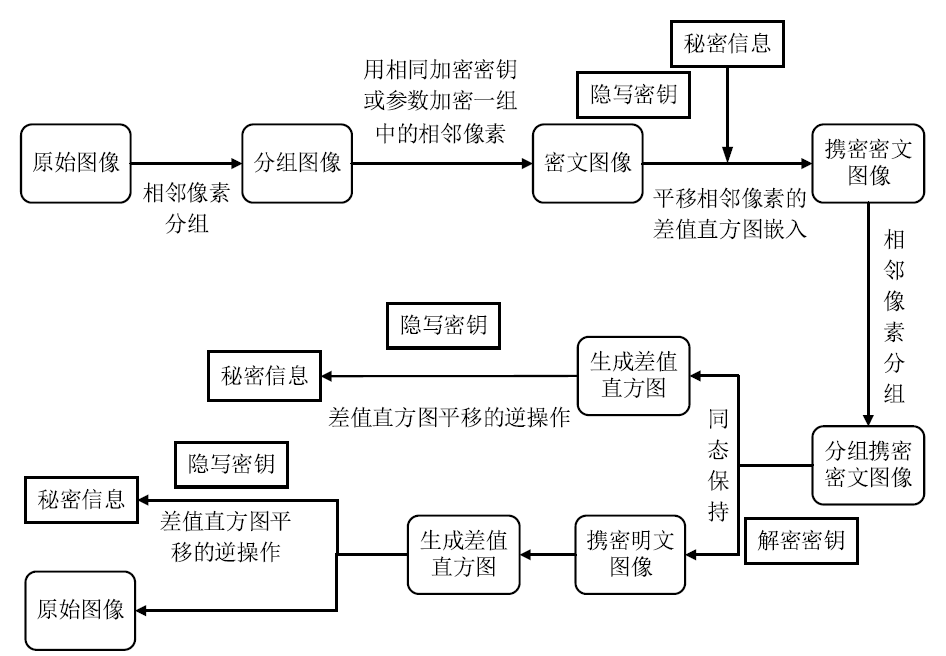
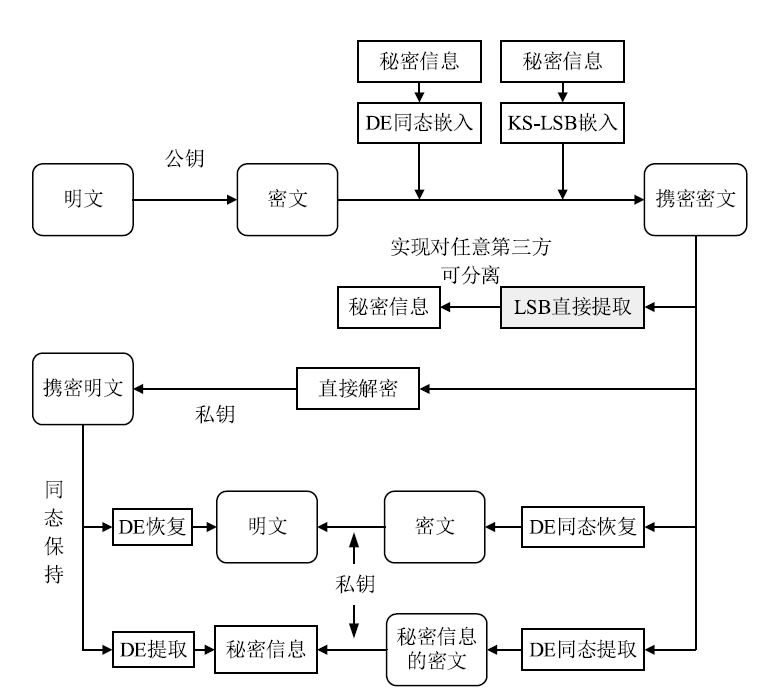
Netinfo Security ›› 2020, Vol. 20 ›› Issue (8): 25-36.doi: 10.3969/j.issn.1671-1122.2020.08.004
Previous Articles Next Articles
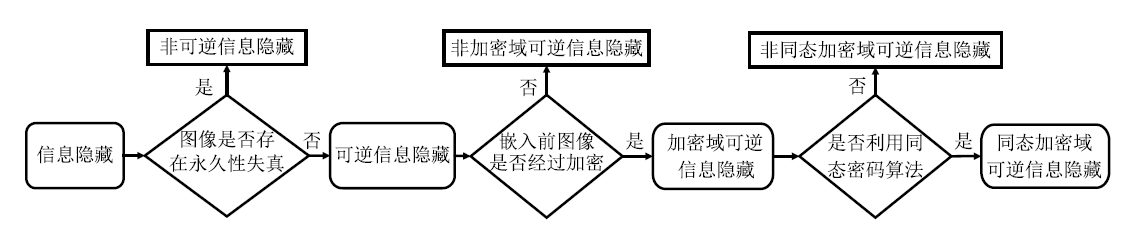
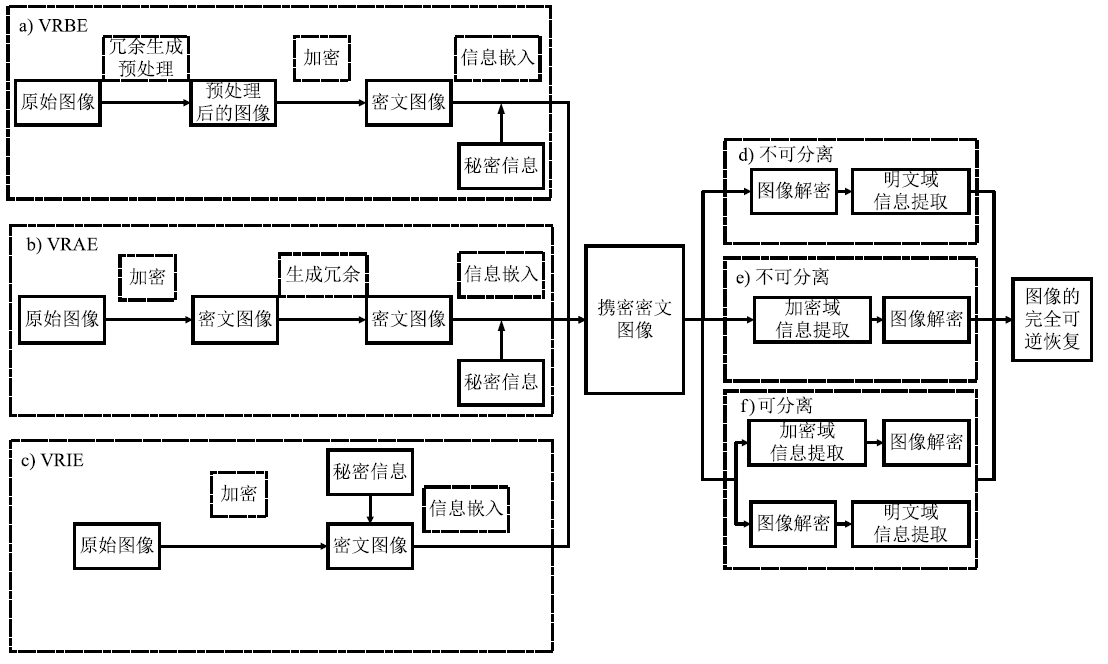
Research on Reversible Data Hiding Technology in Homomorphic Encrypted Domain
ZHANG Minqing1,2( ), ZHOU Neng1,2, LIU Mengmeng1,2, KE Yan1,2
), ZHOU Neng1,2, LIU Mengmeng1,2, KE Yan1,2
- 1. Key Laboratory of Network and Information Security under Chinese People Armed Police Force (PAP), Xi’an 710086, China
2. College of Cryptography Engineering, Engineering University of PAP, Xi’an 710086, China
-
Received:2020-06-10Online:2020-08-10Published:2020-10-20 -
Contact:ZHANG Minqing E-mail:api_zmq@126.com
CLC Number:
Cite this article
ZHANG Minqing, ZHOU Neng, LIU Mengmeng, KE Yan. Research on Reversible Data Hiding Technology in Homomorphic Encrypted Domain[J]. Netinfo Security, 2020, 20(8): 25-36.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.08.004
