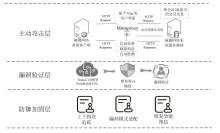
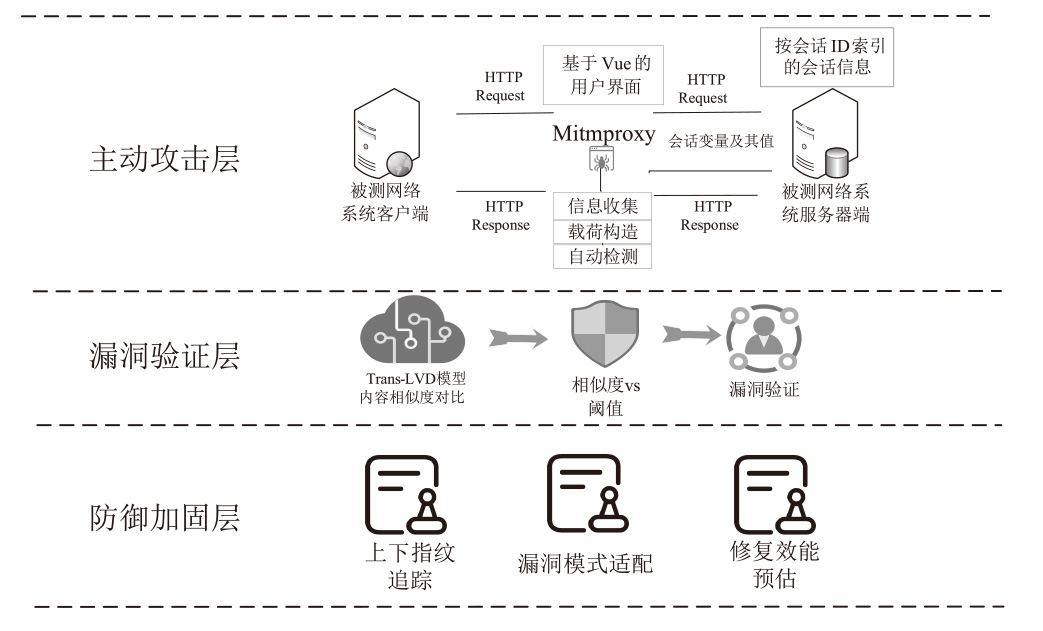
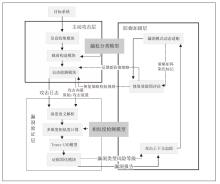
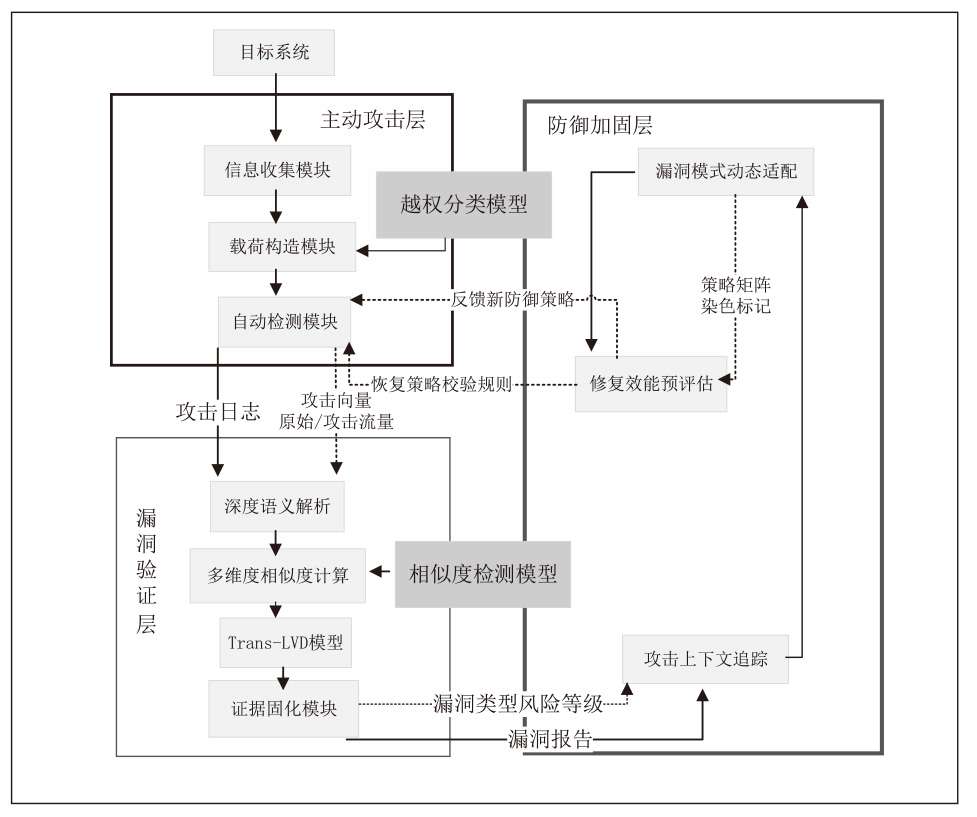
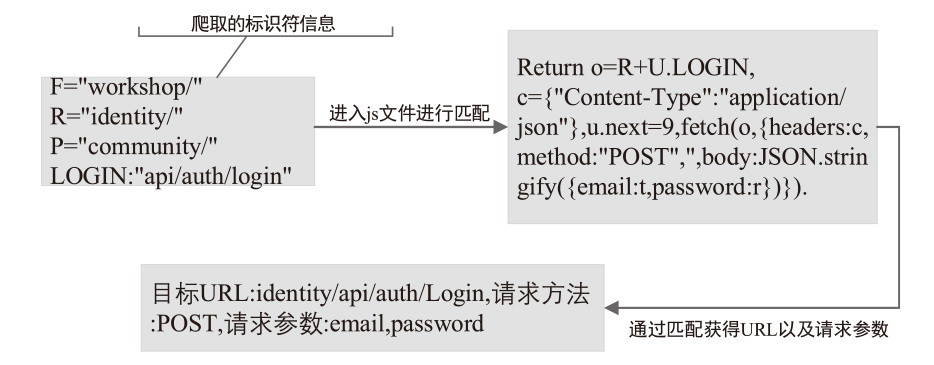
