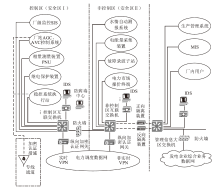
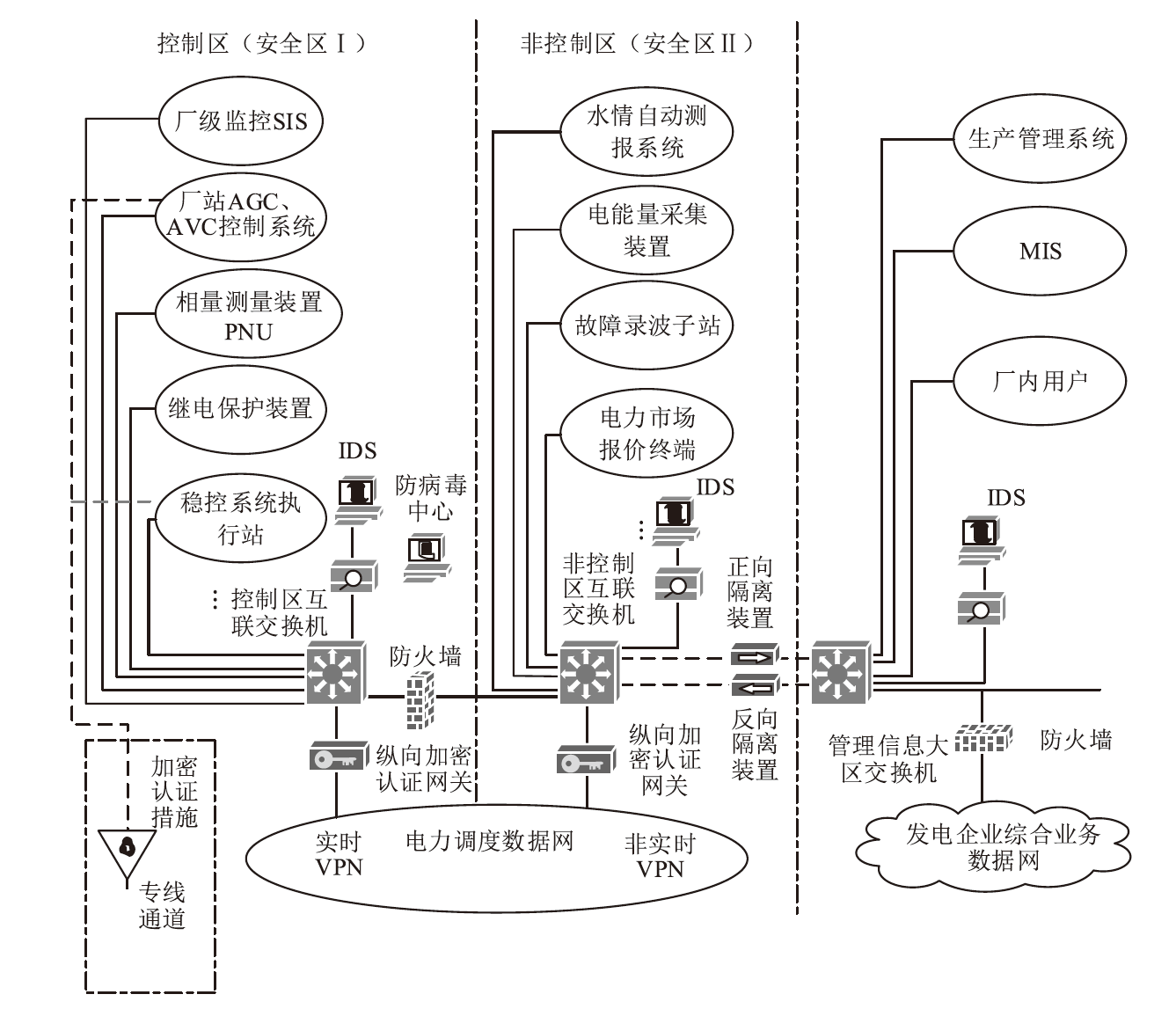
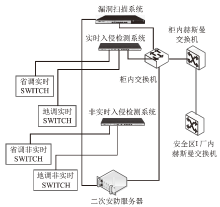
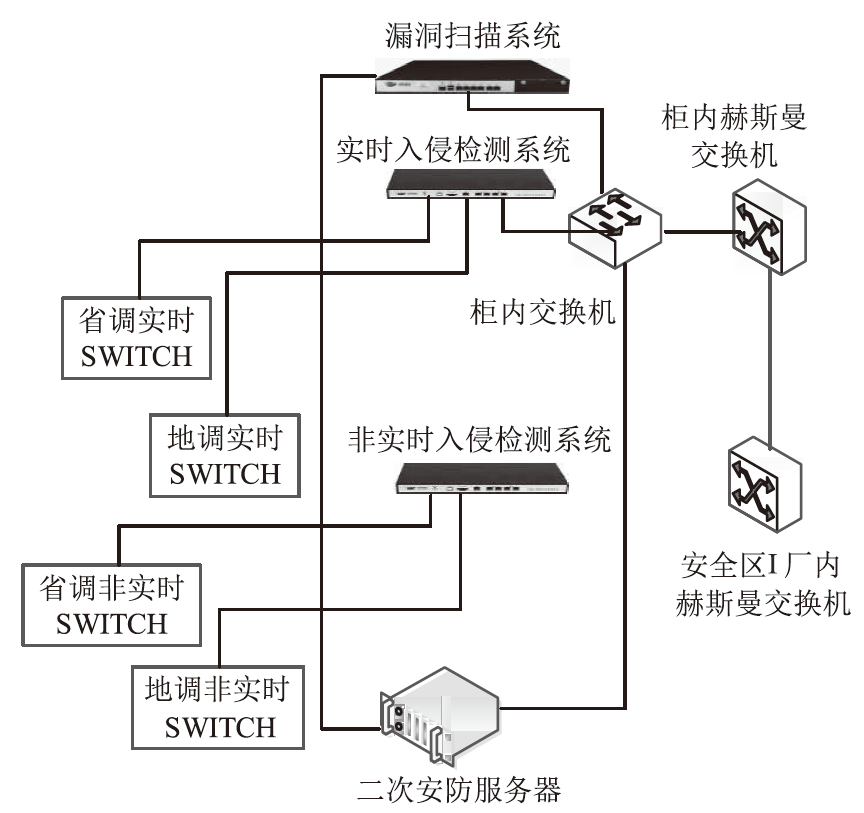
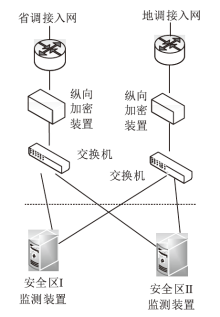
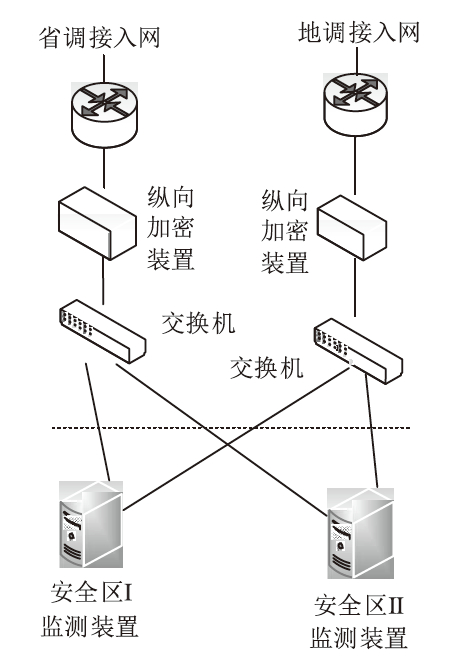
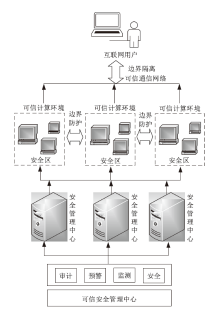
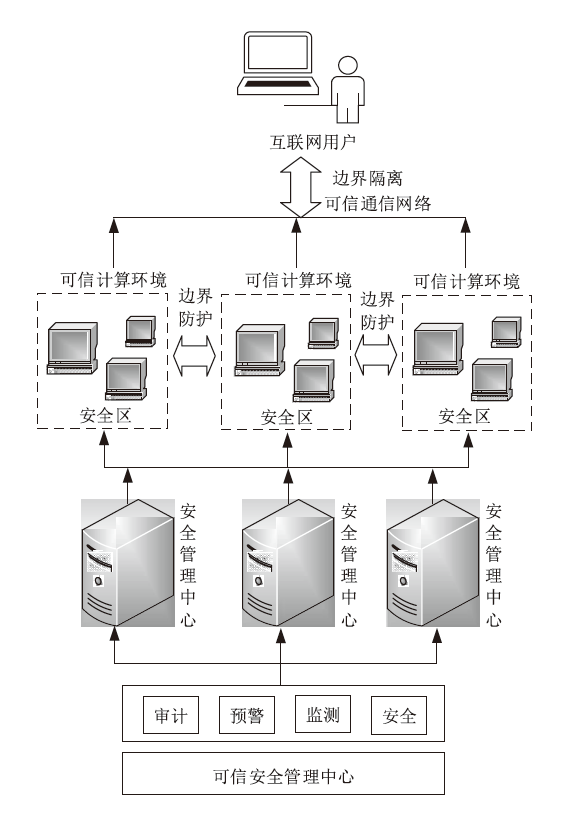
| [1] |
BI Ting, CHEN Xuehong, YANG Shuaifeng. Thoughts on the Protection of Key Information Infrastructure[J]. China Information Security, 2019(6): 92-94.
|
|
毕婷, 陈雪鸿, 杨帅锋. 关键信息基础设施保护工作思考[J]. 中国信息安全, 2019(6):92-94.
|
| [2] |
XIE Yongjiang. Focus on Building a National Integrated Security System for Key Information Infrastructure[J]. Secrecy Work, 2022(12): 50-52.