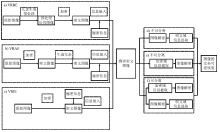
| 算法 | 根据冗余的不同来源进行分类 | 可分离 | 同态密码体制 |
|---|---|---|---|
| 文献[ | VRBE | 否 | Paillier |
| 文献[ | Paillier | ||
| 文献[ | Paillier | ||
| 文献[ | 多秘密共享 | ||
| 文献[ | 秘密共享 | ||
| 文献[ | NTRU | ||
| 文献[ | 是 | Paillier | |
| 文献[ | Paillier | ||
| 文献[ | Paillier | ||
| 文献[ | Paillier | ||
| 文献[ | Paillier | ||
| 文献[ | Paillier | ||
| 文献[ | EC-EG | ||
| 文献[ | 多秘密共享 | ||
| 文献[ | VRAE | 否 | Paillier |
| 文献[ | Paillier | ||
| 文献[ | 秘密共享 | ||
| 文献[ | 是 | RC4 | |
| 文献[ | RC4 | ||
| 文献[ | RC4 | ||
| 文献[ | RC4 | ||
| 文献[ | RC4 | ||
| 文献[ | Paillier | ||
| 文献[ | DGHV | ||
| 文献[ | 基于R-LWE的SHE | ||
| 文献[ | Paillier | ||
| 文献[ | Paillier | ||
| 文献[ | NTRU | ||
| 文献[ | VRIE | 是 | LWE |
| 文献[ | R-LWE | ||
| 文献[ | LWE | ||
| 文献[ | LWE | ||
| 文献[ | R-LWE | ||
| 文献[ | LWE | ||
| 文献[ | 基于LWE的FHE |
| [1] |
WU M, LIU B. Data Hiding in Image and Video: Part I—Fundamental Issues and Solutions[J]. IEEE Transactions on Image Processing, 2003,12(6):685-695.