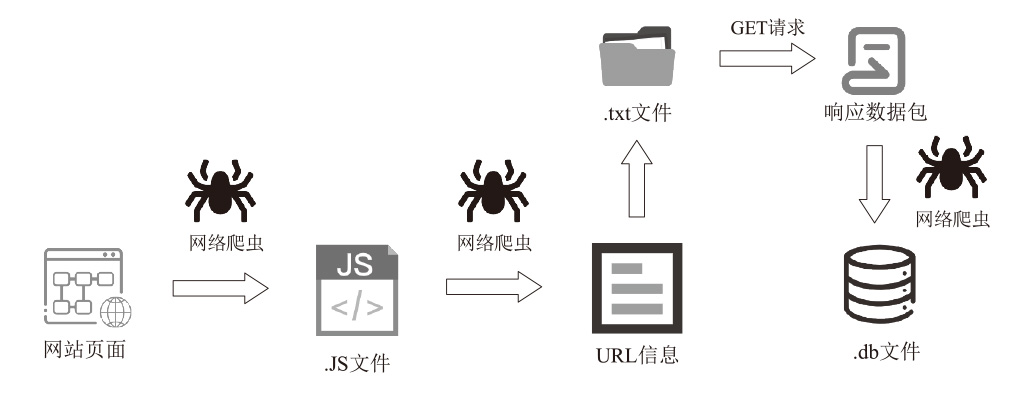
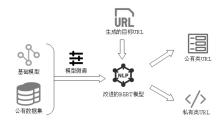
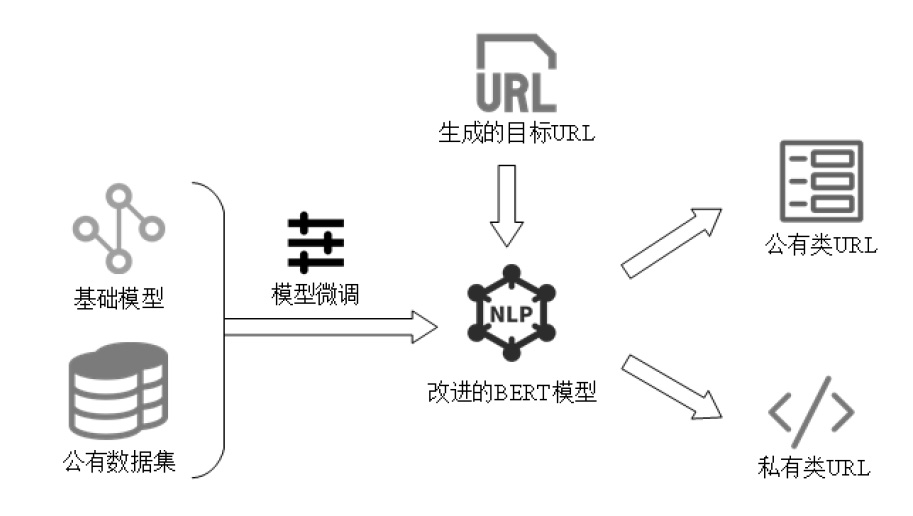
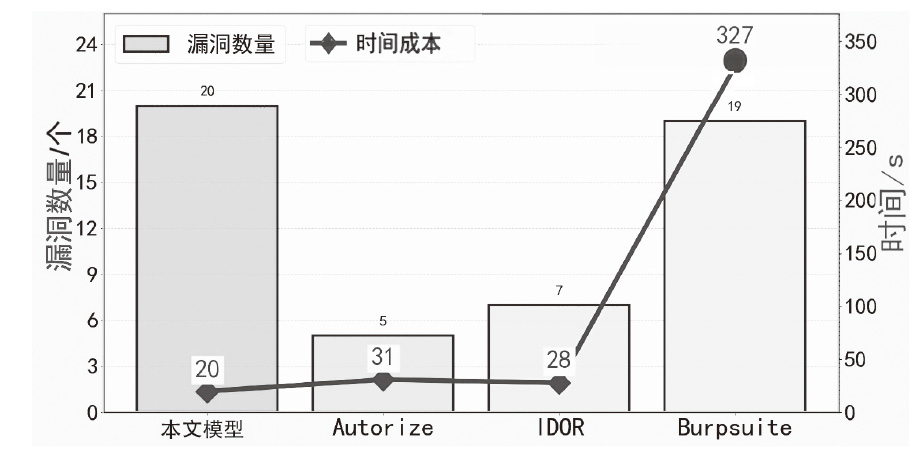
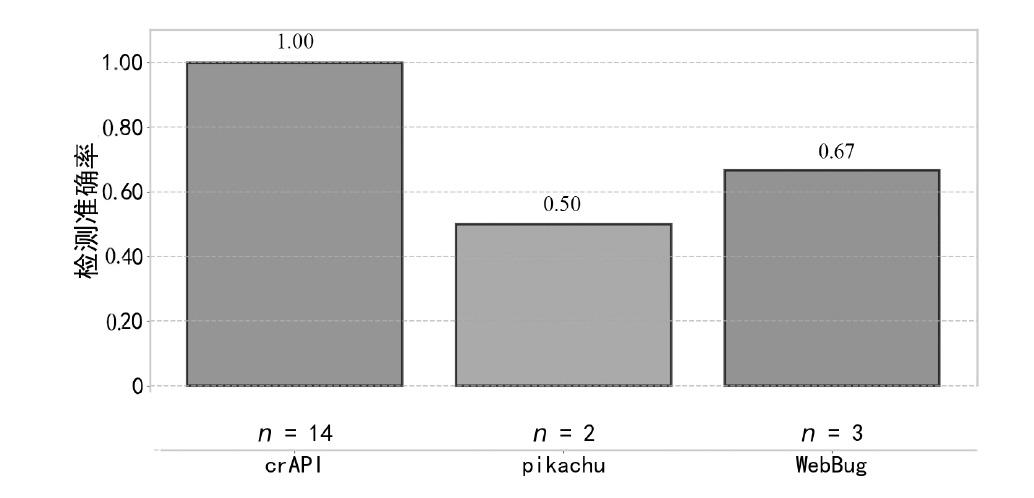
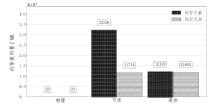
| [1] |
WANG Lian, ZHOU Shiteng, OU Shaohua, et al. Automatic Detection Method,Device and Computer Equipment for Privilege Escalation Vulnerabilities Based on Traffic: China, 202111220698.4[P]. 2022-03-02.
