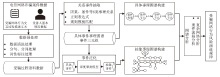
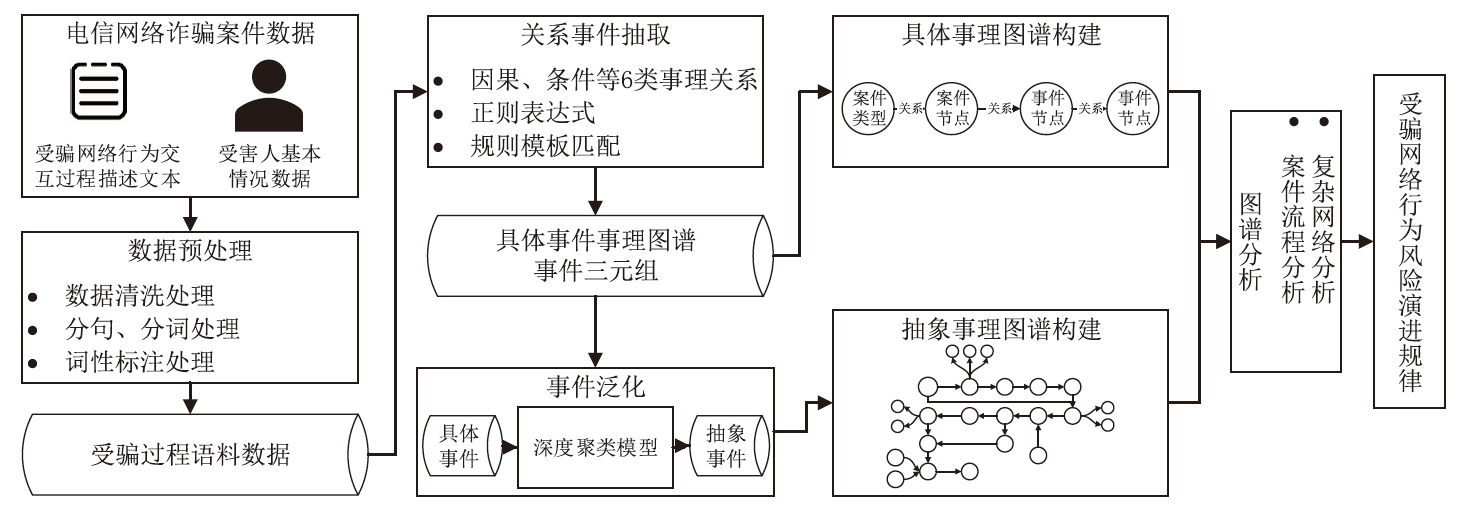
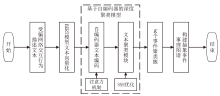
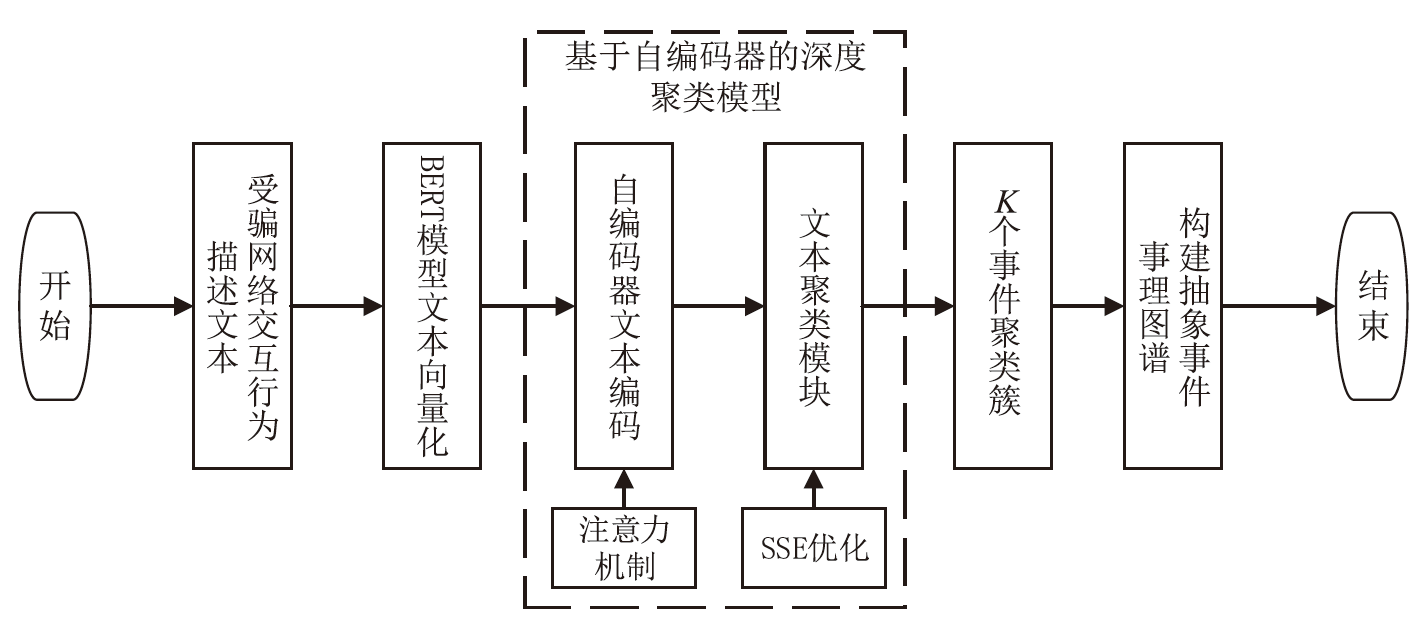
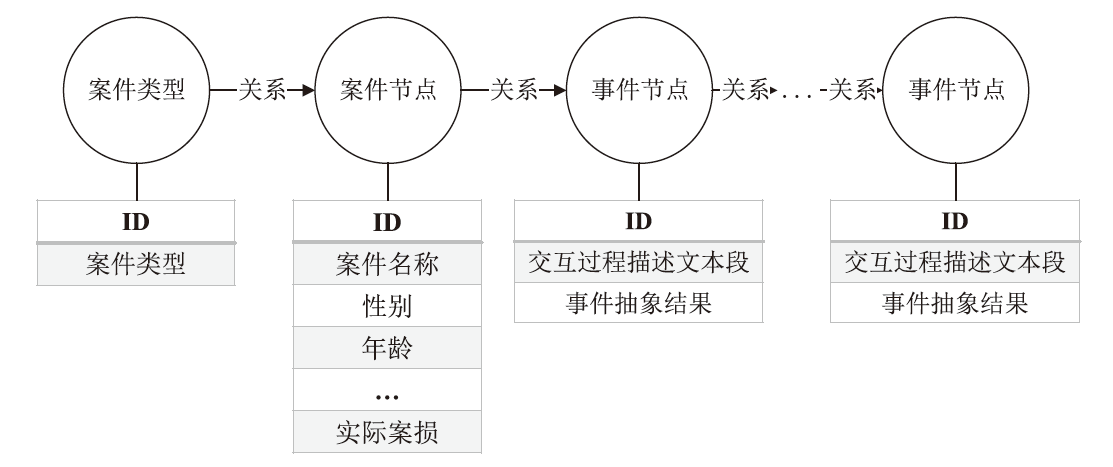
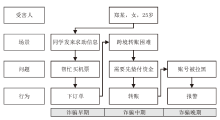
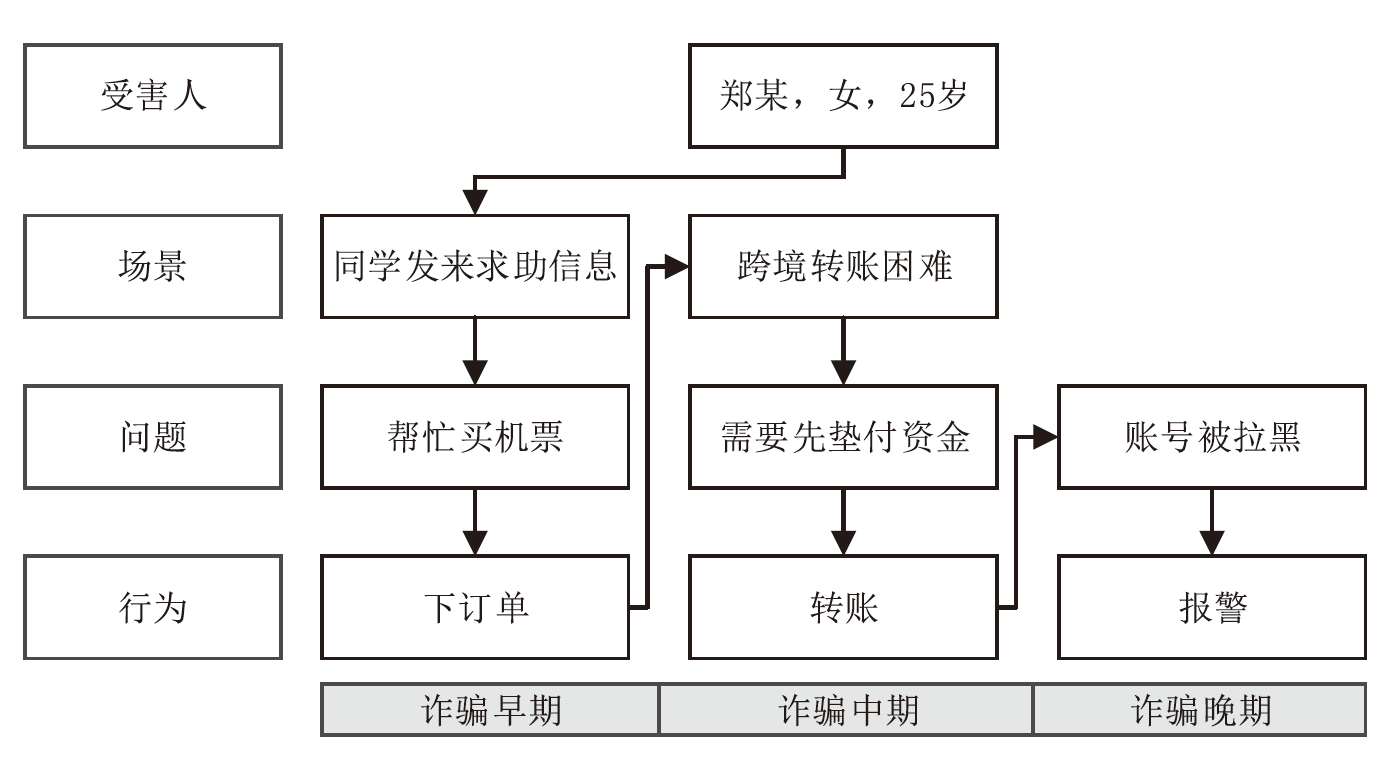
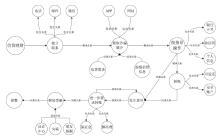
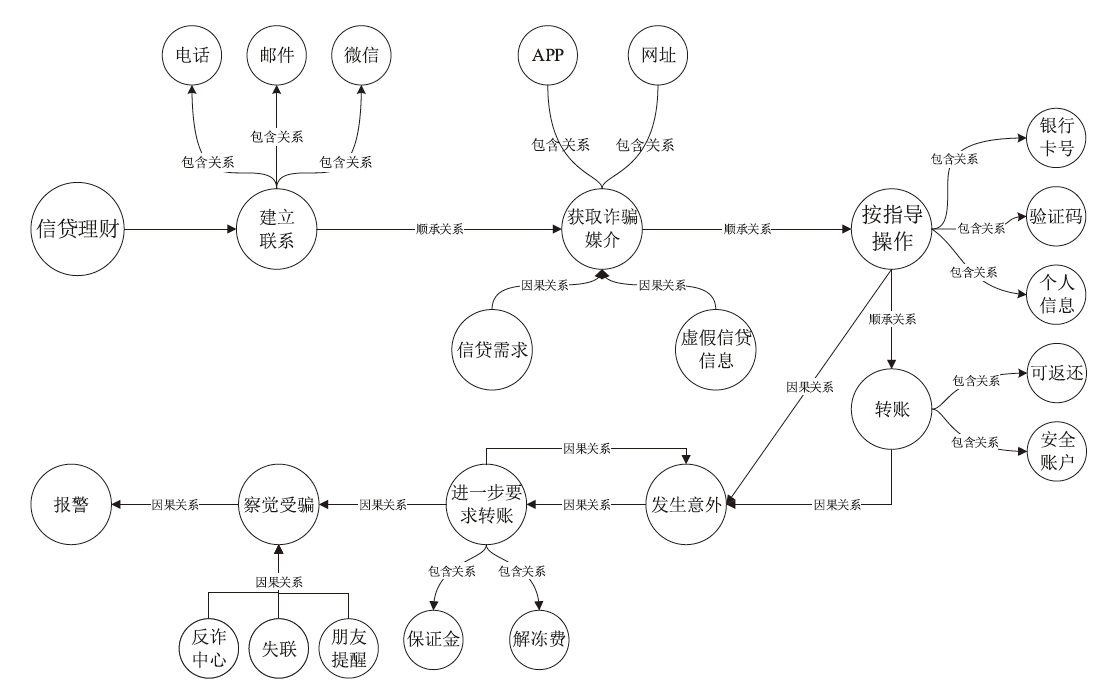
Netinfo Security ›› 2024, Vol. 24 ›› Issue (11): 1696-1709.doi: 10.3969/j.issn.1671-1122.2024.11.009
Previous Articles Next Articles
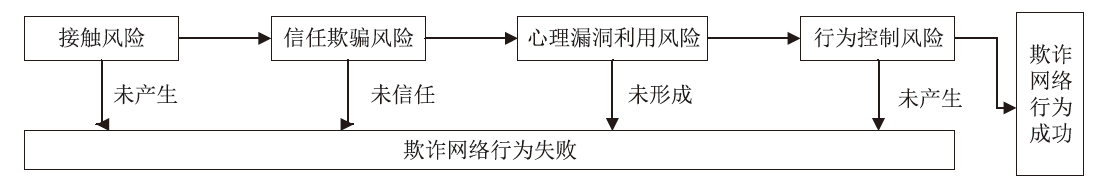
Research on the Evolution of Defrauded Network Behavior Risk Based on Eventic Graph
ZHOU Shengli1,2( ), XU Rui1, CHEN Tinggui3, JIANG Keyi2
), XU Rui1, CHEN Tinggui3, JIANG Keyi2
- 1. School of Cyberspace Security, Hangzhou Dianzi University, Hangzhou 310018, China
2. Department of Computer and Information Security, Zhejiang Police College, Hangzhou 310053, China
3. School of Statistics, Zhejiang Gongshang University, Hangzhou 310018, China