|
|
谢永江. 着力构建全国一体化的关键信息基础设施安全体系[J]. 保密工作, 2022(12):50-52.
|
| [3] |
FU Jing. Exploration and Practice of Security Protection of Critical Information Infrastructure of Water Conservancy[J]. Netinfo Security, 2023, 23(8): 121-127.
|
|
付静. 水利关键信息基础设施安全保护探索与实践[J]. 信息网络安全, 2023, 23(8):121-127.
|
| [4] |
WU Shuang, PENG Zhichen. Considerations on Cyber Security in Hydropower Industry and Response Measures[J]. Dam & Safety, 2020(6): 9-11.
|
|
吴双, 彭之辰. 水电站大坝网络安全与应对措施[J]. 大坝与安全, 2020(6):9-11.
|
| [5] |
CAI Yang, FU Jing, ZHAN Quanzhong, et al. Implement Concept of “Three-Six-Prevention” and Protect Safety of Water Conservancy Key Information Infrastructure[J]. Water Resources Informatization, 2021(6): 1-4.
|
|
蔡阳, 付静, 詹全忠, 等. 贯彻“三化六防” 理念, 保护水利关键信息基础设施安全[J]. 水利信息化, 2021(6):1-4.
|
| [6] |
SHEN Changxiang. Innovation-Driven Development of Active Immunity Trusted Computing, Building a Secure and Trustworthy Foundation for Cyber Power and Digital China[J]. Journal of Cybersecurity, 2023(1): 1-16.
|
| [7] |
ZHANG Min, ZHANG Wuyi, HAN Guifen. Industrial Control System Information System Security[J]. Industrial Control Computer, 2013, 26(10): 25-27.
|
|
张敏, 张五一, 韩桂芬. 工业控制系统信息安全防护体系研究[J]. 工业控制计算机, 2013, 26(10):25-27.
