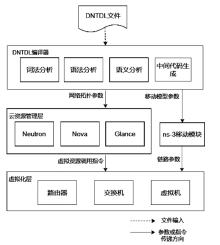
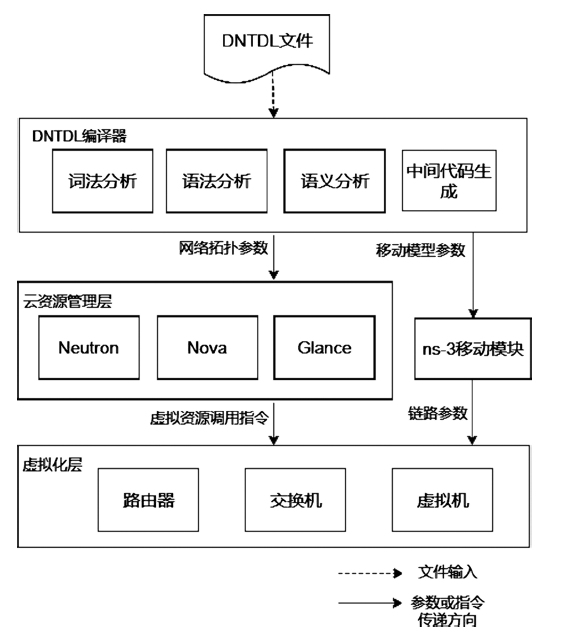
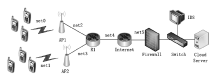
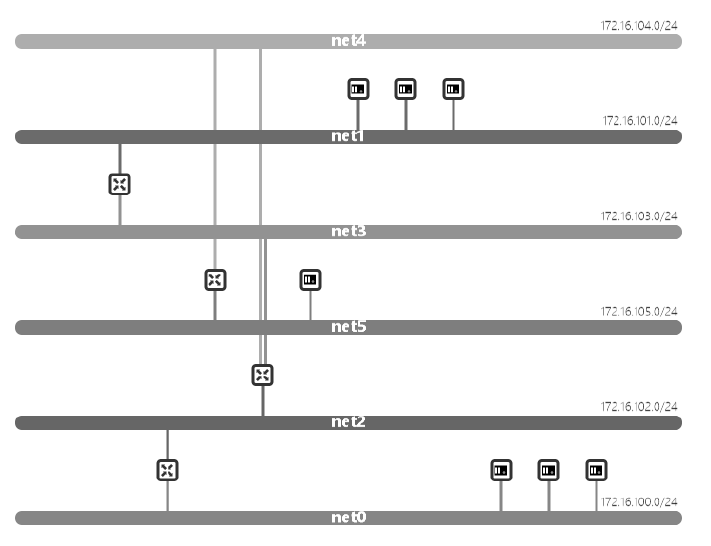
| [1] |
DINH H T, LEE C, NIYATO D, et al.A Survey of Mobile Cloud Computing: Architecture, Applications, and Approaches[J]. Wireless Communications & Mobile Computing, 2013, 13(18): 1587-1611.
|
| [2] |
MOLLAH M B, AZAD M A K, VASILAKOS A. Security and Privacy Challenges in Mobile Cloud Computing: Survey and Way Ahead[J]. Journal of Network and Computer Applications, 2017, 84(2): 38-54.
|
| [3] |
HE Li, YAO Yuanhui.Detection and Recognition Strategy for Anomaly of Cloud Virtual Machine Based on Context Clustering[J]. Netinfo Security, 2018, 18(12): 54-65.
|
|
何利,姚元辉.基于上下文聚类的云虚拟机异常检测与识别策略[J].信息网络安全,2018,18(12):54-65.
|
| [4] |
AHMED A, SABYASACHI A S.Cloud Computing Simulators: A Detailed Survey and Future Direction[C]//IEEE. 2014 IEEE International Advance Computing Conference(IACC), February 21-22, 2014, Gurgaon, India. NJ: IEEE, 2014: 866-872.
|
| [5] |
YUAN Xiao, CAI Zhiping, LIU Shuhao, et al.Large-scale Network Emulation Software and its Key Technologies[J]. Computer Technology and Development, 2014, 7(9): 9-12.
|
|
袁晓,蔡志平,刘书昊,等.大规模网络仿真软件及其仿真技术[J].计算机技术与发展,2014,7(9):9-12.
|
| [6] |
KABIR M H, ISLAM S, HOSSAIN J, et al.Detail Comparison of Network Simulators[J]. International Journal of Scientific & Engineering Research, 2014, 5(10): 203-218.
|
| [7] |
ROGÉRIO Leão Santos de Oliveira, SCHWEITZER C M, SHINODA A A, et al. Using Mininet for Emulation and Prototyping Software-defined Networks[C]//IEEE. 2014 IEEE Colombian Conference on Communications and Computing, June 4-6, 2014, Bogota, Colombia. NJ: IEEE, 2014: 1-6.
|
| [8] |
LIU Fangming, SHU Peng, JIN Hai, et al.Gearing Resource-poor Mobile Devices with Powerful Clouds: Architectures, Challenges, and Applications[J]. IEEE Wireless Communications, 2013, 20(3): 14-22.
|
| [9] |
VERBELEN T, SIMOENS P, TURCK F D, et al.Cloudlets: Bringing the Cloud to the Mobile User[C]//ACM. Proceedings of the Third ACM Workshop on Mobile Cloud Computing and Services, June 22-22, 2012, Low Wood Bay, UK. NY: ACM, 2012: 29-36.
|
| [10] |
CHEN Weibing, LIU Guangcan, ZHANG Ganglin.Principles of Mobile Communication[M]. Beijing: Tsinghua University Press, 2016.
|
|
陈威兵,刘光灿,张刚林.移动通信原理[M].北京:清华大学出版社,2016:195-239.
|
| [11] |
LU Gang, GUO Ronghua, ZHOU Ying, et al.Review of Malicious Traffic Feature Extraction[J]. Netinfo Security, 2018, 18(9): 7-15.
|
|
鲁刚,郭荣华,周颖,等.恶意流量特征提取综述[J].信息网络安全,2018,18(9):7-15.
|
| [12] |
KUMAR R, GUPTA N, CHARU S, et al.Open Source Solution for Cloud Computing Platform Using OpenStack[J]. International Journal of Computer Science and Mobile Computing, 2014, 3(5): 89-98.
|
| [13] |
CHEN Sisi, YANG Jin, LI Tao.Research on an Anomalies Detection Method for Firewall Rules[J]. Netinfo Security, 2018, 18(10): 78-84.
|
|
陈思思,杨进,李涛.一种防火墙规则冲突检测方法研究[J].信息网络安全,2018,18(10):78-84.
|