信息网络安全 ›› 2017, Vol. 17 ›› Issue (7): 52-58.doi: 10.3969/j.issn.1671-1122.2017.07.008
一种抵抗路由欺骗的网络拓扑发现算法
- 北京邮电大学网络空间安全学院,北京 100876
A Network Topology Discovery Algorithm Resistant to Routing Spoofing
- School of Cyberspace Security, Beijing University of Post and Telecommunication, Beijing 100876, China
摘要:
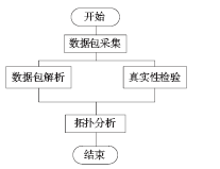
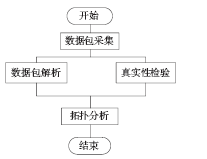
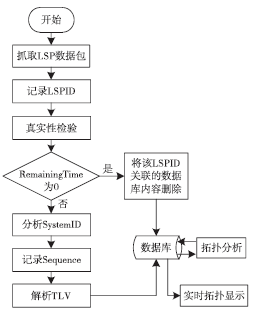
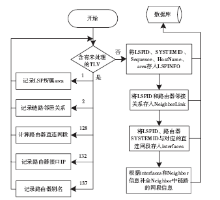
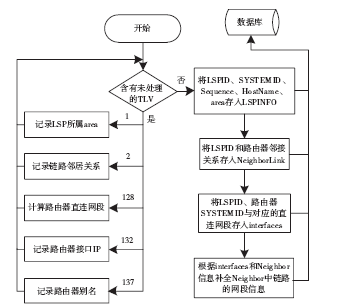
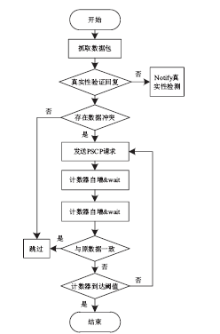
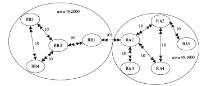
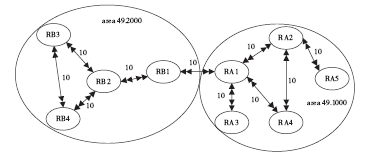
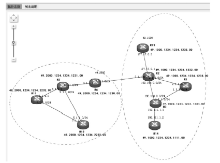
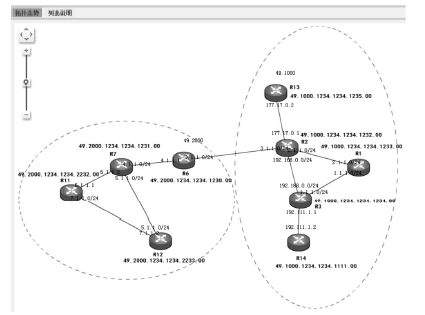
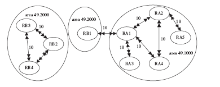
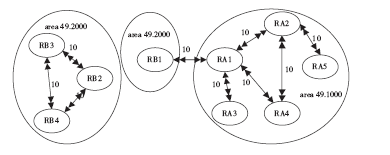
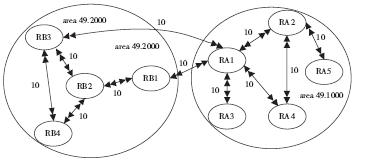
准确的、全面的网络拓扑信息能够直接、有效地将当前网络的结构和状态呈现给网络管理人员,因此网络拓扑结构图的真实性、完整性和准确性对网络故障管理、配置管理和安全管理至关重要。传统的基于ICMP、ARP协议的主动探测手段会在数据平面上对网络负载造成一定的影响,而现有的基于IS-IS协议的网络拓扑发现算法很难保证在遭受路由欺骗攻击的情况下真实地、准确地描述IP网络。文章提出了一种抵抗路由欺骗的网络拓扑发现算法,可以通过分析IS-IS协议报文中的LSP协议数据,获得路由器之间的链路关系等网络拓扑信息,绘制可信的完整的基础网络拓扑图,并对初始绘制完成后网络中产生的可疑的网络拓扑变化通过PSNP请求对数据真实性进行验证,从而避免因路由欺骗攻击造成的网络拓扑变化。仿真实验表明,该算法可以抵抗路由欺骗攻击,能够准确获得完整的网络拓扑结构,保证网络拓扑发现的真实性和准确性。
中图分类号: