信息网络安全 ›› 2020, Vol. 20 ›› Issue (11): 32-42.doi: 10.3969/j.issn.1671-1122.2020.11.005
基于Rootkit隐藏行为特征的Linux恶意代码取证方法
- 北京大学软件与微电子学院,北京 102600
-
收稿日期:2020-07-08出版日期:2020-11-10发布日期:2020-12-31 -
通讯作者:文伟平 E-mail:weipingwen@ss.pku.edu.cn -
作者简介:文伟平(1976—),男,湖南,教授,博士,主要研究方向为系统与网络安全、大数据与云安全、智能计算安全|陈夏润(1997—),男,江西,硕士研究生,主要研究方向为网络与系统安全、漏洞挖掘|杨法偿(1995—),男,河南,硕士研究生,主要研究方向为系统安全、计算机取证 -
基金资助:国家自然科学基金(61872011)
Malicious Code Forensics Method Based on Hidden Behavior Characteristics of Rootkit on Linux
WEN Weiping( ), CHEN Xiarun, YANG Fachang
), CHEN Xiarun, YANG Fachang
- School of Software and Microelectronics, Peking University, Beijing 102600, China
-
Received:2020-07-08Online:2020-11-10Published:2020-12-31 -
Contact:WEN Weiping E-mail:weipingwen@ss.pku.edu.cn
摘要:
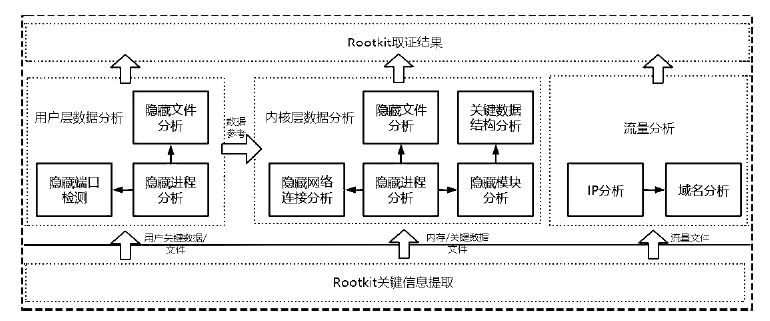
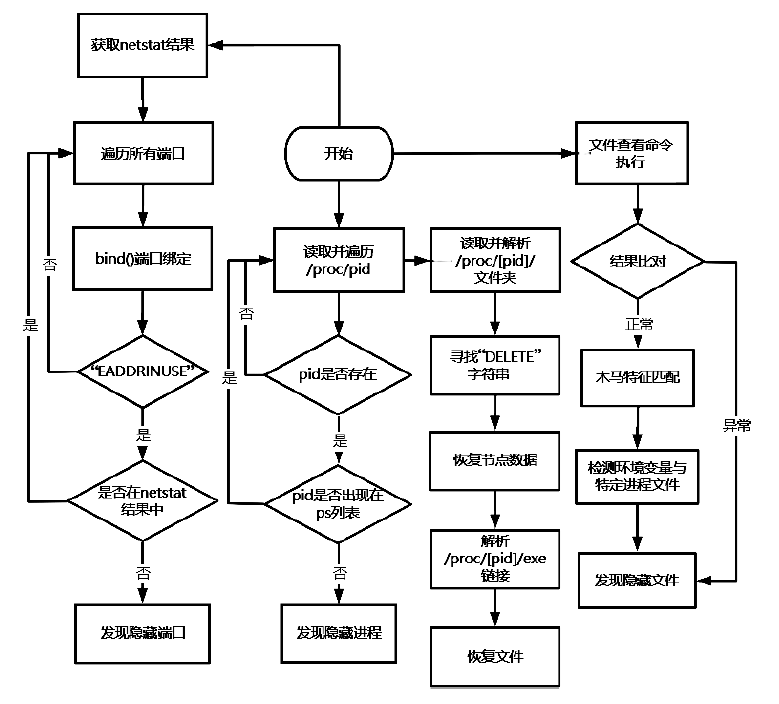
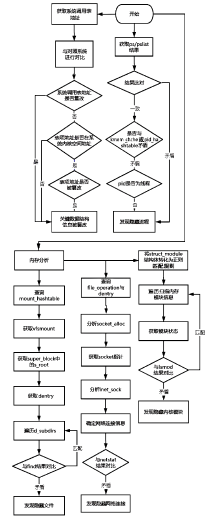
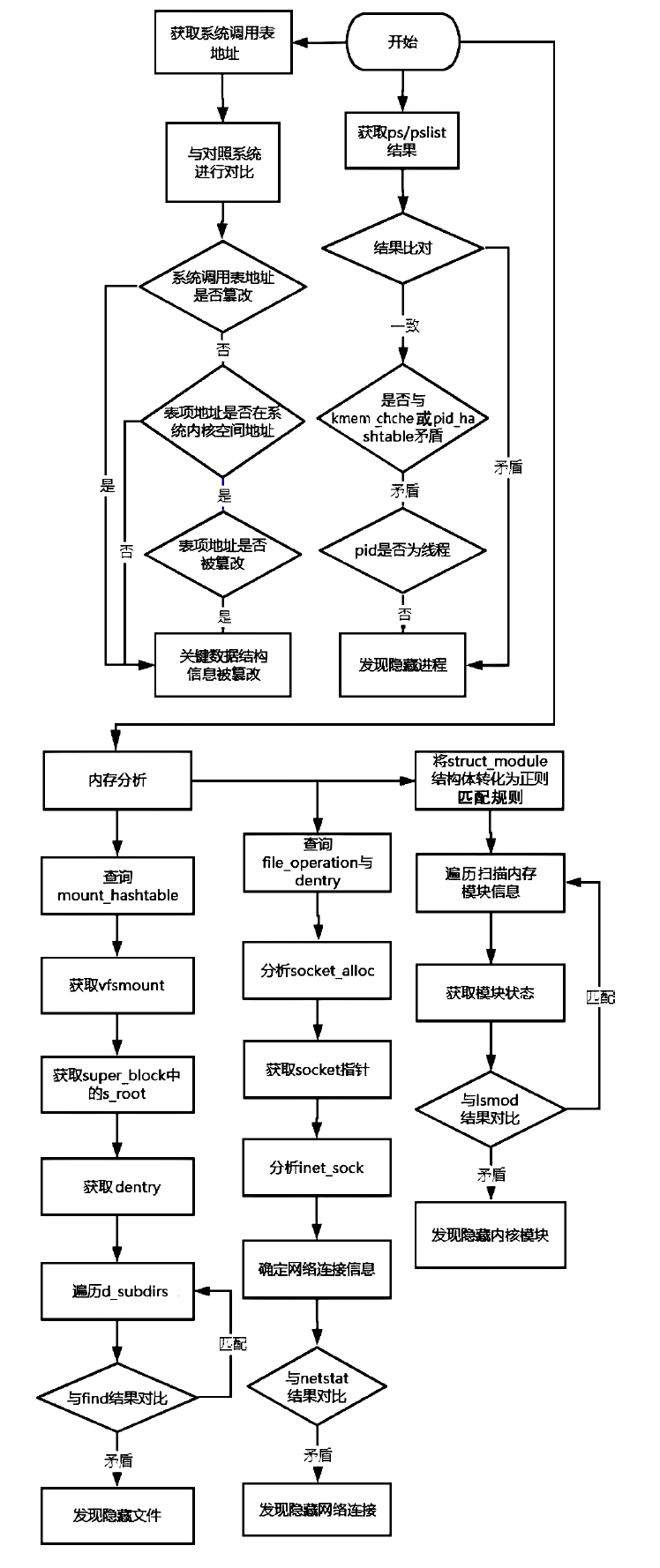
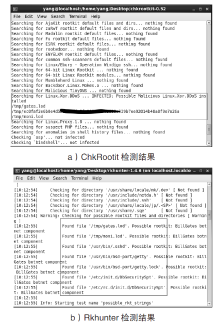
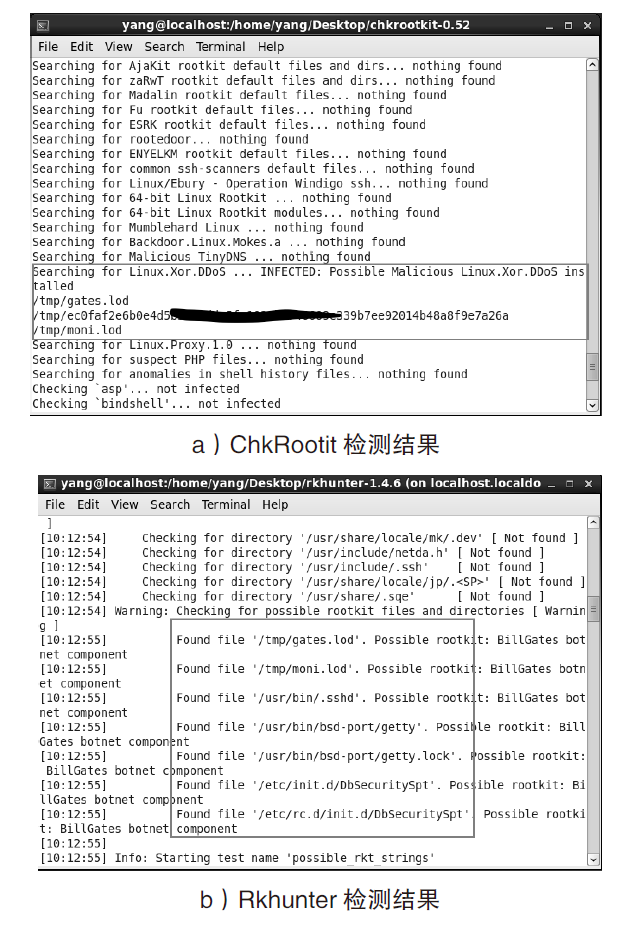
