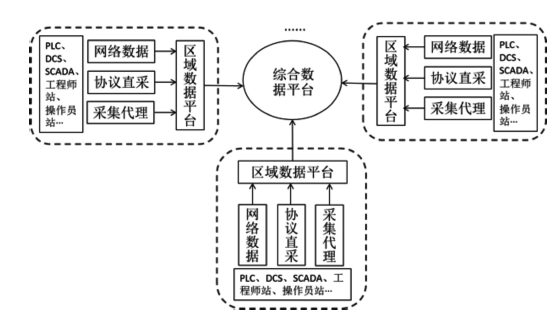
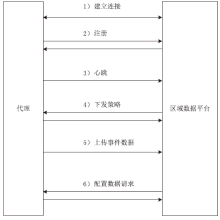
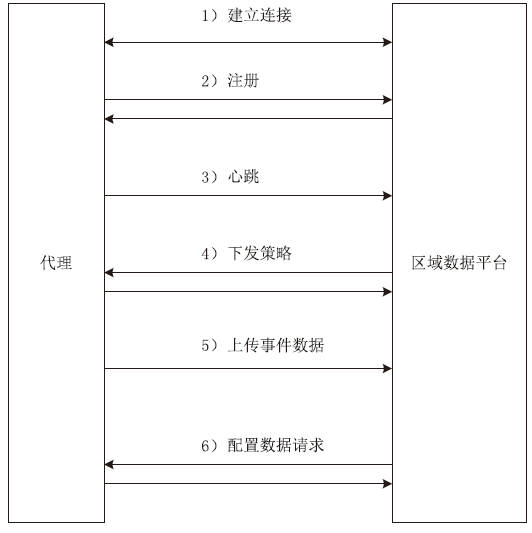
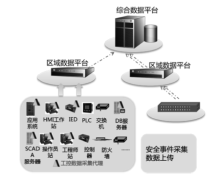
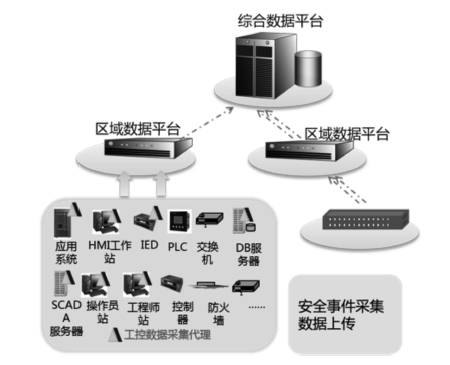
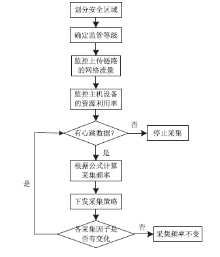
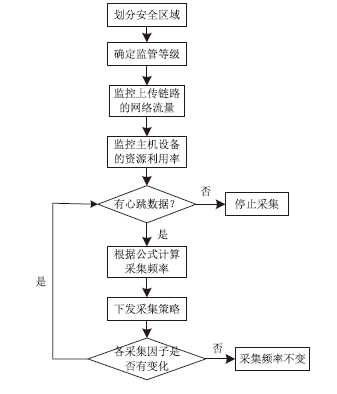
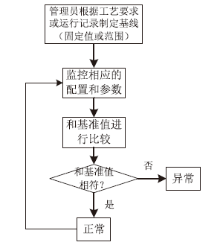
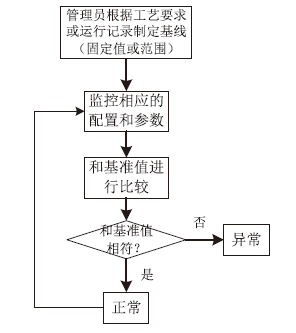
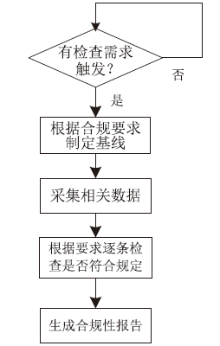
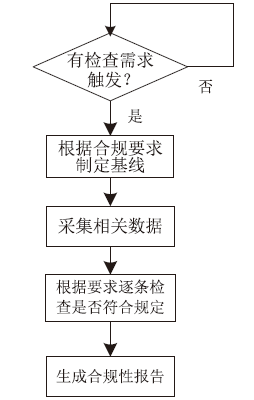
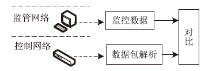
| [1] |
KARNOUSKOS S.Stuxnet Worm Impact on Industrial Cyber-Physical System Security[C]//IEEE.IECON 2011-37th Annual Conference on IEEE Industrial Electronics Society,November 7-10,2011.Melbourne, Victoria, Australia.New Jersey:IEEE,2011:4490-4494.
