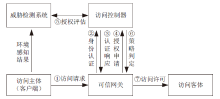
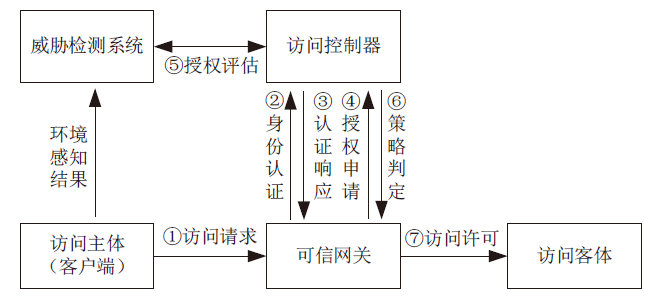
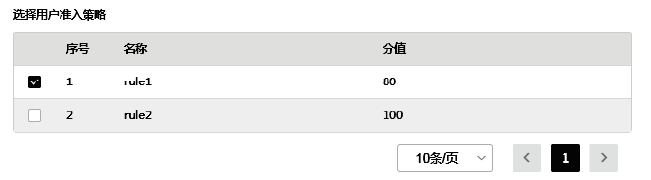
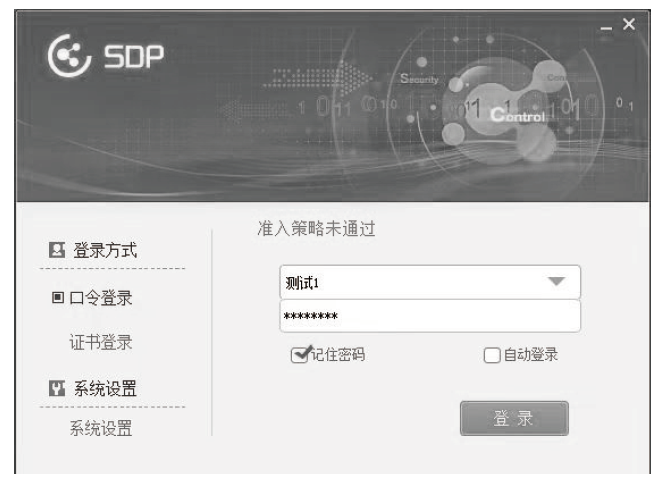
| [1] |
JOHN K. Build Security into Your Network's DNA: The Zero Trust Network Architecture[EB/OL]. (2010-11-05) [2022-03-17]. http://www.virtualstarmedia.com/downloads/Forrester_zero_trust_DNA.pdf.
|
| [2] |
WARD R, BEYER B. Beyondcorp: A New Approach to Enterprise Security[J]. Login the Magazine of USENIX&Sage, 2014, 39(6): 6-11.
|
| [3] |
Software Defined Perimeter Working Group. SDP Specification 1.0[EB/OL]. (2014-04-30) [2022-03-17]. https://downloads.cloudsecurityalliance.org/initiatives/sdp/SDP_Specification_1.0.pdf.
|
| [4] |
GAEHTGENS F, MACDONALD N. Use a CARTA Strategic Approach to Embrace Digital Business Opportunities in an Era of Advanced Threats[R]. Stamford: Gartner, G00332400, 2017.
|
| [5] |
ROSE S, BORCHERT O, MITCHELL S, et al. Zero Trust Architecture[R]. Gaithersburg: National Institute of Standards and Technology Special Publication, NIST.SP.800-207-draft2, 2020.
|
| [6] |
Tencent Security. Zero Trust Solution White Paper[EB/OL]. (2020-05-29) [2022-03-17]. https://cloud.tencent.com/developer/article/1636407.
|
|
腾讯安全. 零信任解决方案白皮书[EB/OL]. (2020-05-29) [2022-03-17]. https://cloud.tencent.com/developer/article/1636407.
|
| [7] |
LIU Yuan, SUN Chen, ZHANG Yanling. A Zero Trust Network Research Based on Overlay Technology[J]. Netinfo Security, 2020, 20(10): 83-91.
|
|
刘远, 孙晨, 张嫣玲. 基于Overlay技术的零信任网络研究[J]. 信息网络安全, 2020, 20(10): 83-91.
|
| [8] |
SONG Yufei, ZHOU Wenhui, LIU Jiandong, et al. Research on Satellite Internet Security Protection Based on Zero Trust[J]. Space-Integrated-Ground Information Networks, 2021, 2(3): 15-23.
|
|
宋宇飞, 周文辉, 刘建东, 等. 基于零信任的卫星互联网安全防护研究[J]. 天地一体化信息网络, 2021, 2(3):15-23.
|
| [9] |
WU Kehe, CHENG Rui, JIANG Xiaochen, et al. Security Protection Scheme of Power IoT Based on SDP[J]. Netinfo Security, 2022, 22(2): 32-38.
|
|
吴克河, 程瑞, 姜啸晨, 等. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2):32-38.
|
| [10] |
LIU Tao, MA Yue, JIANG Hefang, et al. Research on Grid Security Protection Architecture Based on Zero Trust[J]. Electric Power Information and Communication Technology, 2021, 19(7): 25-32.
|
|
刘涛, 马越, 姜和芳, 等. 基于零信任的电网安全防护架构研究[J]. 电力信息与通信技术, 2021, 19(7):25-32.
|
| [11] |
HUANG Lanying, XIONG Zenggang, YE Conghuan. A Trust-Role Access Control Model for Cloud Computing[J]. Journal of Hubei Engineering University, 2016, 36(6): 57-61.
|
|
黄兰英, 熊曾刚, 叶从欢. 一种面向云计算的信任-角色访问控制模型[J]. 湖北工程学院学报, 2016, 36(6):57-61.
|
| [12] |
YU Bo, TAI Xianqing, MA Zhijie. Study on Attribute and Trust-Based RBAC Model in Cloud Computing[J]. Computer Engineering and Applications, 2020, 56(9): 84-92.
|
|
余波, 台宪青, 马治杰. 云计算环境下基于属性和信任的RBAC模型研究[J]. 计算机工程与应用, 2020, 56(9):84-92.
|
| [13] |
LI Xin. Access Control Strategy Based on Trust under Cloud Computing Platform[C]// IEEE. 2018 International Conference on Virtual Reality and Intelligent Systems (ICVRIS). New York:IEEE, 2018: 327-330.
|
| [14] |
ZHAO Zhiyuan, SUN Lei. Attribute-Based Access Control with Dynamic Trust in a Hybrid Cloud Computing Environment[C]// IEEE. Proceedings of the 2017 International Conference on Cryptography, Security and Privacy. New York: IEEE, 2017: 112-118.
|
| [15] |
WU Yunkun, JIANG Bo, PAN Ruixuan, et al. A SDN Access Control Mechanism Based on Zero Trust[J]. Netinfo Security, 2020, 20(8): 37-46.
|
|
吴云坤, 姜博, 潘瑞萱, 等. 一种基于零信任的SDN网络访问控制方法[J]. 信息网络安全, 2020, 20(8): 37-46.
|
 )
)