doi: 10.1109/TIP.2003.810588 URL pmid: 18237944 |
| [2] |
WU M, YU H, LIU B. Data Hiding in Image and Video: Part II—Designs and Applications[J]. IEEE Transactions on Image Processing, 2003,12(6):696-705.
doi: 10.1109/TIP.2003.810589 URL pmid: 18237945 |
| [3] |
SHARIFZADEH M, ALORAINI M, SCHONFELD D. Adaptive Batch Size Image Merging Steganography and Quantized Gaussian Image Steganography[J]. IEEE Transactions on Information Forensics and Security, 2020,15(7):867-879.
doi: 10.1109/TIFS.10206 URL |
| [4] |
FANG H, ZHANG W M, ZHOU H, et al. Screen-Shooting Resilient Watermarking[J]. IEEE Transactions on Information Forensics and Security, 2019,14(6):1403-1418.
doi: 10.1109/TIFS.2018.2878541 URL |
| [5] | BARTON J M. Method and Apparatus for Embedding Authentication Information within Digital Data[P]. U.S. Patent 5646997. 1997. |
| [6] | FRIDRICH J, GOLJAN M, DU R. Lossless Data Embedding-New Paradigm in Digital Watermarking[J]. EURASIP Journal on Applied Signal Processing, 2002,2002(2):185-196. |
| [7] |
CELIK M U, SHARMA G, TEKALP A M, et al. Lossless Generalized-LSB Data Embedding[J]. IEEE Transactions on Image Processing, 2005,14(2):253-266.
doi: 10.1109/tip.2004.840686 URL pmid: 15700530 |
| [8] | TIAN J. Reversible Data Embedding Using a Difference Expansion[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2003,13(8):890-896. |
| [9] |
THODI D M, RODRIGUEZ J J. Expansion Embedding Techniques for Reversible Watermarking[J]. IEEE Transactions on Image Processing, 2007,16(3):721-730.
