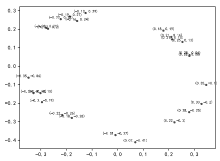
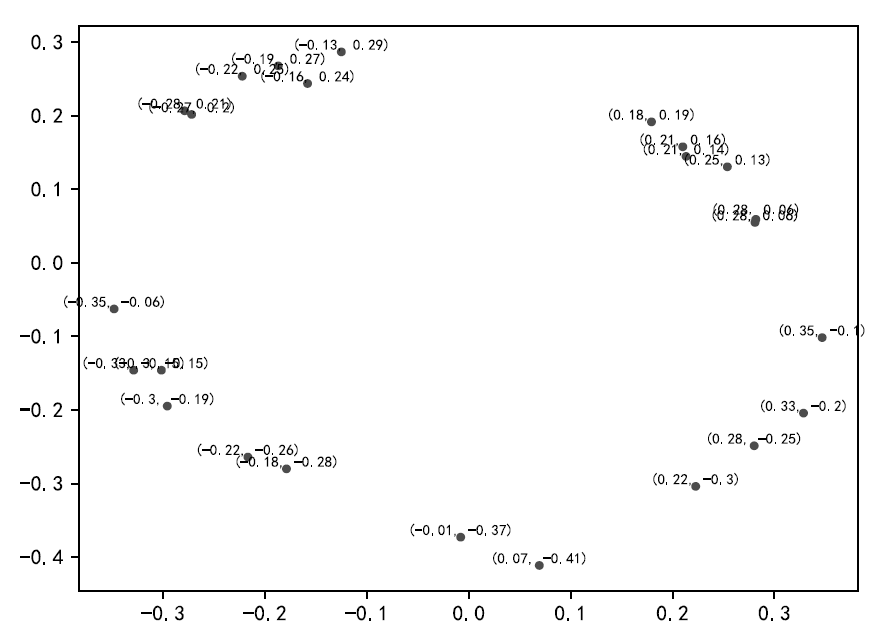
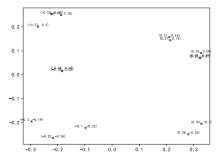
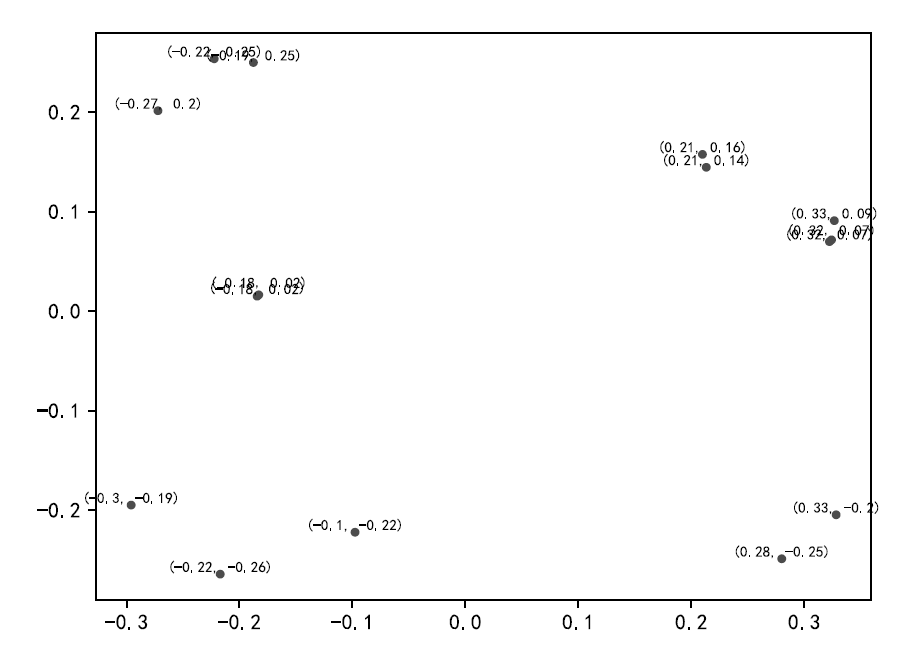
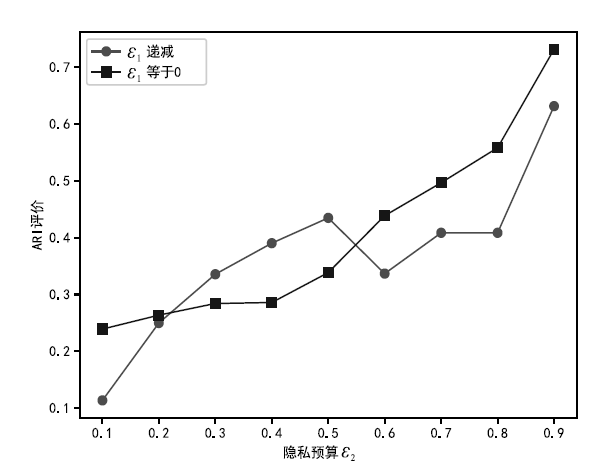
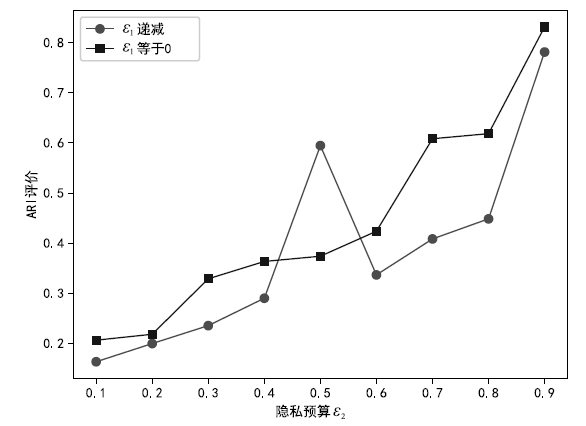
| [1] |
LU Tianliang, WANG Qiao, LIU Yingqing.Problems of User’s Privacy Leakage During Insecure Communication[J]. Netinfo Security, 2015, 15(9): 119-123.
