信息网络安全 ›› 2016, Vol. 16 ›› Issue (4): 31-37.doi: 10.3969/j.issn.1671-1122.2016.04.005
一种基于CAFL模型的抗弹性泄露密钥交换协议研究
- 1.洛阳外国语学院,河南洛阳 471003
2.密码科学技术国家重点实验室,北京 100878
3.西安电子科技大学计算机学院,陕西西安 710071
-
收稿日期:2016-01-10出版日期:2016-04-20发布日期:2020-05-13 -
作者简介:作者简介: 陆思奇(1990—),男,山东,助教,硕士,主要研究方向为密码学和信息安全;范书珲(1993—),女,广东,研究实习员,主要研究方向为密码学和信息安全;韩旭(1992—),男,河南,硕士研究生,主要研究方向为密码学和信息安全;程庆丰(1979—),男,辽宁,副教授,博士,主要研究方向为密码学和信息安全。
-
基金资助:国家自然科学基金[61402522];密码科学技术国家重点实验室开放课题[2015-MS-07];洛阳外国语学院科研基金[2015XYQ004]
A Leakage Resilient Authenticated Key Exchange Protocol Based on the CAFL Model
Siqi LU1,2, Shuhui FAN1, Xu HAN1, Qingfeng CHENG1,2,3( )
)
- 1. Luoyang University of Foreign Languages, Luoyang Henan 471003, China
2. State Key Laboratory of Cryptology, Beijing 100878, China
3. School of Computer Science and Technology, Xidian University, Xi’an Shaanxi 710071, China
-
Received:2016-01-10Online:2016-04-20Published:2020-05-13
摘要:
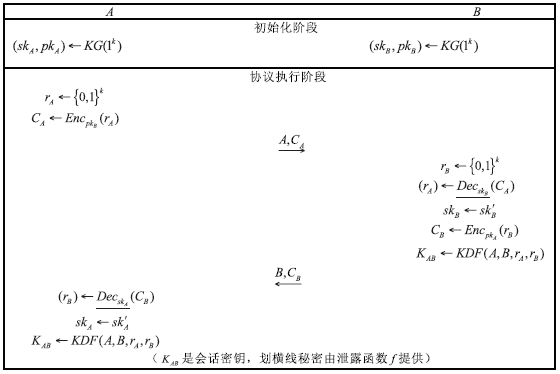
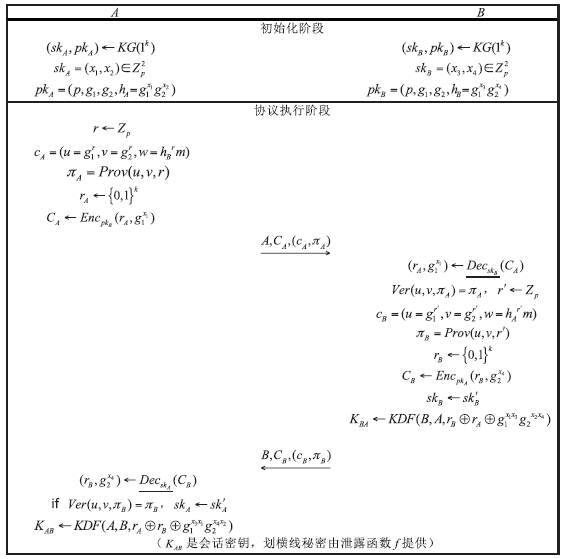
抗弹性泄露密钥交换协议的最初目标就是将存储秘密泄露的危害降到最小,为此Alawatugoda等人提出了基于CAFL安全模型的π协议。该协议在被动攻击下即使一方长期密钥泄露仍是安全的,但在主动攻击下如果一方临时密钥泄露则是不安全的。Toorani等人在2015年给出了对该协议的临时密钥泄露攻击方法。文章针对该安全隐患,在CAFL模型下基于DDH假设和CDH假设对π协议进行了改进,实现了协议参与双方的显式认证。在安全性方面,对其在标准模型下以牺牲较小计算代价获得强安全性进行了证明。此外,文章对π-1协议和 π-2协议的计算代价和安全性进行了分析和讨论。
中图分类号:
引用本文
陆思奇, 范书珲, 韩旭, 程庆丰. 一种基于CAFL模型的抗弹性泄露密钥交换协议研究[J]. 信息网络安全, 2016, 16(4): 31-37.