doi: 10.1109/tip.2006.891046 URL pmid: 17357732 |
| [10] | NI Z C, SHI Y Q, ANSARI N, et al. Reversible Data Hiding[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2006,16(3):354-362. |
| [11] | JIA Y J, YIN Z X, ZHANG X P. Reversible Data Hiding Based on Reducing Invalid Shifting of Pixels in Histogram Shifting[J]. Signal Processing, 2019,163(10):238-246. |
| [12] | THODI D M, RODRÍGUEZ J. Prediction-Error Based Reversible Watermarking[C]// IEEE. Proceedings of International Conference on Image Processing, October 24-27, 2004, Singapore. New York: IEEE, 2004: 1549-1552. |
| [13] | CHEN H, NI J, HONG W, et al. High-Fidelity Reversible Data Hiding Using Directionally Enclosed Prediction[J]. IEEE Signal Processing Letters, 2017,24(5):574-578. |
| [14] | XIANG Yudong, WU Guixing. An Image Reversible Data Hiding Strategy Based on Pixel Prediction[J]. Computer Science, 2018,45(2):189-196. |
| 项煜东, 吴桂兴. 一种基于像素预测的图像可逆信息隐藏策略[J]. 计算机科学, 2018,45(2):189-196. | |
| [15] | KIM S, QU X, SACHNEV V, et al. Skewed Histogram Shifting for Reversible Data Hiding Using a Pair of Extreme Predictions[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2019,29(11):3236-3246. |
| [16] | PUECH W, CHAUMONT M, STRAUSS O, A Reversible Data Hiding Method for Encrypted Images[EB/OL]. https://www.researchgate.net/publication/29633573_A_Reversible_Data_Hiding_Method_for_Encrypted_Images?enrichId=rgreq-475996a69b97c05479c8471136da9bd5-XXX& enrichSource=Y292ZXJQYWdlOzI5NjMzNTczO0FTO jEwMTI2MDg3MTA3Nzg5MEAxNDAxMTUzODgxMDU3&el=1_x_2&_esc=publicationCoverPdf, 2020-3-15. |
| [17] | ZHANG X P. Reversible Data Hiding in Encrypted Image[J]. IEEE Signal Processing Letters, 2011,18(4):255-258. |
| [18] | HONG W, CHEN T S, WU H Y. An Improved Reversible Data Hiding in Encrypted Images Using Side Match[J]. IEEE Signal Processing Letters, 2012,19(4):199-202. |
| [19] | HONG W, CHEN T S, CHEN J, et al. Reversible Data Embedment for Encrypted Cartoon Images Using Unbalanced Bit Flipping[J]. Lecture Notes in Computer Science, 2013,29(3):208-214. |
| [20] |
ZHANG X P. Separable Reversible Data Hiding in Encrypted Image[J]. IEEE Transactions on Information Forensics and Security, 2012,7(2):826-832.
doi: 10.1109/TIFS.2011.2176120 URL |
| [21] |
MA K D, ZHANG W M, ZHAO X F, et al. Reversible Data Hiding in Encrypted Images by Reserving Room before Encryption[J]. IEEE Transactions on Information Forensics and Security, 2013,8(3):553-562.
doi: 10.1109/TIFS.2013.2248725 URL |
| [22] |
ZHANG W M, MA K D, YU N H. Reversibility Improved Data Hiding in Encrypted Images[J]. Signal Processing, 2014,94(1):118-127.
doi: 10.1016/j.sigpro.2013.06.023 URL |
| [23] |
QIAN Z X, ZHANG X P, WANG S. Reversible Data Hiding in Encrypted JPEC Bitstream[J]. IEEE Transactions on Multimedia, 2014,16(5):1486-1491.
doi: 10.1109/TMM.2014.2316154 URL |
| [24] | YIN Z X, NIU X J, ZHANG X P, et al. Reversible Data Hiding in Encrypted AMBTC Images[J]. Multimedia Tools and Applications, 2018,77(14):18067-18083. |
| [25] | DILEEP A, ANUSUDHA K, MUHAMMED ASAD P T. An Efficient Reversible Data Hiding Technique in Encrypted Images Based on Chaotic Map[C]// IEEE. International Conference on Control, Instrumentation, Communication and Computational Technologies, December 18-19, 2015, Kumaracoil, India. New York: IEEE, 2015: 539-543. |
| [26] | KADAM P, KANDHARE A, NAWALE M, et al. Separable Reversible Encrypted Data Hiding in Encrypted Image Using AES Algorithm and Lossy Technique[C]// IEEE. International Conference on Pattern Recognition, Informatics and Mobile Engineering, February 21-22, 2013, Salem, India. New York: IEEE, 2013: 312-316. |
| [27] | WU X T, SUN W. High-Capacity Reversible Data Hiding in Encrypted Images by Prediction Error[J]. Signal Processing, 2014,104(11):387-400. |
| [28] | PUTEAUX P, PUECH W. An Efficient MSB Prediction-Based Method for High-Capacity Reversible Data Hiding in Encrypted Images[J]. IEEE Transactions on Information Forensics and Security, 2018,13(7):1670-1681. |
