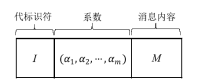
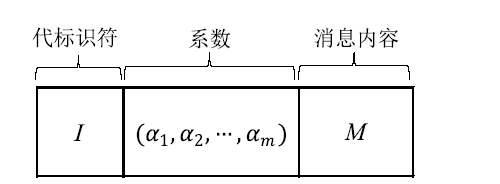
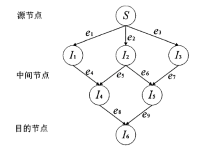
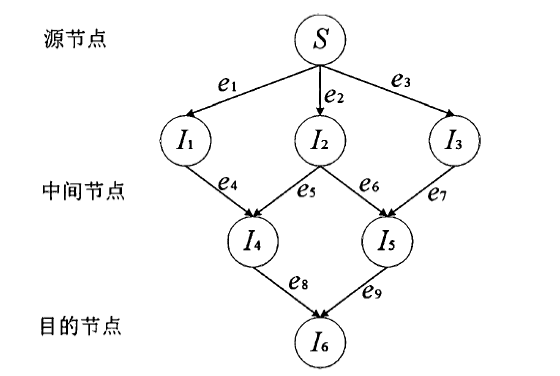
| [1] |
TAO Shaoguo, HUANG Jiaqing, YANG Zongkai, et al.A Survey of Network Coding Research[J]. Small Computer Systems, 2008, 29(4): 583-592.
|
|
陶少国,黄佳庆,杨宗凯,等.网络编码研究综述[J].小型微型计算机系统,2008,29(4):583-592.
|
| [2] |
BOLLOBAS B.Graph Theory an Introductory Course[M]. New York: Springer-Verlag, 1979.
|
| [3] |
AHLSWEDE R, CAI Ning, YEUNG R, et al.Network Information Flow[J]. IEEE Transactions on Information Theory, 2000, 46(4): 1204-1216.
|
| [4] |
KOETTER R, MEDARD M.An Algebraic Approach to Network Coding[J]. IEEE/ACM Transactions on Networking, 2003, 11(5): 782-795.
|
| [5] |
LI S Y R, YEUNG R, CAI Ning. Linear Network Coding[J]. IEEE Transactions on Information Theory, 2003, 49(2): 371-381.
|
| [6] |
CAO Zhanghua, TANG Yuansheng.Overview of Secure Network Coding[J]. Journal of Computer Applications, 2010, 30(2): 499-505.
|
|
曹张华,唐元生.安全网络编码综述[J].计算机应用,2010,30(2):499-505.
|
| [7] |
AGRAWAL S, BONEH D. Homomorphic MACs: MAC-Based Integrity for Network Coding[EB/OL]. , 2017-12-10.
|
| [8] |
CHENG Chi, JIANG Tao.A Novel Homomorphic Mac Scheme for Authentication in Network Coding[J]. IEEE Communications Letters, 2011, 15(11): 1228-1230.
|
| [9] |
LI Chen, LU Rongxing, LI Hui, et al.Comment on A Novel Homomorphic MAC Scheme for Authentication in Network Coding[J]. IEEE Communications Letters, 2014, 18(12): 2129-2130.
|
| [10] |
CHENG Chi, JIANG Tao.An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding[J]. IEEE Transactions on Computers, 2013, 62(10): 2096-2100.
|
| [11] |
WANG Weijia, HU Lei.A Generic Homomorphic MAC Construction for Authentication in Network Coding[J]. Security and Communication Networks, 2014, 7(2): 429-433.
|
| [12] |
CHANG Jinyong, XUE Rui.A Generic Construction of Homomorphic MAC for Multi-file Transmission in Network Coding[J]. Journal of Communications, 2015, 10(1): 43-47.
|
| [13] |
ESFAHANI A, MANTAS G, RODRIGUEZ J.An Efficient Null Space-based Homomorphic MAC Scheme Against Tag Pollution Attacks in RLNC[J]. IEEE Communications Letters, 2016, 20(5): 918-921.
|
| [14] |
ESFAHANI A, MANTAS G, RODRIGUEZ J, et al.An Efficient Homomorphic MAC-based Scheme Against Data and Tag Pollution Attacks in Network Coding-enabled Wireless Networks[J]. International Journal of Information Security, 2017, 16(6): 627-639.
|
| [15] |
LIU Guangjun, WANG Bin.Secure Network Coding Against Intra/Inter-generation Pollution Attacks[J]. China Communications, 2013, 10(8): 100-110.
|
| [16] |
CANETTI R, GARAY J, ITKIS G, et al.Multicast Security: A Taxonomy and Some Efficient Constructions[C]//IEEE. Conference on Computer Communications, March 21-25, 1999, New York, USA. New York: IEEE, 1999: 708-716.
|
| [17] |
KATZ J, LINDELL Y.Introduction to Modern Cryptography: Principles and Protocols[M]. Boca Raton: Chapman and Hall/CRC, 2007.
|
 )
)