|
| [8] |
TDHX. The Path of Critical Information Infrastructure Protection under the Classified Cybersecurity 2.0: Hydropower Chapter[EB/OL]. (2020-05-28)[2024-02-10]. http://www.tdhx.com/news/555.html.
|
|
天地合兴. 关键信息基础设施的等保2.0之路|水力发电篇[EB/OL]. (2020-05-28)[2024-02-10]. http://www.tdhx.com/news/555.html.
|
| [9] |
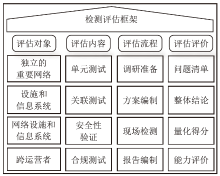
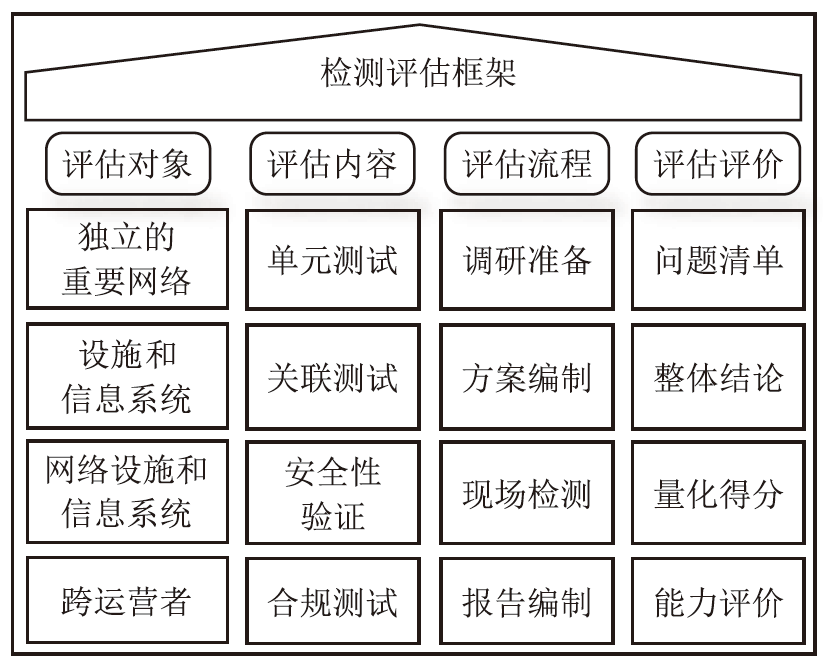
LI Qiuxiang. Building Systematic Assessment Capabilities for Critical Infrastructure to Strengthen the Fundamental Security of Important Networks and Information Facilities[EB/OL]. [2024-02-10]. https://www.dwcon.cn/post/2990.
|
|
李秋香. 构建体系化关基检测评估能力筑牢重要网络和信息设施基础安全防线[EB/OL]. [2024-02-10]. https://www.dwcon.cn/post/2990.
|
| [10] |
SUN Chengcheng. Research on Cybersecurity Governance Countermeasures[J]. Netinfo Security, 2023, 23(6): 104-110.
|
|
孙珵珵. 网络安全治理对策研究[J]. 信息网络安全, 2023, 23(6):104-110.
|
| [11] |
ZHAO Changzhi, LIU Yuling. Exploration of Security Monitoring and Early Warning Technology for Critical Information Infrastructure[J]. China Information Security, 2022(9): 1-6.
|
|
赵昌志, 刘玉玲. 关键信息基础设施安全监测预警技术探析[J]. 中国信息安全, 2022(9):1-6.
|
| [12] |
NI Lishun. Application Framework of Cryptography in Critical Information Infrastructure[EB/OL]. [2024-02-10]. https://baijiahao.baidu.com/s?id=1785150103636106958&wfr=spider&for=pc.
|
|
倪力舜. 密码在关键信息基础设施中的应用体系[EB/OL]. [2024-02-10]. https://baijiahao.baidu.com/s?id=1785150103636106958&wfr=spider&for=pc.
|
 ), ZHU Li1, LIU Xing’an1, ZHENG Wei1, GU Yishun2
), ZHU Li1, LIU Xing’an1, ZHENG Wei1, GU Yishun2