|
|
王练, 周世腾, 欧绍华, 等. 基于流量的越权漏洞自动检测方法、 装置及计算机设备:中国,202111220698.4[P]. 2022-03-02.
|
| [2] |
WANG Lian, OU Shaohua, ZHOU Shiteng, et al. A Method for Detecting Android Malware Based on Multi-Features: China, 202111398522.8[P]. 2021-11-19.
|
|
王练, 欧绍华, 周世腾, 等. 一种基于多特征的安卓恶意软件检测方法:中国, 202111398522.8[P]. 2021-11-19.
|
| [3] |
DEEPA G, SANTHI T P, PRASEED A, et al. DetLogic: A Black-Box Approach for Detecting Logic Vulnerabilities in Web Applications[J]. Journal of Network and Computer Applications, 2018, 109: 89-109.
|
| [4] |
MENG Liang, ZENG Mingfei, XIE Ming, et al. Research on Active Defense Technology Based on Power System Network Security[C]// IEEE. The 12th International Conference on Communication Systems and Network Technologies (CSNT). New York: IEEE, 2023: 710-714.
|
| [5] |
WU Junxi, LIN Feng, GAO Hongyun. A Method for Identifying Security Vulnerabilities in Multi-Attribute Information Exchange under Static Defense[J]. Journal of Xi’an University of Posts and Telecommunications, 2024, 29(6): 79-85.
|
|
伍均玺, 林峰, 高红云. 静态防御下多属性信息交换安全漏洞识别方法[J]. 西安邮电大学学报, 2024, 29(6): 79-85.
|
| [6] |
TIAN Zhenzhou, LYU Jiajun, WANG Fanfan. Function-Level Code Vulnerability Detection Based on Multi-Representation Fusion[J]. Journal of Xi’an University of Posts and Telecommunications, 2023, 28(1): 78-84.
|
|
田振洲, 吕佳俊, 王凡凡. 基于多表征融合的函数级代码漏洞检测方法[J]. 西安邮电大学学报, 2023, 28(1): 78-84.
|
| [7] |
WANG Juan, ZHANG Boxian, ZHANG Zhijie, et al. Java Deserialization Vulnerability Mining Based on Fuzz Testing[J]. Information Network Security, 2025, 25(1): 1-12.
|
|
王鹃, 张勃显, 张志杰, 等. 基于模糊测试的 Java反序列化漏洞挖掘[J]. 信息网络安全, 2025, 25(1): 1-12.
|
| [8] |
MUNONYE K, MARTINEK P. Machine Learning Approach to Vulnerability Detection in OAuth 2.0 Authentication and Authorization Flow[J]. International Journal of Information Security, 2022, 21(4): 223-237.
