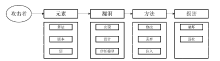
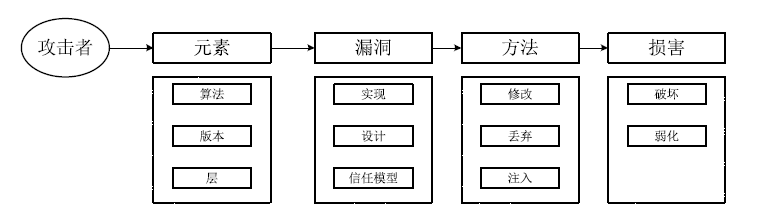
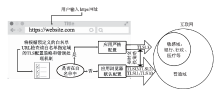
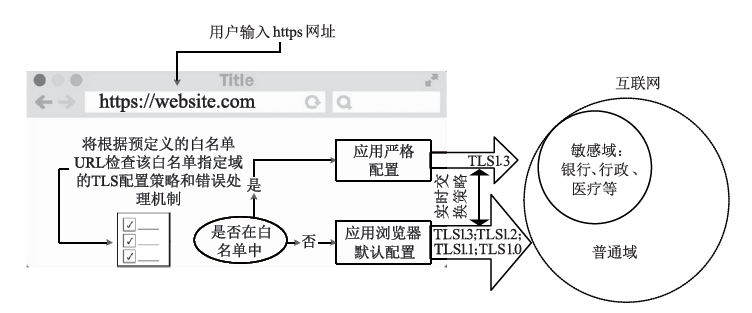
| [1] |
MÖLLER B, DUONG T, KOTOWICZ K. This POODLE Bites: Exploiting the SSL 3.0 Fallback[EB/OL]. , 2014-9-1.
|
| [2] |
BEURDOUCHE B, DELIGNAT L A, KOBEISSI N, et al.FLEXTLS: A Tool for Testing TLS Implementations[C]//USENIX. 9th USENIX Workshop on Offensive Technologies(WOOT 15), August 10-11, 2015, Washington, DC, USA. Washington: USENIX Association, 2015: 123-132.
|
| [3] |
AVIRAM N, SCHINZEL S, SOMOROVSKY J, et al.DROWN: Breaking TLS Using SSLv2[C]//USENIX. 25th USENIX Security Symposium(USENIX Security 16), August 10-12, 2016, Austin, TX, USA. Washington: USENIX Association, 2016: 689-706.
|
| [4] |
MEYER C, SOMOROVSKY J, WEISS E, et al.Revisiting SSL/TLS Implementations: New Bleichenbacher Side Channels and Attacks[C]//USENIX. 23rd USENIX Security Symposium(USENIX Security 14), August 20-22, 2014, San Diego, CA, USA. Washington: USENIX Association, 2014: 733-748.
|
| [5] |
BHARGAVAN K, LEURENT G.Transcript Collision Attacks: Breaking Authentication in TLS, IKE, and SSH[C]//NDSS. the Network and Distributed System Security Symposium(NDSS 2016), February 21-24, 2016, San Diego, California, USA. California: The Internet Society, 2016: 234-239.
|
| [6] |
DURUMERIC Z, ADRIAN D, MIRIAN A, et al.Neither Snow nor Rain nor MITM: An Empirical Analysis of Email Delivery Security[C]//ACM. 2015 Internet Measurement Conference, October 28-30, 2015, Tokyo, Japan. NY: ACM, 2015: 27-39.
|
| [7] |
ADRIAN D, BHARGAVAN K, DURUMERIC Z, et al.Imperfect Forward Secrecy: How Diffie-Hellman Fails in Practice[C]//ACM. 22nd ACM SIGSAC Conference on Computer and Communications Security, October 12-16, 2015, Denver, CO, USA. NY: ACM, 2015: 5-17.
|
| [8] |
BEURDOUCHE B, BHARGAVAN K, DELIGNAT L A, et al.A Messy State of the Union: Taming the Composite State Machines of TLS[C]//IEEE. 2015 IEEE Symposium on Security and Privacy, May 17-21, 2015, San Jose, CA, USA. NJ: IEEE, 2015: 535-552.
|
| [9] |
DURUMERIC Z, MA Z, SPRINGALL D, et al.The Security Impact of HTTPS Interception[C]//NDSS. Network and Distributed System Security Symposium(NDSS 2017), February 26-March 1, 2017, San Diego, California, USA. California, The Internet Society, 2017: 345-354.
|
| [10] |
WAGNER D, SCHEIER B.Analysis of the SSL 3.0 Protocol[C]//USENIX. USENIX Workshop on Electronic Commerce, August 31-September 3, 1996, Boston, Massachusetts, USA. Washington: USENIX Association, 1996: 29-40.
|
| [11] |
BHARGAVAN K, BRZUSKA C, FOURNET C, et al.Downgrade Resilience in Key-exchange Protocols[C]//IEEE. 2016 IEEE Symposium on Security and Privacy, May 22-26, 2016, San Jose, CA, USA. NJ: IEEE, 2016: 506-525.
|
| [12] |
JACKSON C, BARTH A.Forcehttps: Protecting High-security Web Sites from Network Attacks[C]//ACM. 17th International Conference on World Wide Web, April 21-25, 2008, Beijing, China. NY: ACM, 2008: 525-534.
|
| [13] |
SZALACHOWSKI P, MATSUMOTO S, PERRIG A.PoliCert: Secure and Flexible TLS Certificate Management[C]//ACM. 2014 ACM SIGSAC Conference on Computer and Communications Security, November 3-7, 2014, Scottsdale, AZ, USA. NY: ACM, 2014: 406-417.
|
| [14] |
MAVROGIANNOPOULOS N, VERCAUTEREN F, VELICHKOV V, et al.A Cross-protocol Attack on the TLS Protocol[C]//ACM. 2012 ACM Conference on Computer and Communications Security, October 15-19, 2018, Toronto, Canada. NY: ACM, 2012: 62-72.
|
| [15] |
ALASHWALI E S, SZALACHOWSKI P.DSTC: DNS-based Strict TLS Configurations[C]//Springer. Risks and Security of Internet and Systems-13th International Conference(CRiSIS 2018), October 16-18, 2018, Arcachon, France. Berlin: Springer, 2018: 93-109.
|
| [16] |
STONE C M M, CHOTHIA T, Ruiter J. Extending Automated Protocol State Learning for the 802.11 4-way Handshake[C]// Springer. Computer Security-23rd European Symposium on Research in Computer Security(ESORICS 2018), September 3-7, 2018, Barcelona, Spain. Berlin: Springer, 2018: 325-345.
|
| [17] |
SAMARASINGHE N, MANNAN M. Another Look at TLS Ecosystems in Networked Devices vs. Web Servers[EB/OL]. , 2019-2-15.
|
| [18] |
EASTLAKE D. Domain Name System Security Extensions[EB/OL]. , 1999-3-1.
|
| [19] |
SCHECHTER S. Storing HTTP Security Requirements in the Domain Name System[EB/OL]. , 2007-10-28.
|
 ), GUO Lulu1,2
), GUO Lulu1,2