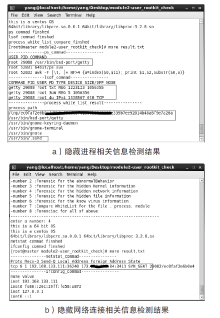
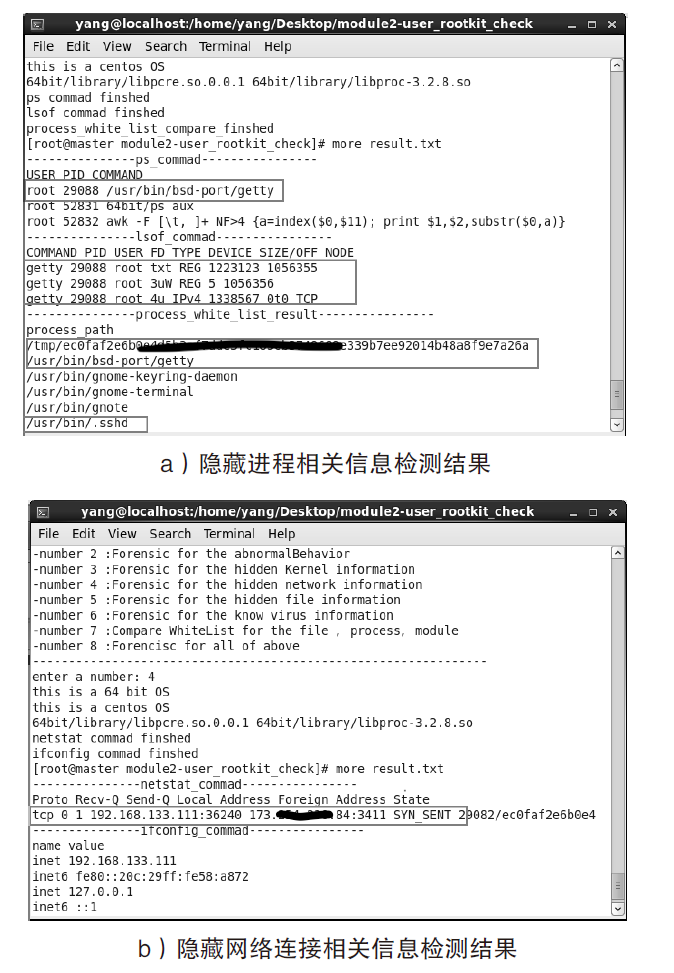
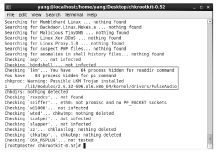
近年来,在互联网不断发展的同时,网络安全问题也层出不穷,而在对抗网络安全威胁时,取证问题一直是个难题。尤其是针对Linux平台,目前主流的Linux开源取证工具多数存在滞后、效率低、无法对隐蔽性强的木马进行取证等问题。在Linux取证研究中,Rootkit木马具有隐蔽性强、危害性大的特点,传统检测方法难以进行有效检测。为解决上述问题,文章从Rootkit的行为和实现技术出发,对其启动机制和内存驻留机制进行研究分析,提炼恶意代码行为作为检测特征,提出一种基于Rootkit隐藏行为特征的Linux恶意代码取证方法。实验表明,文章提出的取证方法对各类Linux恶意代码具有很好的检出效果和取证效果,相较传统取证方法在检测效果上具有明显优势。
中图分类号:
引用本文
文伟平, 陈夏润, 杨法偿. 基于Rootkit隐藏行为特征的Linux恶意代码取证方法[J]. 信息网络安全, 2020, 20(11): 32-42.