-
Received:2024-06-17Online:2024-11-10Published:2024-11-21
CLC Number:
Cite this article
ZHOU Shengli, XU Rui, CHEN Tinggui, JIANG Keyi. Research on the Evolution of Defrauded Network Behavior Risk Based on Eventic Graph[J]. Netinfo Security, 2024, 24(11): 1696-1709.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.11.009
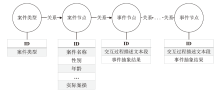
| 模式 | 匹配模板 | 正则表达式(部分) |
|---|---|---|
| 由因到果 | <Conj>{Cause}, <Conj>{Effect} | (因为|由于)([^,。;!?]*)(,|。|;|!|?)([^,。;!?]*)(所以|因此|导致|致使)([^,。;!?]*) |
| 由果溯因 | <Conj>{Effect}, <Conj>{Cause} | (所以|因此|导致|致使)([^,。;!?]*)(,|。|;|!|?)([^,。;!?]*)(因为|由于)([^,。;!?]*) |
| 顺承词完整 | <Conj>{Eventl}, <Conj>{Event2} | (首先|第一)([^,。;!?]+)(然后|接着|之后)([^,。;!?]+) |
| 顺承词居中 | {Eventl},<Conj> {Event2} | ([^,。;!?]+)(就|才|之后)([^,。;!?]+) |
| [1] | LACUSKA M, PERACEK T. Trends in Global Telecommunication Fraud and Its Impact on Business[J]. Developments in Information & Knowledge Management for Business Applications, 2021(1): 459-485. |