|
| [2] |
自动化控制系统市场在2021年将达到810亿美元[EB/OL]..
|
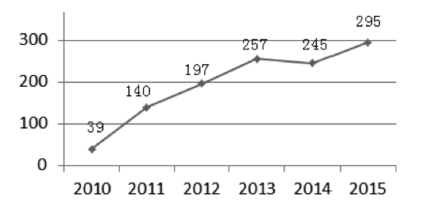
| [3] |
ICS-CERT.ICS-CERTYear-in-Review-2012[EB/OL].,2015-7-10.
|
| [4] |
CS-CERT.ICS-CERT Year-in-Review-2013[EB/OL].,2015-7-10.
|
| [5] |
CS-CERT.ICS-CERTYear-in-Review-2014[EB/OL].,2015-7-10.
|
| [6] |
今日头条,美国工业控制系统网络应急响应小组2015年关键基础设施报告[EB/OL]..
|
| [7] |
SCHUSTER F,PAUL A.A Distributed Intrusion Detection System for Industrial Automation Networks[C]// IEEE.Emerging Technologies & Factory Automation (ETFA),2012 IEEE 17th Conference,September 17-21,2012.Krakow. New Jersey:IEEE,2012:1-4.
|
| [8] |
KISS I,GENGE B,HALLER P,et al.Data Clustering-Based Anomaly Detection in Industrial Control Systems[C]//IEEE.Intelligent Computer Communication and Processing (ICCP),2014 IEEE International Conference,September 4-6 ,2014 .Cluj Napoca.New Jersey:IEEE,2014:275-281.
|
| [9] |
STONE S,TEMPLE M.Radio-Frequency-Based Anomaly Detection for Programmable Logic Controllers in the Critical Infrastructure[J]. International Journal of Critical Infrastructure Protection, 2012, 5(2):66-73.
|
| [10] |
ANDREW GINTER.Experience with Network Anomaly Detection on Industrial Networks[EB/OL]..
|
| [11] |
KNOWLES W,PRINCE D,HUTCHISON D,et al.A Survey of Cyber Security Management in Industrial Control Systems[J]. International Journal of Critical Infrastructure Protection, 2015, 9(C):52-80.
|
| [12] |
PENG J,LIU L.Industrial Control System[C]//IEEE.SecurityIntelligent Human-Machine Systems and Cybernetics (IHMSC) 2011 International Conference,August 26-27 ,2011. Hangzhou Zhejiang.New Jersey:IEEE,2011:156-158.
|
| [13] |
绿盟科技.2013工业控制系统及其安全性研究报告[EB/OL]..
|
| [14] |
CHEN P Y,YANG S,MCCANN J.Distributed Real-Time Anomaly Detection in Networked Industrial Sensing Systems[J]. Industrial Electronics IEEE Transactions on, 2015, 62(6):3832-3842.
|
| [15] |
王小山,杨安,石志强,等. 工业控制系统信息安全新趋势[J]. 信息网络安全,2015(1):6-11.
|
| [16] |
陈庄,黄勇,邹航. 工业控制系统信息安全审计系统分析与设计[J]. 计算机科学,2013,40(06A): 340-343.
|