WEN Weiping, CHEN Xiarun, YANG Fachang. Malicious Code Forensics Method Based on Hidden Behavior Characteristics of Rootkit on Linux[J]. Netinfo Security, 2020, 20(11): 32-42.
表2
各类木马取证结果
| 木马名称 | 用户层检测 结果 | 内核层检测结果 | 流量分析 | 是否检出木马 |
|---|---|---|---|---|
| Remaiten | 隐藏文件 | 无检测结果 | 恶意域名 | 是 |
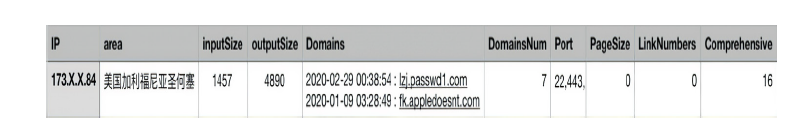
| Billgates | 隐藏进程、隐藏文件、隐藏网络连接 | 隐藏进程、隐藏文件、隐藏网络连接 | 恶意IP | 是 |
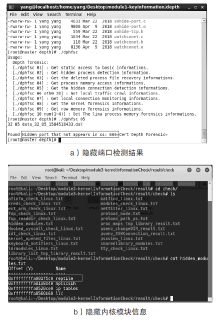
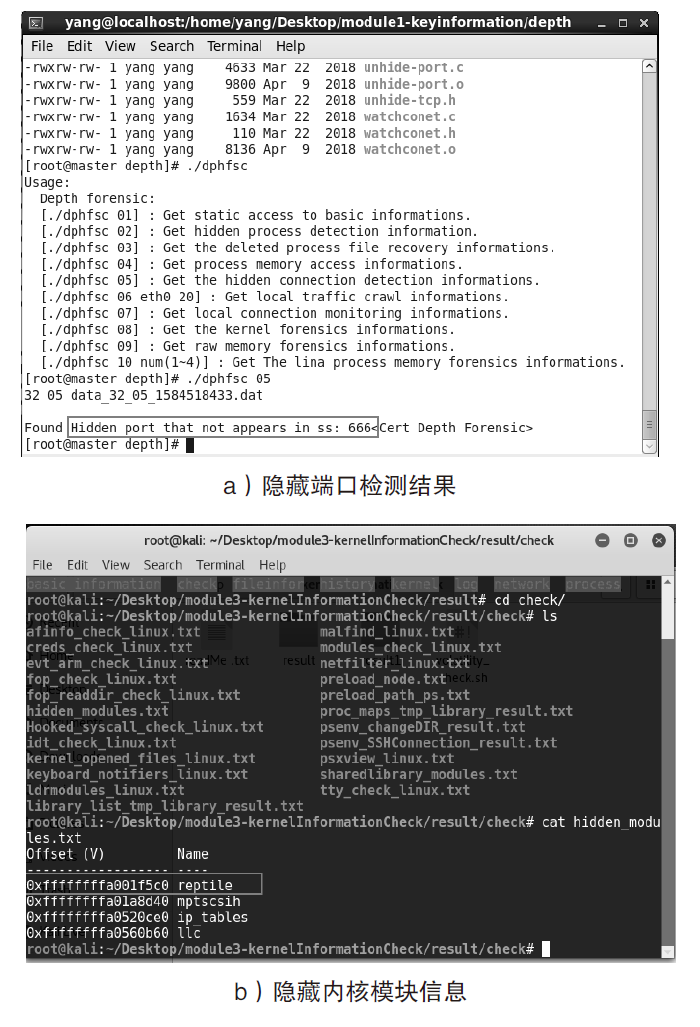
| Reptile | 隐藏端口 | 隐藏文件、隐藏网络连接、隐藏内核模块 | 无检测结果 | 是 |
| WNPS | 无检测结果 | 隐藏文件、隐藏进程、隐藏内核模块、关键数据结构篡改 | 无检测结果 | 是 |
| Ddrk | 隐藏进程 | 隐藏网络连接、隐藏进程、隐藏文件、关键数据 结构篡改 | 无检测结果 | 是 |
| Unknow1 | 隐藏端口 | 隐藏网络连接、隐藏文件、隐藏内核模块 | 恶意域名 | 是 |
| Unknow2 | 无检测结果 | 隐藏内核模块、隐藏进程、关键数据结构篡改 | 无检测结果 | 是 |
| [1] | DAFOULAS G A, NEILSON D, HARA S. State of the Art in Computer Forensic Education-A Review of Computer Forensic Programmes in the UK, Europe and US[C]//IEEE. 2017 International Conference on New Trends in Computing Sciences (ICTCS), October 11-13, 2017, Amman, Jordan. NJ: IEEE, 2017: 144-154. |
| [2] | SI Tianhao, ZHANG Yi, LUO Yuqing. Overview of Linux Rootkit Implementation and Detection Technology[C]// CCF. ICoC. July 10, 2013, Zhangjiajie, China. Beijing: CCF, 2013: 123-128. |
| 斯添浩, 张怡, 罗雨青. Linux Rootkit实现与检测技术综述[C]// 中国计算机学会.中国互联网学术年会,2013-7-10,张家界,中国.北京:中国计算机学会, 2013: 123-128. | |
| [3] | LILLIS D, BECKER B, O'SULLIVAN T, et al. Current Challenges and Future Research Areas for Digital Forensic Investigation[EB/OL]. https://www.researchgate.net/publication/292996779_Current_Challenges_and_Future_Research_Areas_for_Digital_Forensic_Investigation, 2020-4-19. |
