| [1] |
ZHANG Wenxiu, ZHU Qinhua.Research on Construction Methods of Domain Ontology[J]. Library&Information, 2011, 2011(1):16-19.
|
|
张文秀,朱庆华.领域本体的构建方法研究[J].图书与情报, 2011, 2011(1):16-19.
|
| [2] |
SHANG Xinli.Comparative Analysis of Foreign Ontology Construction Methods[J]. Library and Information Service, 2012, 56(4):116-119.
|
|
尚新丽. 国外本体构建方法比较分析[J].图书情报工作, 2012, 56(4):116-119.
|
| [3] |
USCHOLD M,GRUNINGER M.Ontologies: Principles,Methods and Applications[J].Knowledge Engineering Review, 1996, 11(2):14-17.
|
| [4] |
NOY N F, MCGUNINNESS D L.Ontology Development 101: A Guide to Creating Your First Ontology[R]. Knowldege Systems Laboratory, Stanford University,Stanford Knowledge Systems Laboratory Technical Report KSL-01-05 and Stanford Medical Informatics Technical Report SMI-2001-0880, 2001.
|
| [5] |
Schreiber G, Wielinga B, Jansweijer W.The KACTUS View on the 'O' Word[J].IJCAI Workshop on Basic Ontological Issues in Knowledge Sharing, 1995,98(98):159-168.
|
| [6] |
FOX M S,GRUNUNGER M.Enterprise Modeling[J].AI Magazine, 1998, 19(3):109-121.
|
| [7] |
USCHOLD M,KING M,MORALEE S,et al.The Enterprise Ontology[J].The Knowledge Engineering Review, 1998, 13(1):31-89.
|
| [8] |
FERNDANDEZ M,GORMEZ P A,JURISTO N.Methontology: From Ontological Art towards Ontological Engineering[EB/OL].,2018-6-15.
|
| [9] |
LIU Wei, LI Quan-lin, RUI Li.A Performance Analysis Method for Intrusion Prevention System[J]. Netinfo Security, 2015, 15(9): 46-49.
|
|
刘伟, 李泉林, 芮力. 一种入侵防御系统性能分析方法[J]. 信息网络安全, 2015, 15(9): 46-49.
|
| [10] |
ZHANG Qingliang, QIN Yuanqing.Research on Security Assessment Index and Its Application for Shipboard Network Based on DDS[J]. Netinfo Security, 2017, 17(2): 73-78.
|
|
章清亮, 秦元庆. 基于DDS通信的舰载网络安全评估指标及应用研究[J]. 信息网络安全, 2017, 17(2): 73-78.
|
| [11] |
BIALAS A.Ontology-Based Security Problem Definition and Solution for the Common Criteria Compliant Development Process[C]//IEEE. International Conference on Dependability of Computer Systems, June 30-July2,2009,Brunow, Poland. Depcos-Relcomex. NJ: IEEE, 2009:3-10.
|
| [12] |
BIALAS A.Common Criteria Related Security Design Patterns for Intelligent Sensors—Knowledge Engineering-Based Implementation[J].Sensors, 2011, 11(11):8085-8114.
|
| [13] |
ZHANG Zheng.Research On Product Reviews Based on Domain Ontology[D]. Xinxiang: Henan Normal University,2012.
|
|
张征. 基于领域本体的产品评价研究[D]. 新乡: 河南师范大学, 2012.
|
| [14] |
FENG Shufang,WANG Suge.The Construction of Automobile Domain Ontology Knowledge Base for Opinion Mining[J].Computer Applications and Software, 2011, 28(5):45-47.
|
|
冯淑芳,王素格.面向观点挖掘的汽车评价本体知识库的构建[J].计算机应用与软件, 2011, 28(5):45-47.
|
| [15] |
GU Tiejun,LI Yi,GU Jian.Ontology Modeling for Network Vulnerability Scanners Standard and Research on Related Evaluation Tool[J]. Netinfo Security, 2013, 13(10): 141-143.
|
|
顾铁军,李毅,顾健. 网络脆弱性扫描产品标准本体构建及测评工具研究[J]. 信息网络安全, 2013,13(10): 141-143.
|
| [16] |
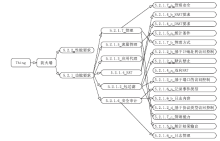
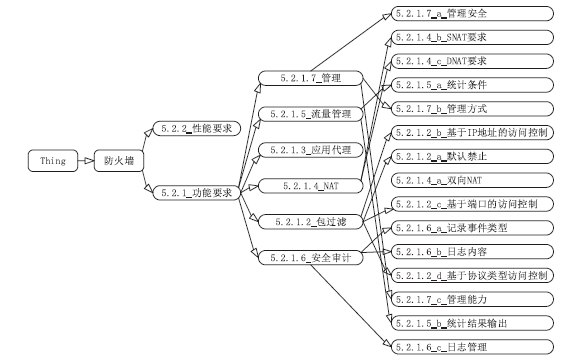
GB/T 20281-2015, Information Security Technology-Security Technical Requirements and Testing and Evaluation Approaches for Firewall[S].Beijing: China standard press,2015.
|
|
GB/T 20281-2015,信息安全技术防火墙技术要求和测试评价方法[S].北京:中国标准出版社,2015
|