| [29] | DRAGOI I C, COLTUC D. Reversible Data Hiding in Encrypted Images Based on Reserving Room After Encryption and Multiple Predictors[C]// IEEE. International Conference on Acoustics, Speech and Signal Processing, April 15-20, 2018, Calgary, AB, Canada. New York: IEEE, 2018: 2102-2105. |
| [30] | QIN C, QIAN X K, HONG W, et al. An Efficient Coding Scheme for Reversible Data Hiding in Encrypted Image with Redundancy Transfer[J]. Information Sciences, 2019,487(6):176-192. |
| [31] | YI S, ZHOU Y. Separable and Reversible Data Hiding in Encrypted Images Using Parametric Binary Tree Labeling[J]. IEEE Transactions on Multimedia, 2019,21(1):51-64. |
| [32] | WU H, YANG Z, CHEUNG Y, et al. High-Capacity Reversible Data Hiding in Encrypted Images by Bit Plane Partition and MSB Prediction[J]. IEEE Access, 2019,7(5):62361-62371. |
| [33] | CHANG C, LI C, CHEN K. Privacy-Preserving Reversible Information Hiding Based on Arithmetic of Quadratic Residues[J]. IEEE Access, 2019,7(4):54117-54132. |
| [34] | YIN Z, XIANG Y, ZHANG X. Reversible Data Hiding in Encrypted Images Based on Multi-MSB Prediction and Huffman Coding[J]. IEEE Transactions on Multimedia, 2020,22(4):874-884. |
| [35] | RIVEST R L, ADLEMAN L, DERTOUZOS M L. On Data Banks and Privacy Homomorphisms[J]. Foundations of Secure Computation, 1978,32(4):169-178. |
| [36] | PAILLIER P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes[C]// Springer.International Conference on the Theory and Applications of Cryptographic Techniques, May 2-6, 1999, Prague, Czech Republic. Berlin: Springer, 1999: 223-238. |
| [37] | ELGAMAL T. A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms[J]. IEEE Transactions on Information Theory, 1985,31(4):469-472. |
| [38] | GENTRY C. Fully Homomorphic Encryption Using Ideal Lattices[C]// ACM. Proceedings of the 41st Annual ACM Symposium on Theory of Computing, May 10-12, 2009, NY, USA. New York: ACM, 2009: 169-178. |
| [39] | DIJK M V, GENTRY C, HALEVI S, et al. Fully Homomorphic Encryption over the Integers[C]// Springer. International Conference on Theory and Applications of Cryptographic Techniques, May 30- June 3, 2010, Monaco and Nice, France. Berlin: Springer, 2010: 24-43. |
| [40] | HOFFSTEIN J, PIPHER J, SILVERMAN J H. NTRU: A Ring-Based Public Key Cryptosystem[C]// Springer. Algorithmic Number Theory, June 21-25, 1998, Portland, OR, USA. Berlin: Springer, 1998: 267-288. |
| [41] |
SHI Y Q, LI X L, ZHANG X P, et al. Reversible Data Hiding: Advances in The Past Two Decades[J]. IEEE Access, 2016,4(5):3210-3237.
doi: 10.1109/ACCESS.2016.2573308 URL |
| [42] |
KE Yan, ZHANG Minqing, LIU Jia, et al. Overview on Reversible Data Hiding in Encrypted Domain[J]. Journal of Computer Applications, 2016,36(11):3067-3076.
doi: 10.11772/j.issn.1001-9081.2016.11.3067 URL |
|
柯彦, 张敏情, 刘佳, 等. 密文域可逆信息隐藏综述[J]. 计算机应用, 2016,36(11):3067-3076.
doi: 10.11772/j.issn.1001-9081.2016.11.3067 URL |
|
| [43] |
CHEN Y C, SHIU C W, HORNG G. Encrypted Signal-Based Reversible Data Hiding with Public Key Cryptosystem[J]. Journal of Visual Communication and Image Representation, 2014,25(5):1164-1170.
doi: 10.1016/j.jvcir.2014.04.003 URL |
| [44] |
SHIU C W, CHEN Y C, HONG W. Encrypted Image-Based Reversible Data Hiding with Public Key Cryptography from Difference Expansion[J]. Signal Processing: Image Communication, 2015,39(11):226-233.
doi: 10.1016/j.image.2015.09.014 URL |
| [45] |
WU X T, CHEN B, WENG J. Reversible Data Hiding for Encrypted Signals by Homomorphic Encryption and Signal Energy Transfer[J]. Journal of Visual Communication and Image Representation, 2016,41(11):58-64.
doi: 10.1016/j.jvcir.2016.09.005 URL |
| [46] |
CHEN Y C, HUNG T, HSIEH S, et al. A New Reversible Data Hiding in Encrypted Image Based on Multi-Secret Sharing and Lightweight Cryptographic Algorithms[J]. IEEE Transactions on Information Forensics and Security, 2019,14(12):3332-3343.
doi: 10.1109/TIFS.10206 URL |
| [47] |
ZHANG X P, LONG J, WANG Z C, et al. Lossless and Reversible Data Hiding in Encrypted Images with Public-Key Cryptography[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2016,26(9):1622-1631.
