信息网络安全 ›› 2017, Vol. 17 ›› Issue (12): 61-66.doi: 10.3969/j.issn.1671-1122.2017.12.011
基于安全容器的Activity钓鱼劫持防御方案
陈璨璨, 崔浩亮, 张文, 牛少彰
- 北京邮电大学智能通信软件与多媒体北京市重点实验室,北京 100876
A Defense Scheme for Activity Hijack Based on Safe Container
Cancan CHEN, Haoliang CUI, Wen ZHANG, Shaozhang NIU
- Beijing Key Lab of Intelligent Telecommunication Software and Multimedia, Beijing University of Posts and Telecommunications, Beijing 100876, China
摘要:
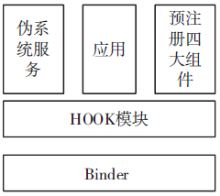
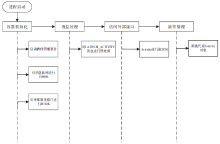
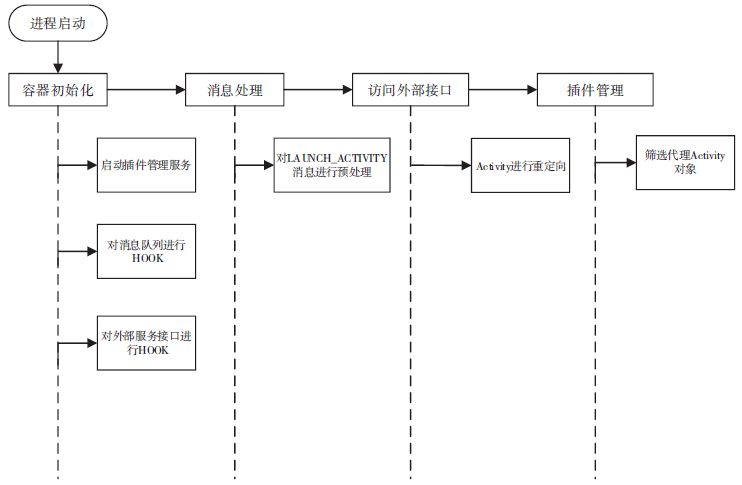
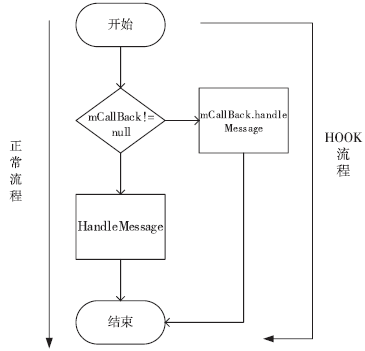
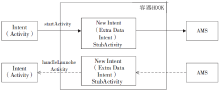
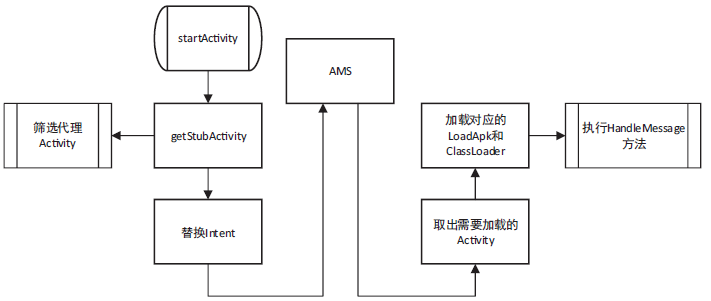
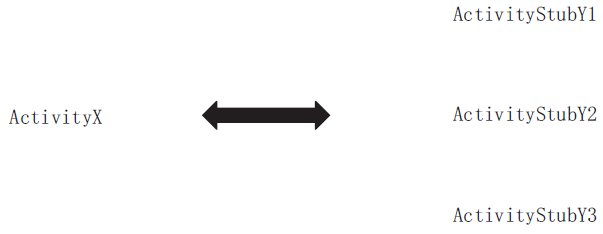
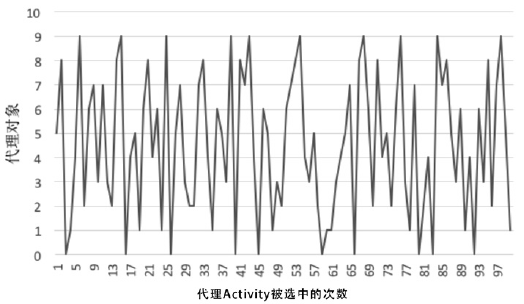
钓鱼劫持作为窃取用户隐私数据的恶意攻击行为,对用户的隐私数据造成了严重的安全威胁。针对钓鱼劫持攻击链中的恶意试探环节,文章提出了利用安全容器将应用与外部环境隔离,使得外部的恶意应用无法获取在容器中运行的应用的状态和在容器中运行的任务栈的栈顶信息,只能获取虚假的代理组件,有效阻止外部的恶意应用对Activity界面进行覆盖。文中方案从钓鱼劫持的攻击流程角度进行分析,设计拦截手段,阻止Activity钓鱼劫持的发生。实验结果表明,文中方案能够有效地为应用提供安全可靠的运行环境,并且不会对系统内核进行修改,保证应用免受Activity钓鱼劫持的恶意攻击。
中图分类号: