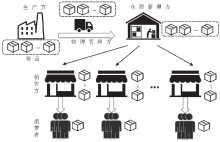
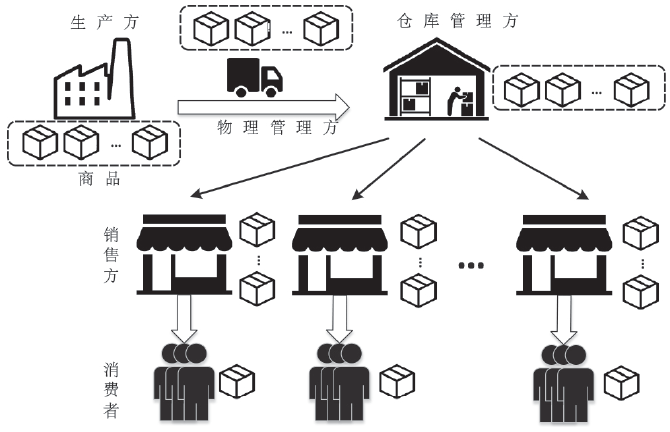
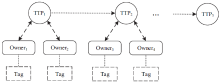
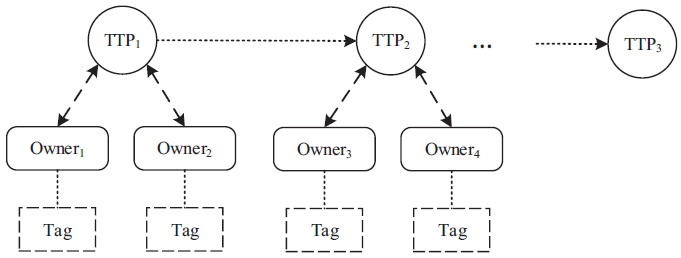
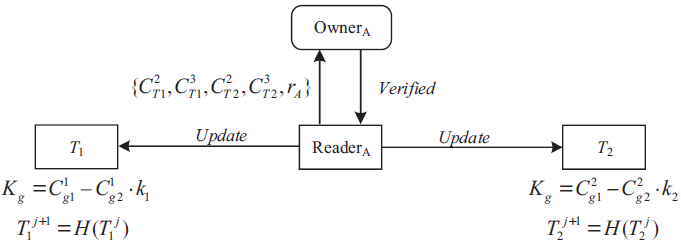
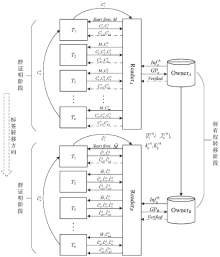
| [1] |
MOLNAR D, SOPPERA A, WAGNER D.A Scalable, Delegatable Pseudonym Protocol Enabling Ownership Transfer of RFID Tags[C]//SAC. Proceedings of the 12th International Conference on Selected Areas in Cryptograph,August 11-12, 2005,Kingston, Canada. Berlin:Springer, 2005: 276-290.
|
| [2] |
ZHOU W, YOON E J, PIRAMUTHU S.Simultaneous Multi-level RFID Tag Ownership & Transfer in Health Care Environments[J]. Decision Support Systems, 2012, 54(1): 98-108.
|
| [3] |
ZUO Y.Changing Hands Together: a Secure Group Ownership Transfer Protocol for RFID Tags[C]//IEEE.HICSS '10 Proceedings of the 2010 43rd Hawaii International Conference on System Sciences,January 5 - 8, 2010,Honolulu, HI, USA. New York:IEEE, 2010: 1-10.
|
| [4] |
XIN W, GUAN Z, YANG T, et al. An Efficient Privacy-preserving RFID Ownership Transfer Protocol[EB/OL]., 2018-1-15.
|
| [5] |
CAO T, CHEN X, DOSS R, et al.RFID Ownership Transfer Protocol Based on Cloud[J]. Computer Networks, 2016, 105: 47-59.
