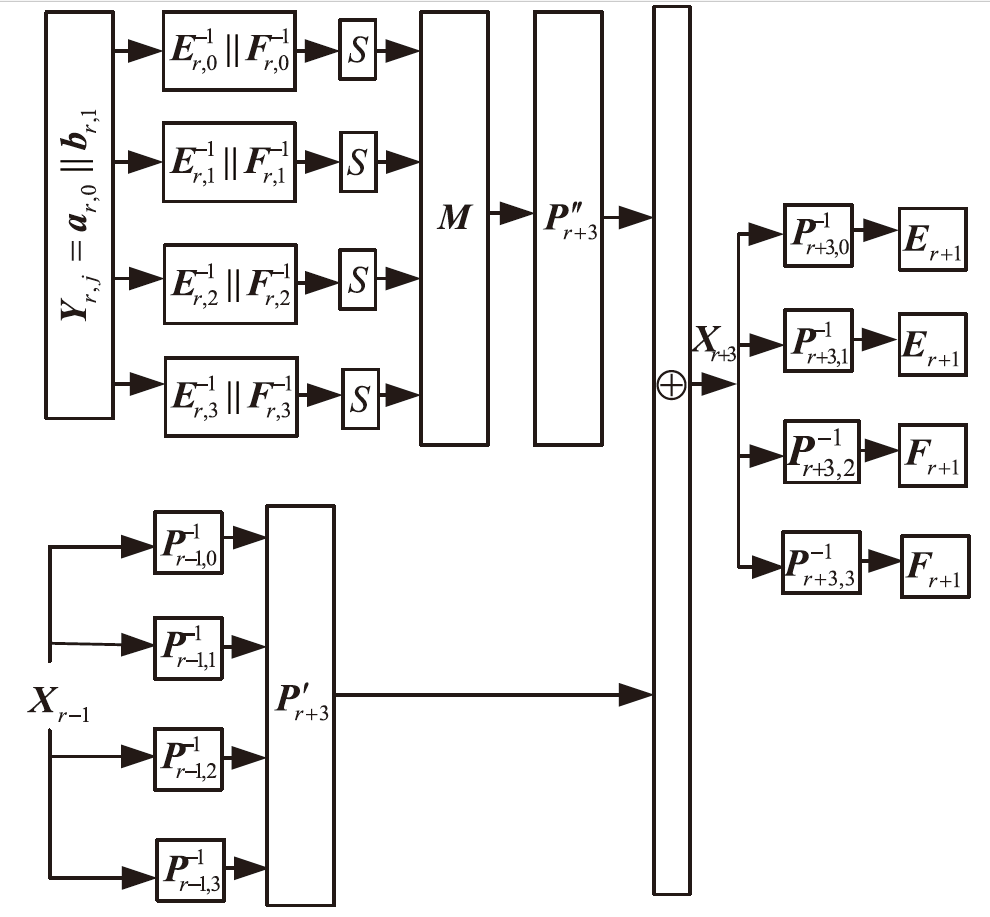
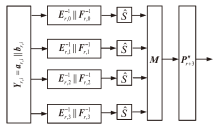
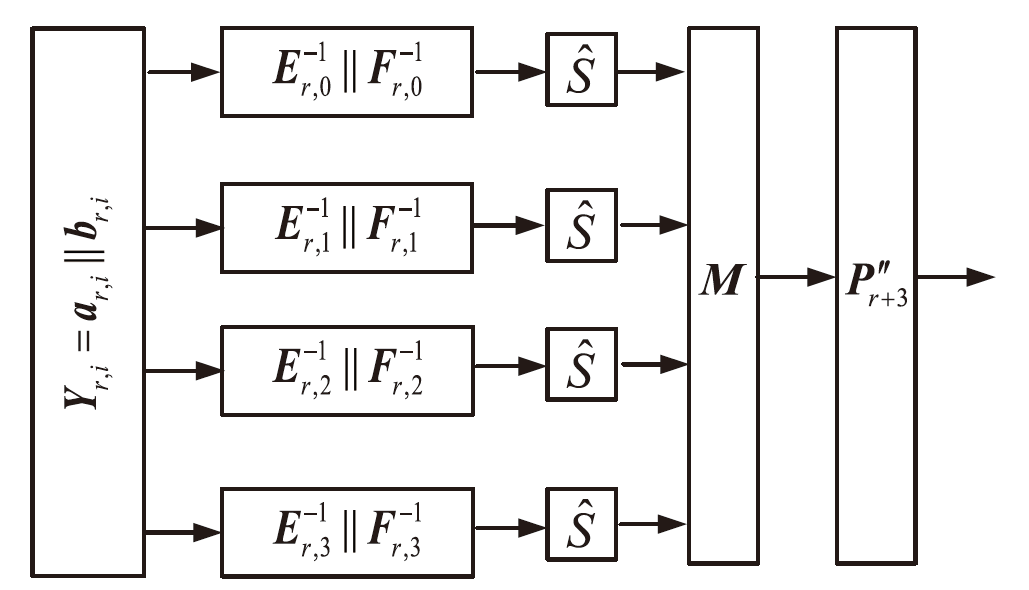
在白盒攻击模型中,攻击者能够访问密码算法的实现过程,观察或修改密码算法的内部细节。基于白盒密码的概念,姚-陈白盒SM4方案探讨了一种扩充内部状态的白盒SM4设计思路,但此方案未能抵抗碰撞攻击,且恢复密钥的时间复杂度仅为O(223.02)。为了保证白盒SM4在碰撞攻击环境中正常运行,文章提出一种针对碰撞攻击的白盒SM4改进方案。该改进方案引入较多随机仿射变换和随机向量,以复杂化内部编码,从而抵抗碰撞攻击。通过反证法证明,改进方案的轮加密函数不能被转化为碰撞函数,因此无法进行碰撞攻击分析。此外,还论证了该方案可以抵抗BGE攻击、代码提取攻击以及结合差分分析和求解方程组的攻击。针对调整仿射常数的差分分析的攻击方法,该改进方案的密钥空间大小为61200×2128,且对仿射等价攻击的时间复杂度为O(297)。
中图分类号:
引用本文
李科慧, 陈杰, 刘君. 一种针对碰撞攻击的白盒SM4改进方案[J]. 信息网络安全, 2024, 24(12): 1871-1881.
LI Kehui, CHEN Jie, LIU Jun. A White-Box Improvement Scheme of SM4 for Collision Attack[J]. Netinfo Security, 2024, 24(12): 1871-1881.
| [1] | CHOW S, EISEN P, JOHNSON H, et al. White-Box Cryptography and an AES Implementation[M]. Heidelberg: Springer, 2003. |
| [2] | VANDERSMISSEN J, RANEA A, PRENEEL B. A White-Box Speck Implementation Using Self-Equivalence Encodings[M]. Heidelberg: Springer, 2022. |
| [3] | BILLET O, GILBERT H, ECH-CHATBI C. Cryptanalysis of a White Box AES Implementation[M]. Heidelberg: Springer, 2004. |
| [4] | LEPOINT T, RIVAIN M, DE M Y, et al. Two Attacks on a White-Box AES Implementation[M]. Heidelberg: Springer, 2014. |
| [5] | MICHIELS W, GORISSEN P, HOLLMANN H D L. Cryptanalysis of a Generic Class of White-Box Implementations[M]. Heidelberg: Springer, 2009. |
| [6] | DE M Y, ROELSE P, PRENEEL B. Cryptanalysis of the Xiao-Lai White-Box AES Implementation[M]. Heidelberg: Springer, 2013. |
| [7] | BOS J W, HUBAIN C, MICHIELS W, et al. Differential Computation Analysis: Hiding Your White-Box Designs is Not Enough[M]. Heidelberg: Springer, 2016. |
| [8] | BANIK S, BOGDANOV A, ISOBE T, et al. Analysis of Software Countermeasures for Whitebox Encryption[J]. IACR Transactions on Symmetric Cryptology, 2017(1): 307-328. |