doi: 10.1109/TCSVT.2015.2433194 URL |
| [48] | XIANG Shijun, LUO Xinrong. Reversible Data Hiding in Encrypted Image Based on Homomorphic Public Key Cryptosystem[J]. Journal of Software, 2016,27(6):1592-1601. |
| 项世军, 罗欣荣. 同态公钥加密系统的图像可逆信息隐藏算法[J]. 软件学报, 2016,27(6):1592-1601. | |
| [49] | XIANG S J, LUO X R. Reversible Data Hiding in Homomorphic Encrypted Domain by Mirroring Ciphertext Group[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2018,28(11):3099-3110. |
| [50] | TAI W L; CHANG Y F. Separable Reversible Data Hiding in Encrypted Signals with Public Key Cryptography[J]. Symmetry, 2018,10(1):23. |
| [51] | WU H T, CHEUNG Y M, YANG Z Y, et al. A High-Capacity Reversible Data Hiding Method for Homomorphic Encrypted Images[J]. Journal of Visual Communication and Image Representation, 2019,62(5):87-96. |
| [52] | ZHANG Minqing, ZHOU Neng, LIU Mengmeng, et al. Reversible Data Hiding in Homomorphic Encrypted Domain Based on Paillier[J]. Journal of Shandong University (Natural Science), 2020,55(3):1-8. |
| 张敏情, 周能, 刘蒙蒙, 等. 基于Paillier的同态加密域可逆信息隐藏[J]. 山东大学学报(理学版), 2020,55(3):1-8. | |
| [53] | ZHOU N, ZHANG M Q, WANG H, et al. Reversible Data Hiding Scheme in Homomorphic Encrypted Image Based on EC-EG[EB/OL]. http://www.researchgate.net/publication/334607570 _Reversible_Data_Hiding_Scheme_in_Homomorphic_Encrypted_Image_Based_on_EC-EG, 2020-3-15. |
| [54] | ZHOU Neng, ZHANG Minqing, LIU Mengmeng. Reversible Data Hiding Algorithm in Homomorphic Encrypted Image Based on Secret Sharing[J]. Science Technology and Engineering, 2020,20(19):7780-7786. |
| 周能, 张敏情, 刘蒙蒙. 基于秘密共享的同态加密图像可逆信息隐藏算法[J]. 科学技术与工程, 2020,20(19):7780-7786. | |
| [55] | ZHOU Neng, ZHANG Minqing, LIN Wenbing. Separable Reversible Data Hiding in Encrypted Domain Based on Secret Sharing[J]. Computer Engineering, 2020,46(11):31-41. |
| 周能, 张敏情, 林文兵. 基于秘密共享的可分离密文域可逆信息隐藏[J]. 计算机工程, 2020,46(11):31-41. | |
| [56] | ZHOU Neng, ZHANG Minqing, TANG Hongqiong. Reversible Data Hiding Algorithm in Encrypted Domain Based on NTRU[J]. Science Technology and Engineering, 2020,20(32):12-18. |
| 周能, 张敏情, 唐洪琼. 基于NTRU的密文域可逆信息隐藏算法[J]. 科学技术与工程, 2020,20(32):12-18. | |
| [57] | LI M, LI Y. Histogram Shifting in Encrypted Images with Public Key Cryptosystem for Reversible Data Hiding[J]. Signal Processing, 2017,130(1):190-196. |
| [58] |
WU H T, CHEUNG Y M, HUANG J. Reversible Data Hiding in Paillier Cryptosystem[J]. Journal of Visual Communication and Image Representation, 2016,40(10):765-771.
doi: 10.1016/j.jvcir.2016.08.021 URL |
| [59] |
WU X T, WENG J, YAN W Q. Adopting Secret Sharing for Reversible Data Hiding in Encrypted Images[J], Signal Processing, 2018,143(2):269-281.
doi: 10.1016/j.sigpro.2017.09.017 URL |
| [60] |
LI M, XIAO D, ZHANG Y, et al. Reversible Data Hiding in Encrypted Images Using Cross Division and Additive Homomorphism[J]. Signal Processing Image Communication, 2015,39(1):234-248.