Siqi LU, Shuhui FAN, Xu HAN, Qingfeng CHENG. A Leakage Resilient Authenticated Key Exchange Protocol Based on the CAFL Model[J]. Netinfo Security, 2016, 16(4): 31-37.
| [1] | SADEGHI A R, NACCACHE D.Towards Hardware-intrinsic Security[M]. Heidelberg: Springer, 2010: 99-134. |
| [2] | DZIEMBOWSKI S, FAUST S.Leakage-resilient Cryptography from the Inner-product Extractor[A]. ASIACRYPT 2011[M]. Heidelberg: Springer,2011: 702-721. |
| [3] | 郁昱, 谷大武. 抗泄露可证明安全流密码研究[J]. 密码学报, 2014, 1(2): 134-145. |
| [4] | 刘伟,叶清,王成. 基于动态密钥管理的改进LEACH路由算法[J]. 信息网络安全,2015(8):41-46. |
| [5] | SHIN S H, KOBARAK K.Secure Password Authentication Schemes and Their Applications[J]. Synthesiology,2014,7(3):179-189. |
| [6] | SHIN S H,KOBARA K,LMAI H.Efficient and Leakage-Resilient Authenticated Key Transport Protocol Based on RSA[C]//ACNS 2005.3rd International Conference,June 7-10, 2005,New York,NY,USA.Heidelberg: Springer,2005: 269-284. |
| [7] | SHIN S H,KOBARA K,LMAI H.An Efficient and Leakage-resilient RSA-Based Authenticated Key Exchange Protocol with Tight Security Reduction[J]. IEICE Transactions on Fundamentals of Electronics, 2007, E90(2): 474-490. |
| [8] | FUJIOKA A,SUZUKI K,USTAOGLU B.Ephemeral Key Leakage Resilient and Efficient ID-AKEs that Can Share Identities,Private and Master Keys[C]//Pairing 2010.Pairing-Based Cryptography - Pairing 2010 4th International Conference,December 13-15,2010,Yamanaka Hot Spring,Japan.Heidelberg: Springer,2010: 187-205. |
| [9] | CHEN L,KUDLA C.Identity Based Authenticated Key Agreement Protocols from Pairings[J]. International Journal of Information Security, 2003, 6(4): 213-241. |
| [10] | FUJIOKA A,SUZUKI K.Sufficient Condition for Identity-Based Authenticated Key Exchange Resilient to Leakage of Secret Keys[C]//ICISC 2011.14th Annual International Conference on Information Security and Cryptology,November 30 - December 2, 2011,Seoul,Korea.Heidelberg: Springer, 2012: 490-509. |
| [11] | 程庆丰, 王永娟, 马传贵. 一种基于身份的密钥协商协议的分析与改进[J]. 信息工程大学学报, 2010, 11(2): 129-136. |
| [12] | 赵洋,包文意,熊虎,等. 云计算里一种陷门无法识别的公钥搜索加密方案[J]. 信息网络安全,2016(1):1-5. |
| [13] | NAOR M. SEGEV G.Public-key Cryptosystems Resilient to Key Leakage[C]//CRYPTO 2009.29th Annual International Cryptology Conference,August 16-20, 2009,Santa Barbara, CA, USA.Heidelberg: Springer, 2009: 18-35. |
| [14] | ALWEN J,DODIS Y,WICHS D.Leakage-Resilient Public-Key Cryptography in the Bounded-retrieval Model[C]//CRYPTO 2009.29th Annual International Cryptology Conference,August 16-20, 2009,Santa Barbara, CA, USA.Heidelberg: Springer, 2009: 36-54. |
| [15] | DODIS Y, HARALAMBIEV K, LOPEZ A, et al.Efficient Public-key Cryptography in the Presence of Key Leakage[C]//ASIACRYPT 2010.16th International Conference on the Theory and Application of Cryptology and Information Security,December 5-9, 2010,Singapore.Heidelberg: Springer, 2010: 613-631. |