|
| [6] |
SUNDARESAN S, DOSS R, ZHOU W, et al.Secure Ownership Transfer for Multi-tag multi-owner Passive RFID Environment with Individual-owner-privacy[J]. Computer Communications, 2015, 55: 112-124.
|
| [7] |
XIA Geming, SHI Lizhe,ZHOU Wen, et al.An Optimal Design to Lightern the Agreement of Bidirectional Identification on RFID[J]. Netinfo Security,2014, 14(2):58-62.
|
|
夏戈明, 史立哲, 周文,等. 轻量级RFID双向通信认证协议优化方案[J]. 信息网络安全, 2014,14(2): 58-62.
|
| [8] |
SAITO J, IMAMOTO K, SAKURAI K.Reassignment Scheme of an RFID Tag’s Key for Owner Transfer[C]//ACM.EUC'05 Proceedings of the 2005 International Conference on Embedded and Ubiquitous Computing,December 6 - 9, 2005,Nagasaki, Japan. Berlin:Springer, 2005: 1303-1312.
|
| [9] |
DOSS R, ZHOU W, YU S.Secure RFID Tag Ownership Transfer Based on Quadratic Residues[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(2): 390-401.
|
| [10] |
ZHANG X, HUANG W, XU H, et al.The Lightweight Ownership Transfer Protocol Using Physically Unclonable Function[J]. International Journal of Security and Its Applications, 2016, 10(2): 115-128.
|
| [11] |
MUNILLA J, BURMESTER M, PEINADO A, et al.RFID Ownership Transfer with Positive Secrecy Capacity Channels[J]. Sensors, 2016, 17(1): 53.
|
| [12] |
GONG L, NEEDHAM R, YAHALOM R.Reasoning about Belief in Cryptographic Protocols[C]//IEEE.1990 IEEE Computer Society Symposium on Research in Security and Privacy,May 7-9, 1990,Oakland, CA.New York:IEEE, 1990: 234-248.
|
| [13] |
KOBLITZ N.Elliptic Curve Cryptosystems[J]. Mathematics of Computation, 1987, 48(177): 203-209.
|
| [14] |
BELLARE M, CANETTI R, KRAWCZYK H.Message Authentication Using Hash Functions: the HMAC Construction[J]. RSA Laboratories’ CryptoBytes, 1996, 2(1): 12-15.
|
| [15] |
YANG X, XU C, LI C.A Privacy Model for RFID Tag Ownership Transfer[J].Security and Communication Networks, 2017(1):1-11.
|
| [16] |
JIANG Zhengjun, TIAN Haibo, ZHANG Fangguo.Survey on PUF-based RFID Anti-counterfeiting Techniques[J].Netinfo Security, 2016, 16(4):38-43.
|
|
蒋政君, 田海博, 张方国. 基于PUF的RFID防伪技术研究综述[J]. 信息网络安全, 2016,16(4): 38-43.
|
| [17] |
WU Xiao, CHANG Cheng, TAN Wenjie, et al.An anti-tampering Tag Authentication Method Based on RFID and Digital Watermarking[J]. Netinfo Security, 2015, 15(8):26-34
|
|
吴潇, 常成, 覃文杰,等. 基于RFID和数字水印技术的标签防伪验证方法[J]. 信息网络安全, 2015,15(8): 26-34.
|
| [18] |
OSAKA K, TAKAGI T, YAMAZAKI K, et al.An Efficient and Secure RFID Security Method with Ownership Transfer[C]//IEEE. 2006 International Conference Computational Intelligence and Security,November 3-6 ,2006, Guangzhou, China.New York:IEEE, 2008: 147-176.
|
| [19] |
FOULADGAR S, AFIFI H.A Simple Privacy Protecting Scheme Enabling Delegation and Ownership Transfer for RFID Tags[J]. Journal of Communications, 2007, 2(6): 6-13.
|
| [20] |
FOULADGAR S, AFIFI H.An Efficient Delegation and Transfer of Ownership Protocol for RFID Tags[EB/OL]., 2018-1-15.
|
 ), Chaoliang LI5
), Chaoliang LI5