|
|
芦天亮,王侨, 刘颖卿. 不安全通信中的用户隐私泄露问题[J]. 信息网络安全,2015,15(9):119-123.
|
| [2] |
FANG Yuejian, ZHU Jinzhong, ZHOU Wen, et al.A Survey on Data Mining Privacy Protection Algorithms[J]. Netinfo Security, 2017, 17(2): 6-11.
|
|
方跃坚,朱锦钟,周文,等. 数据挖掘隐私保护算法研究综述[J]. 信息网络安全,2017,17(2):6-11.
|
| [3] |
LIU Yahui, ZHANG Tieying, JIN Xiaolong, et al.Personal Privacy Protection in the Era of Big Data[J]. Journal of Computer Research and Development, 2015, 52(1): 1-19.
|
|
刘雅辉,张铁赢,靳小龙,等. 大数据时代个人隐私保护[J]. 计算机研究与发展,2015,52(1):1-19.
|
| [4] |
HU Haibo, XU Jianliang, XU Xizhong, et al.Private Search on Key-value Stores with Hierarchical Indexes[C]//IEEE. IEEE 30th International Conference on Data Engineering, March 31-April 4, 2014, Chicago, IL, USA. New Jersey: IEEE, 2014: 628-639.
|
| [5] |
DWORK C.Differential Privacy[C]//Springer. 33rd International Conference on Automata, Languages and Programming, July 10-14, 2006, Venice, Italy. Heidelberg: Springer, 2006: 1-12.
|
| [6] |
WU Weimin, HUANG Huankun.A DP-DBScan Clustering Algorithm Based on Differential Privacy Preserving[J]. Computer Engineering and Science, 2015, 37(4): 830-834.
|
|
吴伟民,黄焕坤. 基于差分隐私保护的DP—DBScan聚类算法研究[J]. 计算机工程与科学,2015,37(4):830-834.
|
| [7] |
MA Yinfang, ZHANG Lin.KDCK-medoids Dynamic Clustering Algorithm Based on Differential Privacy[J]. Computer Science, 2016, 43(z2): 368-372.
|
|
马银方,张琳. 基于差分隐私保护的KDCK-medoids动态聚类算法[J]. 计算机科学,2016,43(z2):368-372.
|
| [8] |
ZHANG Yao, LI Shuyu, LI Zekun, et al.Differential Privacy Protection BIRCH Algorithm[J]. Journal of Southeast University(Natural Science Edition), 2017(s1): 140-144.
|
|
张瑶,李蜀瑜,李泽堃,等. 差分隐私保护BIRCH算法[J]. 东南大学学报:自然科学版,2017(s1):140-144.
|
| [9] |
WANG Hao, XU Zhengquan.Differential privacy protection method for trajectory clustering[J]. Journal of Huazhong University of Science and Technology: Natural Science Edition, 2018, 46(1): 32-36.
|
|
王豪,徐正全. 面向轨迹聚类的差分隐私保护方法[J]. 华中科技大学学报:自然科学版,2018,46(1):32-36.
|
| [10] |
LI Hongcheng, WU Xiaoping, CHEN Yan. k-means Clustering Method Preserving Differential Privacy in MapReduce Framework[J]. Journal on Communications, 2016, 37(2): 124-130.
|
|
李洪成,吴晓平,陈燕. MapReduce框架下支持差分隐私保护的k-means聚类方法[J]. 通信学报,2016,37(2):124-130.
|
| [11] |
DWORK C, MCSHERRY F, NISSIM K, et al.Calibrating Noise to Sensitivity in Private Data Analysis[C]//Springer. 2006 Theory of Cryptography Conference, March 4-7, 2006, New York, NY, USA. Heidelberg: Springer, 2006: 265-284.
|
| [12] |
DANDEKAR P, FAWAZ N, IOANNIDIS S.Privacy Auctions for Recommender Systems[C]//Springer. 2012 International Workshop on Internet and Network Economics, December 10-12, 2012, Liverpool, United Kingdom. Heidelberg: Springer, 2012: 309-322.
|
| [13] |
GAO Zhiqiang, SUN Yixiao, CUI Xiaolong, et al.Privacy-Preserving Hybrid K-Means[J]. International Journal of Data Warehousing and Mining, 2018, 14(2): 1-17.
|
| [14] |
LI Yang, HAO Zhifeng, WEN Wen, et al.Research on Differential Privacy Preserving k-means Clustering[J]. Computer Science, 2013, 40(3): 287-290.
|
|
李杨,郝志峰,温雯,等. 差分隐私保护k-means聚类方法研究[J]. 计算机科学,2013,40(3):287-290.
|
| [15] |
VISWANATH P.Histogranm-based Estimation Techniques in Databases[D]. Madison: University of Wisconsirr-Madison, 1997.
|