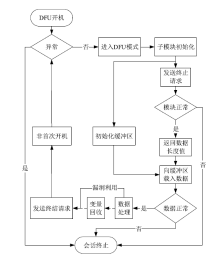
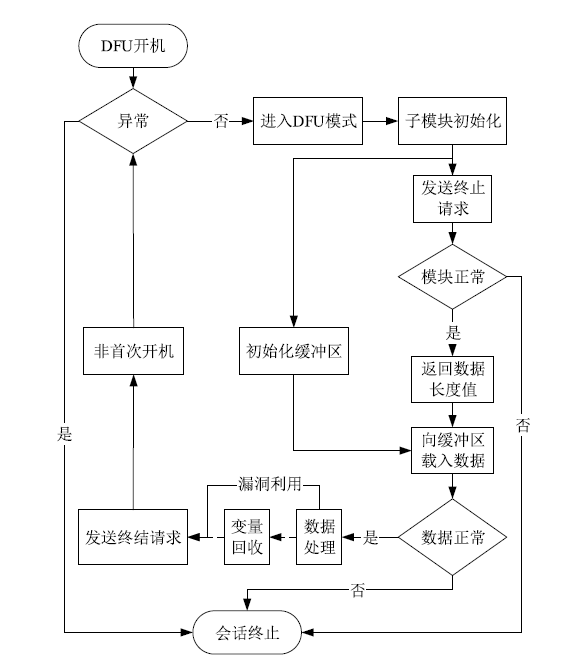
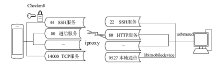
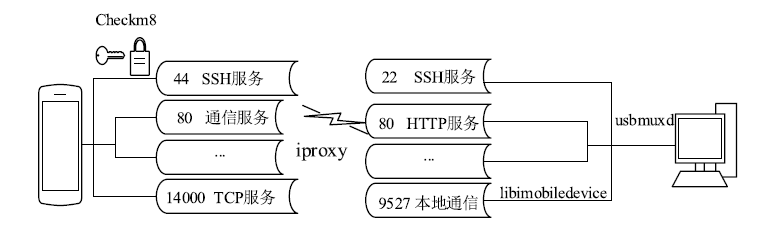
| [1] |
SPAULDING J, KRAUSS A, SRINIVASAN A. Exploring an Open WiFi Detection Vulnerability as A Malware Attack Vector on iOS Devices[C]// IEEE. 7th International Conference on Malicious and Unwanted Software, October 16-18, 2012, Fajardo, PR, USA. New Jersey: IEEE, 2012: 87-93.
|
| [2] |
CHRISTIAN C J D, CHOO K, YANG L Y. Data Exfiltration from Internet of Things Devices: IOS Devices as Case Studies[J]. IEEE Internet of Things Journal, 2016, 4(2):524-535.
doi: 10.1109/JIOT.2016.2569094
URL
|
| [3] |
CHRISTIAN D O, CHOO K. A Generic Process to Identify Vulnerabilities and Design Weaknesses in iOS Healthcare Apps[C]// IEEE. 48th Annual Hawaii International Conference on System Sciences(HICSS), January 5-8, 2015, Kauai, Hawaii State, USA. New Jersey: IEEE, 2015: 5175-5184.
|
| [4] |
LIN Chunhan, YU Fang, JIANG J H R, et al. Static Detection of API Call Vulnerabilities in iOS Executables[C]// IEEE. 40th ACM/IEEE International Conference on Software Engineering(ICSE), May 27-June 3, 2018, Gothenburg, Sweden. New Jersey: IEEE, 2018: 394-395.
|
| [5] |
Sxi0mx. EPIC JAILBREAK: Introducing Checkm8[EB/OL]. https://twitter.com/axi0mX/status/1177542201670168576, 2019-09-28.
|
| [6] |
TAMMA R, MAHALIK H, SKULKIN O, et al. Practical Mobile Forensics: A Hands-on Guide to Mastering Mobile Forensics for the iOS, Android, and Windows Phone platforms[M]. Birmingham: Packt Publishing, 2018.
|
| [7] |
Apple. Glossary[EB/OL]. https://support.apple.com/en-gb/guide/security/sec93292bfa6/web, 2021-09-14.
|
| [8] |
GARG S, BALIYAN N. Comparative Analysis of Android and iOS from Security Viewpoint[EB/OL]. https://doi.org/10.1016/j.cosrev.2021.100372, 2021-08-11.
|
| [9] |
GUNNAR A, STEFAN A, GEIR O D. Chip Chop-smashing the Mobile Phone Secure Chip for Fun and Digital Forensics[EB/OL]. https://doi.org/10.1016/j.fsidi.2021.301191, 2021-04-14.
|
| [10] |
IEEE. 1619-2007-IEEE Standard for Cryptographic Protection of Data on Block-Oriented Storage Devices[EB/OL]. https://ieeexplore.ieee.org/document/4493450, 2008-03-04.
|
| [11] |
DING Liping, LIU Xuehua, CHEN Guangxuan, et al. Overview of Digital Forensics Technologies of RAM in Android Devices[J]. Netinfo Security, 2019, 19(2):10-17.
|
|
丁丽萍, 刘雪花, 陈光宣, 等. Android 智能手机动态内存取证技术综述[J]. 信息网络安全, 2019, 19(2):10-17.
|
| [12] |
KIPERBERG M, LEON R, RESH A, et al. Hypervisor-assisted Atomic Memory Acquisition in Modern Systems[C]// IEEE. 5th International Conference on Information Systems Security and Privacy(ICISSP), February 23-25, 2019, Prague, Czech Republic. New Jersey: IEEE, 2019: 155-162.
|
| [13] |
LIU Pengfei. The Analyses and Prevention of Attact Methods of iOS Applications[D]. Chengdu: University of Electronic Science and Technology of China, 2014.
|
|
刘朋飞. iOS应用程序的攻击手段分析及防护[D]. 成都:电子科技大学, 2014.
|
| [14] |
XU Xin, ZHANG Songnian, HU Jianwei. Research on ASLR Bypass Technology Based on Arbitrary Function Address[J]. Netinfo Securtiy, 2016, 16(7):47-52.
|
|
徐鑫, 张松年, 胡建伟. 基于任意函数地址的ASLR绕过技术研究[J]. 信息网络安全, 2016, 16(7):47-52.
|
| [15] |
GAO Qiang. A First Look at the Encryption Techniques Commonly Used in iOS Development[J]. Computer Knowledge and Technology, 2021, 17(10):51-53.
|
|
高强. iOS开发过程中常用的加密技术初探[J]. 电脑知识与技术, 2021, 17(10):51-53.
|
| [16] |
DEMPSEY P. The Teardown-apple iPhone X[J]. Engineering & Technology, 2018, 1(13):80-81.
|
| [17] |
KO H J, HUANG Chengta, ZHUANG Zhiwei. et al. Cloud Evidence Tracks of Storage Service Linking with iOS Systems[J]. Journal of Supercomputing, 2021, 77(1):77-94.
doi: 10.1007/s11227-020-03255-5
URL
|
| [18] |
LIU Feng, LIU Kesheng, CHANG Chao, et al. Research on the Technology of iOS Jailbreak[C]// IEEE. 6th International Conference on Instrumentation and Measurement, Computer, Communication and Control(IMCCC), July 21-23, 2016, Harbin, China. New Jersey: IEEE, 2016: 644-647.
|
 ), CAO Danni1, XIE Qingquan2
), CAO Danni1, XIE Qingquan2