| [4] | LIU Tao. Research and Implementation of Evidence Collection Based on Linux System[D]. Chengdu: University of Electronic Science and Technology of China, 2011. |
| 刘涛. 基于Linux系统的证据收集研究与实现[D]. 成都:电子科技大学, 2011. | |
| [5] | QIAN Zhigao. Research on Forensics Methods in Computer Intrusion Events[J]. Network Security Technology & Application, 2020,20(4):152-153. |
| 钱志高. 计算机入侵事件中的取证方法探究[J]. 网络安全技术与应用, 2020,20(4):152-153. | |
| [6] | LIU Xiaoli, XU Bohe. Method and Practice of Network Intrusion Forensics Based on Linux System[J]. Network Security Technology & Application, 2016,16(10):34-35. |
| 刘晓丽, 徐博赫. 基于Linux系统的网络入侵取证方法与实践[J]. 网络安全技术与应用, 2016,16(10):34-35. | |
| [7] | HIRANO M, KOBAYASHI R. Machine Learning Based Ransomware Detection Using Storage Access Patterns Obtained From Live-forensic Hypervisor[C]//IEEE. 2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS), October 22-25, 2019, Granada, Spain. NJ: IEEE, 2019: 1-6. |
| [8] | YARI I A, ZARGARI S. An Overview and Computer Forensic Challenges in Image Steganography[C]//IEEE. 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), June 21-23, 2017, Exeter, UK. NJ: IEEE, 2017: 360-364. |
| [9] | LI Tonghong, WANG Ning, LIU Zhijun. Data Hiding and Anti-forensic on Modern Computer System[J]. Computer Systems & Applications, 2013,22(5):1-4, 37. |
| 李佟鸿, 王宁, 刘志军. 计算机系统信息隐藏反取证技术[J]. 计算机系统应用, 2013,22(5):1-4,37. | |
| [10] |
AL FAHDI M, CLARKE N L, LI Fudong, et al. A Suspect-oriented Intelligent and Automated Computer Forensic Analysis[J]. Digital Investigation, 2016,18(9):65-76.