| [16] | BRAKERSKI Z,KALAI Y T,KATZ J,et al.Overcoming the Hole in the Bucket: Public-key Cryptography Resilient to Continual Memory Leakage[C]//FOCS 2010,51st Annual IEEE Symposium on Foundations of Computer Science,October 23-26, 2010,Las Vegas, Nevada.New Jersey:IEEE,2010: 501-510. |
| [17] | HALEVI S,LIN H.After-the-Fact Leakage in Public-key Encryption[C]//TCC 2011.8th Theory of Cryptography Conference,March 28-30,2011,Providence, RI,USA. Heidelberg: Springer, 2011: 107-124. |
| [18] | FAUST S,HAZAY C,NIELSEN J B,et al.Signature Schemes Secure Against Hard-to-invert Leakage[J].Journal of Cryptology,2012(2):98-115. |
| [19] | FAUST S,KILTZ E,PIETRZAK K,et al.Leakage-resilient Signatures[M]. Heidelberg: Springer-Verlag,2010: 343-360. |
| [20] | KATZ J,VAIKUNTANATHAN V.Signature Schemes with Bounded Leakage Resilience[C]// ASIACRYPT 2009.15th International Conference on the Theory and Application of Cryptology and Information Security, December 6-10, 2009, Tokyo, Japan.Heidelberg: Springer,2009, 703-720. |
| [21] | MALKIN T,TERANISHI I,VAHLIS Y,et al.Signatures Resilient to Continual Leakage on Memory and Computation[C]//TCC 2011.8th Theory of Cryptography Conference, TCC 2011,March 28-30,2011.Providence,RI. USA. Heidelberg: Springer,2011: 89-106. |
| [22] | 王志伟,张伟. 有界恢复模型下弹性泄露签名的新构造[J]. 小型微型计算机系统, 2012,33(2): 380-382. |
| [23] | SHIN S H,KOBARA K,IMAI H.Leakage-Resilient Authenticated Key Establishment Protocols[C]// ASIACRYPT 2003.9th International Conference on the Theory and Application of Cryptology and Information Security,November 30-December 4,2003.Taipei, China. Heidelberg: Springer,2003, 155-172. |
| [24] | SHIN S H,KOBARA K,IMAI H.Compact and Efficient Leakage-Resilient Authenticated Key Exchange Protocol[J]. GESTS International Transactions on Computer Science and Engineering, 2005, 19(1): 159-171. |
| [25] | SHIN S H,KOBARA K,IMAI H.A Simple Leakage-resilient Authenticated Key Establishment Protocol, Its Extensions,Applications[J]. IEICE Transactions on Fundamentals of Electronics, 2005, E88-A(3): 736-754. |
| [26] | SHIN S H,KOBARA K,IMAI H.Efficient and Leakage-Resilient Authenticated Key Transport Protocol Based on RSA[C]// ACNS 2005.3rd International Conference ACNS 2005,June 7-10,2005.New York,NY,USA.Heidelberg: Springer,2005: 269-284. |
| [27] | PHAN R C W,CHOO K K R,HENG S H.Security of a Leakage-Resilient Protocol for Key Establishment and Mutual Authentication[C]//ProvSec 2007.1st International Conference ProvSec 2007, November 1-2,2007.Wollongong,Australia.Heidelberg: Springer,2007: 169-177. |
| [28] | SHIN S H,KOBARA K,IMAI H. An Efficient and Leakage-Resilient RSA-based Authenticated Key Exchange Protocol with Tight Security Reducation[J]. IEICE Transactions on Fundamentals of Electronics, 2007, E90-A(2): 474-490. |