| [9] | ALPIREZ B E, BRZUSKA C, MICHIELS W, et al. On the Ineffectiveness of Internal Encodings-Revisiting the DCA Attack on White-Box Cryptography[C]// ACM. 16th Applied Cryptography and Network Security (ACNS 2018). Heidelberg: Springer, 2018: 103-120. |
| [10] | BOGDANOV A, RIVAIN M, VEJRE P S, et al. Higher-Order DCA against Standard Side-Channel Countermeasures[M]. Heidelberg: Springer, 2019. |
| [11] | GOUBIN L, PAILLIER P, RIVAIN M, et al. How to Reveal the Secrets of an Obscure White-Box Implementation[J]. Journal of Cryptographic Engineering, 2020, 10(1): 49-66. |
| [12] | LEE S, KIM M. Improvement on a Masked White-Box Cryptographic Implementation[J]. IEEE Access, 2020, 8: 90992-91004. |
| [13] | BIRYUKOV A, UDOVENKO A. Dummy Shuffling against Algebraic Attacks in White-Box Implementations[M]. Heidelberg: Springer, 2021. |
| [14] | TANG Yufeng, GONG Zheng, SUN Tao, et al. Adaptive Side-Channel Analysis Model and its Applications to White-Box Block Cipher Implementations[C]// Springer. International Conference on Information Security and Cryptology. Heidelberg: Springer, 2021: 399-417. |
| [15] | BATTISTELLO A, CASTELNOVI L, CHABRIER T. Enhanced Encodings for White-Box Designs[C]// Springer. 2021 Smart Card Research and Advanced Applications (CARDIS). Heidelberg: Springer, 2021: 254-274. |
| [16] | Standardization Administration. Information Security Technology-SM4 Block Cipher Algorithm[EB/OL]. (2016-08-29)[2024-01-10]. http://c.gb688.cn/bzgk/gb/showGb?type=online&hcno=7803DE42D3BC5E80B0C3E5D8E873D56A. |
| 国家标准化管理委员会. 信息安全技术SM4分组密码算法[EB/OL]. (2016-08-29)[2024-01-10]. http://c.gb688.cn/bzgk/gb/showGb?type=online&hcno=7803DE42D3BC5E80B0C3E5D8E873D56A. | |
| [17] | XIAO Yaying, LAI Xuejia. White-Box Cryptography and Implementation of SMS4[C]// Chinese Association for Cryptologic Research. The 2009 CACR Annual Meeting. Beijing: Science Press, 2009: 24-34. |