doi: 10.1016/j.diin.2016.08.001 URL |
| [11] | TORASKAR T, BHANGALE U, PATIL S, et al. Efficient Computer Forensic Analysis Using Machine Learning Approaches[C]//IEEE. 2019 IEEE Bombay Section Signature Conference (IBSSC), July 26-28, 2019, Mumbai, India. NJ: IEEE, 2019: 1-5. |
| [12] | ZHANG Yu, LIU Qingzhong, LI Tao, et al. Research and Development of Rootkit[J]. Journal of University of Electronic Science and Technology of China, 2014,44(4):563-578. |
| 张瑜, 刘庆中, 李涛, 等. Rootkit研究综述[J]. 电子科技大学学报, 2014,44(4):563-578. | |
| [13] | LIANG Shengrong, FAN Mingyu, WANG Guangwei, et al. New Method of Detecting Kernel-level Rootkit[J]. Application Research of Computers, 2009,26(8):3047-3049. |
| 梁升荣, 范明钰, 王光卫, 等. 一种新的内核级Rootkit的检测方法[J]. 计算机应用研究, 2009,26(8):3047-3049. | |
| [14] | YAN Renzhong, ZHONG Xichang, ZHANG Ni. A Method to Automatically Detect and Recover from Kernel Level Rootkit[J]. Computer Engineering, 2006,32(10):77-79. |
| 颜仁仲, 钟锡昌, 张倪. 一种自动检测内核级Rootkit并恢复系统的方法[J]. 计算机工程, 2006,32(10):77-79. | |
| [15] | MUSAVI S A, KHARRAZI M. Back to Static Analysis for Kernel-level Rootkit Detection[J]. IEEE Transactions on Information Forensics and Security, 2014,9(9):1465-1476. |
| [16] | CHEN Yuanpeng, LI Yongzhong. Analysis and Detect of Kernel-level Rootkit in Linux Platform[J]. Electronic Design Engineering, 2017,25(1):39-42. |
| 陈远鹏, 李永忠. Linux平台下Rootkit木马分析与检测[J]. 电子设计工程, 2017,25(1):39-42. | |
| [17] | FANG Haifeng, ZHAO Yiqiang, ZANG Hongyong, et al. VMGuard: An Integrity Monitoring System for Management Virtual Machines[C]//IEEE. 2010 IEEE International Conference on Parallel & Distributed Systems, December 8-10, 2010, Shanghai, China. NJ: IEEE, 2011: 67-74. |
| [18] | BEHROZINIA S, AZMI R. KLrtD: Kernel Level Rootkit Detection[C]//IEEE. 2014 22nd Iranian Conference on Electrical Engineering (ICEE), May 20-22, 2014, Tehran, Iran. NJ: IEEE, 2014: 1058-1063. |
| [19] | LUCKETT P, MCDONALD J T, DAWSON J. Neural Network Analysis of System Call Timing for Rootkit Detection[C]//IEEE. 2016 Cybersecurity Symposium (CYBERSEC), April 18-20, 2016, Coeur d'Alene, ID, USA. NJ: IEEE, 2016: 1-6. |
| [20] | LOBO D, WATTERS P, WU Xinwen. Identifying Rootkit Infections Using Data Mining[C]//IEEE. 2010 International Conference on Information Science and Applications, April 21-23, 2010, Seoul, South Korea. NJ: IEEE, 2010: 1-7. |
| [21] | JOY J, JOHN A. A Host Based Kernel Level Rootkit Detection Mechanism Using Clustering Technique[M]// Springer. Trends in Computer Science, Engineering and Information Technology. Heidelberg: Springer, Berlin, Heidelberg, 2011: 564-570. |
| [22] | FENG Peijun, ZHANG Ping, CHEN Zhifeng, et al. Design and Implementation of a New Linux Kernel-Level Rootkit[J]. Journal of Information Engineering University, 2016,17(2):231-237. |