| [29] | IMAI H, SHIN S H, KOBARA K.Introduction to Leakage-Resilient Authenticated Key Exchange Protocols and Their Applications[J]. Special English Edition of Journal of Korean Institute of Information Security and Cryptology, 2008, 18(6B): 207-217. |
| [30] | IMAI H, SHIN S H, KOBARA K. A secure Authenticated Key Exchange Protocol for Credential Services[J]. IEICE Transactions on Fundamentals of Electronics, 2008, E91-A(1): 139-149. |
| [31] | FATHI H,SHIN S H,KOBARA K,et al.Leakage-Resilient Security Architecture for Mobile IPv6 in Wireless Overlay Networks[J]. IEICE Transactions on Communications, 2005, 23(11): 2182-2193. |
| [32] | FATHI H,SHIN S H,KOBARA K,et al.LR-AKE-based AAA for Network Mobility(NEMO)over Wireless Links[J]. IEEE Journal on Selected Areas in Communications, 2006, 24(9): 1725-1737. |
| [33] | SHIN S H,FATHI H,KOBARA K,et al. A New Security Architecture for Personal Networks and Its Performance Evaluation[J]. IEICE Transactions on Communications, 2008, E91-B(7): 2255-2264. |
| [34] | DODIS Y,OSTROVSKY R,REYZIN L,et al.Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data[J]. SIMA Journal on Computing, 2008, 38(1): 97-139. |
| [35] | TOORANI M.On Continuous After-the-Fact Leakage-Resilient Key Exchange[C]//ACM.CS2 '15 Proceedings of the Second Workshop on Cryptography and Security in Computing Systems,January 19-21, 2015, Amsterdam.New York:ACM ,2015: 31-45. |
| [36] | MORIYAMA D,OKAMOTO T.Leakage Resilient eCK-Secure Key Exchange Protocol without Random Oracles[C]// ACM.ASIACCS '11 Proceedings of the 6th ACM Symposium on Information,Computer and Communications Security,March 22-24,2011.Hong Kong, China.New York:ACM ,2011: 441-447. |
| [37] | YANG G,MU Y,SUSILO W,et al.Leakage Resilient Authenticated Key Exchange Secure in the Auxiliary Input Model[C]//ISPEC 2013.9th International Conference ISPEC 2013,May 12-14,2013.Lanzhou,China. Heidelberg: Springer,2013: 204-217. |
| [38] | ALAWATUGODA J,STEBILA D,BOYD C.Modelling After-the-Fact Leakage for Key Exchange[C]//ASIA. CCS '14 Proceedings of the 9th ACM Symposium on Information, Computer and Communications Security,June 3-6,2014.Kyoto,Japan.New York:ACM ,2014: 207-216. |
| [1] | 李喆, 韩益亮, 李鱼. 基于Polar码的密钥交换方案[J]. 信息网络安全, 2019, 19(10): 84-90. |
| [2] | 成娟娟, 郑昉昱, 林璟锵, 董建阔. Curve25519椭圆曲线算法GPU高速实现[J]. 信息网络安全, 2017, 17(9): 122-127. |
| [3] | 游伟青, 陈小明, 齐健. 一类抗量子计算的公钥密码算法研究[J]. 信息网络安全, 2017, 17(4): 53-60. |
| [4] | 项顺伯. 一种有效的基于身份的两方密钥交换协议[J]. , 2012, 12(2): 0-0. |
| [5] | 范永清. IPSec VPN数据安全传输[J]. , 2009, 9(4): 0-0. |
| [6] | 刘晓娟;杜彦辉. RSA公钥体制在PGP中的应用[J]. , 2009, 9(4): 0-0. |
| [7] | 郎为民;孙月光;孙少兰;刘军. PKMvl协议研究[J]. , 2008, 8(10): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||