| [2] | LIU Weijun. Ecological Governance of Telecommunications and Online Fraud: Taking the Anti-Telecom and Online Fraud Law as an Example[J]. Legal Forum, 2023, 38(4): 94-105. |
| 刘为军. 论电信网络诈骗的生态治理——以《反电信网络诈骗法》为主要研究样本[J]. 法学论坛, 2023, 38(4):94-105. | |
| [3] | TIAN Ling, ZHOU Xue, WU Yanping, et al. Knowledge Graph and Knowledge Reasoning: A Systematic Review[J]. Journal of Electronic Science and Technology, 2022, 20(2): 159-168. |
| [4] | MAN Na, WANG Kechao, LIU Lin. Using Computer Cognitive Atlas to Improve Students’ Divergent Thinking Ability[J]. Journal of Organizational and End User Computing (JOEUC), 2021, 33(6): 1-16. |
| [5] | ZHANG Bin, SUN Ximin, LI Xiaoming, et al. Construction and Application of Event Logic Graph: A Survey[C]// Springer. International Conference on Database Systems for Advanced Applications. Heidelberg: Springer, 2022: 160-174. |
| [6] | WEI Jianxiang, LIANG Shuai, ZHU Yunxia, et al. Progress in the Study of Event Evolution Graph[J]. Information and Documentation Services, 2023, 44(6): 35-43. |
| 魏建香, 梁帅, 朱云霞, 等. 事理图谱研究进展[J]. 情报资料工作, 2023, 44(6):35-43. | |
| [7] | DING Xiao, LI Zhongyang. Event-Reasoning Graph: Patterns and Models of Event Evolution[EB/OL]. (2019-07-22)[2024-06-02]. https://www.leiphone.com/category/ai/rz7I2kfM7VIkNPSM.html. |
| 丁效, 李忠阳. 事理图谱:事件演化的规律和模式[EB/OL]. (2019-07-22)[2024-06-02]. https://www.leiphone.com/category/ai/rz7I2kfM7VIkNPSM.html. | |
| [8] | CUI Ying. Event Extraction in Political Diplomacy Based on Similar Semantics and Dependency Syntax[J]. Computer Engineering & Science, 2020, 42(9): 1632-1639. |
| 崔莹. 基于相似义原和依存句法的政外领域事件抽取方法[J]. 计算机工程与科学, 2020, 42(9):1632-1639. | |
| [9] | LI Qian, PENG Hao, LI Jianxin, et al. Reinforcement Learning-Based Dialogue Guided Event Extraction to Exploit Argument Relations[J]. IEEE/ACM Transactions on Audio, Speech, and Language Processing, 2021, 21(5): 520-533. |