| 肖雅莹, 来学嘉. 白盒密码及SMS4算法的白盒实现[C]// 中国密码学会.中国密码学会2009年会. 北京: 科学出版社, 2009: 24-34. | |
| [18] | LIN Tingting, LAI Xuejia. Efficient Attack to White-Box SMS4 Implementation[J]. Journal of Software, 2013, 24(9): 2238-2249. |
| 林婷婷, 来学嘉. 对白盒SMS4实现的一种有效攻击[J]. 软件学报, 2013, 24(9): 2238-2249. | |
| [19] |
SHI Yang, WEI Wujing, HE Zongjian. A Lightweight White-Box Symmetric Encryption Algorithm against Node Capture for WSNS[J]. Sensors, 2015, 15(5): 11928-11952.
doi: 10.3390/s150511928 pmid: 26007737 |
| [20] | BAI Kunpeng, WU Chuankun. A Secure White-Box SM4 Implementation[J]. Security and Communication Networks, 2016, 9(10): 996-1006. |
| [21] | BAI Kunpeng, WU Chuankun, ZHANG Zhenfeng. Protect White-Box AES to Resist Table Composition Attacks[J]. IET Information Security, 2018, 12(4): 305-313. |
| [22] | LIN Tingting. Research on White Box Cryptography[D]. Shanghai: Shanghai Jiao Tong University, 2016. |
| 林婷婷. 白盒密码研究[D]. 上海: 上海交通大学, 2016. | |
| [23] | YAO Si, CHEN Jie. A New Method for White-Box Implementation of SM4 Algorithm[J]. Journal of Cryptologic Research, 2020, 7(3): 358-374. |
|
姚思, 陈杰. SM4算法的一种新型白盒实现[J]. 密码学报, 2020, 7(3): 358-374.
doi: 10.13868/j.cnki.jcr.000373 |
|
| [24] | LU Jiqiang, LI Jingyu. Cryptanalysis of Two White-Box Implementations of the SM4 Block Cipher[J]. Journal of Computer Science, 2021(13118): 54-69. |
| [25] | WANG Rusi, GUO Hua, LU Jiqiang, et al. Cryptanalysis of a White-Box SM4 Implementation Based on Collision Attack[J]. IET Information Security, 2022, 16(1): 18-27. |
| [1] | 张兴兰, 李登祥. 基于Grover量子搜索算法的MD5碰撞攻击模型[J]. 信息网络安全, 2024, 24(8): 1210-1219. |
| [2] | 罗一诺, 姚思, 陈杰, 董晓丽. 基于白盒CLEFIA实现的软件防篡改方案[J]. 信息网络安全, 2023, 23(6): 66-73. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||