|
| [9] |
ZHONG Li. A Survey of Prevent and Detect Access Control Vulnerabilities[EB/OL]. (2023-04-20)[2024-09-03]. https://arxiv.org/abs/2304.10600.
|
| [10] |
QIAN Xingzhi. LAMD: Context-Driven Android Malware Detection and Classification with LLMs[EB/OL]. (2025-02-18)[2025-02-21]. https://arxiv.org/html/2502.13055v1.
|
| [11] |
YANG Lisheng, LUO Wenhua. Tri-BERT-SENet: Malicious Web Page Detection Integrating Multiple Features[J]. Journal of Chinese computer Systems, 2023, 44(4): 875-880.
|
|
杨立圣, 罗文华. Tri-BERT-SENet:融合多特征的恶意网页识别[J]. 小型微型计算机系统. 2023, 44(4): 875-880.
|
| [12] |
ZHANG Zhifei, LIU Feng, GE Yiyang, et al. An Intrusion Detection Method Based on Depthwise Separable Convolution and Attention Mechanism[J]. Journal of Internet of Things, 2023, 7(1): 49-59.
|
|
张志飞, 刘峰, 葛祎阳, 等. 一种基于深度可分离卷积和注意力机制的入侵检测方法[J]. 物联网学报, 2023, 7(1): 49-59.
doi: 10.11959/j.issn.2096-3750.2023.00307
|
| [13] |
HUANG Yiwei. The GAN is Dead; Long Live the GAN! A Modern GAN Baseline[EB/OL]. (2025-01-01)[2025-02-03]. https://arxiv.org/abs/2501.05441.
|
| [14] |
AL-SADA B, SADIGHIAN A, OLIGERI G, et al. MITRE ATT&CK: State of the Art and Way Forward[EB/OL]. (2023-08-27)[2025-02-03]. https://arxiv.org/abs/2308.14016.
|
| [15] |
LYU Tao, LI Ruishi, YANG Yi, et al. RTFM! Automatic Assumption Discovery and Verification Derivation from Library Document for API Misuse Detection[C]// ACM. 2020 ACM SIGSAC Conference on Computer and Communications Security (CCS). New York: ACM, 2020: 1-12.
|
| [16] |
WU Panpan, YU Jiawen, HAN Bingqing. Discussion on the Mining Approach for Web Security Logic Vulnerabilities Based on HTTP Packets[J]. Computer Era, 2023(9): 24-28.
|
|
吴盼盼, 俞嘉雯, 韩冰青. 浅谈基于HTTP数据包的Web安全逻辑漏洞挖掘思路[J]. 计算机时代, 2023(9): 24-28.
|
| [17] |
SHI Chong, PENG Jiahao, ZHU Shuying, et al. From Passive Defense to Proactive Defence: Strategies and Challenges[J]. Journal of Cybersecurity and Information Systems, 2022, 15(2): 123-135.
|
| [18] |
RIGGS H, TUFAIL M, KUMAR S, et al. Impact, Vulnerabilities, and Mitigation Strategies for Cyber-Secure Critical Infrastructure[J]. Sensors. 2023, 23(8): 4060-4069.
|
| [19] |
CHENG Jia, MAO Pengpeng. Research on Network Information Security Technology in Cloud Computing Environment[J]. Wireless Internet Technology, 2023, 20(14): 161-164.
|
|
程嘉, 冒鹏鹏. 云计算环境下网络信息安全技术研究[J]. 无线互联科技, 2023, 20(14): 161-164.
|
| [20] |
ZHANG Huanqing, LIU Chunming, ZHAO Yulong, et al. A Novel Proactive Operation Strategy to Enhance Power System Resilience[J]. Power System Technology, 2024, 48(5): 2012-2021.
|
|
张焕青, 刘春明, 赵宇龙, 等. 一种提升电力系统韧性的新型主动防御策略[J]. 电网技术, 2024, 48(5): 2012-2021.
|
 ), ZHAO Xiang
), ZHAO Xiang