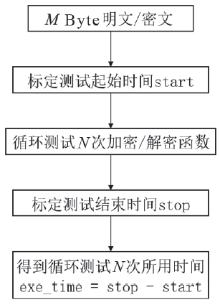
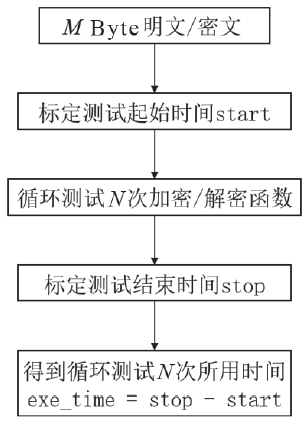
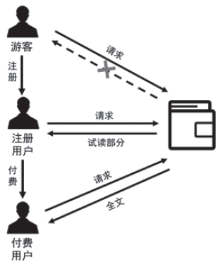
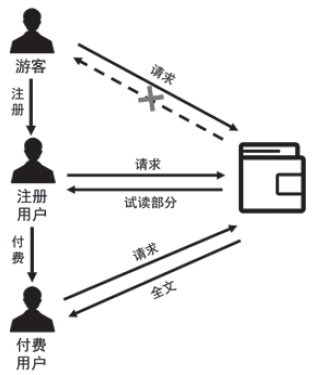
信息网络安全 ›› 2018, Vol. 18 ›› Issue (7): 69-78.doi: 10.3969/j.issn.1671-1122.2018.07.009
一种基于双明文的数据对称加密算法
- 1. 62101部队信息中心,湖北武汉430010
2. 武汉大学国家网络安全学院,湖北武汉 430072
3.中国海洋大学信息
-
收稿日期:2018-03-15出版日期:2018-07-15发布日期:2020-05-11 -
作者简介:作者简介:向永谦(1962—)男,湖北,高级工程师,硕士,主要研究方向为网络安全;宋智琪(1995—),女,四川,硕士研究生,主要研究方向为密码学;王天宇(1996—),女,山东,本科,主要研究方向为白盒密码学。
-
基金资助:国家重点研发计划[2017YFB0503700,2016YFB0501801];国家自然科学基金[61170026];国家标准研究计划[2016BZYJ-WG7-001]
A Data Symmetric Encryption Algorithm Based on Double Plaintext
Yongqian XIANG1( ), Zhiqi SONG2, Tianyu WANG3
), Zhiqi SONG2, Tianyu WANG3
- 1. Information Centre, 62101 Military, Wuhan Hubei 430010, China
2. School of Cyber Science and Engineering, Wuhan University, Wuhan Hubei 430072, China
3.College of Information Science and Engineering, Ocean University of China, Qingdao Shandong 266100, China
-
Received:2018-03-15Online:2018-07-15Published:2020-05-11
摘要:
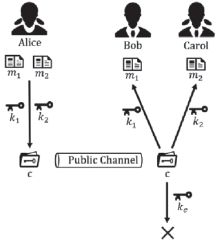
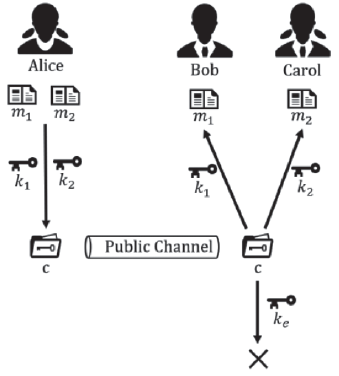
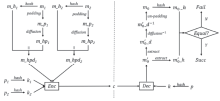
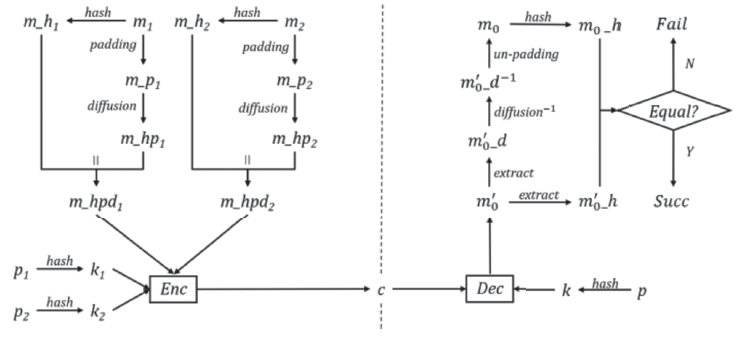
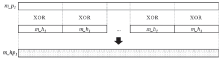
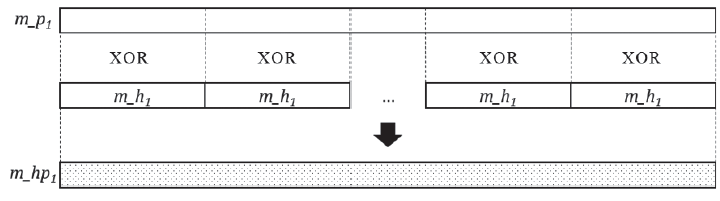
传统对称密钥密码体制的安全完全依赖于密钥的保密,常用的对称密码算法DES、3DES、IDEA、AES 等都是采用对一组明文加密得到一组密文的方法,信息利用方式枯燥,信息传递量有待增加,且对于特定的使用环境,无法在不使用分支判断的条件下提供不同的信息。为此,文章介绍了一种基于双明文的数据对称加密算法及其工作原理,并给出了核心算法的功能和描述,对核心算法的安全考虑逐一说明;文章还总结了其与目前常见对称算法的不同,并结合应用场景进行解释,以展示其应用前景;最后对该算法的优势进行总结,并分析其可能存在的问题和改进方向。该算法可以成倍增加信息传递量,并能选择性提供明文,这在阻止攻击者穷举密钥方面具有创新性,且算法简单,运行速度快,加密高效。同时引入hash算法,既能够保证数据的完整性,又能提供防篡改与检验机制,在安全性上得到保证,具有良好的技术优势。
中图分类号:
引用本文
向永谦, 宋智琪, 王天宇. 一种基于双明文的数据对称加密算法[J]. 信息网络安全, 2018, 18(7): 69-78.
Yongqian XIANG, Zhiqi SONG, Tianyu WANG. A Data Symmetric Encryption Algorithm Based on Double Plaintext[J]. Netinfo Security, 2018, 18(7): 69-78.
| [1] | HU Yupu Symmetric Cryptography [M]U Yupu Symmetric Cryptography [M]. Beijing:Mechanical Industry Publishing House, 2002. |
| 胡予濮. 对称密码学[M]. 北京:机械工业出版社, 2002. | |