doi: 10.1016/j.image.2015.10.001 URL |
| [61] | XU D W, CHEN K, WANG R D, et al. Completely Separable Reversible Data Hiding in Encrypted Images[C]// Springer. International Workshop on Digital Watermarking, October 7-10, 2015, Tokyo, Japan. Berlin: Springer, 2016: 365-377. |
| [62] | XIAO Di, WANG Ying, CHANG Yanting, et al. Reversible Data Hiding in Encrypted Image Based on Additive Homomorphism and Multi-Level Difference Histogram Shifting[J]. Netinfo Security, 2016,16(4):9-16. |
| [63] | XIAO D, XIANG Y P, ZHENG H Y, et al. Separable Reversible Data Hiding in Encrypted Image Based on Pixel Value Ordering and Additive Homomorphism[J]. Journal of Visual Communication and Image Representation, 2017,45(5):1-10. |
| [64] | LI Zhijia, XIA Wei. Reversible Information Hiding Algorithm in Encrypted Domain Based on Difference Histogram Shifting[J]. Computer Engineering, 2019,45(11):152-158. |
| 李志佳, 夏玮. 基于差值直方图平移的密文域可逆信息隐藏算法[J]. 计算机工程, 2019,45(11):152-158. | |
| [65] | XIANG S J, LUO X R. Efficient Reversible Data Hiding in Encrypted Image with Public Key Cryptosystem[J]. EURASIP Journal on Signal Processing in Signal Processing, 2017,2017(1):59. |
| [66] | LI J, LIANG X, DAI C, et al. Reversible Data Hiding Algorithm in Fully Homomorphic Encrypted Domain[J]. Entropy. 2019,21(7):625. |
| [67] | XIONG L Z, DONG D P, XIA Z H, et al. High-Capacity Reversible Data Hiding for Encrypted Multimedia Data with Somewhat Homomorphic Encryption[J]. IEEE Access, 2018,6(10):60635-60644. |
| [68] | WU H T, CHEUNG Y M, ZHUANG Z W, et al. Reversible Data Hiding in Homomorphic Encrypted Images without Preprocessing[EB/OL]. https://www.semanticscholar.org/paper/Reversible-Data-Hiding-in-Homomorphic-Encrypted-Wu-Cheung/1ef843b4c643a8e53fd56dfe19dc30da7707ea28, 2020-3-15. |
| [69] | KHAN A N, FAN M Y, NAZEER M I, et al. An Efficient Separable Reversible Data Hiding Using Paillier Cryptosystem for Preserving Privacy in Cloud Domain[J]. Electronics, 2019,8(6):682. |
| [70] | ZHOU N, ZHANG M Q, WANG H, et al. Separable Reversible Data Hiding Scheme in Homomorphic Encrypted Domain Based on NTRU[J]. IEEE Access, 2020,8(1):81412-81424. |
| [71] | ZHANG Minqing, KE Yan, SU Tingting. Reversible Steganography in Encrypted Domain Based on LWE[J]. Journal of Electronics and Information Technology, 2016,38(2):354-360. |
|
张敏情, 柯彦, 苏婷婷. 基于LWE的密文域可逆信息隐藏[J]. 电子与信息学报, 2016,38(2):354-360.
doi: 10.11999/JEIT150702 URL |
|
| [72] | KE Yan, ZHANG Minqing, SU Tingting. A Novel Multiple Bits Reversible Data Hiding in Encrypted Domain Based on R-LWE[J]. Journal of Computer Research and Development, 2016,53(10):2307-2322. |
| 柯彦, 张敏情, 苏婷婷. 基于R-LWE的密文域多比特可逆信息隐藏算法[J]. 计算机研究与发展, 2016,53(10):2307-2322. | |
| [73] | KE Yan, ZHANG Minqing, ZHANG Yingnan. Separable Reversible Steganography in Encrypted Domain[J]. Application Research of Computers, 2016,33(11):3476-3479. |
| 柯彦, 张敏情, 张英男. 可分离的密文域可逆信息隐藏[J]. 计算机应用研究, 2016,33(11):3476-3479. | |
| [74] | KE Yan, ZHANG Minqing, XIANG Wen. Separable Reversible Quaternary Data Hiding Algorithm in Encrypted Domain[J]. Science Technology and Engineering, 2016,16(27):58-64. |
| 柯彦, 张敏情, 项文. 加密域的可分离四进制可逆信息隐藏算法[J]. 科学技术与工程, 2016,16(27):58-64. | |
| [75] | KE Yan, ZHANG Minqing, LIU Jia. Separable Reversible Hexadecimal Data Hiding Algorithm in Encrypted Domain[J]. Journal of Computer Applications, 2016,36(11):3082-3087. |
| 柯彦, 张敏情, 刘佳. 可分离的加密域十六进制可逆信息隐藏[J]. 计算机应用, 2016,36(11):3082-3087. | |