| [10] | ZHOU Yang, CHEN Yubo, ZHAO Jun, et al. What the Role is vs. What Plays the Role: Semi-Supervised Event Argument Extraction via Dual Question Answering[C]// AAAI. Proceedings of the AAAI Conference on Artificial Intelligence. New York: AAAI, 2021: 14638-14646. |
| [11] |
ZHAI Lizhi, LI Ruixiang, YANG Jiabei, et al. Overview about Composite Semantic-Based Event Graph Construction[J]. Computer Science, 2023, 50(9): 242-259.
doi: 10.11896/jsjkx.230400046 |
|
翟利志, 李睿祥, 杨佳贝, 等. 基于复合语义特征的事件图谱构建技术研究进展[J]. 计算机科学, 2023, 50(9):242-259.
doi: 10.11896/jsjkx.230400046 |
|
| [12] | SU Qi, ZHAO Xiaozhe, SUN Dongpu, et al. Event Knowledge Graph Extracted from Intelligence Text[C]// IEEE. 2022 8th International Symposium on System Security, Safety, and Reliability (ISSSR). New York: IEEE, 2022: 139-145. |
| [13] |
LIU Yashu, LUAN Yu, ZHOU Honglei, et al. Research on the Dynamic Evolution of Major Emergencies Based on Event Knowledge Graph[J]. Library and Information Service, 2022, 66(10): 143-151.
