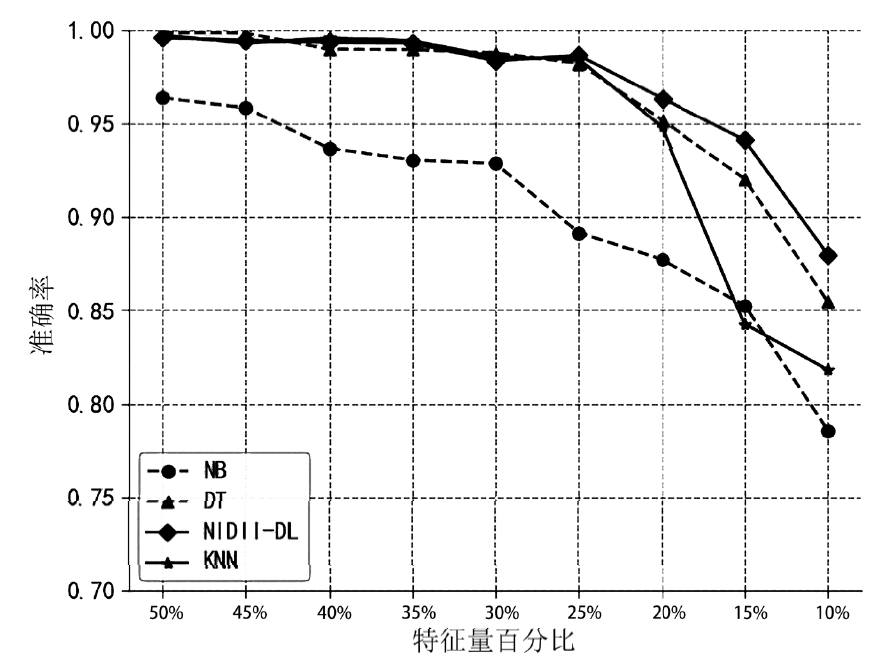
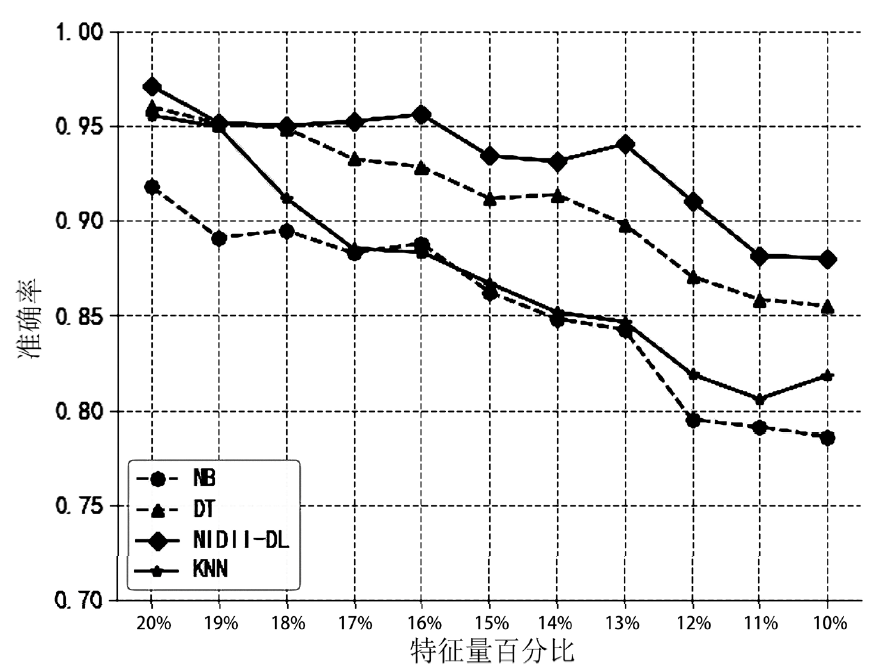
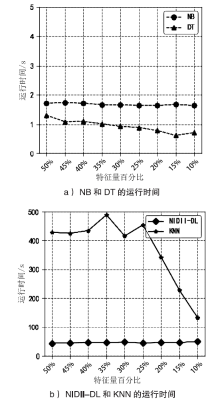
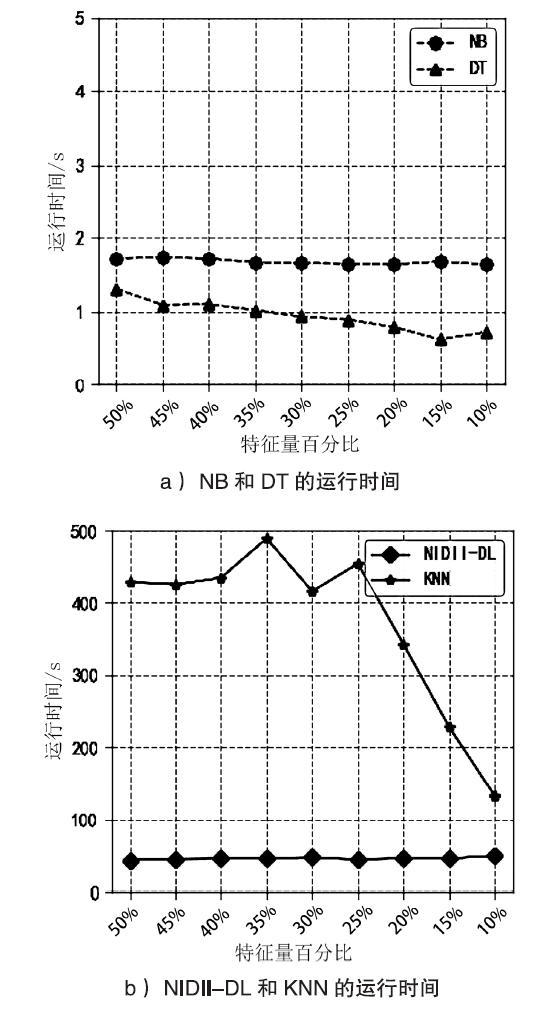
| [1] |
MA Liya, RAO Yu.February 2018 Network Security Monitoring Data Release[J]. Netinfo Security, 2018, 18(4): 97-98.
|
|
马莉雅,饶毓. 2018年2月网络安全监测数据发布[J]. 信息网络安全,2018,18(4):97-98.
|
| [2] |
MOUSTAFA N, SLAY J. The Significant Features of the UNSW-NB15 and the KDD99 Data Sets for Network Intrusion Detection Systems[EB/OL]. , 2019-2-11.
|
| [3] |
KANG S H, KIM K J.A Feature Selection Approach to Find Optimal Feature Subsets for the Network Intrusion Detection System[J]. Cluster Computing, 2016, 19(1): 1-9.
|
| [4] |
BUCZAK A L, GUVEN E.A Survey of Data Mining and Machine Learning Methods for Cyber Security Intrusion Detection[J]. IEEE Communications Surveys & Tutorials, 2016, 18(2): 1153-1176.
|
| [5] |
LEE W, STOLFO S J, CHAN P K, et al.Real Time Data Mining-based Intrusion Detection[C]// DARPA . DARPA Information Survivability Conference & Exposition II, June 12-14, 2001, Anaheim, CA, USA. NJ: IEEE, 2001: 89-100.
|
| [6] |
NADIAMMAI G V, HEMALATHA M.Effective Approach toward Intrusion Detection System Using Data Mining Techniques[J]. Egyptian Informatics Journal, 2014, 15(1): 37-50.
|
| [7] |
ZHANG Jiong, ZULKEMINE, M, HAQUE A, et al.Random-Forests-based Network Intrusion Detection Systems[J]. IEEE Transactions on Systems Man & Cybernetics Part C, 2008, 38(5): 649-659.