| [76] | KE Y, ZHANG M Q, LIU J, et al. A Multilevel Reversible Data Hiding Scheme in Encrypted Domain Based on LWE[J]. Journal of Visual Communication & Image Representation, 2018,54(7):133-144. |
| [77] | KE Y, LIU J, ZHANG M Q, et al. Fully Homomorphic Encryption Encapsulated Difference Expansion for Reversible Data hiding in Encrypted Domain[EB/OL]. https://ieeexplore.ieee.org/document/8947953, 2020-3-15. |
| [78] | SHANNON C E. A Mathematical Theory of Communication[J]. Bell Labs Technical Journal, 1948,27(4):379-423. |
| [79] | CHEN Jiayong, WANG Chao, ZHANG Weiming, et al. A Secure Image Steganographic Method in Encrypted Domain[J]. Journal of Electronics & Information Technology, 2012,34(7):1721-1726. |
| 陈嘉勇, 王超, 张卫明, 等. 安全的密文域图像隐写术[J]. 电子与信息学报, 2012,34(7):1721-1726. |
| [1] | Hongqiong TANG, Ke NIU, Yingnan ZHANG, Xiaoyuan YANG. Reversible Data Hiding in Videos Based on Adaptive Two-dimensional Histogram Modification [J]. Netinfo Security, 2019, 19(9): 106-110. |
| [2] | Yihua ZHOU, Zhuqing LV, Yuguang YANG, Weimin SHI. Data Deposit Management System Based on Blockchain Technology [J]. Netinfo Security, 2019, 19(8): 8-14. |
| [3] | Lin LI, Xuxia ZHANG. National Secret Substitution of zk-snark Bilinear Pair [J]. Netinfo Security, 2019, 19(10): 10-15. |
| [4] | Bo OU, Xianglian SHI. Reversible Data Hiding for Three-dimensional Image Based on Depth No-synthesis-error Model [J]. Netinfo Security, 2018, 18(5): 24-31. |
| [5] | Yan CHEN, Jianyong GE, Jing LAI, Zhen LU. Security System of the Information System in the Cloud [J]. Netinfo Security, 2018, 18(4): 79-86. |
| [6] | Congdong LV, Zhen HAN. A Security Model of Cloud Computing Based on IP Model [J]. Netinfo Security, 2018, 18(11): 27-32. |
| [7] | Baoyuan KANG, Jiaqiang WANG, Dongyang SHAO, Chunqing LI. A Secure Authentication and Key Agreement Protocol for Heterogeneous Ad Hoc Wireless Sensor Networks [J]. Netinfo Security, 2018, 18(1): 23-30. |
| [8] | Chunhua GU, Yuan GAO, Xiuxia TIAN. Security Optimized RBAC Access Control Model [J]. Netinfo Security, 2017, 17(5): 74-79. |
| [9] | Zhong LIANG, Jiakun ZHOU, Han ZHU, Bo CHEN. Research on Aggregation Technology for Information Security Knowledge Based on Security Ontology [J]. Netinfo Security, 2017, 17(4): 78-85. |
| [10] | Jingzhe ZHOU, Changsong CHEN. Analysis of Network Information Security in the Cloud Computing Architecture [J]. Netinfo Security, 2017, 17(11): 74-79. |
| [11] | Qi SU, Wei WANG, Yin LIU, Zhanpeng YU. Research on the Scheme of Information Security Protection in Electric Power Industry [J]. Netinfo Security, 2017, 17(11): 84-88. |
| [12] | Nana HUANG, Liang WAN, Xuankun DENG, Huifan YI. A Cross Site Script Vulnerability Detection Technology Based on Sequential Minimum Optimization Algorithm [J]. Netinfo Security, 2017, 17(10): 55-62. |
| [13] | Lei ZHANG, Dongsheng YU, Jun YANG, Jiming HU. Research on Information Security Supervision Strategy Based on Private Cloud Model [J]. Netinfo Security, 2017, 17(10): 86-89. |
| [14] | Yubin WANG, Si CHEN, Nan CHENG. Research on Industrial Control System Security Defense [J]. Netinfo Security, 2016, 16(9): 35-39. |
| [15] | Xin FU, Yuhua LU, Zijian SHAO. Research on Information Security Simulation Experimental Platform of Public Security Video Monitoring System [J]. Netinfo Security, 2016, 16(9): 56-59. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||