| [2] | FIPSPUB 46-3 Data Encryption Standard(DES)[S]. U.S. DEPARTMENT OF COMMERCE/National Institute of Standards and and Technology(NIST). Federal Information Processing Standards Publication 46-3, 1999-10-25. |
| [3] | XU Hongbo, LI Yinghua.The Application of DES Encryption Algorithm to Protect Data Security in the File Transfer[J]. Netinfo Security, 2009,9(6): 24-26, 76. |
| 徐洪波, 李颖华. DES加密算法在保护文件传输中数据安全的应用[J]. 信息网络安全, 2009,9(6):24-26, 76. | |
| [4] | KARN P,METAGER P,SIMPSON W.RFC1851[EB/OL]. ,2018-1-15. |
| [5] | LAI X.International Data Encryption Algorithm[J]. Hepatology, 2016, 60(6):2125-2126. |
| [6] | FIPSPUB 197 Specification for the Advanced Encryption Standard(AES)[S]. New York:Federal Information Processing Standards Publication,2001. |
| [7] | ZHANG Jinhui, GUO Xiaobiao, FU Xin.AES Encryption Algorithm Analysis and the Application in Information Security[J]. Netinfo Security, 2011, 11(5): 31-33. |
| 张金辉, 郭晓彪, 符鑫. AES加密算法分析及其在信息安全中的应用[J]. 信息网络安全, 2011, 11(5): 31-33. | |
| [8] | FENG Dengguo.Status Quo and Trend of Cryptography[J]. Journal of China Institute of Communications, 2002,23(5):18-26. |
| 冯登国. 国内外密码学研究现状及发展趋势[J]. 通信学报, 2002, 23(5):18-26. | |
| [9] | ISO/IEC 9797-1[S].Switzerland:International Organization for Standardization,1999. |
| [10] | HOUSLEY R, RFC5652[EB/OL]. ,2018-1-15. |
| [11] | ZHANG Xinjuan.Feasible Suggestions of Digital Works Copyright Protection[J]. Published Reference, 2015(8):18-19. |
| 张新娟. 数字作品版权保护可行性建议[J].出版参考,2015,8:18-19. | |
| [12] | LI Fagen, ZHONG Di.A Survey of Digital Signcryption[J]. Netinfo Security, 2011, 11(12): 1-8. |
| 李发根, 钟笛. 数字签密综述[J]. 信息网络安全, 2011,11(12):1-8. | |
| [13] | LIU Xinyue, LI Hua.A New Digital Copyright Protection Method Based on Digital Certificate and Device: China, CN101714195A [P]. 2010. |
| 刘辛越, 李华.一种基于数字证书的新型数字版权保护方法和装置:中国,CN101714195A[P]. 2010. | |
| [14] | LIU Wenlong, LI Hui, JIN Dongxun.Research on Digital Fingerprinting Generation Scheme and Key Algorithm[J]. Netinfo Security, 2015,15(2):66-70. |
| 刘文龙, 李晖, 金东勋. 数字指纹生成方案及关键算法研究[J]. 信息网络安全, 2015,15(2):66-70. | |