|
| [8] |
DEVARAKONDA N, PAMIDI S, KUMARI V V, et al.Intrusion Detection System using Bayesian Network and Hidden Markov Model[J]. Procedia Technology, 2012, 4: 506-514.
|
| [9] |
ZHAO Jianhua, LIU Ning.A Dynamic Intrusion Detection Model Based on Immunity for Wireless Sensor Network[C]// ISA . 3rd International Workshop on Intelligent Systems and Applications, May 28-29, 2011, Wuhan, China. NJ: IEEE, 2011: 1-3.
|
| [10] |
SRINIVASA K G, PRAMOD N. gNIDS: Rule-based Network Intrusion Detection System Using Genetic Algorithms[J]. Intelligent Systems Technologies and Applications, 2012, 11(3/4): 252-266.
|
| [11] |
HANSEN J V, LOWRY P B, MESERVY R D, et al.Genetic Programming for Prevention of Cyberterrorism through Dynamic and Evolving Intrusion Detection[J]. Decision Support Systems, 2007, 43(4): 1362-1374.
|
| [12] |
HOOKS D, YUAN Xiaohong, ROY K, et al.Applying Artificial Immune System for Intrusion Detection[C]//IEEE. 2018 IEEE Fourth International Conference on Big Data Computing Service and Applications (BigDataService), March 26-29, 2018, Bamberg, Germany. NJ: IEEE, 2018: 287-292.
|
| [13] |
LIU Lingbing.Research on Intrusion Detection System Based on Neural Network[D]. huainan: Anhui University of Science & Technology, 2011.
|
|
刘凌冰. 基于神经网络的入侵检测系统的研究[D].淮南:安徽理工大学,2011.
|
| [14] |
AL-ZEWAIRI M, ALMAJALI S, AWAJAN A.Experimental Evaluation of a Multi-layer Feed-Forward Artificial Neural Network Classifier for Network Intrusion Detection System[C]//ICTCS. International Conference on New Trends in Computing Sciences, October 11-13, 2017, Amman, Jordan. NJ: IEEE, 2017: 167-172.
|
| [15] |
HAMID Y, SHAH F A, SUGUMARAN M.Wavelet Neural Network Model for Network Intrusion Detection System[J]. International Journal of Information Technology, 2019, 11(2): 251-263.
|
| [16] |
MOHAMMADI M, RAAHEMI B, AKBARI A, et al.New Class-dependent Feature Transformation for Intrusion Detection Systems[J]. Security & Communication Networks, 2012, 5(12): 1296-1311.
|
| [17] |
HE Xiang, LIU Sheng, JIANG Jiguo.Comparative Study of Intrusion Detection Methods Based on Machine Learning[J]. Netinfo Security, 2018, 18(5): 1-11.
|
|
和湘,刘晟,姜吉国. 基于机器学习的入侵检测方法对比研究[J]. 信息网络安全,2018,18(5):1-11.
|
| [18] |
SULTANA N, CHILAMKURTI N, WEI Peng, et al.Survey on SDN-based Network Intrusion Detection System Using Machine Learning Approaches[J]. Peer-to-Peer Networking and Applications, 2019, 12(2): 493-501.
|
| [19] |
BUCKLEY C, VOORHEES E M.Retrieval Evaluation with Incomplete Information[C]//ACM. The 27th Annual International ACM SIGIR Conference on Research and Development in Information Retrieval, July 25-29, 2004, Sheffield, United Kingdom. New York: ACM, 2004: 25-32.
|
| [20] |
LI Wei, YANG Zhongming.Review of Intrusion Detection System[J]. Journal of Jilin University:Information Sci Ed, 2016(5): 657-662.
|
|
李威,杨忠明. 入侵检测系统的研究综述[J]. 吉林大学学报:信息科学版,2016(5):657-662.
|
| [21] |
AL-KASASSBEH M, AL-NAYMAT G, HAMADNEH N, et al. Intensive Preprocessing of KDD Cup 99 for Network Intrusion Classification Using Machine Learning Techniques[EB/OL]. , 2019-2-11.
|
 )
)