doi: 10.13266/j.issn.0252-3116.2022.10.013 |
|
刘雅姝, 栾宇, 周红磊, 等. 基于事理图谱的重大突发事件动态演变研究[J]. 图书情报工作, 2022, 66(10):143-151.
doi: 10.13266/j.issn.0252-3116.2022.10.013 |
|
| [14] | WU Jiang, HUANG Qian, HE Chaocheng, et al. Propagation and Evolution of Public Opinion in the Outbreak of AlGC Based on the Theory of Tipping Point[J]. Journal of Modern Information, 2023, 43(7): 145-161. |
|
吴江, 黄茜, 贺超城, 等. 基于引爆点理论的人工智能生成内容微博网络舆情传播与演化分析[J]. 现代情报, 2023, 43(7):145-161.
doi: 10.3969/j.issn.1008-0821.2023.07.014 |
|
| [15] |
ZHOU Linxing, WANG Shuai. Research on the Triggering and Mitigating Mechanisms of Network Public Opinion in Major Emergencies under the Event Evolutionary Graph Model[J]. Library and Information Service, 2023, 67(12): 58-69.
doi: 10.13266/j.issn.0252-3116.2023.12.006 |
|
周林兴, 王帅. 事理图谱模型下的重大突发事件网络舆情诱发与缓释机理研究[J]. 图书情报工作, 2023, 67(12):58-69.
doi: 10.13266/j.issn.0252-3116.2023.12.006 |
|
| [16] | ZENG Ziming, LI Qingqing, SUN Shouqiang, et al. Construction of the Event Evolution Graph and Analysis of Evolutionary Situation of Network Public Opinion for Public Health Emergencies[J]. Information Studies: Theory & Application, 2023, 46(8): 147-155. |
| 曾子明, 李青青, 孙守强, 等. 面向突发公共卫生事件网络舆情的事理图谱构建及演化分析[J]. 情报理论与实践, 2023, 46(8):147-155. | |
| [17] | TIAN Yilin, LI Xing. Analysis on the Evolution Path of COVID-19 Network Public Opinion Based on the Event Evolutionary Graph[J]. Information Studies: Theory & Application, 2021, 44(3): 76-83. |
|
田依林, 李星. 基于事理图谱的新冠肺炎疫情网络舆情演化路径分析[J]. 情报理论与实践, 2021, 44(3):76-83.
doi: 10.16353/j.cnki.1000-7490.2021.03.011 |
|
| [18] | SUN Chuanming, CHEN Xi, WANG Ping. The Construction of Audience Needs Event Logic Graph of Intangible Cultural Heritage Documentary Based on Online Reviews[J]. Information Science, 2023, 41(9): 107-114. |
| 孙传明, 陈熙, 王萍. 基于在线评论的非遗纪录片受众需求事理图谱构建研究[J]. 情报科学, 2023, 41(9):107-114. | |
| [19] |
DENG Jianfeng, WANG Tao, CHENG Lianglun. Research on Construction of Event Logic Knowledge Graph of Robot Fault Diagnosis[J]. Computer Engineering and Applications, 2023, 59(13): 139-148.
doi: 10.3778/j.issn.1002-8331.2203-0398 |
|
邓健峰, 王涛, 程良伦. 机器人故障诊断事理逻辑知识图谱构建研究[J]. 计算机工程与应用, 2023, 59(13):139-148.