| 冯培钧, 张平, 陈志锋, 等. 一种新型Linux内核级Rootkit设计与实现[J]. 信息工程大学学报, 2016,17(2):231-237. | |
| [23] | WANG Xueyang, KARRI R. Reusing Hardware Performance Counters to Detect and Identify Kernel Control-Flow Modifying Rootkits[J]. IEEE Transactions on Computer-aided Design of Integrated Circuits and Systems, 2016,35(3):485-498. |
| [24] | ZHOU Liwei, MAKRIS Y. Hardware-assisted Rootkit Detection via On-line Statistical Fingerprinting of Process Execution[C]//IEEE. 2018 Design, Automation & Test in Europe Conference & Exhibition (DATE), March 19-23, 2018, Dresden, Germany. NJ: IEEE, 2018: 1580-1585. |
| [25] | PETRONI N L, FRASER T, MOLINA J, et al. Copilot-a coprocessor-based Kernel Runtime Integrity Monitor[C]//USENIX. The 13th USENIX Security Symposium, August 9-13, 2004, San Diego, CA, USA. Berkeley: USENIX Association, 2004: 13. |
| [26] | AKAO Y, YAMAUCHI T. KRGuard: Kernel Rootkits Detection Method by Monitoring Branches Using Hardware Features[C]//IEEE. 2016 International Conference on Information Science and Security (ICISS), December 19-22, 2016, Pattaya, Thailand. NJ: IEEE, 2016: 1-5. |
| [27] | MOON H, LEE H, HEO I, et al. Detecting and Preventing Kernel Rootkit Attacks with Bus Snooping[J]. IEEE Transactions on Dependable and Secure Computing, 2015,14(2):145-157. |
| [28] | CARRIER B D, GRAND J. A Hardware-based Memory Acquisition Procedure for Digital Investigations[J]. Journal of Digital Investigation, 2004,1(1):50-60. |
| [29] | BBN Technologies. Fred: Forensic Ram Extraction Device[EB/OL]. http://www. ir. bbn. com/vkawadia/, 2012-12-10. |
| [1] | 乔延臣, 姜青山, 古亮, 吴晓明. 基于汇编指令词向量与卷积神经网络的恶意代码分类方法研究[J]. 信息网络安全, 2019, 19(4): 20-28. |
| [2] | 李云春, 鲁文涛, 李巍. 基于Shapelet的恶意代码检测方法[J]. 信息网络安全, 2018, 18(3): 70-77. |
| [3] | 周振飞, 方滨兴, 崔翔, 刘奇旭. 基于相似性分析的WordPress主题恶意代码检测[J]. 信息网络安全, 2017, 17(12): 47-53. |
| [4] | 王毅, 唐勇, 卢泽新, 俞昕. 恶意代码聚类中的特征选取研究[J]. 信息网络安全, 2016, 16(9): 64-68. |
| [5] | 蔡林, 陈铁明. Android移动恶意代码检测的研究概述与展望[J]. 信息网络安全, 2016, 16(9): 218-222. |
| [6] | 张家旺, 李燕伟. 基于N-gram算法的恶意程序检测系统研究与设计[J]. 信息网络安全, 2016, 16(8): 74-80. |
| [7] | 王昱镔, 吴薇, 程楠. 反网络恐怖主义策略研究[J]. 信息网络安全, 2015, 15(9): 175-179. |
| [8] | 梁宏, 张慧云, 肖新光. 基于社会工程学的邮件样本关联分析[J]. 信息网络安全, 2015, 15(9): 180-185. |
| [9] | 夏荣. Web取证分析技术研究与应用[J]. 信息网络安全, 2015, 15(9): 201-205. |
| [10] | 夏坤鹏, 谢正勇, 崔伟. 基于IDS报警和rootkit的威胁溯源方法研究[J]. 信息网络安全, 2015, 15(9): 231-235. |
| [11] | 张磊, 陈兴蜀, 任益, 李辉. 一种基于VMM的内核级Rootkit检测技术[J]. 信息网络安全, 2015, 15(4): 56-61. |
| [12] | 芦天亮, 周运伟, 曹巍. 移动互联网攻击技术及违法犯罪手段分析[J]. 信息网络安全, 2014, 14(9): 176-179. |
| [13] | 任伟, 柳坤, 周金. AnDa:恶意代码动态分析系统[J]. 信息网络安全, 2014, 14(8): 28-33. |
| [14] | . 电力移动智能终端安全技术研究[J]. , 2014, 14(4): 70-. |
| [15] | . 基于 Windows API 调用机制的 Rootkit检测系统的设计与研究[J]. , 2014, 14(11): 52-. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||