| [15] | HUANG Qinlong, MA Zhaofeng, FU Jingyi, et al.Privacy-preserving Digital Rights Management Scheme in Cloud Computing[J].Journal on Communications,2014(2):95-103. |
| 黄勤龙,马兆丰,傅镜艺,等.云计算环境中支持隐私保护的数字版权保护方案[J].通信学报,2014(2):95-103. | |
| [16] | HUANG TAO, ZHANG Zhiyong, TIAN Weili, et al.A Digital Rights Management System Based on Trusted Computing: China, CN202663435U [P]. 2013. |
| 黄涛, 张志勇, 田伟莉,等.一种基于可信计算的数字版权管理系统:中国,CN202663435U[P]. 2013. | |
| [17] | XING Bin, LIU Jiqiang, HAN Zhen.A New Model for Measuring the Integrity of Trusted Computing Platforms[J]. Netinfo Security, 2016,16(6) :8-14. |
| 邢彬, 刘吉强, 韩臻. 一种可信计算平台完整性度量的新模型[J].信息网络安全,2016,16(6): 8-14. | |
| [18] | ZHU LEI, JING LEI."Internet +" under the Environment of Digital Copyright Protection Model[J]. Journal of Electronic Technology and Software Engineering, 2017 (20) : 209-211. |
| 朱磊,荆磊.“互联网+”环境下数字版权保护模式[J].电子技术与软件工程,2017(20):209-211. | |
| [19] | YU Yinyan, TANG Zhi.A Survey of the Research on Digital Rights Management[J]. Chinese Journal of Computers, 2005, 28(12) :1957-1968. |
| 俞银燕,汤帜.数字版权保护技术研究综述[J].计算机学,2005 , 28(12) :1957-1968. | |
| [20] | An XiaoLan Tan Yunming. Amazon E-book Business Model Analysis[J]. Journal of Published Research, 2009 (6) : 49-52. |
| 安小兰, 谭云明. 亚马逊电子书经营模式分析[J]. 出版发行研究, 2009(6):49-52. |
| [1] | 董晓丽, 商帅, 陈杰. 分组密码9轮Rijndael-192的不可能差分攻击[J]. 信息网络安全, 2020, 20(4): 40-46. |
| [2] | 王沂, 韩广国, 李慧智. 无线网络中可证安全的移动用户密钥交换协议[J]. 信息网络安全, 2015, 15(3): 54-58. |
| [3] | . 基于分组密码的认证加密工作模式[J]. , 2014, 14(11): 8-. |
| [4] | . 新型数学难题及其在分组密码中的应用研究[J]. , 2014, 14(11): 79-. |
| [5] | 孙亮;金伟信. 基于对称密码体制的通信加密方案设计与研究[J]. , 2013, 13(8): 0-0. |
| [6] | 李淼;徐建博. 对称密码中复合域乘法运算可重构设计研究[J]. , 2012, 12(8): 0-0. |
| [7] | 杨佳;鲁青远. C2密码及其安全性研究[J]. , 2011, 11(3): 0-0. |
| [8] | 关振胜;李晓峰. 电子支付中的密码技术应用(上)[J]. , 2009, 9(4): 0-0. |
| [9] | 吕兴凤;姜誉. 计算机密码学中的加密技术研究进展[J]. , 2009, 9(4): 0-0. |
| [10] | 李卷孺;谷大武;张媛媛. 一种针对特定结构SPN密码算法的差分故障攻击[J]. , 2009, 9(4): 0-0. |
| [11] | 范永清. 密码学及其在现代通讯中的应用[J]. , 2009, 9(3): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||