doi: 10.3778/j.issn.1002-8331.2203-0398 |
|
| [20] | XIANG Jing, LIU Yalan. Analysis on the Mechanism of Psychological Control about the Telecommunications Fraud of “Pig Killing Plate”[J]. Journal of People’s Public Security University of China(Social Sciences Edition), 2021, 37(4): 1-10. |
| 向静, 刘亚岚. “杀猪盘”电信诈骗犯罪的心理控制机制剖析[J]. 中国人民公安大学学报(社会科学版), 2021, 37(4):1-10. | |
| [21] | ZHANG Yaowen, LUO Wenhua. On Characteristics of Victims in Telecommunication Network Frauds: Comparative Analysis Based on Data from Different Regions[J]. Journal of Shanxi Police College, 2023, 31(10): 80-87. |
| 张耀文, 罗文华. 电信网络诈骗受害人特征研究——基于不同地区数据对比分析[J]. 山西警察学院学报, 2023, 31(10):80-87. | |
| [22] | WU Hequn, WANG Qiang, ZHENG Ziwan. Spatial Characteristics and Influencing Factors of the Origin of Telecommunication Network Fraud Criminals[J]. Geographical Research, 2023, 42(12): 3219-3234. |
|
吴鹤群, 王强, 郑滋椀. 电信网络诈骗犯罪人来源地的空间分布特征及影响因素[J]. 地理研究, 2023, 42(12):3219-3234.
doi: 10.11821/dlyj020230154 |
|
| [23] | LIU Xinyue, FAN Chaoyun, LI Hui. Characteristics and Preventive Countermeasures of Telecom and Network Fraud Victims[J]. The Journal of Yunnan Police College, 2022(4): 111-122. |
| 刘鑫悦, 范超云, 李辉. 电信网络诈骗被害人群体特征及防范对策[J]. 云南警官学院学报, 2022(4):111-122. | |
| [24] | CHEN Shyh-wei, CHEN Po-hsiang, TSAI Ching-tsorng, et al. Development of Machine Learning Based Fraudulent Website Detection Scheme[C]// IEEE. 2022 IEEE 5th International Conference on Knowledge Innovation and Invention (ICKII). New York: IEEE, 2022: 108-110. |
| [25] | ZHANG Penghui, OEST A, CHO H, et al. Crawlphish: Large-Scale Analysis of Client-Side Cloaking Techniques in Phishing[C]// IEEE. 2021 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2021: 1109-1124. |
| [26] | JIANG Yan, LIU Guannan, WU Junjie, et al. Telecom Fraud Detection via Hawkes-Enhanced Sequence Model[J]. IEEE Transactions on Knowledge and Data Engineering, 2022, 35(5): 5311-5324. |
| [27] | PRIYA G J, SARADHA S. Fraud Detection and Prevention Using Machine Learning Algorithms: A Review[C]// IEEE. 2021 7th International Conference on Electrical Energy Systems (ICEES). New York: IEEE, 2021: 564-568. |
| [28] | CHE Wanxiang, FENG Yunlong, QIN Libo, et al. N-LTP: An Open-Source Neural Language Technology Platform for Chinese[C]// ACL. Proceedings of the 2021 Conference on Empirical Methods in Natural Language Processing. New York: ACL, 2021: 42-49. |
| [29] | CHANG Chao, TANG Yong, LONG Yongxu, et al. Multi-Information Preprocessing Event Extraction with BiLSTM-CRF Attention for Academic Knowledge Graph Construction[J]. IEEE Transactions on Computational Social Systems, 2022, 10(5): 2713-2724. |
| [1] | JIA Fan, KANG Shuya, JIANG Weiqiang, WANG Guangtao. Vulnerability Similarity Algorithm Evaluation Based on NLP and Feature Fusion [J]. Netinfo Security, 2023, 23(1): 18-27. |
| [2] | LUO Wenhua, ZHANG Yaowen. Analysis on Characteristics of Victims of Telecom Network Fraud Based on Bayesian Network [J]. Netinfo Security, 2021, 21(12): 25-30. |
| [3] | TONG Xin, WANG Luona, WANG Runzheng, WANG Jingya. A Generation Method of Word-level Adversarial Samples for Chinese Text Classification [J]. Netinfo Security, 2020, 20(9): 12-16. |
| [4] | Wenjiang HAO, Liping XU, Jinlei JIANG, Cuicui LI. Research on Control Technology of Telecom Network Fraud Crime [J]. Netinfo Security, 2016, 16(9): 213-217. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||