信息网络安全 ›› 2016, Vol. 16 ›› Issue (6): 15-21.doi: 10.3969/j.issn.1671-1122.2016.06.003
基于Voronoi图的路网轨迹隐私保护研究
肖剑川1,2, 许力1,2( ), 叶阿勇1,2, 林丽美1,2
), 叶阿勇1,2, 林丽美1,2
- 1.福建师范大学数学与计算机科学学院, 福建福州 350007
2.福建省网络安全与密码技术重点实验室, 福建福州 350007
Research on Trajectory Privacy Preserving over Road Network Based on Voronoi Diagram
Jianchuan XIAO1,2, Li XU1,2( ), A-yong YE1,2, Limei LIN1,2
), A-yong YE1,2, Limei LIN1,2
- 1. School of Mathematics and Computer Science, Fujian Normal University, Fuzhou Fujian 350007, China
2.Fujian Provincial Key Laboratory of Network Security and Cryptology, Fuzhou Fujian 350007, China
摘要:
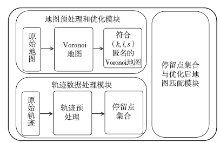
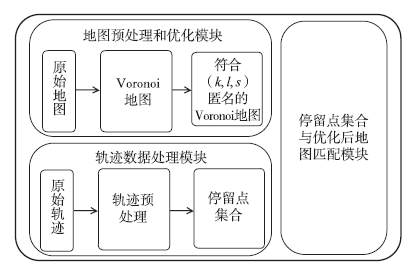
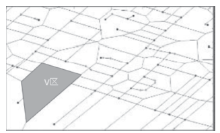
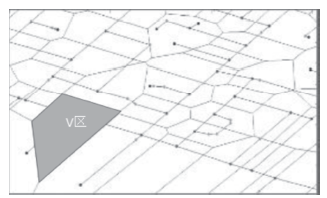
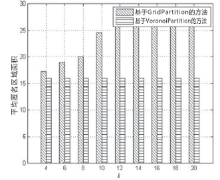
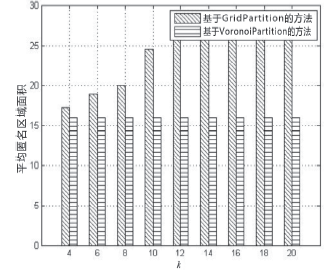
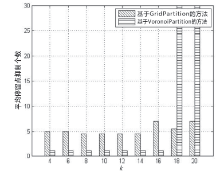
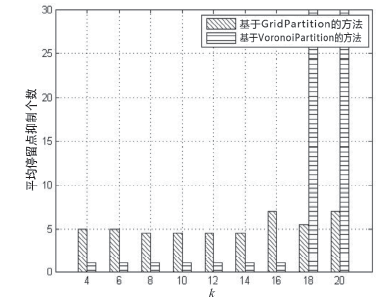
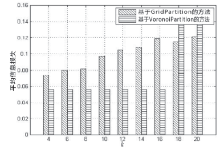
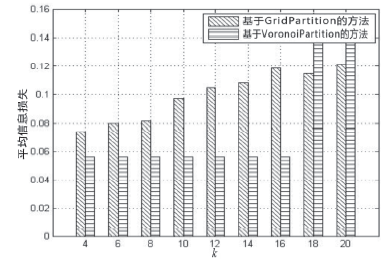
轨迹数据的发布可能泄露用户隐私,文章提出一种基于Voronoi图的停留点路网轨迹隐私保护方法来解决这个问题。根据Voronoi图的特性,文章提出的方法可以保证路段的多样性。在此基础上,考虑到初始划分的区域面积和区域内兴趣点数量存在差异,文章将预处理生成的Voronoi区域进一步优化,使得每个区域满足(k,l,s)匿名。此外,通过识别轨迹中有意义的停留点,根据停留点所在区域做泛化或抑制处理,进一步实现个性化隐私保护。在路网轨迹数据生成器Brinkhoff上的仿真实验表明,在同等隐私安全条件下,文章提出的方法信息损失小。
中图分类号: